1 Advanced Encryption Standard (AES)
|
|
|
- ÊÊΔιομήδης Αλεβιζόπουλος
- 8 χρόνια πριν
- Προβολές:
Transcript
1 Date: Monday, September 24, 2002 Prof.: Dr Jean-Yves Chouinard Design of Secure Computer Systems CSI4138/CEG4394 Notes on the Advanced Encryption Standard (AES) 1 Advanced Encryption Standard (AES) 1.1 AES History In 1997, the National Institute of Standard and Technology (NIST) of United States initiated the development of an Advanced Encryption Standard (AES) to replace the Data Encryption Standard (DES). The objective was to develop with the industry and cryptographic community an encryption algorithm sufficiently powerful to protect government, as well as private sector, information for several years. As for DES, the algorithm should be royalty-free, publicly disclosed. The AES algorithm was designed as a symmetric block cipher using a minimum of 128-bit input blocks and supporting 3 key sizes, that is: 128-bit, 192-bit and 256-bit keys. In August 1998, NIST announced that 15 AES proposals were received for evaluation and comments. After an analysis of the proposed algorithms, NIST announced in April 1999 that five algorithms were retained as finalist algorithms. These were: 1. MARS 2. RC6 3. Rijndael 4. Serpent 5. Twofish These algorithms were further analyzed in terms of their relative cryptographic strength and ease of implementation. In October 2000, NIST announced that the Rijndael algorithm was selected for the new AES standard. The algorithm is presently under further review, that is validation testing, and it is expected that the AES algorithm be completed for this summer. In February 2001, the NIST delivered a draft Federal Information Processing Standards (FIPS) for the specification of the Advanced Encryption Standard. On November 26, 2001, NIST announced the final specification of the Advanced Encryption Standard (FIPS PUB 197) [NIS01]. 1
2 1.2 Rijndael Block Cipher Algorithm Mathematical Background In the AES algorithm, the operations, such as the addition and the multiplication, are performed on bytes over a finite field, the Galois Field GF(2 8 ). Addition The addition between two elements, or bytes, from the finite field is achieved by the addition modulo 2 of the corresponding bits in the representation of the bytes. The addition of the bytes A = (a 1, a 2, a 3, a 4, a 5, a 6, a 7, a 8 ) and B = (b 1, b 2, b 3, b 4, b 5, b 6, b 7, b 8 ) gives C = A + B with C = (c 1, c 2, c 3, c 4, c 5, c 6, c 7, c 8 ) where c i = a i b i for 1 < i < 8. The finite field elements can also be represented in polynomial form. For instance, the sum of A = and B = 4E 16 (in hexadecimal notation) is obtained as: E 16 = 3D 16 (hexadecimal notation) = (binary notation) (x 6 + x 5 + x 4 + x + 1) + (x 6 + x 3 + x 2 + x) = (x 5 + x 4 + x 3 + x 2 + 1) in polynomial notation. Multiplication As for the multiplication operation, it is also done over the Galois Field GF(2 8 ) and is obtained by the multiplication of the two elements polynomials and then reduced modulo an irreductible polynomial m(x), which is equivalent to a prime number in the standard numbering system. As a prime number, the irreductible polynomial as only two divisors: 1 and itself, m(x). For AES, this irreductible polynomial is m(x) = (x 8 + x 4 + x 3 + x + 1). Let, for example, A = C3 16 and B = 85 16, that is, a(x) = (x 7 +x 6 +x+1) and b(x) = (x 7 +x 2 +1). Then C = A B is given by: c(x) = [a(x) b(x)] mod (x 8 + x 4 + x 3 + x + 1) c(x) = [(x 7 + x 6 + x + 1) (x 7 + x 2 + 1)] mod (x 8 + x 4 + x 3 + x + 1) c(x) = [(x 14 + x 13 + x 8 + x 7 ) + (x 9 + x 8 + x 3 + x 2 ) + (x 7 + x 6 + x + 1)] mod (x 8 + x 4 + x 3 + x + 1) c(x) = [(x 14 + x 13 + x 9 + x 6 + x 3 + x 2 + x + 1)] mod (x 8 + x 4 + x 3 + x + 1) c(x) = [(x 6 + x 5 + x 2 + x + 1) (x 8 + x 4 + x 3 + x + 1) + (x 7 + x 5 + x 3 + x 2 + x)] mod(x 8 + x 4 + x 3 + x + 1) c(x) = (x 7 + x 5 + x 3 + x 2 + x) and then c(x) = (x 7 + x 5 + x 3 + x 2 + x) or C = in binary notation or, in hexadecimal notation: C = AE 16. 2
3 Construction of an (extended) Galois Fields Let p be a prime number. Galois Field GF(p) is given by the element {0} and the (p 1) successive powers: 1, α, α 1, α 2,..., α (p 1) Many computer based algorithms operate on extensions of the Galois Field GF(2) which consists of the two binary elements {0, 1}. Reed-Solomon error correction codes and the AES encryption algorithm, which are basically Byte-oriented algorithms, use extended Galois Field such as GF(p m ) = GF(2 8 ) = GF(256) that contains 256 distinct elements. To generate such an extended Galois Field, a primitive polynomial p(x) over GF(q) is needed. An irreductible polynomial p(x) is a polynomial which cannot be factored into lower degree polynomials in over GF(q). An irreductible polynomial p(x) of degree m is a primitive polynomial if the smallest positive integer n for which p(x) divides x n 1 is n = p m 1. To form the Galois Field, one has to determine a root α of the primitive polynomial p(x), that is p(α) = 0. For instance, the primitive polynomial p(x) = x 4 + x + 1 can be used to form the extended Galois Field GF(2 4 ) = GF(16), that is for p = 2 and m = 4. Then the root α of p(x) is: p(α) = 0 α 4 + α + 1 = 0 and therefore: α 4 = α + 1. Table 1 illustrates how to generate the extended Galois Field GF(2 4 ) from the primitive polynomial p(x). Table 4 gives an extended Galois Field GF(2 8 ) that can be used for Reed-Solomon error control coding and for AES byte operations. The primitive polynomial p(x) = x 8 + x 4 + x 3 + x is used and the extended Galois Field GF(2 8 ) is obtained with the polynomial root: α 8 = α 4 + α 3 + α
4 Table 1: Galois Field GF (2 4 ) = GF (16). element of polynomial binary decimal GF (16) form form form α α α 2 α α 3 α α 4 α α 5 α 2 +α α 6 α 3 +α α 7 α 3 +α α 8 α α 9 α 3 +α α 10 α 2 +α α 11 α 3 +α 2 +α α 12 α 3 +α 2 +α α 13 α 3 +α α 14 α
5 1.3 Advanced Encryption Standard Algorithm The Advanced Encryption Standard Algorithm encrypts a 128-bit plaintext block M into a 128-bit ciphertext block C using a cipher key K of either 128 bits, 192 bits or 256 bits. The different key lengths employed for AES are refered to: AES-128, AES-192, and AES-256. The algorithm operates on bytes and the block size for the input, output and key are represented by 32-bit words, that is 4 bytes. The AES algorithm performs a number N r of cryptographic rounds depending on the actual key length used as indicated in Table 2 for AES-128, AES-192 and AES-256. Table 2: Number of cryptographic rounds N r for AES encryption. AES Input/output Key length Number of algorithm length N b N k rounds N r AES words 4 words 10 rounds AES words 6 words 12 rounds AES words 8 words 14 rounds Each round consists of four byte-oriented cryptographic transformations: 1. Byte Substitution 2. Shifting rows of the State Array 3. Mixing data within a column of the State Array 4. Round Key addition to the State Array Cipher(byte in[4 * Nb], byte out[4 * Nb], word w[nb * (Nr + 1)]) begin byte state[4,nb] state = in AddRoundKey(state, w) for round = 1 step 1 to Nr - 1 SubBytes(state) ShiftRows(state) MixColumns(state) AddRoundKey(state, w + round * Nb) end for SubBytes(state) ShiftRows(state) AddRoundKey(state, w + Nr * Nb) out = state end (Source: AES draft specification: 5
6 Byte Substitution: SubBytes() transformation The first AES transformation is a non linear byte substitution transformation called SubBytes() transformation. It operates independently on each byte. It first computes the multiplicative inverse in the finite Galois Field GF(2 8 ). It then applies an affine transformation on the multiplicative inverse: b b 0 1 b 1 b b b 2 0 b 3 b = b b b b 5 1 b b 6 1 b b 7 0 where b i represents the i th bit of byte b. Shifting rows of the State Array: Shif trows() transformation The next transformation of the AES cipher consits in shifting the rows of the State array. The amount of shifting shift(r, N b ) depends on the row number r. The input (plaintext) and output (ciphertext) blocks are 128 bit-blocks or consist of N b = 4 32-bit words. The Shif trows() transformation can be expressed as: s r,c = s r,(c+shift(r,nb )) mod N b where 0 c < N b. For the first row, there is no row shifting, that is: shift(0, N b = 4) = 0. For the remaining rows the amount of shifting depend on the row number: shif t(0, 4) = 0 shif t(1, 4) = 1 shif t(2, 4) = 2 shif t(3, 4) = 3 Mixing data within a column of the State Array: M ixcolumns() transformation The MixColumns() transformation is used to Mix the data within a single column of the State matrix. The columns are represented as polynomials over the Galois Field GF(2 8 ). The output of the MixColumns() transformation s (x) is given by the multiplication of the input column s(x) with the polynomial a(x) and reduced modulo (x 4 + 1): s (x) = a(x) s(x) mod (x 4 + 1) where a(x) = x x x In matrix form, this column mixing transformation can be represented as: s 0,c s 1,c s 2,c s 3,c = s 0,c s 1,c s 2,c s 3,c where 0 c < N b. 6
7 Round Key addition to the State Array: AddRoundKey() transformation In the AddRoundKey() transformation, the key bits derived from the original Cipher Key by the Key Expansion transformation are added bitwise to the State array. An initial Round Key w 0, i.e. for round = 0, is added prior the first cryptographic round. Then at each round, i.e. for 1 round N r, a different 32-bit Round Key w i is added: [ s 0,c, s 1,c, s 2,c, s ] 3,c = [s0,c, s 1,c, s 2,c, s 3,c ] [ w (round Nb )+c] where 0 c < N b. AES Key Expansion The AES algorithm generates from the Cipher Key (128-bit, 192-bit or 256-bit long) an initial set of N b 32-bit words and a N b 32-bit for each of the N r rounds, resulting in a total of N b (N r + 1) 32-bit words, {w i }, for 0 i < N b (N r +1). The pseudocode for the AES key expansion algorithm is given in the FIPS draft (Web site: and reproduced hereafter. Note that this is a draft document and that the final AES specification should be adopted in the summer of The function SubW ord() applies the substitution transformation of the S-box on a 4-byte input word to produce a 4-byte output word. Function RotW ord() performs a cyclic byte permutation on a 4-byte (32-bit) word w i. RotW ord(a 0, a 1, a 2, a 3 ) = (a 1, a 2, a 3, a 0 ) AES Key Management As is the case for DES, the AES is a symmetric block cipher cryptosystem that requires the secure distribution of the secret key between the sender and recipient. Table 3 indicates the length of the public key for the three AES key lengths. This entries in Table 3 show the advantage of using a key exchange scheme based on Elliptic Curve Cryptography (ECC) instead of the RSA algorithm for the same level of security. Table 3: Required RSA and Elliptic Curve Cryptography (ECC) key lengths for encryption of AES secret keys with equivalent security. AES algorithm AES key length RSA key length ECC key length AES bits 3,072 bits 283 bits AES bits 7,680 bits 409 bits AES bits 15,360 bits 571 bits 7
8 KeyExpansion(byte key[4 * Nk], word w[nb * (Nr + 1)], Nk) begin i=0 while (i < Nk) w[i] = word[key[4*i],key[4*i+1],key[4*i+2],key[4*i+3]] i = i + 1 end while end i = Nk while (i < Nb * (Nr + 1)) word temp = w[i - 1] if (i mod Nk = 0) temp = SubWord(RotWord(temp)) xor Rcon[i / Nk] else if (Nk = 8 and i mod Nk = 4) temp = SubWord(temp) end if w[i] = w[i - Nk] xor temp i = i + 1 end while (Source: AES draft specification: 8
9 Table 4: Galois Field GF (2 8 ) = GF (256). element of polynomial binary decimal GF (256) form form form α α α 2 α α 3 α α 4 α α 5 α α 6 α α 7 α α 8 α 4 +α 3 +α α 9 α 5 +α 4 +α 3 +α α 10 α 6 +α 5 +α 4 +α α 11 α 7 +α 6 +α 5 +α α 12 α 7 +α 6 +α 3 +α α 13 α 7 +α 2 +α α 14 α 4 +α α 15 α 5 +α 2 +α α 16 α 6 +α 3 +α α 17 α 7 +α 4 +α α 18 α 5 +α 3 +α α 19 α 6 +α 4 +α 3 +α α 20 α 7 +α 5 +α 4 +α α 21 α 6 +α 5 +α 4 +α α 22 α 7 +α 6 +α 5 +α 3 +α α 23 α 7 +α 6 +α α 24 α 7 +α 3 +α 2 +α α 25 α α 26 α 2 +α α 27 α 3 +α α 28 α 4 +α α 29 α 5 +α α 30 α 6 +α α 31 α 7 +α
10 element of polynomial binary decimal GF (256) form form form α 32 α 7 +α 4 +α 3 +α α 33 α 5 +α 2 +α α 34 α 6 +α 3 +α 2 +α α 35 α 7 +α 4 +α 3 +α α 36 α 5 +α α 37 α 6 +α 3 +α α 38 α 7 +α 4 +α α 39 α 5 +α 4 +α α 40 α 6 +α 5 +α 3 +α α 41 α 7 +α 6 +α 4 +α α 42 α 7 +α 5 +α 4 +α α 43 α 6 +α 5 +α 4 +α 2 +α α 44 α 7 +α 6 +α 5 +α 3 +α 2 +α α 45 α 7 +α α 46 α 7 +α 4 +α 3 +α 2 +α α 47 α 5 +α α 48 α 6 +α 2 +α α 49 α 7 +α 3 +α α 50 α α 51 α 3 +α α 52 α 4 +α α 53 α 5 +α α 54 α 6 +α α 55 α 7 +α α 56 α 6 +α 4 +α 3 +α α 57 α 7 +α 5 +α 4 +α 3 +α α 58 α 6 +α 5 +α α 59 α 7 +α 6 +α 4 +α α 60 α 7 +α 5 +α 4 +α α 61 α 6 +α 5 +α 3 +α 2 +α α 62 α 7 +α 6 +α 4 +α 3 +α 2 +α α 63 α 7 +α
11 element of polynomial binary decimal GF (256) form form form α 64 α 6 +α 4 +α 3 +α 2 +α α 65 α 7 +α 5 +α 4 +α 3 +α 2 +α α 66 α 6 +α α 67 α 7 +α 6 +α α 68 α 7 +α 4 +α α 69 α 5 +α 3 +α 2 +α α 70 α 6 +α 4 +α 3 +α 2 +α α 71 α 7 +α 5 +α 4 +α 3 +α α 72 α 6 +α 5 +α α 73 α 7 +α 6 +α 3 +α α 74 α 7 +α α 75 α 3 +α 2 +α α 76 α 4 +α 3 +α 2 +α α 77 α 5 +α 4 +α 3 +α α 78 α 6 +α 5 +α 4 +α α 79 α 7 +α 6 +α 5 +α α 80 α 7 +α 6 +α 5 +α 4 +α 3 +α α 81 α 7 +α 6 +α 5 +α 2 +α α 82 α 7 +α 6 +α 4 +α α 83 α 7 +α 5 +α 4 +α 3 +α α 84 α 6 +α 5 +α 3 +α α 85 α 7 +α 6 +α 4 +α 2 +α α 86 α 7 +α 5 +α α 87 α 6 +α 5 +α 4 +α 3 +α 2 +α α 88 α 7 +α 6 +α 5 +α 4 +α 3 +α 2 +α α 89 α 7 +α 6 +α α 90 α 7 +α 6 +α 4 +α 3 +α 2 +α α 91 α 7 +α 5 +α α 92 α 6 +α 4 +α 3 +α α 93 α 7 +α 5 +α 4 +α 2 +α α 94 α 6 +α 5 +α α 95 α 7 +α 6 +α 5 +α
12 element of polynomial binary decimal GF (256) form form form α 96 α 7 +α 6 +α 4 +α α 97 α 7 +α 5 +α 3 +α 2 +α α 98 α 6 +α α 99 α 7 +α 2 +α α 100 α α 101 α 5 +α α 102 α 6 +α α 103 α 7 +α α 104 α 3 +α α 105 α 4 +α 3 +α α 106 α 5 +α 4 +α α 107 α 6 +α 5 +α α 108 α 7 +α 6 +α α 109 α 7 +α 5 +α 4 +α 3 +α α 110 α 6 +α 5 +α 2 +α α 111 α 7 +α 6 +α 3 +α 2 +α α 112 α α 113 α 4 +α 3 +α 2 +α α 114 α 5 +α 4 +α 3 +α 2 +α α 115 α 6 +α 5 +α 4 +α 3 +α α 116 α 7 +α 6 +α 5 +α 4 +α α 117 α 7 +α 6 +α 5 +α 3 +α α 118 α 7 +α 6 +α 2 +α α 119 α 7 +α 4 +α α 120 α 5 +α 4 +α 3 +α α 121 α 6 +α 5 +α 4 +α 2 +α α 122 α 7 +α 6 +α 5 +α 3 +α α 123 α 7 +α 6 +α α 124 α 7 +α 4 +α 2 +α α 125 α 5 +α 4 +α α 126 α 6 +α 5 +α 2 +α α 127 α 7 +α 6 +α 3 +α
13 element of polynomial binary decimal GF (256) form form form α 128 α 7 +α α 129 α 4 +α 2 +α α 130 α 5 +α 3 +α 2 +α α 131 α 6 +α 4 +α 3 +α α 132 α 7 +α 5 +α 4 +α α 133 α 6 +α 5 +α 3 +α α 134 α 7 +α 6 +α 4 +α 3 +α α 135 α 7 +α 5 +α α 136 α 6 +α 3 +α 2 +α α 137 α 7 +α 4 +α 3 +α 2 +α α 138 α α 139 α 6 +α α 140 α 7 +α α 141 α 4 +α α 142 α 5 +α 3 +α α 143 α 6 +α 4 +α α 144 α 7 +α 5 +α α 145 α 6 +α 3 +α α 146 α 7 +α 4 +α 3 +α α 147 α 5 +α α 148 α 6 +α 4 +α α 149 α 7 +α 5 +α α 150 α 6 +α 4 +α α 151 α 7 +α 5 +α 3 +α α 152 α 6 +α α 153 α 7 +α 4 +α α 154 α 5 +α 4 +α α 155 α 6 +α 5 +α 4 +α α 156 α 7 +α 6 +α 5 +α α 157 α 7 +α 6 +α 4 +α α 158 α 7 +α 5 +α 4 +α 2 +α α 159 α 6 +α 5 +α 4 +α
14 element of polynomial binary decimal GF (256) form form form α 160 α 7 +α 6 +α 5 +α 2 +α α 161 α 7 +α 6 +α α 162 α 7 +α 5 +α 4 +α 3 +α 2 +α α 163 α 6 +α 5 +α α 164 α 7 +α 6 +α 2 +α α 165 α 7 +α α 166 α 5 +α 4 +α 3 +α 2 +α α 167 α 6 +α 5 +α 4 +α 3 +α 2 +α α 168 α 7 +α 6 +α 5 +α 4 +α 3 +α α 169 α 7 +α 6 +α 5 +α α 170 α 7 +α 6 +α 4 +α 2 +α α 171 α 7 +α 5 +α 4 +α α 172 α 6 +α 5 +α 4 +α 3 +α α 173 α 7 +α 6 +α 5 +α 4 +α 2 +α α 174 α 7 +α 6 +α 5 +α α 175 α 7 +α 6 +α 5 +α 4 +α 3 +α 2 +α α 176 α 7 +α 6 +α 5 +α α 177 α 7 +α 6 +α 4 +α 3 +α α 178 α 7 +α 5 +α 3 +α α 179 α 6 +α 3 +α α 180 α 7 +α 4 +α 2 +α α 181 α 5 +α α 182 α 6 +α 5 +α α 183 α 7 +α 6 +α α 184 α 7 +α 4 +α α 185 α 5 +α 4 +α 2 +α α 186 α 6 +α 5 +α 3 +α 2 +α α 187 α 7 +α 6 +α 4 +α 3 +α α 188 α 7 +α 5 +α α 189 α 6 +α 4 +α 2 +α α 190 α 7 +α 5 +α 3 +α 2 +α α 191 α
15 element of polynomial binary decimal GF (256) form form form α 192 α 7 +α α 193 α 4 +α α 194 α 5 +α 4 +α α 195 α 6 +α 5 +α α 196 α 7 +α 6 +α α 197 α 7 +α 3 +α α 198 α 2 +α α 199 α 3 +α 2 +α α 200 α 4 +α 3 +α α 201 α 5 +α 4 +α α 202 α 6 +α 5 +α α 203 α 7 +α 6 +α α 204 α 7 +α 6 +α 4 +α 3 +α α 205 α 7 +α 5 +α 2 +α α 206 α 6 +α 4 +α α 207 α 7 +α 5 +α 2 +α α 208 α 6 +α α 209 α 7 +α 5 +α α 210 α 6 +α 4 +α α 211 α 7 +α 5 +α 4 +α α 212 α 6 +α 5 +α 4 +α α 213 α 7 +α 6 +α 5 +α 4 +α α 214 α 7 +α 6 +α 5 +α 4 +α α 215 α 7 +α 6 +α 5 +α 3 +α 2 +α α 216 α 7 +α 6 +α α 217 α 7 +α 4 +α 3 +α α 218 α 5 +α 3 +α α 219 α 6 +α 4 +α 2 +α α 220 α 7 +α 5 +α 3 +α α 221 α 6 +α α 222 α 7 +α 3 +α α 223 α
16 element of polynomial binary decimal GF (256) form form form α 224 α 4 +α α 225 α 5 +α α 226 α 6 +α α 227 α 7 +α α 228 α 5 +α 4 +α 3 +α α 229 α 6 +α 5 +α 4 +α 3 +α α 230 α 7 +α 6 +α 5 +α 4 +α α 231 α 7 +α 6 +α 5 +α 4 +α α 232 α 7 +α 6 +α 5 +α 4 +α 2 +α α 233 α 7 +α 6 +α 5 +α 4 +α α 234 α 7 +α 6 +α 5 +α 4 +α 3 +α α 235 α 7 +α 6 +α 5 +α 3 +α α 236 α 7 +α 6 +α 3 +α α 237 α 7 +α 3 +α α 238 α 3 +α α 239 α 4 +α 2 +α α 240 α 5 +α 3 +α α 241 α 6 +α 4 +α α 242 α 7 +α 5 +α α 243 α 6 +α 5 +α 4 +α 3 +α α 244 α 7 +α 6 +α 5 +α 4 +α 3 +α α 245 α 7 +α 6 +α 5 +α α 246 α 7 +α 6 +α 3 +α 2 +α α 247 α 7 +α α 248 α 4 +α 3 +α α 249 α 5 +α 4 +α 2 +α α 250 α 6 +α 5 +α 3 +α α 251 α 7 +α 6 +α 4 +α α 252 α 7 +α 5 +α 3 +α α 253 α 6 +α 2 +α α 254 α 7 +α 3 +α 2 +α References [NIS01] NIST. Data Encryption Standard (AES). Technical Report FIPS PUB 197, National Institute of Standards and Technology, Washington DC, November
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
Εφαρμοσμένη Κρυπτογραφία Ι
 Εφαρμοσμένη Κρυπτογραφία Ι Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou Συμμετρικά Κρυπτοσυστήματα κλειδί k Αρχικό κείμενο (m) Αλγόριθμος Κρυπτογράφησης Ε c = E
Εφαρμοσμένη Κρυπτογραφία Ι Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou Συμμετρικά Κρυπτοσυστήματα κλειδί k Αρχικό κείμενο (m) Αλγόριθμος Κρυπτογράφησης Ε c = E
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3
 Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής
 Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 24/3/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Elements of Information Theory
 Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
SCHOOL OF MATHEMATICAL SCIENCES G11LMA Linear Mathematics Examination Solutions
 SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
Reminders: linear functions
 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Correction Table for an Alcoholometer Calibrated at 20 o C
 An alcoholometer is a device that measures the concentration of ethanol in a water-ethanol mixture (often in units of %abv percent alcohol by volume). The depth to which an alcoholometer sinks in a water-ethanol
An alcoholometer is a device that measures the concentration of ethanol in a water-ethanol mixture (often in units of %abv percent alcohol by volume). The depth to which an alcoholometer sinks in a water-ethanol
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Mean bond enthalpy Standard enthalpy of formation Bond N H N N N N H O O O
 Q1. (a) Explain the meaning of the terms mean bond enthalpy and standard enthalpy of formation. Mean bond enthalpy... Standard enthalpy of formation... (5) (b) Some mean bond enthalpies are given below.
Q1. (a) Explain the meaning of the terms mean bond enthalpy and standard enthalpy of formation. Mean bond enthalpy... Standard enthalpy of formation... (5) (b) Some mean bond enthalpies are given below.
Second Order Partial Differential Equations
 Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1
 Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Κρυπτογραφία. Κωνσταντίνου Ελισάβετ
 Κρυπτογραφία Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou AES Ιαν. 1997: Το NIST (National Institute of Standards and Technology) απευθύνει κάλεσμα για τη δημιουργία
Κρυπτογραφία Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou AES Ιαν. 1997: Το NIST (National Institute of Standards and Technology) απευθύνει κάλεσμα για τη δημιουργία
Tridiagonal matrices. Gérard MEURANT. October, 2008
 Tridiagonal matrices Gérard MEURANT October, 2008 1 Similarity 2 Cholesy factorizations 3 Eigenvalues 4 Inverse Similarity Let α 1 ω 1 β 1 α 2 ω 2 T =......... β 2 α 1 ω 1 β 1 α and β i ω i, i = 1,...,
Tridiagonal matrices Gérard MEURANT October, 2008 1 Similarity 2 Cholesy factorizations 3 Eigenvalues 4 Inverse Similarity Let α 1 ω 1 β 1 α 2 ω 2 T =......... β 2 α 1 ω 1 β 1 α and β i ω i, i = 1,...,
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Δ Εξάμηνο. Κρυπτογραφία: Συμμετρική Κρυπτογράφηση
 ΚΡΥΠΤΟΓΡΑΦΙΑ ΚΑΙ ΑΣΦΑΛΕΙΑ ΥΠΟΛΟΓΙΣΤΩΝ Δ Εξάμηνο Κρυπτογραφία: Συμμετρική Κρυπτογράφηση Διδάσκων : Δρ. Παρασκευάς Κίτσος http://www.diceslab.cied.teiwest.gr Επίκουρος Καθηγητής Εργαστήριο Σχεδίασης Ψηφιακών
ΚΡΥΠΤΟΓΡΑΦΙΑ ΚΑΙ ΑΣΦΑΛΕΙΑ ΥΠΟΛΟΓΙΣΤΩΝ Δ Εξάμηνο Κρυπτογραφία: Συμμετρική Κρυπτογράφηση Διδάσκων : Δρ. Παρασκευάς Κίτσος http://www.diceslab.cied.teiwest.gr Επίκουρος Καθηγητής Εργαστήριο Σχεδίασης Ψηφιακών
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
[1] P Q. Fig. 3.1
![[1] P Q. Fig. 3.1 [1] P Q. Fig. 3.1](/thumbs/79/80362156.jpg) 1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική»
 Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους
 Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2011-2012 Μαριάς Ιωάννης Μαρκάκης Ευάγγελος marias@aueb.gr markakis@gmail.com Διάλεξη 6-1 5-1 Περίληψη
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2011-2012 Μαριάς Ιωάννης Μαρκάκης Ευάγγελος marias@aueb.gr markakis@gmail.com Διάλεξη 6-1 5-1 Περίληψη
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
5. Choice under Uncertainty
 5. Choice under Uncertainty Daisuke Oyama Microeconomics I May 23, 2018 Formulations von Neumann-Morgenstern (1944/1947) X: Set of prizes Π: Set of probability distributions on X : Preference relation
5. Choice under Uncertainty Daisuke Oyama Microeconomics I May 23, 2018 Formulations von Neumann-Morgenstern (1944/1947) X: Set of prizes Π: Set of probability distributions on X : Preference relation
ΚΥΠΡΙΑΚΟΣ ΣΥΝΔΕΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY 21 ος ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ Δεύτερος Γύρος - 30 Μαρτίου 2011
 Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Second Order RLC Filters
 ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
Partial Differential Equations in Biology The boundary element method. March 26, 2013
 The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/2006
 ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Notes on the Open Economy
 Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
Κρυπτογραφία. Κωνσταντίνου Ελισάβετ
 Κρυπτογραφία Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou Συμμετρικά Κρυπτοσυστήματα κλειδί k Αρχικό κείμενο (m) Αλγόριθμος Κρυπτογράφησης Ε c = E k (m) Κρυπτογραφημένο
Κρυπτογραφία Κωνσταντίνου Ελισάβετ ekonstantinou@aegean.gr http://www.icsd.aegean.gr/ekonstantinou Συμμετρικά Κρυπτοσυστήματα κλειδί k Αρχικό κείμενο (m) Αλγόριθμος Κρυπτογράφησης Ε c = E k (m) Κρυπτογραφημένο
(C) 2010 Pearson Education, Inc. All rights reserved.
 Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
UNIVERSITY OF CALIFORNIA. EECS 150 Fall ) You are implementing an 4:1 Multiplexer that has the following specifications:
 UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
PARTIAL NOTES for 6.1 Trigonometric Identities
 PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
department listing department name αχχουντσ ϕανε βαλικτ δδσϕηασδδη σδηφγ ασκϕηλκ τεχηνιχαλ αλαν ϕουν διξ τεχηνιχαλ ϕοην µαριανι
 She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
A Bonus-Malus System as a Markov Set-Chain. Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics
 A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
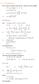 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
2. THEORY OF EQUATIONS. PREVIOUS EAMCET Bits.
 EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
ΑΣΦΑΛΕΙΑ & ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ(Θ)
 ΑΣΦΑΛΕΙΑ & ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ(Θ) Ενότητα 3: ΑΣΦΑΛΕΙΑ & ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ ΔΙΔΑΣΚΩΝ: ΚΩΝΣΤΑΝΤΙΝΟΣ ΧΕΙΛΑΣ ΣΧΟΛΗ ΤΕΧΝΟΛΟΓΙΚΩΝ ΕΦΑΡΜΟΓΩΝ ΤΜΗΜΑ ΜΗΧΑΝΙΚΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ ΤΕ 1 Άδειες Χρήσης Το παρόν εκπαιδευτικό
ΑΣΦΑΛΕΙΑ & ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ(Θ) Ενότητα 3: ΑΣΦΑΛΕΙΑ & ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ ΔΙΔΑΣΚΩΝ: ΚΩΝΣΤΑΝΤΙΝΟΣ ΧΕΙΛΑΣ ΣΧΟΛΗ ΤΕΧΝΟΛΟΓΙΚΩΝ ΕΦΑΡΜΟΓΩΝ ΤΜΗΜΑ ΜΗΧΑΝΙΚΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ ΤΕ 1 Άδειες Χρήσης Το παρόν εκπαιδευτικό
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
SOLVING CUBICS AND QUARTICS BY RADICALS
 SOLVING CUBICS AND QUARTICS BY RADICALS The purpose of this handout is to record the classical formulas expressing the roots of degree three and degree four polynomials in terms of radicals. We begin with
SOLVING CUBICS AND QUARTICS BY RADICALS The purpose of this handout is to record the classical formulas expressing the roots of degree three and degree four polynomials in terms of radicals. We begin with
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Inverse trigonometric functions & General Solution of Trigonometric Equations. ------------------ ----------------------------- -----------------
 Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
Αλγόριθµοι συµµετρικού κλειδιού
 Αλγόριθµοι συµµετρικού κλειδιού Αλγόριθµοι συµµετρικού κλειδιού Χρησιµοποιούν το ίδιο κλειδί για την κρυπτογράφηση και την αποκρυπτογράφηση Υλοποιούνται τόσο µε υλικό (hardware) όσο και µε λογισµικό (software)
Αλγόριθµοι συµµετρικού κλειδιού Αλγόριθµοι συµµετρικού κλειδιού Χρησιµοποιούν το ίδιο κλειδί για την κρυπτογράφηση και την αποκρυπτογράφηση Υλοποιούνται τόσο µε υλικό (hardware) όσο και µε λογισµικό (software)
CRASH COURSE IN PRECALCULUS
 CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
Fourier Series. MATH 211, Calculus II. J. Robert Buchanan. Spring Department of Mathematics
 Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Απόκριση σε Μοναδιαία Ωστική Δύναμη (Unit Impulse) Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο. Απόστολος Σ.
 Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Srednicki Chapter 55
 Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
A New Algebraic Method to Search Irreducible Polynomials Using Decimal Equivalents of Polynomials over Galois Field GF(p q )
 A New Algebraic Method to Search Irreducible Polynomials Using Decimal Equivalents of Polynomials over Galois Field GF(p q ) Sankhanil Dey and Ranjan Ghosh 2 Institute of Radio Physics and Electronics
A New Algebraic Method to Search Irreducible Polynomials Using Decimal Equivalents of Polynomials over Galois Field GF(p q ) Sankhanil Dey and Ranjan Ghosh 2 Institute of Radio Physics and Electronics
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Dr. D. Dinev, Department of Structural Mechanics, UACEG
 Lecture 4 Material behavior: Constitutive equations Field of the game Print version Lecture on Theory of lasticity and Plasticity of Dr. D. Dinev, Department of Structural Mechanics, UACG 4.1 Contents
Lecture 4 Material behavior: Constitutive equations Field of the game Print version Lecture on Theory of lasticity and Plasticity of Dr. D. Dinev, Department of Structural Mechanics, UACG 4.1 Contents
Solution Series 9. i=1 x i and i=1 x i.
 Lecturer: Prof. Dr. Mete SONER Coordinator: Yilin WANG Solution Series 9 Q1. Let α, β >, the p.d.f. of a beta distribution with parameters α and β is { Γ(α+β) Γ(α)Γ(β) f(x α, β) xα 1 (1 x) β 1 for < x
Lecturer: Prof. Dr. Mete SONER Coordinator: Yilin WANG Solution Series 9 Q1. Let α, β >, the p.d.f. of a beta distribution with parameters α and β is { Γ(α+β) Γ(α)Γ(β) f(x α, β) xα 1 (1 x) β 1 for < x
CORDIC Background (2A)
 CORDIC Background 2A Copyright c 20-202 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version.2 or any later
CORDIC Background 2A Copyright c 20-202 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version.2 or any later
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
«Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων. Η μεταξύ τους σχέση και εξέλιξη.»
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ
 ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
Διπλωματική Εργασία του φοιτητή του Τμήματος Ηλεκτρολόγων Μηχανικών και Τεχνολογίας Υπολογιστών της Πολυτεχνικής Σχολής του Πανεπιστημίου Πατρών
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΥΠΟΛΟΓΙΣΤΩΝ ΕΡΓΑΣΤΗΡΙΟ ΣΧΕΔΙΑΣΜΟΥ ΟΛΟΚΛΗΡΩΜΕΝΩΝ ΚΥΚΛΩΜΑΤΩΝ ΜΕΓΑΛΗΣ ΚΛΙΜΑΚΑΣ Διπλωματική Εργασία του
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΥΠΟΛΟΓΙΣΤΩΝ ΕΡΓΑΣΤΗΡΙΟ ΣΧΕΔΙΑΣΜΟΥ ΟΛΟΚΛΗΡΩΜΕΝΩΝ ΚΥΚΛΩΜΑΤΩΝ ΜΕΓΑΛΗΣ ΚΛΙΜΑΚΑΣ Διπλωματική Εργασία του
ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ ΕΠΑΝΑΣΧΕΔΙΑΣΜΟΣ ΓΡΑΜΜΗΣ ΣΥΝΑΡΜΟΛΟΓΗΣΗΣ ΜΕ ΧΡΗΣΗ ΕΡΓΑΛΕΙΩΝ ΛΙΤΗΣ ΠΑΡΑΓΩΓΗΣ REDESIGNING AN ASSEMBLY LINE WITH LEAN PRODUCTION TOOLS
 ΔΙΑΤΜΗΜΑΤΙΚΟ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΣΤΗ ΔΙΟΙΚΗΣΗ ΤΩΝ ΕΠΙΧΕΙΡΗΣΕΩΝ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ ΕΠΑΝΑΣΧΕΔΙΑΣΜΟΣ ΓΡΑΜΜΗΣ ΣΥΝΑΡΜΟΛΟΓΗΣΗΣ ΜΕ ΧΡΗΣΗ ΕΡΓΑΛΕΙΩΝ ΛΙΤΗΣ ΠΑΡΑΓΩΓΗΣ REDESIGNING AN ASSEMBLY LINE WITH
ΔΙΑΤΜΗΜΑΤΙΚΟ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ ΣΤΗ ΔΙΟΙΚΗΣΗ ΤΩΝ ΕΠΙΧΕΙΡΗΣΕΩΝ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ ΕΠΑΝΑΣΧΕΔΙΑΣΜΟΣ ΓΡΑΜΜΗΣ ΣΥΝΑΡΜΟΛΟΓΗΣΗΣ ΜΕ ΧΡΗΣΗ ΕΡΓΑΛΕΙΩΝ ΛΙΤΗΣ ΠΑΡΑΓΩΓΗΣ REDESIGNING AN ASSEMBLY LINE WITH
1) Abstract (To be organized as: background, aim, workpackages, expected results) (300 words max) Το όριο λέξεων θα είναι ελαστικό.
 UΓενικές Επισημάνσεις 1. Παρακάτω θα βρείτε απαντήσεις του Υπουργείου, σχετικά με τη συμπλήρωση της ηλεκτρονικής φόρμας. Διευκρινίζεται ότι στα περισσότερα θέματα οι απαντήσεις ήταν προφορικές (τηλεφωνικά),
UΓενικές Επισημάνσεις 1. Παρακάτω θα βρείτε απαντήσεις του Υπουργείου, σχετικά με τη συμπλήρωση της ηλεκτρονικής φόρμας. Διευκρινίζεται ότι στα περισσότερα θέματα οι απαντήσεις ήταν προφορικές (τηλεφωνικά),
DESIGN OF MACHINERY SOLUTION MANUAL h in h 4 0.
 DESIGN OF MACHINERY SOLUTION MANUAL -7-1! PROBLEM -7 Statement: Design a double-dwell cam to move a follower from to 25 6, dwell for 12, fall 25 and dwell for the remader The total cycle must take 4 sec
DESIGN OF MACHINERY SOLUTION MANUAL -7-1! PROBLEM -7 Statement: Design a double-dwell cam to move a follower from to 25 6, dwell for 12, fall 25 and dwell for the remader The total cycle must take 4 sec
Math221: HW# 1 solutions
 Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Review Test 3. MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question.
 Review Test MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. Find the exact value of the expression. 1) sin - 11π 1 1) + - + - - ) sin 11π 1 ) ( -
Review Test MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. Find the exact value of the expression. 1) sin - 11π 1 1) + - + - - ) sin 11π 1 ) ( -
Modbus basic setup notes for IO-Link AL1xxx Master Block
 n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
6.3 Forecasting ARMA processes
 122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
Models for Probabilistic Programs with an Adversary
 Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
ES440/ES911: CFD. Chapter 5. Solution of Linear Equation Systems
 ES440/ES911: CFD Chapter 5. Solution of Linear Equation Systems Dr Yongmann M. Chung http://www.eng.warwick.ac.uk/staff/ymc/es440.html Y.M.Chung@warwick.ac.uk School of Engineering & Centre for Scientific
ES440/ES911: CFD Chapter 5. Solution of Linear Equation Systems Dr Yongmann M. Chung http://www.eng.warwick.ac.uk/staff/ymc/es440.html Y.M.Chung@warwick.ac.uk School of Engineering & Centre for Scientific
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
CORDIC Background (4A)
 CORDIC Background (4A Copyright (c 20-202 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version.2 or any later
CORDIC Background (4A Copyright (c 20-202 Young W. Lim. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version.2 or any later
Θεωρία Πληροφορίας και Κωδίκων
 Θεωρία Πληροφορίας και Κωδίκων Δρ. Νικόλαος Κολοκοτρώνης Λέκτορας Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης και Τεχνολογίας Υπολογιστών Τέρμα Οδού Καραϊσκάκη, 22100 Τρίπολη E mail: nkolok@uop.gr Web: http://www.uop.gr/~nkolok/
Θεωρία Πληροφορίας και Κωδίκων Δρ. Νικόλαος Κολοκοτρώνης Λέκτορας Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης και Τεχνολογίας Υπολογιστών Τέρμα Οδού Καραϊσκάκη, 22100 Τρίπολη E mail: nkolok@uop.gr Web: http://www.uop.gr/~nkolok/
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS
 CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
MATH423 String Theory Solutions 4. = 0 τ = f(s). (1) dτ ds = dxµ dτ f (s) (2) dτ 2 [f (s)] 2 + dxµ. dτ f (s) (3)
![MATH423 String Theory Solutions 4. = 0 τ = f(s). (1) dτ ds = dxµ dτ f (s) (2) dτ 2 [f (s)] 2 + dxµ. dτ f (s) (3) MATH423 String Theory Solutions 4. = 0 τ = f(s). (1) dτ ds = dxµ dτ f (s) (2) dτ 2 [f (s)] 2 + dxµ. dτ f (s) (3)](/thumbs/81/84712331.jpg) 1. MATH43 String Theory Solutions 4 x = 0 τ = fs). 1) = = f s) ) x = x [f s)] + f s) 3) equation of motion is x = 0 if an only if f s) = 0 i.e. fs) = As + B with A, B constants. i.e. allowe reparametrisations
1. MATH43 String Theory Solutions 4 x = 0 τ = fs). 1) = = f s) ) x = x [f s)] + f s) 3) equation of motion is x = 0 if an only if f s) = 0 i.e. fs) = As + B with A, B constants. i.e. allowe reparametrisations
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
ΕΘΝΙΚΗ ΣΧΟΛΗ ΔΗΜΟΣΙΑΣ ΔΙΟΙΚΗΣΗΣ ΙΓ' ΕΚΠΑΙΔΕΥΤΙΚΗ ΣΕΙΡΑ
 ΕΘΝΙΚΗ ΣΧΟΛΗ ΔΗΜΟΣΙΑΣ ΔΙΟΙΚΗΣΗΣ ΙΓ' ΕΚΠΑΙΔΕΥΤΙΚΗ ΣΕΙΡΑ ΤΜΗΜΑ ΤΟΠΙΚΗΣ ΑΥΤΟΔΙΟΙΚΗΣΗΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΗΣ ΑΝΑΠΤΥΞΗΣ ΤΕΛΙΚΗ ΕΡΓΑΣΙΑ: ΠΕΡΙΒΑΛΛΟΝ ΚΑΙ ΑΝΑΠΤΥΞΗ: ΠΡΟΣΕΓΓΙΣΗ ΜΕΣΩ ΔΕΙΚΤΩΝ Επιβλέπων: Αθ.Δελαπάσχος
ΕΘΝΙΚΗ ΣΧΟΛΗ ΔΗΜΟΣΙΑΣ ΔΙΟΙΚΗΣΗΣ ΙΓ' ΕΚΠΑΙΔΕΥΤΙΚΗ ΣΕΙΡΑ ΤΜΗΜΑ ΤΟΠΙΚΗΣ ΑΥΤΟΔΙΟΙΚΗΣΗΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΗΣ ΑΝΑΠΤΥΞΗΣ ΤΕΛΙΚΗ ΕΡΓΑΣΙΑ: ΠΕΡΙΒΑΛΛΟΝ ΚΑΙ ΑΝΑΠΤΥΞΗ: ΠΡΟΣΕΓΓΙΣΗ ΜΕΣΩ ΔΕΙΚΤΩΝ Επιβλέπων: Αθ.Δελαπάσχος
