Topic Aware Influence Maximization Framework
|
|
|
- Πυθις Καραβίας
- 1 χρόνια πριν
- Προβολές:
Transcript
1 NATIONAL AND KAPODISTRIAN UNIVERSITY OF ATHENS SCHOOL OF SCIENCES DEPARTMENT OF INFORMATICS AND TELECOMMUNICATIONS PROGRAM OF POSTGRADUATE STUDIES COMPUTER SCIENCE MASTER THESIS Xenofon V. Kitsios SUPERVISOR: Alexis Delis, Professor ATHENS NOVEMBER 202
2 ΕΘΝΙΚΟ ΚΑΙ ΚΑΠΟΔΙΣΤΡΙΑΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΘΗΝΩΝ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΚΑΙ ΤΗΛΕΠΙΚΟΙΝΩΝΙΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΠΛΗΡΟΦΟΡΙΚΗ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Πλαίσιο Μεγιστοποίησης Επιρροής με Επιγνωσή Θέματος Ξενοφών Β. Κίτσιος ΕΠΙΒΛΕΠΩΝ: Αλέξης Δελής, Καθηγητής ΑΘΗΝΑ ΝΟΕΜΒΡΙΟΣ 202
3 MASTER THESIS Xenofon V. Kitsios R.N.: CS SUPERVISOR: Alexis Delis, Professor EXAMINATION COMMITTEE: Alexis Delis, Professor Mema Rousopoulou, Professor Panagiotis Liakos, Postdoctoral Researcher November 202
4 ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Πλαίσιο Μεγιστοποίησης Επιρροής με Επιγνωσή Θέματος Ξενοφών Β. Κίτσιος Α.Μ.: CS ΕΠΙΒΛΕΠΩΝ: Αλέξης Δελής, Καθηγητής ΕΞΕΤΑΣΤΙΚΗ ΕΠΙΤΡΟΠΗ: Αλέξης Δελής, Καθηγητής Μέμα Ρουσοπούλου, Καθηγήτρια Παναγιώτης Λιάκος, Μεταδιδακτορικός Ερευνητής Νοέμβριος 202
5 ABSTRACT The focus of the thesis is given on the development of a novel framework to deal with the topic aware influence maximization problem. The problem appears high computational complexity and belong in the area of social influence which involves both psychological and sociological aspects. In particular, the influence maximization problem aims to find a subset of nodes that maximize the expected spread of influence in a network. Due to NP hard computational complexity, the approximation algorithms are imperative to gain optimal or near optimal solution with minor computational effort. In addition, real life networks should be used to provide valid results and significant information about how social influence is spread avoiding errors and problematic conclusions. In the context of this thesis, the topic aware influence maximization problem is studied and a novel framework based on the Hyperlink Induced Topic Search (HITS) algorithm is introduced. The proposed solution approach consists of two main components, i.e., the HITS algorithm and the Greedy or Cost Effective Lazy Forward (CELF) algorithms with modified Independent Cascade model in order to improve the results of the influence according to a topic. The HITS algorithm aims to analyze links and the Greedy and CELF algorithms to find the nodes that maximize the expected spread of influence in a network. For the evaluation, the Neo4j graph database is used as a platform for the empirical experiments. Moreover, datasets of the Yelp social network alongside with generated graphs based on Barabási Albert model provide the necessary data for testing. The computational results illustrate the pertinence of the developed algorithms and underline the role of the proposed framework s components. Finally, it is worth to mention that the developed Greedy and CELF algorithms of this thesis have been contributed to the Neo4j opensource community. SUBJECT AREA: Social Network Analysis Cas KEYWORDS: Influence Maximization, Topic Aware, Greedy, CELF, Independent cade model, HITS, Neo4j, Barabási Albert model, Yelp dataset
6 ΠΕΡΙΛΗΨΗ H διπλωματική εργασία εστιάζει στην ανάπτυξη ενός νέου πλαισίου για την αντιμετώπιση του προβλήματος της μεγιστοποίησης με επίγνωση θέματος. Το πρόβλημα παρουσιάζει υψηλή υπολογιστική πολυπλοκότητα και ανήκει στην περιοχή της κοινωνικής επιρροής η οποία περιλαμβάνει τόσο ψυχολογικές όσο και κοινωνιολογικές πτυχές. Συγκεκριμένα, το πρόβλημα μεγιστοποίησης επιρροής στοχεύει στην εύρεση ενός υποσυνόλου από κόμβους που μεγιστοποιούν την αναμενόμενη διάδοση επιρροής σε ένα δίκτυο. Λόγω της NP hard υπολογιστικής πολυπλοκότητας, οι προσεγγιστικοί αλγόριθμοι είναι επιτακτικοί για την εύρεση της βέλτιστης ή σχεδόν βέλτιστης λύσης με μικρή υπολογιστική προσπάθεια. Επιπλέον, θα πρέπει να χρησιμοποιούνται πραγματικά δίκτυα για να παρέχουν έγκυρα αποτελέσματα και σημαντικές πληροφορίες σχετικά με το τρόπο διάδοσης της κοινωνικής επιρροής αποφεύγοντας έτσι λάθη και προβληματικά συμπεράσματα. Στο πλαίσιο αυτής της διπλωματικής εργασίας, το πρόβλημα της μεγιστοποίησης επιρροής με επίγνωση θέματος μελετήθηκε και ένα νέο πλαίσιο βασισμένο στον αλγόριθμο Hyperlink Induced Topic Search (HITS) εισήχθη. Η προτεινόμενη προσεγγιστική λύση αποτελείται από δύο μέρη, δηλαδή τον αλγόριθμο HITS και τους αλγορίθμους Greedy ή Cost Effective Lazy Forward (CELF) με τροποποιημένο το μοντέλο Independent Cascade ώστε να βελτιωθούν τα αποτελέσματα της επιρροής με επίγνωση θέματος. Ο αλγόριθμος HITS στοχεύσει να αναλύει συνδέσεις και οι αλγόριθμοι Greedy και CELF να βρίσκουν τους κόμβους που μεγιστοποιούν την αναμενόμενη διάδοση επιρροής σε ένα δίκτυο. Για την αξιολόγηση, η Neo4j βάση δεδομένων γράφου χρησιμοποιήθηκε σαν πλατφόρμα για τα εμπειρικά πειράματα. Επιπλέον, σύνολα δεδομένων από το κοινωνικό δίκτυο Yelp μαζί με δημιουργούμενους γράφους βασισμένους στο μοντέλο Barabási Albert παρέχουν τα απαραίτητα δεδομένα για δοκιμή. Τα υπολογιστικά πειράματα απεικονίζουν την συνάφεια των αναπτυγμένων αλγορίθμων και υπογραμμίζουν το ρόλο των μερών του προτεινόμενου πλαισίου. Τέλος, αξίζει να σημειωθεί ότι οι αναπτυγμένοι αλγόριθμοι Greedy και CELF αυτής της διπλωματικής εργασίας έχουν γίνει συνεισφορά στη Neo4j κοινότητα ανοιχτού κώδικα. ΘΕΜΑΤΙΚΗ ΠΕΡΙΟΧΗ: Ανάλυση Κοινωνικών Δικτύων ΛΕΞΕΙΣ ΚΛΕΙΔΙΑ: Μεγιστοποίηση Επιρροής, Επιγνωσή Θέματος, Greedy, CELF, Μοντέλο Independent Cascade, HITS, Neo4j, Μοντέλο Barabási Albert, Σύνολο Δεδομένων Yelp
7 ACKNOWLEDGEMENTS Firstly, I would like to express my appreciation to Prof. Alexis Delis. Furthermore, I would like to thank the committee examiner Prof. Mema Rousopoulou. The completion of this study could not have been possible without the expertise and support of Dr. Panagiotis Liakos. Finally, I would like to thank my family for their support. Especially my cousin Afroditi Anagnostopoulou.
8 CONTENTS PREFACE... 5 INTRODUCTION INFLUENCE MAXIMIZATION PROBLEM Definition Literature Review HYPERLINK INDUCED TOPIC SEARCH (HITS) ALGORITHM Definition Example TOPIC AWARE INFLUENCE MAXIMIZATION FRAMEWORK Definition Example Create a Projected Graph to Apply HITS Algorithm Apply HITS Algorithm Create a Projected Graph to Apply Greedy or CELF Algorithm Apply Greedy or CELF Algorithm EXPERIMENTS Software Neo4j Graph Data Science (GDS) Library Data Sources Barabási Albert Model Yelp Dataset Performance Experiments on Greedy and CELF Algorithms Greedy/CELF Algorithms Experiment Multithreads Large Scale Networks Experiment Seed Set Size Experiment Monte Carlo Simulations Experiment Propagation Probability Experiment Evaluating Topic Aware Results CONCLUSIONS ABBREVIATIONS ACRONYMS APPENDICES... 55
9 A EXPERIMENTS RUNNING TIMES AND PARAMETERS REFERENCES... 6
10 LIST OF FIGURES 3. HITS algorithm example Results of the query newspapers HITS algorithm example Setting all hubscore = and authorityscore = HITS algorithm example Applying authority update rule for step HITS algorithm example Applying hub update rule for step HITS algorithm example Applying authority update rule for step HITS algorithm example Applying hub update rule for step HITS algorithm example Normalizing authorityscore and hubscore Example /2 of using hubscore into influence maximization process Example 2/2 of using hubscore into influence maximization process Topic aware influence maximization framework example The initial network Topic aware influence maximization framework example edges of the initial network Topic aware influence maximization framework example edges of the initial network Topic aware influence maximization framework example IN_CATEGORY edges of the initial network Topic aware influence maximization framework example Projected graph for topic Bars Topic aware influence maximization framework example Projected graph for topic Shopping GDS library Standard operations Barabási Albert model Schema used in topic blind experiments Yelp dataset Schema used in topic aware experiments Performance experiment Greedy/CELF algorithms Performance experiment Greedy algorithm multithreads Performance experiment CELF algorithm multithreads Performance experiment Greedy/CELF algorithms multithreads Performance experiment Number of nodes Performance experiment Seed set size... 46
11 5.0 Performance experiment Monte Carlo simulations (part /2) Performance experiment Monte Carlo simulations (part 2/2) Performance experiment Propagation probability... 48
12 LIST OF TABLES 4. Topic aware influence maximization framework example HITS algorithm results for topic Bars Topic aware influence maximization framework example HITS algorithm results for topic Shopping Topic aware influence maximization framework example Influence maximization results for topic Bars Topic aware influence maximization framework example Influence maximization results for topic Shopping Topic aware influence maximization framework example Influence maximization results on topic blind Yelp dataset Number of nodes/edges per type Performance experiment Spread with various number of Monte Carlo simulations Yelp dataset Top 0 categories based on the number of businesses Evaluating experiment 0 users with the highest topic blind influence in Yelp dataset Evaluating experiment 0 users with the highest influence for Restaurant category in Yelp dataset Evaluating experiment 0 users with the highest influence for Food category in Yelp dataset Evaluating experiment s with the highest influence for Shopping category in Yelp dataset Evaluating experiment Parameters of topic aware influence maximization with HITS algorithm Evaluating experiment Running time per topic of topic aware influence maximization with HITS algorithm... 5 A. Performance experiment Greedy/CELF algorithms running times and parameters A.2 Performance experiment Large scale networks running times and parameters A.3 Performance experiment Seed set size running times and parameters... 57
13 A.4 Performance experiment Monte Carlo simulations running times and parameters A.5 Performance experiment Propagation probability running times and parameters... 59
14 LIST OF ALGORITHMS 2. Independent Cascade model Linear Threshold model Greedy algorithm CELF algorithm... 22
15 PREFACE This thesis entitled as has been prepared by Xenofon Kitsios. The thesis is submitted as partial fulfilment of the requirement for the MSc degree Computer Science at Department of Informatics and Telecommunications at the National and Kapodistrian University of Athens. The subject of this thesis has been inspired from the Social Network Analysis course taught by Dr. Panagiotis Liakos.
16 . INTRODUCTION Social influence involves the ways and efforts in order to change another person s beliefs, attitudes, or behavior. The main characteristic of the social influence process is the high level of complexity since it involves both psychological and sociological aspects. However, the target group may not understand the influence attempt and many times the outcomes are not consistent with the goals of the communicator. Research on social influence covers multidisciplinary fields and explores it on the basis of different questions such as viral marketing, disease modelling, etc. In this context, social influence is modelled upon networks and is based on sociological assumptions about how people become influenced. Even though this is an efficient approach to present interactions among individuals, it is not capable to provide information about how influence is spread. Towards this direction, the influence maximization problem aims to find a subset of nodes such that the resulting propagation from the subset reaches the largest number of nodes in the network. The influence maximization problem is an NP hard and several approximation algorithms have been proposed to deal with it. However, they focus on a non real representation without considering a dynamic environment which responds to the realistic conditions. Most of the times, this simplification result to errors and problematic conclusions that do not capture the effect of social influence in practice. For this reason, real life networks should be used in an attempt to provide valid results and significant information about how social influence is spread. Limited studies conducted to study the topic aware modification, in which the network is modelled as a graph where the edge of any two users is associated with a topic distribution. The focus of this thesis is given on the development of a novel framework to deal with the topic aware influence maximization problem. The framework succeeds to turn classical topic blind influence maximization algorithms into topic aware by using an established link analysis algorithm. In addition, algorithms developed in Neo4j (i.e., a modern graph database) following the proposed novel framework. The remainder of this thesis is arranged as follows: Chapter 2 describes the research background of the influence maximization problem and a literature review of the most significant studies. Chapter 3 introduces the Hyperlink Induced Topic Search (HITS) algorithm, which used for analyzing links and rating nodes by comparing edges pointing in and out of them in a graph. Chapter 4 addresses the influence maximization problem and the proposed novel framework is presented and its components are thoroughly explained. Chapter 5 presents in detail the conducted experiments and analyses the derived results. X. Kitsios 6
17 Chapter 6 provides an overall synopsis of conclusions and directions of future research. X. Kitsios 7
18 2. INFLUENCE MAXIMIZATION PROBLEM 2. Definition The influence maximization problem aims to find a subset of nodes in a network such that the resulting influence propagating from that subset reaches the largest number of nodes in the network. The influence could represent information, behavior, disease, product adoption, traffic etc., that can pass across edges of connected peers within a network. Definition 2.. (Influence maximization problem). Given a network G(V, E) with V vertices (also called nodes), E edges, and a number k, where k < V, find a set S of k nodes that the expected spread of influence is maximized. The influence maximization problem is a NP hard problem and for this reason significant ( ) n computational effort is required. For example, a network of.000 nodes has k different possible candidates of size k = 5 seed set, which is impossible to be solved exactly even using state of the art computing resources of high performance. 2.2 Literature Review The first algorithmic treatment of the problem is provided by Domingos and Richardson [] [2], who modelled the diffusion process in term of Markov random fields and proposed heuristic solutions to the problem. Kempe et al. [3] study the influence maximization problem as a discrete optimization problem focusing on two propagation models, the Independent Cascade, and the Linear Threshold. In both models, at a given timestamp, each node is either active or inactive. Each node s tendency to become active increases monotonically as more of its neighbor becomes active. An active node never becomes inactive again. In the Independent Cascade model when a node υ first becomes active, say at time t, it is considered contagious. It has one chance of influence each inactive neighbor u with probability p (υ,u), independently of the history so far. If the tentative succeeds, u becomes active at time t +. Independent Cascade model is presented in Algorithm 2.. X. Kitsios 8
19 Algorithm 2. Independent Cascade model : procedure IndependentCascade(G(V, E), Φ(t 0 ), p) 2: i 0 i represents the current round 3: while Φ(t i ) do As long as a new node activates 4: i i + 5: Φ(t i ) 6: for all υ Φ(t i ) do Nodes activated in previous round 7: for all u Nυ V do Neighbors of activated node 8: if u / i j=0φ(t j ) then Neighbor must be inactive 9: if rand(0, ) < p (υ,u) then A chance to get active 0: Φ(t i ) Φ(t i ) {u} Neighbor becomes active : end if 2: end if 3: end for 4: end for 5: end while 6: return i j=0φ(t j ) Return the activated nodes of all rounds 7: end procedure In the Linear Threshold model, each node u is influenced by each neighbor υ according to a weight b (υ,u), so that the sum of incoming weights to u is less than or equal to. Each node u chooses a threshold θ u uniformly at random in the [0, ] range. At any timestamp t, if the total weight from the active neighbors of an inactive node u is at least θ u, then u becomes active at timestamp t +. Linear Threshold model is presented in Algorithm 2.2. X. Kitsios 9
20 Algorithm 2.2 Linear Threshold model : procedure LinearT hreshold(g(v, E), Φ(t 0 ), b) 2: for all υ V do 3: θ υ rand(0, ) Set random thresholds 4: end for 5: i 0 i represents the current round 6: while i = 0 or Φ(t i ) Φ(t i ) do As long as a new node activates 7: Φ(t i+ ) Φ(t i ) 8: for all υ V \Φ(t i ) do Inactive nodes b (υ,u) θ υ then A chance to get active 9: if u N Φ(t i ) υ 0: Φ(t i+ ) Φ(t i+ ) {u} Node becomes active : end if 2: end for 3: i i + 4: end while 5: return Φ(t i ) Return the activated nodes 6: end procedure Both Independent Cascade and Linear Threshold models are repeated until there is not any new node to become active. In the Independent Cascade model, the influencer becomes more important, since s/he holds a probability. This is one of the major differences between the two models since that in Linear Threshold model the influence parameter is assigned to the nodes randomly. The algorithm introduced by Kempe et al. [3] is known as Greedy. Greedy algorithm successively selects the node that maximize the marginal gain and provides an approximation of the optimum solution within a factor of ( /e). This is due to the nice properties of monotonicity and submodularity that the spread function exhibits under these models. Given a propagation model m and a seed set S, where S V, the expected number of active nodes at the end of process is denoted by σ m (S). The influence maximization problem requires to find the set S V, S = k, such that σ m (S) is maximum. Monotonicity indicates that as more neighbors of some arbitrary node gets active, the probability of u to become active increases (i.e. σ m (S) σ m (T ) whenever S T ). Submodularity indicates that the marginal gain of a new node shrinks as the set grows (i.e. σ m (S {u}) σ m (S) σ m (T {u}) σ m (T ) whenever S T ). In their paper [3], Kempe et al. run Monte Carlo simulations to obtain an accurate estimation of the expected spread. In particularly, they show that for any ε > 0, there is a γ > 0 such that by using ( + γ) approximate values of expected spread a ( /e ε) approximation for the influence maximization problem is obtained. There are two major limitations in Greedy algorithm: X. Kitsios 20
21 . The algorithm requires repeated computations of the spread function for various set of seed. The problem of computing the spread under Independent Cascade and Linear Threshold models is #P hard. As a result, Monte Carlo simulations are run for sufficiently times to obtain an accurate estimation which result in long computation time. 2. In each iteration, the algorithm searches all the nodes in the graph as a potential candidate for the next seed node. As a result, this algorithm entails a quadratic number of steps in terms of the number of nodes. Greedy algorithm is presented in Algorithm 2.3. Algorithm 2.3 Greedy algorithm : procedure Greedy(G(V, E), k, w, simulations) 2: S 3: for i = to k do 4: for all u V \S do Calculate the spread for all not selected nodes 5: s u 0 6: for j = to simulations do 7: s u s u + Inf(S {u}) 8: end for 9: s u s u /simulations 0: end for : S S {arg max u V \S {s u }} Select the node that maximize the spread 2: end for 3: return S 4: end procedure Leskovec et al. [4] introduced an efficient algorithm called Cost Effective Lazy Forward (CELF). In CELF algorithm the submodularity is exploited based on a Lazy Forward optimization approach by selecting new nodes. The idea is that the marginal gain of a node in the current iteration cannot be better than its marginal gain in previous iterations. CELF algorithm maintains a table u, u (S) sorted on u (S) decreasing order, where S is the current seed and u (S) is re evaluated only for the top node at a time and if it is needed, the table is resorted. If a node remains at the top, it is picked in the next seed. Empirical experiments show that the CELF algorithm dramatically improves the efficiency, being 700 times faster than the Greedy algorithm. It is worth to mention that the Greedy algorithm proposes ( /e ε) optimal solutions and CELF algorithm proposes /2( /e) optimal solutions. CELF algorithm is presented in Algorithm 2.4. X. Kitsios 2
22 Algorithm 2.4 CELF algorithm : procedure CELF(G(V, E), k, w, simulations) 2: S 3: for i = to k do 4: for all u V \S do Calculate the spread for all not selected nodes 5: if s r u < s r u then If top node spread is higher than others, continue 6: continue 7: end if 8: s u 0 9: for j = to simulations do 0: s u s u + Inf(S {u}) : end for 2: s u s u /simulations 3: end for 4: S S {arg max u V \S {s u }} Select the node that maximize the spread 5: end for 6: return S 7: end procedure Goyal et al. [5] propose the CELF++ algorithm which constitutes a highly optimized approach based on the CELF algorithm to further improve the naive Greedy algorithm. CELF++ algorithm exploits the property of submodularity of the spread function for influence propagation models to avoid unnecessary recomputations of gains incurred by CELF algorithm. Empirical experiments show that CELF++ algorithm works effectively and efficiently, resulting in significant improvements in terms of both running time and the average number of node look ups. Several techniques [4, 5] are proposed to optimize the Greedy algorithm [3]. Moreover, researchers have started to search new ways of maximizing the spread of influence [6, 7, 8, 9]. Some of these new ways focus on topic aware influence maximization problem [7, 9]. Saito et al. [6] study how to learn the probabilities for the Independent Cascade model from a set of past propagations. They formally define the likelihood maximization problem and then apply the Expectation Maximization algorithm to solve it. Even though the proposed formulation is elegant, it is not scalable to voluminous datasets for the reason that in each iteration the Expectation Maximization algorithm must update the influence probability associated to each edge. Tang et al. [7] are among the first that studied the problem of influence maximization based on a topic. Given a network and a topic distribution for each node, the aim to find topic specific subnetworks, and topic specific influence weights among subnetworks. They introduce the Topical Affinity Propagation approach using a graphical probabilistic model. Moreover, Tang et al. deal with the efficiency by devising a distributed learning algorithm under the MapReduce model. The focus of their work is the expert finding problem without X. Kitsios 22
23 proposing any propagation model or studying the influence maximization problem. Most of the works assume a weighted graph as input and do not address how the edge probabilities (or influence weights) can be obtained. Goyal et al. [8] study this problem an instance of General Threshold model. They extend this model by introducing temporal decay, as well as factors such as the influenceability of a specific user and influenceproneness of a certain action. The interesting fact about their work is that they manage to predict whether a user will perform an action and when. Barbieri et al. [9] extent the Independent Cascade model to be topic aware. The model of this work named Topic aware Independent Cascade. The relationship strength between two nodes is computed by their topic preference learned from history activities on a social network. In their experiments show that topic aware influence propagation models are more accurate in describing real world influence driven propagations than the state ofthe art topic blind models and considering the characteristics of the item, many adoptions can be obtained in the influence maximization problem. This thesis utilizes the Greedy and CELF algorithms as well as the Independent Cascade model in order to develop a novel framework that deals with the topic aware influence maximization problem. X. Kitsios 23
24 3. HYPERLINK INDUCED TOPIC SEARCH (HITS) ALGORITHM 3. Definition Kleinberg [0] developed the Hyperlink Induced Topic Search (HITS) algorithm for analyzing the links in a network. The HITS algorithm has been successfully applied in rating websites and scientific journals. HITS algorithm defines a hubscore and an authorityscore for each node. The authorityscore estimates the value of the node and the hubscore estimates the value of its links to other nodes. The idea stemmed from a particular insight into the creation of web pages when the internet was originally forming. Certain web pages, known as hubs, served as large directories that were not actually authoritative in the information that they held, but were used as compilations of a broad catalog of information that led users direct to other authoritative pages. The steps of the algorithm are:. Set for each node the hubscore = and the authorityscore =. 2. Choose a number of k steps. 3. In each step, perform a sequence of updates. Each update works as follows: First apply the Authority Update Rule. Then apply the Hub Update Rule. 4. Normalize hubscore and authorityscore to their relative sizes; divide down each authorityscore by the sum of all authorityscore and divide down each hubscore by the sum of all hubscore. Definition 3.. (Authority update rule). For each node, update authorityscore to be the sum of the hubscore of all nodes that points to the node. Definition 3..2 (Hub update rule). For each node, update hubscore to be the sum of the authorityscore of all nodes that the node points to. 3.2 Example In the following example [], the results of the query newspapers that are retrieved from the web are examined. Figure 3. shows the results. Query returns websites relevant to newspapers, like USA Today, New York Time, Wall St. Journal, SJ Merc News, and popular websites, like Amazon, Yahoo!, Facebook. The unnamed nodes represent the sample of websites relevant to query. X. Kitsios 24
25 Name: SJ Merc News Name: Wall St. Journal Name: New York Times Name: USA Today Name: Facebook Name: Yahoo! Name: Amazon Figure 3.: HITS algorithm example Results of the query newspapers X. Kitsios 25
26 In Figure 3.2 all hubscore and authorityscore are set equal to. Moreover, in this example two sequence of updates are going to be performed; so the number of steps k is set 2. authscore: authscore: Name: SJ Merc News authscore: authscore: Name: Wall St. Journal authscore: authscore: Name: New York Times authscore: authscore: Name: USA Today authscore: authscore: Name: Facebook authscore: authscore: Name: Yahoo! authscore: authscore: Name: Amazon authscore: authscore: Figure 3.2: HITS algorithm example Setting all hubscore = and authorityscore = X. Kitsios 26
27 In Figure 3.3, the authority update rule for step is shown. For each node, authorityscore is updated to be the sum of the hubscore of all nodes that point to the node. Nodes on the left have authorityscore = 0 due to no incoming edges. Moreover, the authorityscore of the websites relevant to newspaper is relative increased. Name: SJ Merc News authorityscore: 2 Name: Wall St. Journal authorityscore: 2 Name: New York Times authorityscore: 4 Name: USA Today authorityscore: 3 Name: Facebook authorityscore: Name: Yahoo! authorityscore: 3 Name: Amazon authorityscore: 3 Figure 3.3: HITS algorithm example Applying authority update rule for step X. Kitsios 27
28 In Figure 3.4, the hub update rule for step is shown. For each node, hubscore is updated to be the sum of the authorityscore for all nodes that the node points to. The set of nodes on the right have hubscore = 0 due to no outgoing edges. Moreover, it is important to mention that websites that point to websites relevant to newspaper have higher hubscore. hubscore: 8 Name: SJ Merc News hubscore: 0 authorityscore: 2 hubscore: 7 Name: Wall St. Journal hubscore: 0 authorityscore: 2 hubscore: 6 Name: New York Times hubscore: 0 authorityscore: 4 hubscore: 5 Name: USA Today hubscore: 0 authorityscore: 3 hubscore: 3 Name: Facebook hubscore: 0 authorityscore: hubscore: 6 Name: Yahoo! hubscore: 0 authorityscore: 3 hubscore: 3 Name: Amazon hubscore: 0 authorityscore: 3 hubscore: 3 Figure 3.4: HITS algorithm example Applying hub update rule for step X. Kitsios 28
29 In Figure 3.5, the authority update rule for step 2 is shown. s relevant to newspaper have the highest authorityscore. That is, the authorityscore will tend to be increased as more hub and authority updates occurs in the following steps. hubscore: 8 Name: SJ Merc News hubscore: 0 authorityscore: 9 hubscore: 7 Name: Wall St. Journal hubscore: 0 authorityscore: 9 hubscore: 6 Name: New York Times hubscore: 0 authorityscore: 3 hubscore: 5 Name: USA Today hubscore: 0 authorityscore: 24 hubscore: 3 Name: Facebook hubscore: 0 authorityscore: 5 hubscore: 6 Name: Yahoo! hubscore: 0 authorityscore: 5 hubscore: 3 Name: Amazon hubscore: 0 authorityscore: 2 hubscore: 3 Figure 3.5: HITS algorithm example Applying authority update rule for step 2 X. Kitsios 29
30 In Figure 3.6, the hub update rule for step 2 is shown. s that point only to websites relevant to newspaper tend to have increased hubscore. That is, the hubscore will tend to be increased as more hub and authority updates occurs in the following steps. hubscore: 38 hubscore: 93 Name: SJ Merc News hubscore: 0 authorityscore: 9 hubscore: 55 Name: Wall St. Journal hubscore: 0 authorityscore: 9 hubscore: 39 Name: New York Times hubscore: 0 authorityscore: 3 hubscore: 36 Name: USA Today hubscore: 0 authorityscore: 24 5 Name: Facebook hubscore: 0 authorityscore: 5 hubscore: 27 Name: Yahoo! hubscore: 0 authorityscore: 5 2 Name: Amazon hubscore: 0 authorityscore: 2 2 Figure 3.6: HITS algorithm example Applying hub update rule for step 2 X. Kitsios 30
31 In Figure 3.7, the authorityscore and the hubscore are normalized by dividing down each authorityscore by the sum of all authorityscore and divide down each hubscore by the sum of all hubscore. hubscore: 0,6 hubscore: 0,284 Name: SJ Merc News hubscore: 0,52 hubscore: 0,68 Name: Wall St. Journal hubscore: 0,52 hubscore: 0,9 Name: New York Times hubscore: 0,248 hubscore: 0,0 Name: USA Today hubscore: 0,92 hubscore: 0,046 Name: Facebook hubscore: 0,040 hubscore: 0,083 Name: Yahoo! hubscore: 0,20 hubscore: 0,037 Name: Amazon hubscore: 0,096 hubscore: 0,037 Figure 3.7: HITS algorithm example Normalizing authorityscore and hubscore X. Kitsios 3
32 4. TOPIC AWARE INFLUENCE MAXIMIZATION FRAMEWORK 4. Definition The proposed novel framework consists of two main components in order to improve the results of the social influence according to a topic. This is achieved by using a HITS algorithm, which aims to analyze links, and a Greedy or a CELF algorithm with modified Independent Cascade model in order to find k nodes that maximize the expected spread of influence in a network. Using the link analysis results of HITS algorithm, the main goal is to highlight the appropriate nodes for a topic that is examined. Aiming to calculate the influence maximization spread that takes into account the HITS scores a modified Independent Cascade model is used. The modification also considers the chance to influence a node by the hubscore which is given as input. The Algorithm 2. presents the Independent Cascade model, where a node considers only one chance of influencing each inactive neighbour with probability p (υ). Thus, the probability is going to be multiplied by the hubscore (υ,u) in order to take advantage of the HITS algorithm. Since the HITS algorithm scores are normalized p hubscore <. Below is the change made to the Independent Cascade model. 9: if rand(0, ) < p (υ,u) hubscore (υ) then Previously: rand(0, ) < p (υ,u) 0: Φ(t i ) Φ(t i ) {u} : end if The hubscore expresses the value of links of the node and the authorityscore expresses the value of the node. The hubscore is ideal to be used since the goal is to highlight the nodes. In case there is no hubscore for the node an assumption is made that the hubscore is equal to zero. In Figures 4. and 4.2 red nodes are inactive, green are active and all p (υ,u) =. In Figure 4. the chance Alice to influence Bob is 0, 40. Alice has high hubscore after the link analysis on the topic and she is benefited. Name: Alice hubscore: 0,40 Name:... hubscore:... p: p: Name: Bob hubscore: 0,0 Name:... hubscore:... p: Figure 4.: Example /2 of using hubscore into influence maximization process X. Kitsios 32
33 On the other hand, in Figure 4.2 the chance Bob to influence other nodes is 0, 0. Bob has low hubscore after the link analysis on the topic and he is not benefited. In practice, Alice is master on choosing restaurants because she reviews restaurants with high authorityscore and her friends trust her more than Bob. Name: Alice hubscore: 0,40 Name:... hubscore:... p: p: Name: Bob hubscore: 0,0 Name:... hubscore:... p: Figure 4.2: Example 2/2 of using hubscore into influence maximization process Since Bob may or may not likes restaurants the variable p (υ,u) should remain. In addition, a use of universal probability based on widely accepted facts is recommended. Facts like, most of people like restaurants so all p (υ,u) should be increased, a specific cuisine is less likely to be liked so all p (υ,u) should be lowered, etc. The framework involves the following steps:. Create a projected graph G for a topic, from the initial graph G, using the necessary nodes and edges needed to apply HITS algorithm. 2. Apply HITS algorithm on G and store HITS algorithm results on G. 3. Create a projected graph G, from the initial graph G, using the necessary nodes and edges needed to apply either Greedy or CELF algorithm. 4. Apply either Greedy or CELF algorithm with the modified Independent Cascade model on G and store influence maximization results on G. 4.2 Example Figures 4.3, 4.4, 4.5 and 4.6 represents the initial graph G of the example. There are three types of nodes,, Business and Category, and there are three types of edges,, and IN_CATEGORY. X. Kitsios 33
34 In Figure 4.3, the initial network is presented. Name: Korova Name: George Name: Anna Category Name: Bars IN_CATEGORY IN_CATEGORY Business Business Name: Au Grand Zinc Name: Stevie Name: Natasha Name: Lydia Name: Alice Name: Shopping IN_CATEGORY Name: Bookstore Politeia Business Category IN_CATEGORY Name: GRobotronics Name: Martha Name: Joy Business Figure 4.3: Topic aware influence maximization framework example The initial network In Figure 4.4, edges of the initial network are presented. Name: George Name: Anna Name: Stevie Name: Natasha Name: Lydia Name: Alice Name: Martha Name: Joy Figure 4.4: Topic aware influence maximization framework example edges of the initial network X. Kitsios 34
35 In Figure 4.5, edges of the initial network are presented. Name: Korova Name: George Name: Anna Business Name: Au Grand Zinc Business Name: Stevie Name: Natasha Name: Lydia Name: Alice Name: Bookstore Politeia Business Name: GRobotronics Name: Martha Name: Joy Business Figure 4.5: Topic aware influence maximization framework example edges of the initial network In Figure 4.6, IN_CATEGORY edges of the initial network are presented. Name: Korova Category Name: Bars IN_CATEGORY IN_CATEGORY Business Name: Au Grand Zinc Business Name: Bookstore Politeia Category Name: Shopping IN_CATEGORY IN_CATEGORY Business Name: GRobotronics Business Figure 4.6: Topic aware influence maximization framework example IN_CATEGORY edges of the initial network The topics for this network are expressed by Category nodes, i.e., Bars or Shopping. X. Kitsios 35
36 The goal is to find the users that can spread the most for each topic. Based on the graph and what represents, there will be a feature that expresses the topic Create a Projected Graph to Apply HITS Algorithm To apply HITS algorithm, the and Business nodes are required. The edges connect these two types of nodes. Since the goal is to maximize the spread based on a topic, it is needed to make a projected graph with and Business nodes, and edges by filtering on each Category node. Figure 4.7 shows the projection by filtering on category Bars. Using this projection, the HITS algorithm is executed to calculate the hubscore and authorityscore. Name: Korova Name: George Name: Anna Business Name: Au Grand Zinc Business Name: Stevie Name: Natasha Name: Lydia Name: Alice Name: Martha Name: Joy Figure 4.7: Topic aware influence maximization framework example Projected graph for topic Bars Figure 4.8 shows the projection by filtering on category Shopping. Using this projection, the HITS algorithm is executed to calculate the hubscore and authorityscore. X. Kitsios 36
37 Name: George Name: Anna Name: Stevie Name: Natasha Name: Lydia Name: Alice Business Name: Bookstore Politeia Name: GRobotronics Name: Martha Name: Joy Business Figure 4.8: Topic aware influence maximization framework example Projected graph for topic Shopping Apply HITS Algorithm The 2nd step includes the execution of the HITS algorithm. Tables 4. and 4.2 show the results of hubscore and authorityscore. Table 4.: Topic aware influence maximization framework example HITS algorithm results for topic Bars Name Type hubscore authorityscore Alice 0,00 0,00 Anna 0,00 0,00 George 0,50 0,00 Joy 0,00 0,00 Lydia 0,50 0,00 Martha 0,00 0,00 Natasha 0,50 0,00 Stevie 0,50 0,00 Au Grand Zinc Business 0, Korova Business 0, X. Kitsios 37
38 Table 4.2: Topic aware influence maximization framework example HITS algorithm results for topic Shopping Name Type hubscore authorityscore Alice ,00 Anna 0,00 0,00 George 0,00 0,00 Joy 0.5 0,00 Lydia 0,5 0,00 Martha 0.5 0,00 Natasha 0,50 0,00 Stevie 0,27 0,00 Bookstore Politeia Business 0, GRobotronics Business 0, Create a Projected Graph to Apply Greedy or CELF Algorithm Figure 4.4 shows edges among nodes. Using this projection an influence maximization algorithm, either Greedy or CELF, is executed to calculate the influence spread. Either Greedy or CELF algorithm should run, in this case, between users and their friendship relation Apply Greedy or CELF Algorithm In the final step of topic aware influence maximization framework, the hubscore from a previous step is considered as input parameter of Greedy or CELF algorithms. Tables 4.3 and 4.4 show the results of the spread for the topics. Table 4.3: Topic aware influence maximization framework example Influence maximization results for topic Bars Name Spread Natasha,50 George 2,290 Lydia 3,330 Stevie 4,330 Anna 5,330 Joy 6,330 Martha 7,330 Alice 8,330 X. Kitsios 38
39 Table 4.4: Topic aware influence maximization framework example Influence maximization results for topic Shopping Name Spread Joy,200 Natasha 2,300 Lydia 3,340 Stevie 4,336 George 5,360 Anna 6,360 Martha 7,360 Alice 8,360 In addition, a topic blind influence maximization is executed in order to compare the topic results with the topic blind results. Table 4.5 shows the results of the spread for a topicblind. Table 4.5: Topic aware influence maximization framework example Influence maximization results on topic blind Name Spread George,747 Natasha 2,937 Anna 4,036 Joy 5,6 Lydia 6,96 Stevie 7,96 Martha 8,96 Alice 9,96 Based on the derived results, is observed the top nodes differs for each category and topic blind case. X. Kitsios 39
40 5. EXPERIMENTS 5. Software A graph database, specifically the Neo4j graph database (Subsection 5..), was used as a platform for the empirical experiments. For the needs of thesis, Greedy and CELF algorithms were implemented for Neo4j. Those implementations have been contributed to the Neo4j open source community and released in version.6 of the GDS library (Subsection 5..2). Graph databases belong to NoSQL database based on graph theory that addresses the limitations of relational databases. Those database uses graph structures for semantic queries with nodes, edges, and properties to represent and store data. The graph, as the key concept of the system, relates the data items to a collection of nodes and edges. Graph databases portray the data conceptually by transferring the data into nodes and its relationships into edges. Graph databases have become especially popular nowadays with the growth of the needs of social networks and the needs of analyzing complex networks. Some of the well known such databases are Neo4j, ArangoDB, Dgraph, OrientDB, etc. 5.. Neo4j Neo4j is the most popular graph database management system. The community edition is licensed under the free GNU General Public License v3 while the enterprise edition is licensed under a Neo4j commercial license. The Neo4j is an ACID compliant transactional database with native graph storage and processing. In Neo4j everything is stored in the form of node, edge, and property. Each node and edge can have any number of properties. Both nodes and edges can be labelled. Labels can be used to narrow searches. Neo4j supports indexes. Cypher declarative query language, used in Neo4j, allows expressive and efficient data querying. The language is designed with the power and capability of SQL in mind, but Cypher is based on the components and needs of a database built upon the concepts of graph theory Graph Data Science (GDS) Library Graph Data Science (GDS) library uses the graph database and provides many algorithms. Graph algorithms are used to compute metrics for graphs, nodes, or relationships. They can provide insights on relevant entities in a graph (centralities, ranking), or inherent structures like communities (community detection, graph partitioning, clustering). Their X. Kitsios 40
41 algorithms are efficiently implemented and parallel. To run the algorithms as efficiently as possible, the GDS library uses a specialized in memory graph format to represent the graph data. It is therefore necessary to load the graph data from the Neo4j database into an in memory graph catalogue. The amount of data loaded can be controlled by so called graph projections, which also allow, for example, filtering on node labels and relationship types, among other options. Figure 5. shows the standard operations of the GDS library. Figure 5.: GDS library Standard operations 5.2 Data Sources For the experiments, two type of data source are used. Generated graphs, based on the Barabási Albert model (Subsection 5.2.), were used to evaluate the performance of the algorithms and the Yelp dataset (Subsection 5.2.2) was used to evaluate the proposed framework Barabási Albert Model The Barabási Albert model [2] is an algorithm for generating random scale free networks using a preferential attachment mechanism. The algorithm is introduced by Albert László Barabási and Réka Albert. Many observed networks fall into the class of scale free networks, meaning that they have power law degree distributions, while random graph models do not exhibit power laws. The Barabási Albert model is one of the several proposed models that generate scale free networks. It incorporates two important general concepts: Growth means that the number of nodes in the network increases over time. X. Kitsios 4
42 Preferential attachment means that the more connected a node is, the more likely is to receive new links. Both growth and preferential attachment exist widely in real networks. Awesome Procedures on Cypher (APOC) library is a Neo4j library that includes a procedure to generate a random graph according to the Barabási Albert model. Figure 5.2 represents the schema that is used for the experiments. Figure 5.2: Barabási Albert model Schema used in topic blind experiments Yelp Dataset Yelp s website, yelp.com, is a crowd sourced local business review and social networking website. The website includes pages devoted to individual locations, such as restaurants, schools, etc., where Yelp users can submit a review of their products or services using a one tofive star rating system. In addition to writing reviews, users can react to reviews, etc. The Yelp dataset is a subset of Yelp businesses, reviews, and user data for use in personal, educational, and academic purposes. Figure 5.3 represents the schema of Yelp dataset that is used for the experiments. Table 5. shows the number of each label of nodes and edges. Person Business IN_CATEGORY Category Figure 5.3: Yelp dataset Schema used in topic aware experiments Table 5.: Yelp dataset Number of nodes/edges per type Type Number of nodes/edges Business Category REVIEW IN_CATEGORY X. Kitsios 42
43 5.3 Performance Experiments on Greedy and CELF Algorithms In this section, the performance of the implementations that contributed in Neo4j community is examined. Besides testing, behavior of each algorithm is also observed. All experiments were conducted in generated graphs, via Neo4j APOC library, based on Barabási Albert model. The experiments were conducted in a personal computer (Windows 0, Intel i7 4 cores, 6GB ram) using Neo4j enterprise v4.3., APOC v and GDS v.6.. In Appendix A, tables with the settings of parameters and the running times of all experiments are listed Greedy/CELF Algorithms Experiment In this experiment the advantage of CELF algorithm that uses the Lazy Forward feature is observed. Figure 5.4 shows that the running time of Greedy algorithm escalates, as expected, much faster than CELF algorithm running time. Running time in s Greedy thread CELF thread Number of nodes Figure 5.4: Performance experiment Greedy/CELF algorithms Multithreads In the same experiment it is worth to compare, in Figures 5.5, 5.6, and 5.7, the multithreading implementations. Threading the function of the Independent Cascade model offers advantage to the Greedy algorithm. On the other hand, due to Lazy Forward feature, the CELF algorithm uses the Independent Cascade model much lower times, and threads do not offer any significant advantage. X. Kitsios 43
44 Running time in s Greedy thread Greedy 4 threads Number of nodes Figure 5.5: Performance experiment Greedy algorithm multithreads Running time in s CELF thread CELF 4 threads Number of nodes Figure 5.6: Performance experiment CELF algorithm multithreads X. Kitsios 44
45 Running time in s Greedy 4 thread CELF 4 threads Number of nodes Figure 5.7: Performance experiment Greedy/CELF algorithms multithreads Large Scale Networks Experiment In this experiment, in Figure 5.8, the behavior in large scale networks is tested. For instance, in a large scale network with nodes and edges, Greedy algorithm needs almost 4 hours to be executed and CELF algorithm about hour and 30 minutes. Therefore, CELF algorithm should be preferred in large scale networks Greedy 4 threads CELF 4 threads Running time in s Number of nodes Figure 5.8: Performance experiment Number of nodes X. Kitsios 45
46 5.3.3 Seed Set Size Experiment In this experiment the impact of requesting a large seed set is observed. Once again, CELF algorithm is not affected because in Lazy Forward implementation the use of the Independent Cascade mode is minimal. Figure 5.9 shows that Greedy algorithm escalate as the seed set increases. Running time in s Greedy thread CELF 4 thread Greedy 4 threads CELF 4 threads Seed set size Figure 5.9: Performance experiment Seed set size Monte Carlo Simulations Experiment In this experiment, in Figures 5.0 and 5., the impact of running large number of Monte Carlo simulations is tested. As the number of simulations increased it is logical the running time to increases. Moreover, it is observed the need of multithreads which reduces significantly the running time. X. Kitsios 46
47 Running time in s Greedy thread CELF thread Greedy 4 threads CELF 4 threads Monte Carlo simulations Figure 5.0: Performance experiment Monte Carlo simulations (part /2) Running time in s Greedy thread CELF thread Greedy 4 threads CELF 4 threads Monte Carlo simulations Figure 5.: Performance experiment Monte Carlo simulations (part 2/2) Table 5.2 shows how the spread differences among various Monte Carlo simulations. As the number of simulations increases, the spread also tents to increases. Since this is not a significant gap the overall spread could be considered as stable. X. Kitsios 47
48 Table 5.2: Performance experiment Spread with various number of Monte Carlo simulations Monte Carlo st Node 2nd Node 3nd Node simulations spread spread spread , , , , , , , , , , , , , , , , ,9 4.64, , , , ,49 4.0, , , , , , , , , , , , , , , ,8 4.45, , ,2 4.4, Propagation Probability Experiment In this experiment, in Figure 5.2, the impact of propagation probability is observed. As the propagation probability increases, more nodes tend to become active and therefore the algorithm needs more time to examine the increased active nodes. Running time in s Greedy threads CELF threads Greedy 4 threads CELF 4 threads 0 0, 0,2 0,3 0,4 0,5 0,6 0,7 0,8 0,9 Propagation probability Figure 5.2: Performance experiment Propagation probability X. Kitsios 48
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΠΟΛΥΤΕΧΝΙΚΗ ΣΧΟΛΗ ΤΜΗΜΑ ΜΗΧΑΝΙΚΩΝ Η/Υ & ΠΛΗΡΟΦΟΡΙΚΗΣ. του Γεράσιμου Τουλιάτου ΑΜ: 697
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΠΟΛΥΤΕΧΝΙΚΗ ΣΧΟΛΗ ΤΜΗΜΑ ΜΗΧΑΝΙΚΩΝ Η/Υ & ΠΛΗΡΟΦΟΡΙΚΗΣ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ ΣΤΑ ΠΛΑΙΣΙΑ ΤΟΥ ΜΕΤΑΠΤΥΧΙΑΚΟΥ ΔΙΠΛΩΜΑΤΟΣ ΕΙΔΙΚΕΥΣΗΣ ΕΠΙΣΤΗΜΗ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑ ΤΩΝ ΥΠΟΛΟΓΙΣΤΩΝ του Γεράσιμου Τουλιάτου
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΠΟΛΥΤΕΧΝΙΚΗ ΣΧΟΛΗ ΤΜΗΜΑ ΜΗΧΑΝΙΚΩΝ Η/Υ & ΠΛΗΡΟΦΟΡΙΚΗΣ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ ΣΤΑ ΠΛΑΙΣΙΑ ΤΟΥ ΜΕΤΑΠΤΥΧΙΑΚΟΥ ΔΙΠΛΩΜΑΤΟΣ ΕΙΔΙΚΕΥΣΗΣ ΕΠΙΣΤΗΜΗ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑ ΤΩΝ ΥΠΟΛΟΓΙΣΤΩΝ του Γεράσιμου Τουλιάτου
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Απόκριση σε Μοναδιαία Ωστική Δύναμη (Unit Impulse) Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο. Απόστολος Σ.
 Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ. Υποβάλλεται στην
 ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Η ΨΥΧΙΑΤΡΙΚΗ - ΨΥΧΟΛΟΓΙΚΗ ΠΡΑΓΜΑΤΟΓΝΩΜΟΣΥΝΗ ΣΤΗΝ ΠΟΙΝΙΚΗ ΔΙΚΗ
 ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ ΝΟΜΙΚΗ ΣΧΟΛΗ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΤΟΜΕΑΣ ΙΣΤΟΡΙΑΣ ΦΙΛΟΣΟΦΙΑΣ ΚΑΙ ΚΟΙΝΩΝΙΟΛΟΓΙΑΣ ΤΟΥ ΔΙΚΑΙΟΥ Διπλωματική εργασία στο μάθημα «ΚΟΙΝΩΝΙΟΛΟΓΙΑ ΤΟΥ ΔΙΚΑΙΟΥ»
ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ ΝΟΜΙΚΗ ΣΧΟΛΗ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΤΟΜΕΑΣ ΙΣΤΟΡΙΑΣ ΦΙΛΟΣΟΦΙΑΣ ΚΑΙ ΚΟΙΝΩΝΙΟΛΟΓΙΑΣ ΤΟΥ ΔΙΚΑΙΟΥ Διπλωματική εργασία στο μάθημα «ΚΟΙΝΩΝΙΟΛΟΓΙΑ ΤΟΥ ΔΙΚΑΙΟΥ»
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
ΠΑΡΑΜΕΤΡΟΙ ΕΠΗΡΕΑΣΜΟΥ ΤΗΣ ΑΝΑΓΝΩΣΗΣ- ΑΠΟΚΩΔΙΚΟΠΟΙΗΣΗΣ ΤΗΣ BRAILLE ΑΠΟ ΑΤΟΜΑ ΜΕ ΤΥΦΛΩΣΗ
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΜΑΚΕΔΟΝΙΑΣ ΟΙΚΟΝΟΜΙΚΩΝ ΚΑΙ ΚΟΙΝΩΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΕΚΠΑΙΔΕΥΤΙΚΗΣ ΚΑΙ ΚΟΙΝΩΝΙΚΗΣ ΠΟΛΙΤΙΚΗΣ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΠΑΡΑΜΕΤΡΟΙ ΕΠΗΡΕΑΣΜΟΥ ΤΗΣ ΑΝΑΓΝΩΣΗΣ- ΑΠΟΚΩΔΙΚΟΠΟΙΗΣΗΣ ΤΗΣ BRAILLE
ΠΑΝΕΠΙΣΤΗΜΙΟ ΜΑΚΕΔΟΝΙΑΣ ΟΙΚΟΝΟΜΙΚΩΝ ΚΑΙ ΚΟΙΝΩΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΕΚΠΑΙΔΕΥΤΙΚΗΣ ΚΑΙ ΚΟΙΝΩΝΙΚΗΣ ΠΟΛΙΤΙΚΗΣ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΠΑΡΑΜΕΤΡΟΙ ΕΠΗΡΕΑΣΜΟΥ ΤΗΣ ΑΝΑΓΝΩΣΗΣ- ΑΠΟΚΩΔΙΚΟΠΟΙΗΣΗΣ ΤΗΣ BRAILLE
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Second Order RLC Filters
 ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
«Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων. Η μεταξύ τους σχέση και εξέλιξη.»
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Potential Dividers. 46 minutes. 46 marks. Page 1 of 11
 Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
department listing department name αχχουντσ ϕανε βαλικτ δδσϕηασδδη σδηφγ ασκϕηλκ τεχηνιχαλ αλαν ϕουν διξ τεχηνιχαλ ϕοην µαριανι
 She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Fractional Colorings and Zykov Products of graphs
 Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
NATIONAL AND KAPODISTRIAN UNIVERSITY OF ATHENS SCHOOL OF SCIENCE FACULTY OF INFORMATICS AND TELECOMMUNICATIONS
 NATIONAL AND KAPODISTRIAN UNIVERSITY OF ATHENS SCHOOL OF SCIENCE FACULTY OF INFORMATICS AND TELECOMMUNICATIONS INTERDICIPLINARY POSTGRADUATE PROGRAMME "INFORMATION TECHNOLOGIES IN MEDICINE AND BIOLOGY"
NATIONAL AND KAPODISTRIAN UNIVERSITY OF ATHENS SCHOOL OF SCIENCE FACULTY OF INFORMATICS AND TELECOMMUNICATIONS INTERDICIPLINARY POSTGRADUATE PROGRAMME "INFORMATION TECHNOLOGIES IN MEDICINE AND BIOLOGY"
Problem Set 3: Solutions
 CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Γιπλυμαηική Δπγαζία. «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ. Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο
 ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΒΑΛΕΝΤΙΝΑ ΠΑΠΑΔΟΠΟΥΛΟΥ Α.Μ.: 09/061. Υπεύθυνος Καθηγητής: Σάββας Μακρίδης
 Α.Τ.Ε.Ι. ΙΟΝΙΩΝ ΝΗΣΩΝ ΠΑΡΑΡΤΗΜΑ ΑΡΓΟΣΤΟΛΙΟΥ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ ΚΑΙ ΕΠΙΚΟΙΝΩΝΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Η διαμόρφωση επικοινωνιακής στρατηγικής (και των τακτικών ενεργειών) για την ενδυνάμωση της εταιρικής
Α.Τ.Ε.Ι. ΙΟΝΙΩΝ ΝΗΣΩΝ ΠΑΡΑΡΤΗΜΑ ΑΡΓΟΣΤΟΛΙΟΥ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ ΚΑΙ ΕΠΙΚΟΙΝΩΝΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Η διαμόρφωση επικοινωνιακής στρατηγικής (και των τακτικών ενεργειών) για την ενδυνάμωση της εταιρικής
ΚΒΑΝΤΙΚΟΙ ΥΠΟΛΟΓΙΣΤΕΣ
 Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Τμήμα Ηλεκτρονικών Μηχανικών Τ.Ε. ΚΒΑΝΤΙΚΟΙ ΥΠΟΛΟΓΙΣΤΕΣ Πτυχιακή Εργασία Φοιτητής: ΜIΧΑΗΛ ΖΑΓΟΡΙΑΝΑΚΟΣ ΑΜ: 38133 Επιβλέπων Καθηγητής Καθηγητής Ε.
Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Τμήμα Ηλεκτρονικών Μηχανικών Τ.Ε. ΚΒΑΝΤΙΚΟΙ ΥΠΟΛΟΓΙΣΤΕΣ Πτυχιακή Εργασία Φοιτητής: ΜIΧΑΗΛ ΖΑΓΟΡΙΑΝΑΚΟΣ ΑΜ: 38133 Επιβλέπων Καθηγητής Καθηγητής Ε.
ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΠΕΛΟΠΟΝΝΗΣΟΥ
 ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΠΕΛΟΠΟΝΝΗΣΟΥ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΚΑΙ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΔΙΟΙΚΗΣΗΣ ΕΠΙΧΕΙΡΗΣΕΩΝ ΚΑΙ ΟΡΓΑΝΙΣΜΩΝ Κατ/νση Τοπικής Αυτοδιοίκησης ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Μοντέλα στρατηγικής διοίκησης και
ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΠΕΛΟΠΟΝΝΗΣΟΥ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΚΑΙ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΔΙΟΙΚΗΣΗΣ ΕΠΙΧΕΙΡΗΣΕΩΝ ΚΑΙ ΟΡΓΑΝΙΣΜΩΝ Κατ/νση Τοπικής Αυτοδιοίκησης ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Μοντέλα στρατηγικής διοίκησης και
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ»
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
ΕΘΝΙΚΟ ΚΑΙ ΚΑΠΟΔΙΣΤΡΙΑΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΘΗΝΩΝ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΚΑΙ ΤΗΛΕΠΙΚΟΙΝΩΝΙΩΝ
 ΕΘΝΙΚΟ ΚΑΙ ΚΑΠΟΔΙΣΤΡΙΑΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΘΗΝΩΝ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΚΑΙ ΤΗΛΕΠΙΚΟΙΝΩΝΙΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ "ΤΕΧΝΟΛΟΓΙΕΣ ΠΛΗΡΟΦΟΡΙΚΗΣ ΣΤΗΝ ΙΑΤΡΙΚΗ ΚΑΙ ΤΗ ΒΙΟΛΟΓΙΑ" ΔΙΠΛΩΜΑΤΙΚΗ
ΕΘΝΙΚΟ ΚΑΙ ΚΑΠΟΔΙΣΤΡΙΑΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΘΗΝΩΝ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΚΑΙ ΤΗΛΕΠΙΚΟΙΝΩΝΙΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ "ΤΕΧΝΟΛΟΓΙΕΣ ΠΛΗΡΟΦΟΡΙΚΗΣ ΣΤΗΝ ΙΑΤΡΙΚΗ ΚΑΙ ΤΗ ΒΙΟΛΟΓΙΑ" ΔΙΠΛΩΜΑΤΙΚΗ
[1] P Q. Fig. 3.1
![[1] P Q. Fig. 3.1 [1] P Q. Fig. 3.1](/thumbs/79/80362156.jpg) 1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Overview. Transition Semantics. Configurations and the transition relation. Executions and computation
 Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Συστήματα Διαχείρισης Βάσεων Δεδομένων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
Παράλληλος προγραμματισμός περιστροφικών αλγορίθμων εξωτερικών σημείων τύπου simplex ΠΛΟΣΚΑΣ ΝΙΚΟΛΑΟΣ
 Παράλληλος προγραμματισμός περιστροφικών αλγορίθμων εξωτερικών σημείων τύπου simplex ΠΛΟΣΚΑΣ ΝΙΚΟΛΑΟΣ Διπλωματική Εργασία Μεταπτυχιακού Προγράμματος στην Εφαρμοσμένη Πληροφορική Κατεύθυνση: Συστήματα Υπολογιστών
Παράλληλος προγραμματισμός περιστροφικών αλγορίθμων εξωτερικών σημείων τύπου simplex ΠΛΟΣΚΑΣ ΝΙΚΟΛΑΟΣ Διπλωματική Εργασία Μεταπτυχιακού Προγράμματος στην Εφαρμοσμένη Πληροφορική Κατεύθυνση: Συστήματα Υπολογιστών
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ
 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
Η ΠΡΟΣΩΠΙΚΗ ΟΡΙΟΘΕΤΗΣΗ ΤΟΥ ΧΩΡΟΥ Η ΠΕΡΙΠΤΩΣΗ ΤΩΝ CHAT ROOMS
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ Ι Ο Ν Ι Ω Ν Ν Η Σ Ω Ν ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : ΑΤΕΙ Ιονίων Νήσων- Λεωφόρος Αντώνη Τρίτση Αργοστόλι Κεφαλληνίας, Ελλάδα 28100,+30
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ Ι Ο Ν Ι Ω Ν Ν Η Σ Ω Ν ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : ΑΤΕΙ Ιονίων Νήσων- Λεωφόρος Αντώνη Τρίτση Αργοστόλι Κεφαλληνίας, Ελλάδα 28100,+30
Démographie spatiale/spatial Demography
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
ΔΙΠΛΩΜΑΣΙΚΗ ΕΡΓΑΙΑ. του φοιτητή του Σμήματοσ Ηλεκτρολόγων Μηχανικών και. Σεχνολογίασ Τπολογιςτών τησ Πολυτεχνικήσ χολήσ του. Πανεπιςτημίου Πατρών
 ΠΑΝΕΠΙΣΗΜΙΟ ΠΑΣΡΩΝ ΣΜΗΜΑ ΗΛΕΚΣΡΟΛΟΓΩΝ ΜΗΦΑΝΙΚΩΝ ΚΑΙ ΣΕΦΝΟΛΟΓΙΑ ΤΠΟΛΟΓΙΣΩΝ ΣΟΜΕΑ: ΗΛΕΚΣΡΟΝΙΚΗ ΚΑΙ ΤΠΟΛΟΓΙΣΩΝ ΕΡΓΑΣΗΡΙΟ ΗΛΕΚΣΡΟΝΙΚΩΝ ΤΠΟΛΟΓΙΣΩΝ ΔΙΠΛΩΜΑΣΙΚΗ ΕΡΓΑΙΑ του φοιτητή του Σμήματοσ Ηλεκτρολόγων Μηχανικών
ΠΑΝΕΠΙΣΗΜΙΟ ΠΑΣΡΩΝ ΣΜΗΜΑ ΗΛΕΚΣΡΟΛΟΓΩΝ ΜΗΦΑΝΙΚΩΝ ΚΑΙ ΣΕΦΝΟΛΟΓΙΑ ΤΠΟΛΟΓΙΣΩΝ ΣΟΜΕΑ: ΗΛΕΚΣΡΟΝΙΚΗ ΚΑΙ ΤΠΟΛΟΓΙΣΩΝ ΕΡΓΑΣΗΡΙΟ ΗΛΕΚΣΡΟΝΙΚΩΝ ΤΠΟΛΟΓΙΣΩΝ ΔΙΠΛΩΜΑΣΙΚΗ ΕΡΓΑΙΑ του φοιτητή του Σμήματοσ Ηλεκτρολόγων Μηχανικών
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
Μηχανική Μάθηση Hypothesis Testing
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών δικτύων ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΕΠΙΚΟΙΝΩΝΙΩΝ, ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΣΥΣΤΗΜΑΤΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΕΠΙΚΟΙΝΩΝΙΩΝ, ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΣΥΣΤΗΜΑΤΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών
Bayesian statistics. DS GA 1002 Probability and Statistics for Data Science.
 Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
6.3 Forecasting ARMA processes
 122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ
 ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ ΕΛΕΝΑ ΦΛΟΚΑ Επίκουρος Καθηγήτρια Τµήµα Φυσικής, Τοµέας Φυσικής Περιβάλλοντος- Μετεωρολογίας ΓΕΝΙΚΟΙ ΟΡΙΣΜΟΙ Πληθυσµός Σύνολο ατόµων ή αντικειµένων στα οποία αναφέρονται
ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ ΕΛΕΝΑ ΦΛΟΚΑ Επίκουρος Καθηγήτρια Τµήµα Φυσικής, Τοµέας Φυσικής Περιβάλλοντος- Μετεωρολογίας ΓΕΝΙΚΟΙ ΟΡΙΣΜΟΙ Πληθυσµός Σύνολο ατόµων ή αντικειµένων στα οποία αναφέρονται
«ΑΓΡΟΤΟΥΡΙΣΜΟΣ ΚΑΙ ΤΟΠΙΚΗ ΑΝΑΠΤΥΞΗ: Ο ΡΟΛΟΣ ΤΩΝ ΝΕΩΝ ΤΕΧΝΟΛΟΓΙΩΝ ΣΤΗΝ ΠΡΟΩΘΗΣΗ ΤΩΝ ΓΥΝΑΙΚΕΙΩΝ ΣΥΝΕΤΑΙΡΙΣΜΩΝ»
 I ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ ΣΧΟΛΗ ΝΟΜΙΚΩΝ ΟΙΚΟΝΟΜΙΚΩΝ ΚΑΙ ΠΟΛΙΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΟΙΚΟΝΟΜΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΣΤΗΝ «ΔΙΟΙΚΗΣΗ ΚΑΙ ΟΙΚΟΝΟΜΙΑ» ΚΑΤΕΥΘΥΝΣΗ: ΟΙΚΟΝΟΜΙΚΗ
I ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ ΣΧΟΛΗ ΝΟΜΙΚΩΝ ΟΙΚΟΝΟΜΙΚΩΝ ΚΑΙ ΠΟΛΙΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΟΙΚΟΝΟΜΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΣΤΗΝ «ΔΙΟΙΚΗΣΗ ΚΑΙ ΟΙΚΟΝΟΜΙΑ» ΚΑΤΕΥΘΥΝΣΗ: ΟΙΚΟΝΟΜΙΚΗ
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ. Ψηφιακή Οικονομία. Διάλεξη 7η: Consumer Behavior Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Ψηφιακή Οικονομία Διάλεξη 7η: Consumer Behavior Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών Τέλος Ενότητας Χρηματοδότηση Το παρόν εκπαιδευτικό υλικό έχει αναπτυχθεί
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Ψηφιακή Οικονομία Διάλεξη 7η: Consumer Behavior Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών Τέλος Ενότητας Χρηματοδότηση Το παρόν εκπαιδευτικό υλικό έχει αναπτυχθεί
the total number of electrons passing through the lamp.
 1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
Optimal Impartial Selection
 Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
Numerical Analysis FMN011
 Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
Code Breaker. TEACHER s NOTES
 TEACHER s NOTES Time: 50 minutes Learning Outcomes: To relate the genetic code to the assembly of proteins To summarize factors that lead to different types of mutations To distinguish among positive,
TEACHER s NOTES Time: 50 minutes Learning Outcomes: To relate the genetic code to the assembly of proteins To summarize factors that lead to different types of mutations To distinguish among positive,
Section 7.6 Double and Half Angle Formulas
 09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
Modbus basic setup notes for IO-Link AL1xxx Master Block
 n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΤΜΗΜΑ ΠΟΛΙΤΙΚΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΟΜΟΣΤΑΤΙΚΗΣ ΕΡΓΑΣΤΗΡΙΟ ΜΕΤΑΛΛΙΚΩΝ ΚΑΤΑΣΚΕΥΩΝ ΕΙΣΑΓΩΓΗ ΣΤΟΝ ΑΥΤΟΜΑΤΟ ΕΛΕΓΧΟ ΤΩΝ ΚΑΤΑΣΚΕΥΩΝ Ανεµόµετρο AMD 1 Αισθητήρας AMD 2 11 ος όροφος Υπολογιστής
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΤΜΗΜΑ ΠΟΛΙΤΙΚΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΟΜΟΣΤΑΤΙΚΗΣ ΕΡΓΑΣΤΗΡΙΟ ΜΕΤΑΛΛΙΚΩΝ ΚΑΤΑΣΚΕΥΩΝ ΕΙΣΑΓΩΓΗ ΣΤΟΝ ΑΥΤΟΜΑΤΟ ΕΛΕΓΧΟ ΤΩΝ ΚΑΤΑΣΚΕΥΩΝ Ανεµόµετρο AMD 1 Αισθητήρας AMD 2 11 ος όροφος Υπολογιστής
Επιβλέπουσα Καθηγήτρια: ΣΟΦΙΑ ΑΡΑΒΟΥ ΠΑΠΑΔΑΤΟΥ
 EΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΕΚΠΑΙΔΕΥΤΙΚΟ ΤΕΧΝΟΛΟΓΙΚΟ ΙΔΡΥΜΑ ΤΕΙ ΙΟΝΙΩΝ ΝΗΣΩΝ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : Λεωφ. Αντ.Τρίτση, Αργοστόλι Κεφαλληνίας Τ.Κ. 28 100 τηλ. : 26710-27311 fax : 26710-27312
EΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΕΚΠΑΙΔΕΥΤΙΚΟ ΤΕΧΝΟΛΟΓΙΚΟ ΙΔΡΥΜΑ ΤΕΙ ΙΟΝΙΩΝ ΝΗΣΩΝ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : Λεωφ. Αντ.Τρίτση, Αργοστόλι Κεφαλληνίας Τ.Κ. 28 100 τηλ. : 26710-27311 fax : 26710-27312
Modern Greek Extension
 Centre Number 2017 HIGHER SCHOOL CERTIFICATE EXAMINATION Student Number Modern Greek Extension Written Examination General Instructions Reading time 10 minutes Working time 1 hour and 50 minutes Write
Centre Number 2017 HIGHER SCHOOL CERTIFICATE EXAMINATION Student Number Modern Greek Extension Written Examination General Instructions Reading time 10 minutes Working time 1 hour and 50 minutes Write
A Method for Creating Shortcut Links by Considering Popularity of Contents in Structured P2P Networks
 P2P 1,a) 1 1 1 P2P P2P P2P P2P A Method for Creating Shortcut Links by Considering Popularity of Contents in Structured P2P Networks NARISHIGE Yuki 1,a) ABE Kota 1 ISHIBASHI Hayato 1 MATSUURA Toshio 1
P2P 1,a) 1 1 1 P2P P2P P2P P2P A Method for Creating Shortcut Links by Considering Popularity of Contents in Structured P2P Networks NARISHIGE Yuki 1,a) ABE Kota 1 ISHIBASHI Hayato 1 MATSUURA Toshio 1
On a four-dimensional hyperbolic manifold with finite volume
 BULETINUL ACADEMIEI DE ŞTIINŢE A REPUBLICII MOLDOVA. MATEMATICA Numbers 2(72) 3(73), 2013, Pages 80 89 ISSN 1024 7696 On a four-dimensional hyperbolic manifold with finite volume I.S.Gutsul Abstract. In
BULETINUL ACADEMIEI DE ŞTIINŢE A REPUBLICII MOLDOVA. MATEMATICA Numbers 2(72) 3(73), 2013, Pages 80 89 ISSN 1024 7696 On a four-dimensional hyperbolic manifold with finite volume I.S.Gutsul Abstract. In
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3
 Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Test Data Management in Practice
 Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
Section 1: Listening and responding. Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016
 Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ "ΠΟΛΥΚΡΙΤΗΡΙΑ ΣΥΣΤΗΜΑΤΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ. Η ΠΕΡΙΠΤΩΣΗ ΤΗΣ ΕΠΙΛΟΓΗΣ ΑΣΦΑΛΙΣΤΗΡΙΟΥ ΣΥΜΒΟΛΑΙΟΥ ΥΓΕΙΑΣ "
 ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΚΑΛΑΜΑΤΑΣ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΜΟΝΑΔΩΝ ΥΓΕΙΑΣ ΚΑΙ ΠΡΟΝΟΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ "ΠΟΛΥΚΡΙΤΗΡΙΑ ΣΥΣΤΗΜΑΤΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ. Η ΠΕΡΙΠΤΩΣΗ ΤΗΣ ΕΠΙΛΟΓΗΣ ΑΣΦΑΛΙΣΤΗΡΙΟΥ ΣΥΜΒΟΛΑΙΟΥ
ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΚΑΛΑΜΑΤΑΣ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΜΟΝΑΔΩΝ ΥΓΕΙΑΣ ΚΑΙ ΠΡΟΝΟΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ "ΠΟΛΥΚΡΙΤΗΡΙΑ ΣΥΣΤΗΜΑΤΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ. Η ΠΕΡΙΠΤΩΣΗ ΤΗΣ ΕΠΙΛΟΓΗΣ ΑΣΦΑΛΙΣΤΗΡΙΟΥ ΣΥΜΒΟΛΑΙΟΥ
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
þÿ¼ ½ ±Â : ÁÌ» Â Ä Å ÃÄ ²µ þÿä Å ÃÇ»¹º Í Á³ Å
 Neapolis University HEPHAESTUS Repository School of Economic Sciences and Business http://hephaestus.nup.ac.cy Master Degree Thesis 2015 þÿ ½»Åà Äɽ µ½½ ¹Î½ Ä Â þÿ±¾¹»ì³ à  º±¹ Ä Â þÿ±à ĵ»µÃ¼±Ä¹ºÌÄ Ä±Â
Neapolis University HEPHAESTUS Repository School of Economic Sciences and Business http://hephaestus.nup.ac.cy Master Degree Thesis 2015 þÿ ½»Åà Äɽ µ½½ ¹Î½ Ä Â þÿ±¾¹»ì³ à  º±¹ Ä Â þÿ±à ĵ»µÃ¼±Ä¹ºÌÄ Ä±Â
Πτυχιακή Εργασία Η ΠΟΙΟΤΗΤΑ ΖΩΗΣ ΤΩΝ ΑΣΘΕΝΩΝ ΜΕ ΣΤΗΘΑΓΧΗ
 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΥΓΕΙΑΣ Πτυχιακή Εργασία Η ΠΟΙΟΤΗΤΑ ΖΩΗΣ ΤΩΝ ΑΣΘΕΝΩΝ ΜΕ ΣΤΗΘΑΓΧΗ Νικόλας Χριστοδούλου Λευκωσία, 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΥΓΕΙΑΣ
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΥΓΕΙΑΣ Πτυχιακή Εργασία Η ΠΟΙΟΤΗΤΑ ΖΩΗΣ ΤΩΝ ΑΣΘΕΝΩΝ ΜΕ ΣΤΗΘΑΓΧΗ Νικόλας Χριστοδούλου Λευκωσία, 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΥΓΕΙΑΣ
Context-aware και mhealth
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΜΕΤΑΔΟΣΗΣ ΠΛΗΡΟΦΟΡΙΑΣ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΛΙΚΩΝ Context-aware και mhealth ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Του Κουβαρά
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΜΕΤΑΔΟΣΗΣ ΠΛΗΡΟΦΟΡΙΑΣ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΛΙΚΩΝ Context-aware και mhealth ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Του Κουβαρά
ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ ΤΣΗΜΑΣΟ ΨΗΦΙΑΚΗ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ
 ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
Οικονοµετρική ιερεύνηση των Ελλειµµάτων της Ελληνικής Οικονοµίας
 Οικονοµετρική ιερεύνηση των Ελλειµµάτων της Ελληνικής Οικονοµίας του Παντελίδη Παναγιώτη ιδακτορική ιατριβή η οποία υποβλήθηκε στο Τµήµα Εφαρµοσµένης Πληροφορικής του Πανεπιστηµίου Μακεδονίας Οικονοµικών
Οικονοµετρική ιερεύνηση των Ελλειµµάτων της Ελληνικής Οικονοµίας του Παντελίδη Παναγιώτη ιδακτορική ιατριβή η οποία υποβλήθηκε στο Τµήµα Εφαρµοσµένης Πληροφορικής του Πανεπιστηµίου Μακεδονίας Οικονοµικών
Business English. Ενότητα # 9: Financial Planning. Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ
 ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ Ενότητα 1β: Principles of PS Ιφιγένεια Μαχίλη Τμήμα Οικονομικών Επιστημών Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης
ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ Ενότητα 1β: Principles of PS Ιφιγένεια Μαχίλη Τμήμα Οικονομικών Επιστημών Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης
ΠΕΡΙΛΗΨΗ. Εισαγωγή. Σκοπός
 ΠΕΡΙΛΗΨΗ Εισαγωγή Η παιδική παχυσαρκία έχει φτάσει σε επίπεδα επιδημίας στις μέρες μας. Μαστίζει παιδιά από μικρές ηλικίες μέχρι και σε εφήβους. Συντείνουν αρκετοί παράγοντες που ένα παιδί γίνεται παχύσαρκο
ΠΕΡΙΛΗΨΗ Εισαγωγή Η παιδική παχυσαρκία έχει φτάσει σε επίπεδα επιδημίας στις μέρες μας. Μαστίζει παιδιά από μικρές ηλικίες μέχρι και σε εφήβους. Συντείνουν αρκετοί παράγοντες που ένα παιδί γίνεται παχύσαρκο
ΑΝΑΠΤΥΞΗ ΣΕΝΑΡΙΩΝ ΒΕΛΤΙΣΤΟΠΟΙΗΣΗΣ ΤΗΣ ΔΙΑΧΕΙΡΙΣΗΣ ΚΑΙ ΤΗΣ ΥΔΡΟΗΛΕΚΤΡΙΚΗΣ ΠΑΡΑΓΩΓΗΣ ΤΟΥ ΥΔΡΟΣΥΣΤΗΜΑΤΟΣ ΤΟΥ ΠΟΤΑΜΟΥ ΝΕΣΤΟΥ
 ΑΝΑΠΤΥΞΗ ΣΕΝΑΡΙΩΝ ΒΕΛΤΙΣΤΟΠΟΙΗΣΗΣ ΤΗΣ ΔΙΑΧΕΙΡΙΣΗΣ ΚΑΙ ΤΗΣ ΥΔΡΟΗΛΕΚΤΡΙΚΗΣ ΠΑΡΑΓΩΓΗΣ ΤΟΥ ΥΔΡΟΣΥΣΤΗΜΑΤΟΣ ΤΟΥ ΠΟΤΑΜΟΥ ΝΕΣΤΟΥ ΑΝΑΠΤΥΞΗ ΣΕΝΑΡΙΩΝ ΒΕΛΤΙΣΤΟΠΟΙΗΣΗΣ ΤΗΣ ΔΙΑΧΕΙΡΙΣΗΣ ΚΑΙ ΤΗΣ ΥΔΡΟΗΛΕΚΤΡΙΚΗΣ ΠΑΡΑΓΩΓΗΣ
ΑΝΑΠΤΥΞΗ ΣΕΝΑΡΙΩΝ ΒΕΛΤΙΣΤΟΠΟΙΗΣΗΣ ΤΗΣ ΔΙΑΧΕΙΡΙΣΗΣ ΚΑΙ ΤΗΣ ΥΔΡΟΗΛΕΚΤΡΙΚΗΣ ΠΑΡΑΓΩΓΗΣ ΤΟΥ ΥΔΡΟΣΥΣΤΗΜΑΤΟΣ ΤΟΥ ΠΟΤΑΜΟΥ ΝΕΣΤΟΥ ΑΝΑΠΤΥΞΗ ΣΕΝΑΡΙΩΝ ΒΕΛΤΙΣΤΟΠΟΙΗΣΗΣ ΤΗΣ ΔΙΑΧΕΙΡΙΣΗΣ ΚΑΙ ΤΗΣ ΥΔΡΟΗΛΕΚΤΡΙΚΗΣ ΠΑΡΑΓΩΓΗΣ
ΣΥΓΧΡΟΝΕΣ ΤΑΣΕΙΣ ΣΤΗΝ ΕΚΤΙΜΗΣΗ ΚΑΙ ΧΑΡΤΟΓΡΑΦΗΣΗ ΤΩΝ ΚΙΝΔΥΝΩΝ
 ΕΘΝΙΚΗ ΣΧΟΛΗ ΤΟΠΙΚΗΣ ΑΥΤΟΔΙΟΙΚΗΣΗΣ Δ ΕΚΠΑΙΔΕΥΤΙΚΗ ΣΕΙΡΑ ΤΜΗΜΑ ΠΟΛΙΤΙΚΗΣ ΠΡΟΣΤΑΣΙΑΣ ΣΥΓΧΡΟΝΕΣ ΤΑΣΕΙΣ ΣΤΗΝ ΕΚΤΙΜΗΣΗ ΚΑΙ ΧΑΡΤΟΓΡΑΦΗΣΗ ΤΩΝ ΚΙΝΔΥΝΩΝ Σπουδάστρια: Διαούρτη Ειρήνη Δήμητρα Επιβλέπων καθηγητής:
ΕΘΝΙΚΗ ΣΧΟΛΗ ΤΟΠΙΚΗΣ ΑΥΤΟΔΙΟΙΚΗΣΗΣ Δ ΕΚΠΑΙΔΕΥΤΙΚΗ ΣΕΙΡΑ ΤΜΗΜΑ ΠΟΛΙΤΙΚΗΣ ΠΡΟΣΤΑΣΙΑΣ ΣΥΓΧΡΟΝΕΣ ΤΑΣΕΙΣ ΣΤΗΝ ΕΚΤΙΜΗΣΗ ΚΑΙ ΧΑΡΤΟΓΡΑΦΗΣΗ ΤΩΝ ΚΙΝΔΥΝΩΝ Σπουδάστρια: Διαούρτη Ειρήνη Δήμητρα Επιβλέπων καθηγητής:
EPL 603 TOPICS IN SOFTWARE ENGINEERING. Lab 5: Component Adaptation Environment (COPE)
 EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
Lecture 34 Bootstrap confidence intervals
 Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΗΡΑΚΛΕΙΟ ΚΡΗΤΗΣ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΚΑΙ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΛΟΓΙΣΤΙΚΗΣ
 ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΗΡΑΚΛΕΙΟ ΚΡΗΤΗΣ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΚΑΙ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΛΟΓΙΣΤΙΚΗΣ Π Τ Υ Χ Ι Α Κ Η Ε Ρ Γ Α Σ Ι Α: Ο ΡΟΛΟΣ ΤΗΣ ΣΥΝΑΙΣΘΗΜΑΤΙΚΗΣ ΝΟΗΜΟΣΥΝΗΣ ΣΤΗΝ ΑΠΟΤΕΛΕΣΜΑΤΙΚΗ ΗΓΕΣΙΑ ΕΠΙΜΕΛΕΙΑ
ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ ΗΡΑΚΛΕΙΟ ΚΡΗΤΗΣ ΣΧΟΛΗ ΔΙΟΙΚΗΣΗΣ ΚΑΙ ΟΙΚΟΝΟΜΙΑΣ ΤΜΗΜΑ ΛΟΓΙΣΤΙΚΗΣ Π Τ Υ Χ Ι Α Κ Η Ε Ρ Γ Α Σ Ι Α: Ο ΡΟΛΟΣ ΤΗΣ ΣΥΝΑΙΣΘΗΜΑΤΙΚΗΣ ΝΟΗΜΟΣΥΝΗΣ ΣΤΗΝ ΑΠΟΤΕΛΕΣΜΑΤΙΚΗ ΗΓΕΣΙΑ ΕΠΙΜΕΛΕΙΑ
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΓΕΩΤΕΧΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΚΑΙ ΔΙΑΧΕΙΡΙΣΗΣ ΠΕΡΙΒΑΛΛΟΝΤΟΣ. Πτυχιακή εργασία
 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΓΕΩΤΕΧΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΚΑΙ ΔΙΑΧΕΙΡΙΣΗΣ ΠΕΡΙΒΑΛΛΟΝΤΟΣ Πτυχιακή εργασία ΑΝΑΛΥΣΗ ΚΟΣΤΟΥΣ-ΟΦΕΛΟΥΣ ΓΙΑ ΤΗ ΔΙΕΙΣΔΥΣΗ ΤΩΝ ΑΝΑΝΕΩΣΙΜΩΝ ΠΗΓΩΝ ΕΝΕΡΓΕΙΑΣ ΣΤΗΝ ΚΥΠΡΟ ΜΕΧΡΙ ΤΟ 2030
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΓΕΩΤΕΧΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΚΑΙ ΔΙΑΧΕΙΡΙΣΗΣ ΠΕΡΙΒΑΛΛΟΝΤΟΣ Πτυχιακή εργασία ΑΝΑΛΥΣΗ ΚΟΣΤΟΥΣ-ΟΦΕΛΟΥΣ ΓΙΑ ΤΗ ΔΙΕΙΣΔΥΣΗ ΤΩΝ ΑΝΑΝΕΩΣΙΜΩΝ ΠΗΓΩΝ ΕΝΕΡΓΕΙΑΣ ΣΤΗΝ ΚΥΠΡΟ ΜΕΧΡΙ ΤΟ 2030
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
ΣΤΥΛΙΑΝΟΥ ΣΟΦΙΑ Socm09008@soc.aegean.gr
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΙΓΑΙΟΥ ΣΧΟΛΗ ΚΟΙΝΩΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΚΟΙΝΩΝΙΟΛΟΓΙΑΣ ΜΕΤΑΠΤΥΧΙΑΚΟ ΠΡΟΓΡΑΜΜΑ ΣΠΟΥΔΩΝ «ΕΡΕΥΝΑ ΓΙΑ ΤΗΝ ΤΟΠΙΚΗ ΚΟΙΝΩΝΙΚΗ ΑΝΑΠΤΥΞΗ ΚΑΙ ΣΥΝΟΧΗ» ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Θέμα: Διερεύνηση των απόψεων
ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΙΓΑΙΟΥ ΣΧΟΛΗ ΚΟΙΝΩΝΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΚΟΙΝΩΝΙΟΛΟΓΙΑΣ ΜΕΤΑΠΤΥΧΙΑΚΟ ΠΡΟΓΡΑΜΜΑ ΣΠΟΥΔΩΝ «ΕΡΕΥΝΑ ΓΙΑ ΤΗΝ ΤΟΠΙΚΗ ΚΟΙΝΩΝΙΚΗ ΑΝΑΠΤΥΞΗ ΚΑΙ ΣΥΝΟΧΗ» ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ Θέμα: Διερεύνηση των απόψεων
þÿ ³¹µ¹½ º±¹ ±ÃÆ»µ¹± ÃÄ ÇÎÁ
 Neapolis University HEPHAESTUS Repository School of Economic Sciences and Business http://hephaestus.nup.ac.cy Master Degree Thesis 2014 þÿ ³¹µ¹½ º±¹ ±ÃÆ»µ¹± ÃÄ ÇÎÁ þÿµá³±ã ±Â Äɽ ½ à º ¼µ ɽ : Georgiou,
Neapolis University HEPHAESTUS Repository School of Economic Sciences and Business http://hephaestus.nup.ac.cy Master Degree Thesis 2014 þÿ ³¹µ¹½ º±¹ ±ÃÆ»µ¹± ÃÄ ÇÎÁ þÿµá³±ã ±Â Äɽ ½ à º ¼µ ɽ : Georgiou,
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
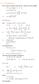 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
ΔΗΜΟΚΡΙΤΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΡΑΚΗΣ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΑΓΩΓΗΣ
 ΔΗΜΟΚΡΙΤΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΡΑΚΗΣ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΑΓΩΓΗΣ ΤΜΗΜΑ ΕΠΙΣΤΗΜΩΝ ΕΚΠΑΙΔΕΥΣΗΣ ΣΤΗΝ ΠΡΟΣΧΟΛΙΚΗ ΗΛΙΚΙΑ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ Διαπολιτισμική Εκπαίδευση και Θρησκευτική Ετερότητα: εθνικές και θρησκευτικές
ΔΗΜΟΚΡΙΤΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΡΑΚΗΣ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΑΓΩΓΗΣ ΤΜΗΜΑ ΕΠΙΣΤΗΜΩΝ ΕΚΠΑΙΔΕΥΣΗΣ ΣΤΗΝ ΠΡΟΣΧΟΛΙΚΗ ΗΛΙΚΙΑ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ Διαπολιτισμική Εκπαίδευση και Θρησκευτική Ετερότητα: εθνικές και θρησκευτικές
Figure A.2: MPC and MPCP Age Profiles (estimating ρ, ρ = 2, φ = 0.03)..
 Supplemental Material (not for publication) Persistent vs. Permanent Income Shocks in the Buffer-Stock Model Jeppe Druedahl Thomas H. Jørgensen May, A Additional Figures and Tables Figure A.: Wealth and
Supplemental Material (not for publication) Persistent vs. Permanent Income Shocks in the Buffer-Stock Model Jeppe Druedahl Thomas H. Jørgensen May, A Additional Figures and Tables Figure A.: Wealth and
ΓΗΠΛΧΜΑΣΗΚΖ ΔΡΓΑΗΑ ΑΡΥΗΣΔΚΣΟΝΗΚΖ ΣΧΝ ΓΔΦΤΡΧΝ ΑΠΟ ΑΠΟΦΖ ΜΟΡΦΟΛΟΓΗΑ ΚΑΗ ΑΗΘΖΣΗΚΖ
 ΔΘΝΗΚΟ ΜΔΣΟΒΗΟ ΠΟΛΤΣΔΥΝΔΗΟ ΥΟΛΖ ΠΟΛΗΣΗΚΧΝ ΜΖΥΑΝΗΚΧΝ ΣΟΜΔΑ ΓΟΜΟΣΑΣΗΚΖ ΓΗΠΛΧΜΑΣΗΚΖ ΔΡΓΑΗΑ ΑΡΥΗΣΔΚΣΟΝΗΚΖ ΣΧΝ ΓΔΦΤΡΧΝ ΑΠΟ ΑΠΟΦΖ ΜΟΡΦΟΛΟΓΗΑ ΚΑΗ ΑΗΘΖΣΗΚΖ ΔΤΘΤΜΗΑ ΝΗΚ. ΚΟΤΚΗΟΤ 01104766 ΔΠΗΒΛΔΠΧΝ:ΑΝ.ΚΑΘΖΓΖΣΖ ΗΧΑΝΝΖ
ΔΘΝΗΚΟ ΜΔΣΟΒΗΟ ΠΟΛΤΣΔΥΝΔΗΟ ΥΟΛΖ ΠΟΛΗΣΗΚΧΝ ΜΖΥΑΝΗΚΧΝ ΣΟΜΔΑ ΓΟΜΟΣΑΣΗΚΖ ΓΗΠΛΧΜΑΣΗΚΖ ΔΡΓΑΗΑ ΑΡΥΗΣΔΚΣΟΝΗΚΖ ΣΧΝ ΓΔΦΤΡΧΝ ΑΠΟ ΑΠΟΦΖ ΜΟΡΦΟΛΟΓΗΑ ΚΑΗ ΑΗΘΖΣΗΚΖ ΔΤΘΤΜΗΑ ΝΗΚ. ΚΟΤΚΗΟΤ 01104766 ΔΠΗΒΛΔΠΧΝ:ΑΝ.ΚΑΘΖΓΖΣΖ ΗΧΑΝΝΖ
