Γηαρείξηζε δηθηύσλ SNMP
|
|
|
- Σπύρος Δουρέντης
- 9 χρόνια πριν
- Προβολές:
Transcript
1 Γηαρείξηζε δηθηύσλ SNMP
2 SNMP: Simple Network Management Protocol Δίλαη έλα de facto Internet standard (βαζηζκέλν ζε RFCs). Τα δεδνκέλα πνπ δηαρεηξίδεηαη ην SNMP αλαπαξηζηώληαη ζε έλα δέληξν, ην ΜΙΒ (Management Information Base). Tα θξηηήξηα ζρεδηαζκνύ ήηαλ: Simple. Lightweight. Low-bandwidth. Φξεζηκνπνίεζε TCP/IP πξσηνθόιισλ (επίπεδα 3 θαη 4).
3 SNMP Simple Network Management Protocol Doesn't SNMP solve all these problems? Don't be silly!
4 SNMP Where did it come from? Internet Engineering Task Force» Network Management Area SNMP V1 MIB definitions SNMPV2
5 What is it? more than just a protocol It defines an architecture for extracting information from the network regarding the current operational state of the network, using a vendor-independent family of mechanisms
6 Structure of Management Information (SMI) identifies and defines structure of management information RFC1155 defines commonly defined data item syntax of the data type semantics of the data object
7 Syntax uses ASN.1 (Abstract Syntax Notation) binary encoding is a 1 byte integer, value 6 Primitive Types INTEGER, OCTECT STRING, OBJECT IDENTIFIER, NULL Constructor Types SEQUENCE <primitive-type>... SEQUENCE OF <primitive-type>... ie. a record ie. an array
8 Syntax Defined Data Types IpAddress Counter Gauge TimeTicks what you expect non-negative integer that wraps non-negative integer that latches time in hundredths of seconds
9 SNMP NAMES SNMP Name Structure 1 - iso 3 - org 6 - dod 1 - Internet 1 - directory 2 - mgmt 3 - expt 4 - private 1 - mib 1 - Enterprise 1 - system 2 - interfaces 9 - cisco 1 - sysdescr 2 - sysobjectid 1 - iftable 1 - ifentry 1 - ifindex 2 - ifdescr 3 - iftype ifinoctets
10 SNMP Management Information Base (MIB) "database"of network objects Groups:» System, Interfaces, Address Translation, IP, ICMP, TCP, UDP, EGP "Access" and "Status" attributes actual variables are "instances" of OIDs sysdescr ifinoctets for interface iproutenexthop for network
11 SNMP The SNMP protocol itself allows inspection and alteration of MIB variables UDP Based not acknowledged transactions PUT, GET, GET-NEXT operators
12 SNMP SNMP Traps unsolicited notification of events can include variable list ColdStart, WarmStart LinkUp, LinkDown Authentication Failure EGP Neighbour Loss Enterprise Specific
13 Network Management Software SNMP Agents provided by all router vendors many expanded (enterprise) MIBs bridges, wiring concentrators, toasters
14 Network Management Software Public Domain Application Programming Interfaces available from CMU and MIT include variety of applications
15 Network Management Software Commercially many offerings, UNIX and PC based» HP OpenView» SunNet Manager» Cabletron Spectrum» *MANY* others
16 Does it: Choosing a Management Platform a) Support your systems? b) Run on your platforms? c) Meet your requirements? d) Match your resources?
17 Choosing a Management Platform Maybe you can get away with something quick and dirty using existing tools Maybe a commercial management product will meet your operational requirements
18 SNMP Tutorial
19 Tutorial Overview Introduction Management Information Base (MIB) Simple Network Management Protocol (SNMP) SNMP Commands Tools - SNMPwalk (CLI) - MIB Browser (GUI)
20 Introduction SNMP Simple Network Management Protocol is an application layer protocol that facilitates the exchange of management information between network devices - Application-layer protocol for managing TCP/IP based networks. - Runs over UDP, which runs over IP using Port 161 and Two versions of SNMP exist: SNMP version 1 (SNMPv1) and SNMP version 2 (SNMPv2).
21 Basic tasks that fall under this category are Configuration Management Keeping track of device setting Fault Management -Dealing with problems and emergencies in the network i.e. server, router Performance Management
22 Network Management Success factors The management interface must be Standardized Extendable Portable The management mechanism must be In expensive
23 Major functions Configuration Management - inventory, configuration, provisioning Fault Management - reactive and proactive network fault management Performance Management - # of packets dropped, timeouts, collisions, CRC errors Security Management - SNMP doesn t provide much here Accounting Management - cost management and chargeback assessment Asset Management - statistics of equipment, facility, and administration personnel Planning Management - analysis of trends to help justify a network upgrade or bandwidth increase
24 History TCP/IP replaces ARPANET at U.S. Dept. of Defense, effective birth of Internet First model for net management - HEMS - High-Level Entity Management System (RFCs 1021,1022,1024,1076) ISO OSI proposes CMIP - Common Management Information Protocol, and CMOT (CMIP over TCP) for the actual network management protocol for use on the internet Nov SGMP - Simple Gateway Monitoring protocol (RFC 1028) Marshall T. Rose heads up SNMP working group to create a common network management framework to be used by both SGMP and CMOT to allow for transition to CMOT Aug Internet-standard Network Management Framework defined (RFCs 1065, 1066, 1067) Apr SNMP promoted to recommended status as the de facto TCP/IP network management framework (RFC 1098) June IAB committee decides to let SNMP and CMOT develop separately May IAB promotes SNMP to a standard protocol with a recommended status (RFC 1157) Mar format of MIBs and traps defined (RFCs 1212, 1215) TCP/IP MIB definition revised to create SNMPv1 (RFC 1213)
25 SNMP & OSI model 7 Application Layer Management and Agent APIs SNMP 6 Presentation Layer ASN.1 and BER 5 Session Layer RPC and NetBIOS 4 Transport Layer TCP and UDP 3 Network Layer IP and IPX 2 Data Link Layer Ethernet, Token Ring, FDDI 1 Physical Layer
26 Port & UDP SNMP uses User Datagram Protocol (UDP) as the transport mechanism for SNMP messages Ethernet Frame IP Packet UDP Datagram SNMP Message CRC Like FTP, SNMP uses two well-known ports to operate: UDP Port SNMP Messages UDP Port SNMP Trap Messages
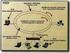
27 SNMP Components An SNMP-managed network consists of three key components: managed devices, agents, and network-management systems (NMSs).
28 SNMP components A managed device is a network node that contains an SNMP agent and that resides on a managed network. Managed devices collect and store management information and make this information available to NMSs using SNMP. Managed devices, sometimes called network elements, can be routers and access servers, switches and bridges, hubs, computer hosts, or printers. An agent is a network-management software module that resides in a managed device. An agent has local knowledge of management information and translates that information into a form compatible with SNMP. An NMS executes applications that monitor and control managed devices. NMSs provide the bulk of the processing and memory resources required for network management. One or more NMSs must exist on any managed network.
29
30 Basic Command Managed devices are monitored and controlled using four basic SNMP commands: read, write, trap, and traversal operations. The read command is used by an NMS to monitor managed devices. The NMS examines different variables that are maintained by managed devices. The write command is used by an NMS to control managed devices. The NMS changes the values of variables stored within managed devices. The trap command is used by managed devices to asynchronously report events to the NMS. When certain types of events occur, a managed device sends a trap to the NMS. Traversal operations are used by the NMS to determine which variables a managed device supports and to sequentially gather information in variable tables, such as a routing table.
31 Language of SNMP Structure of Management Information (SMI) specifies the format used for defining managed objects that are accessed via the SNMP protocol Abstract Syntax Notation One (ASN.1) used to define the format of SNMP messages and managed objects (MIB modules) using an unambiguous data description format Basic Encoding Rules (BER) used to encode the SNMP messages into a format suitable for transmission across a network
32 Abstract Syntax Notation One ASN.1 is nothing more than a language definition. It is similar to C/C++ and other programming languages. Syntax examples: -- two dashes is a comment -- The C equivalent is written in the comment MostSevereAlarm ::= INTEGER -- typedef MostSevereAlarm int; circuitalarms MostSevereAlarm ::= 3 -- MostSevereAlarm circuitalarms = 3; MostSevereAlarm ::= INTEGER (1..5) -- specify a valid range ErrorCounts ::= SEQUENCE { circuitid erroredseconds OCTET STRING, INTEGER, unavailableseconds INTEGER } -- data structures are defined using the SEQUENCE keyword
33 Simple Data Types INTEGER -- signed 32-bit integer OCTET STRING OBJECT IDENTIFIER (OID) NULL -- not actually data type, but data value IpAddress -- OCTET STRING of size 4, in network byte order (B.E.) Counter -- unsigned 32-bit integer (rolls over) Gauge -- unsigned 32-bit integer (will top out and stay there) TimeTicks -- unsigned 32-bit integer (rolls over after 497 days) Opaque -- used to create new data types not in SNMPv1 RED items defined by ASN.1 Blue items defined by RFC 1155 DateAndTime, DisplayString, MacAddress, PhysAddress, TimeInterval, TimeStamp, TruthValue, VariablePointer -- textual conventions used as types
34 SNMP overview: 4 key parts Management information base (MIB): distributed information store of network management data Structure of Management Information (SMI): data definition language for MIB objects SNMP protocol convey manager<->managed object info, commands security, administration capabilities major addition in SNMPv3
35 MIB Management Information Base (MIB) is a collection of information that is organized hierarchically. MIBs are accessed using a network-management protocol such as SNMP. They are comprised of managed objects and are identified by object identifiers.
36 Two types of managed objects exist: scalar and tabular Scalar objects define a single object instance. Tabular objects define multiple related object instances that are grouped in MIB tables.
37 Always defined and referenced within the context of a MIB A typical MIB variable definition: syscontact OBJECT-TYPE -- OBJECT-TYPE is a macro SYNTAX DisplayString (SIZE (0..255)) ACCESS read-write -- or read-write, write-only, notaccessible STATUS mandatory -- or optional, deprecated, obsolete DESCRIPTION CEPN1331 Computer Network ::= { system 4 }
38 MIB Management Information Base MIB Breakdown - OBJECT-TYPE - String that describes the MIB object. - Object IDentifier (OID). - SYNTAX - Defines what kind of info is stored in the MIB object. - ACCESS - READ-ONLY, READ-WRITE. - STATUS - State of object in regards the SNMP community. - DESCRIPTION - Reason why the MIB object exists. Standard MIB Object: sysuptime OBJECT-TYPE SYNTAX Time-Ticks ACCESS read-only STATUS mandatory DESCRIPTION Time since the network management portion of the system was last reinitialised. ::= {system 3}
39 MIB Management Information Base Object IDentifier (OID) - Example iso(1) org(3) dod(6) internet(1) mgmt(2) mib-2(1) system(1) Note: ~100% present. - mgmt and private most common. - MIB-2 successor to original MIB. - STATUS mandatory, All or nothing in group 1 directory(1) system(1) iso(1) org(3) dod(6) 6 1 mgmt(2) 2 3 internet(1) private(4) mib-2(1) experimental(3) interfaces(2) ip(4) tcp(6)
40
41 MIB Management Information Base system(1) group - Contains objects that describe some basic information on an entity. - An entity can be the agent itself or the network object that the agent is on. 1 system(1) 2 1 mib-2(1) interfaces(2) system(1) group objects - sysdescr(1) Description of the entity. - sysobjectid(2) Vendor defined OID string. - sysuptime(3) Time since net-mgt was last re-initialised. - syscontact(4) Name of person responsible for the entity.
42 MIB Management Information Base MIB - tree view MIB - syntax view 1 sysdesc(1) 2 1 system(1) sysobjectid(2) mib-2(1) sysuptime OBJECT-TYPE SYNTAX INTEGER ACCESS read-only STATUS mandatory DESCRIPTION The time (in hundredths of a second) since the network management portion of the system was last resyscontact(3) sysuptime(3)
43 MIB Management Information Base SNMP Instances - Each MIB object can have an instance. - A MIB for a router s (entity) interface information iso(1) org(3) dod(6) internet(1) mgmt(2) mib-2(1) interfaces(2) iftable(2) ifentry(1) iftype(3) - Require one iftype value per interface (e.g. 3) - One MIB object definition can represent multiple instances through Tables, Entries, and Indexes.
44 MIB Management Information Base Tables, Entries, and Indexes. - Imagine tables as spreadsheets - Three interface types require 3 rows (index no.s) - Each column represents a MIB object, as defined by the entry node. ENTRY + INDEX = INSTANCE iftype(3) ifmtu(4) Etc Index #1 Index #2 Index #3 iftype.1[6] iftype.2:[9] iftype.3:[15] ifmtu.1 ifmtu.2 ifmtu.3
45 Simple Network Management Protocol Retrieval protocol for MIB. Can retrieve by - CLI (snmpwalk), - GUI (MIB Browser), or - Larger applications (Sun Net Manager) called Network Management Software (NMS). NMS collection of smaller applications to manage network with illustrations, graphs, etc. NMS run on Network Management Stations (also NMS), which can run several different NMS software applications.
46 SMI: data definition language Purpose: syntax, semantics of management data well-defined, unambiguous base data types: straightforward, boring OBJECT-TYPE data type, status, semantics of managed object MODULE-IDENTITY groups related objects into MIB module Basic Data Types INTEGER Integer32 Unsigned32 OCTET STRING OBJECT IDENTIFIED IPaddress Counter32 Counter64 Guage32 Time Ticks Opaque
47 SNMP MIB MIB module specified via SMI MODULE-IDENTITY (100 standardized MIBs, more vendor-specific) MODULE OBJECT TYPE: OBJECT TYPE: OBJECT TYPE: objects specified via SMI OBJECT-TYPE construct
48 SMI: Object, module examples OBJECT-TYPE: ipindelivers ipindelivers OBJECT TYPE SYNTAX Counter32 MAX-ACCESS read-only STATUS current DESCRIPTION The total number of input datagrams successfully delivered to IP userprotocols (including ICMP) ::= { ip 9} MODULE-IDENTITY: ipmib ipmib MODULE-IDENTITY LAST-UPDATED Z ORGANZATION IETF SNPv2 Working Group CONTACT-INFO Keith McCloghrie DESCRIPTION The MIB module for managing IP and ICMP implementations, but excluding their management of IP routes. REVISION Z ::= {mib-2 48}
49 MIB example: UDP module Object ID Name Type Comments UDPInDatagrams Counter32 total # datagrams delivered at this node UDPNoPorts Counter32 # underliverable datagrams no app at portl UDInErrors Counter32 # undeliverable datagrams all other reasons UDPOutDatagrams Counter32 # datagrams sent udptable SEQUENCE one entry for each port in use by app, gives port # and IP address
50 SNMP Naming question: how to name every possible standard object (protocol, data, more..) in every possible network standard?? answer: ISO Object Identifier tree: hierarchical naming of all objects each branchpoint has name, number ISO ISO-ident. Org. US DoD Internet udpindatagrams UDP MIB2 management
51 OSI Object Identifier Tree Check out
52 SNMP protocol Two ways to convey MIB info, commands: request managing entity response agent data managing entity trap msg agent data Managed device request/response mode Managed device trap mode
53 SNMP protocol: message types Message type GetRequest GetNextRequest GetBulkRequest InformRequest SetRequest Response Trap Function Mgr-to-agent: get me data (instance,next in list, block) Mgr-to-Mgr: here s MIB value Mgr-to-agent: set MIB value Agent-to-mgr: value, response to Request Agent-to-mgr: inform manager of exceptional event
54 SNMP protocol: message formats
55 SNMP security and administration encryption: DES-encrypt SNMP message authentication: compute, send MIC(m,k): compute hash (MIC) over message (m), secret shared key (k) protection against playback: use nonce view-based access control SNMP entity maintains database of access rights, policies for various users database itself accessible as managed object!
56 SNMP Commands SNMP has 5 different functions referred to as Protocol Data Units (PDU s), which are: (1) GetRequest, aka Get (2) GetNextRequest, aka GetNext (3) GetResponse, aka Response (4) SetRequest, aka Set (5) Trap
57 SNMP Commands [Get] GetRequest [Get] - Most common PDU. - Used to ask SNMP agent for value of a particular MIB agent. - NMS sends out 1 Get PDU for each instance, which is a unique OID string. - What happens if you don t know how many instances of a MIB object exist?
58 SNMP Commands [GetNext] GetNextRequest [GetNext] - NMS application uses GetNext to walk down a table within a MIB. - Designed to ask for the OID and value of the MIB instance that comes after the one asked for. - Once the agent responds the NMS application can increment its count and generate a GetNext. - This can continue until the NMS application detects that the OID has changed, i.e. it has reached the end of the table.
59 SNMP Commands [GetResponse] GetResponse [Response] - Simply a response to a Get, GetNext or Set. - SNMP agent responds to all requests or commands via this PDU.
60 SNMP Commands [SetRequest] SetRequest [Set] - Issued by an NMS application to change a MIB instance to the variable within the Set PDU. - For example, you could issue a - GetRequest against a KDEG server asking for syslocation.0 and may get ORI as the response. - Then, if the server was moved, you could issue a Set against that KDEG server to change its location to INS. - You must have the correct permissions when using the set PDU.
61 SNMP Commands [Trap] Trap - Asynchronous notification. - SNMP agents can be programmed to send a trap when a certain set of circumstances arise. - Circumstances can be view as thresholds, i.e. a trap may be sent when the temperature of the core breaches a predefined level.
62 SNMP Security SNMP Community Strings (like passwords) - 3 kinds: - READ-ONLY: You can send out a Get & GetNext to the SNMP agent, and if the agent is using the same read-only string it will process the request. - READ-WRITE: Get, GetNext, and Set. If a MIB object has an ACCESS value of read-write, then a Set PDU can change the value of that object with the correct read-write community string. - TRAP: Allows administrators to cluster network entities into communities. Fairly redundant.
63 SNMP Tools Command Line Interface e.g. snmpwalk Graphical User Interface e.g. ireasoning s MIB Browser» Or via
64 SNMP MIB Browser (1) Initial set-up... java -Xmx384m -jar XYZ\lib\browser.jar (where XYZ = your specific path) Breakdown - LHS is the SNMP MIB structure. - Lower LHS has details of MIB structure. - RHS will present MIB values.
65 SNMP MIB Browser (2) Discovery - Subnet: 134.XXX.XXX.* - Read Community: public Start Note IP Address. Stop
66 SNMP MIB Browser (3) Navigation - MIB Tree System sysuptime -Notice Lower LHS - Notice OID
67 SNMP MIB Browser (4) SNMP PDU s (1) Get - Select Go Get - RHS has values. - OID Value
68 SNMP MIB Browser (5) SNMP PDU s (2) GetNext -Selected OID is: Returned value: ( ) or DSG, O Reilly Institute, F.35
69 SNMP MIB Browser (6) SNMP (3) Get SubTree -Position of MIB: (a.k.a. system) -RHS values: Returns all values below system.
70 SNMP MIB Browser (7) SNMP (4) Walk -MIB Location: (a.k.a. mib-2) - Returns *ALL* values under mib-2
71 SNMP MIB Browser (8) Tables - MIB Location: (or interfaces) - Select iftable, Go, then Table View. - Refresh/Poll
72 SNMP MIB Browser (9) SNMP - Graph - Select a value from the RHS, say sysuptime - Highlight and select Go, then Graph. - Interval = 1s set.
73 The presentation problem Q: does perfect memory-to-memory copy solve the communication problem? A: not always! struct { char code; int x; } test; test.x = 256; test.code= a test.code test.x a host 1 format test.code test.x a host 2 format problem: different data format, storage conventions
74 A real-life presentation problem: grandma 2004 teenager aging 60 s hippie
75 Presentation problem: potential solutions 1. Sender learns receiver s format. Sender translates into receiver s format. Sender sends. real-world analogy? pros and cons? 2. Sender sends. Receiver learns sender s format. Receiver translate into receiver-local format real-world-analogy pros and cons? 3. Sender translates host-independent format. Sends. Receiver translates to receiver-local format. real-world analogy? pros and cons?
76 Solving the presentation problem 1. Translate local-host format to host-independent format 2. Transmit data in host-independent format 3. Translate host-independent format to remote-host format grandma aging 60 s hippie 2004 teenager
77 ASN.1: Abstract Syntax Notation 1 ISO standard X.680 used extensively in Internet like eating vegetables, knowing this good for you! defined data types, object constructors like SMI BER: Basic Encoding Rules specify how ASN.1-defined data objects to be transmitted each transmitted object has Type, Length, Value (TLV) encoding
78 TLV Encoding Idea: transmitted data is self-identifying T: data type, one of ASN.1-defined types L: length of data in bytes V: value of data, encoded according to ASN.1 standard Tag Value Type Boolean Integer Bitstring Octet string Null Object Identifier Real
79 TLV encoding: example Value, 259 Length, 2 bytes Type=2, integer Value, 5 octets (chars) Length, 5 bytes Type=4, octet string
80 Network Management: summary network management extremely important: 80% of network cost ASN.1 for data description SNMP protocol as a tool for conveying information Network management: more art than science what to measure/monitor how to respond to failures? alarm correlation/filtering?
81 Network Management and Security Outline Basic Concepts of SNMP SNMPv1 Community Facility SNMPv3
82 Basic Concepts of SNMP An integrated collection of tools for network monitoring and control. Single operator interface Minimal amount of separate equipment. Software and network communications capability built into the existing equipment SNMP key elements: Management station Managament agent Management information base Network Management protocol» Get, Set and Notify
83 Protocol context of SNMP
84 Proxy Configuration
85
86 SNMP v1 and v2 Trap an unsolicited message (reporting an alarm condition) SNMPv1 is connectionless since it utilizes UDP (rather than TCP) as the transport layer protocol. SNMPv2 allows the use of TCP for reliable, connection-oriented service.
87 Comparison of SNMPv1 and SNMPv2 SNMPv1 PDU SNMPv2 PDU Direction Description GetRequest GetRequest Manager to agent Request value for each listed object GetRequest GetRequest Manager to agent Request next value for each listed object GetBulkRequest Manager to agent Request multiple values SetRequest SetRequest Manager to agent Set value for each listed object InformRequest Manager to manager GetResponse Response Agent to manager or Manage to manager(snmpv2) Transmit unsolicited information Respond to manager request Trap SNMPv2-Trap Agent to manager Transmit unsolicited information
88 SNMPv1 Community Facility SNMP Community Relationship between an SNMP agent and SNMP managers. Three aspect of agent control: Authentication service» Access to MIB is restricted to authorised managers Access policy» Different access rights to different managers Proxy service» The agent as a broker for other agents
89 Access policy (Πνιηηηθή πξόζβαζεο) Με ηνλ θαζνξηζκό κηαο θνηλόηεηαο ν πξάθηνξαο πεξηνξίδεη ηελ πξόζβαζε ζηε βάζε ΜΙΒ Διεγρνο πξόζβαζεο: Πξνβνιή SNMP MIB: έλα ππνζύλνιν από αληηθείκελα κέζα ζε κηα ΜΙΒ. Μπνξνύλ λα νξηζηνύλ δηαθνξεηηθέο πξνβνιέο. Τν ζύλνιν αληηθεηκέλσλ ηεο πξνβνιήο δε ρξεηάδεηαη λα αλήθεη ζε ελα κόλν ππνδέλδξν ηεο ΜΙΒ Καηάζηαζε πξόζβαζεο SNMP: έλα ζηνηρείην από ην ζύλνιν {READ-ONLY, READ-WRITE}. Οξίδεηαη κηα θαηάζηαζε πξόζβαζεο γηα θάζε θνηλόηεηα. Πξνθίι θνηλόηεηαο SNMP (SNMP community profile)
90 SNMPv1 Administrative Concepts
91 SNMPv3 SNMPv3 defines a security capability to be used in conjunction with SNMPv1 or v2 User security model USM
92 Traditional SNMP Manager
93 Traditional SNMP Agent
94
95 SNMPv3 Flow
96 SNMP3 Message Format with USM
97 User Security Model (USM) Designed to secure against: Modification of information (Τξνπνπνίεζε πιεξνθνξηώλ) Masquerade (Μεηακθίεζε) Message stream modification (Τξνπνπνίεζε ξνήο κελπκάησλ) Disclosure (Απνθάιπςε) Not intended to secure against: Denial of Service (DoS attack) (Αξλεζε παξνρήο ππεξεζηώλ) Traffic analysis (Αλάιπζε θίλεζεο)
98 Key Localization Process
99 View-Based Access Control Model (VACM) VACM has two characteristics: Determines whether access to a managed object should be allowed. Make use of an MIB that:» Defines the access control policy for this agent.» Makes it possible for remote configuration to be used.
100 Access control decision
101 Network security Intruders and Viruses
102 Outline Intruders Intrusion Techniques Password Protection Password Selection Strategies Intrusion Detection Viruses and Related Threats Malicious Programs The Nature of Viruses Antivirus Approaches Advanced Antivirus Techniques
103 Intruders Three classes of intruders (hackers or crackers): Masquerader (κεηακθηεζκέλνο) Misfeasor (παξάλνκνο) Clandestine user (θξπθόο ρξήζηεο)
104 Intrusion Techniques System maintain a file that associates a password with each authorized user. Password file can be protected with: One-way encryption (κνλόδξνκε θξππηνγξάθεζε: απνζήθεπζε θξππηνγξαθεκέλεο κνξθήο ζπλζεκαηηθνύ ρξήζηε) Access Control (έιεγρνο πξόζβαζεο ζην αξρείν ζπλζεκαηηθώλ)
105 Intrusion Techniques Techniques for guessing passwords: Try default passwords. Try all short words, 1 to 3 characters long. Try all the words in an electronic dictionary(60,000). Collect information about the user s hobbies, family names, birthday, etc. Try user s phone number, social security number, street address, etc. Try all license plate numbers (MUP103). Use a Trojan horse Tap the line between a remote user and the host system. Prevention: Enforce good password selection (Ij4Gf4Se%f#)
106 UNIX Password Scheme Loading a new password
107 UNIX Password Scheme Verifying a password file
108 Storing UNIX Passwords UNIX passwords were kept in a publicly readable file, etc/passwords. Now they are kept in a shadow directory and only visible by root.
109 Salt The salt serves three purposes: Prevents duplicate passwords. Effectively increases the length of the password. Prevents the use of hardware implementations of DES
110 Password Selecting Strategies User ducation (εθπαίδεπζε ρξεζηώλ) Computer-generated passwords (παξαγόκελα από ηνλ ππνινγηζηή ζπλζεκαηηθά) Reactive password checking (ζηξαηεγηθή αληηδξαζηηθνύ ειέγρνπ ζπλζεκαηηθνύ: ην ζύζηεκα εθηειεί πεξηνδηθά ην δηθό ηνπ πξνγξακκα ζπαζίκαηνο ζπλζεκαηηθώλ) Proactive password checking (πξνιεπηηθόο έιεγρνο ζπλζεκαηηθώλ)
111 Markov Model: ηερληθή πξνιεπηηθνύ ειεγθηή Μνληέιν γηα ηελ παξαγσγή πξνβιέςηκσλ ζπλζεκαηηθώλ: m: ν αξηζκόο θαηαζηάζεσλ ζην κνληειν Α: ν ρώξνο θαηαζηάζεσλ Τ: πηλαθαο πηζαλνηεησλ K: ε ηάμε ηνπ κνληέινπ
112 Transition Matrix 1. Determine the frequency matrix f, where f(i,j,k) is the number of occurrences of the trigram consisting of the ith, jth and kth character. 2. For each bigram ij, calculate f(i,j, ) as the total number of trigrams beginning with ij. 3. Compute the entries of T as follows: T( i, j, k) f ( i, j, k) f ( i, j, )
113 Spafford (Bloom Filter) H i where X i D ( X ) y 1 i k; 1 j D; 0 y N 1 i jthword inpassworddictionary numberof wordinpassworddictionary The following procedure is then applied to the dictionary: 1. A hash table of N bits is definied, with all bits initially set to For each password, its k hash values are calculated, and the responding bits in the hash table are set to 1
114 Spafford (Bloom Filter) Design the hash scheme to minimize false positive. Probability of false positive: kd/ N k P (1 e ) (1 e or, equivalent ly, k R 1/ k ln(1 P ) k / R ) k where k numberof hash function N numberof bitsinhashtable D numberof wordsindictionary R N / D, ratioof hash tablesize( bits) todictionarysize( words)
115 Performance of Bloom Filter
116 The Stages of a Network Intrusion 1. Scan the network to: locate which IP addresses are in use, what operating system is in use, what TCP or UDP ports are open (being listened to by Servers). 2. Run Exploit scripts against open ports 3. Get access to Shell program which is suid (has root privileges). 4. Download from Hacker Web site special versions of systems files that will let Cracker have free access in the future without his cpu time or disk storage space being noticed by auditing programs. 5. Use IRC (Internet Relay Chat) to invite friends to the feast.
117 Intusion Detection The intruder can be identified and ejected from the system. An effective intrusion detection can prevent intrusions. Intrusion detection enables the collection of information about intrusion techniques that can be used to strengthen the intrusion prevention facility.
118 Profiles of Behavior of Intruders and Authorized Users
119 Intrusion Detection Statistical anomaly detection (αλίρλεπζε ζηαηηζηηθώλ αλσκαιηώλ) Treshold detection (αλίρλεπζε κε θαηώθιηα) Profile based (αλίρλεπζε βαζηζκάλε ζε πξνθίι) Rule based detection (Αλίρλεπζε βαζηζκέλε ζε θαλόλεο) Anomaly detection (αλίρλεπζε αλσκαιηώλ) Penetration identidication (αλαγλσ ξηζε δηείζδπζεο)
120 Measures used for Intrusion Detection Login frequency by day and time. Frequency of login at different locations. Time since last login. Password failures at login. Execution frequency. Execution denials. Read, write, create, delete frequency. Failure count for read, write, create and delete.
121 Distributed Intrusion Detection Developed at University of California at Davis
122 Distributed Intrusion Detection
123 Viruses and Malicious Programs Computer Viruses and related programs have the ability to replicate themselves on an ever increasing number of computers. They originally spread by people sharing floppy disks. Now they spread primarily over the Internet (a Worm ). Other Malicious Programs may be installed by hand on a single machine. They may also be built into widely distributed commercial software packages. These are very hard to detect before the payload activates (Trojan Horses, Trap Doors, and Logic Bombs).
124 Taxonomy of Malicious Programs Malicious Programs Need Host Program Independent Trapdoors Logic Bombs Trojan Horses Viruses Bacteria Worms
125 Definitions Virus (Ινο) - code that copies itself into other programs. A Bacteria replicates until it fills all disk space, or CPU cycles. Payload - harmful things the malicious program does, after it has had time to spread. Worm (Σθνπιήθη) - a program that replicates itself across the network (usually riding on messages or attached documents (e.g., macro viruses).
126 Definitions Trojan Horse (Γνύξεηνο Ιππνο) - instructions in an otherwise good program that cause bad things to happen (sending your data or password to an attacker over the net). Logic Bomb (Λνγηθή Βόκβα) - malicious code that activates on an event (e.g., date). Trap Door (or Back Door) (Κεξθόπνξηα) - undocumented entry point written into code for debugging that can allow unwanted users.
127 Definitions Exploits (Σεκεία Δθκεηάιεπζεο) Πξνγξάκκαηα πνπ εθκεηαιεύνληαη ζπγθεθξηκέλεο αδπλακίεο. Downloaders (Πξνγξάκκαηα Καηεβάζκαηνο) εγθαζηζηά άιια πξνγξάκκαηα ζην ζύζηεκα ζην νπνίν βξίζθεηαη. Σπλήζσο κεηαδίδνληαη κέζσ ει. ηαρπδξνκείνπ Spammer εξγαιεία πνπ ζηέιλνπλ κεγάιν όγθν κελπκάησλ ει. Ταρπδξνκείνπ Flooder ρξεζηκνπνηνύληαη ζε επηζέζεηο θαηά δηθηπσκέλσλ ζπζηεκάησλ θαη πξνθαινύλ επηζέζεηο άξλεζεο εμππεξέηεζεο. Zombie πξόγξακκα ην νπνίν νηαλ ελεξγνπνηείηαη ζε ελαλ ππνινγηζηή, μεθηλά επηζέζεηο ζε άιινπο ππνινγηζηέο
128 Virus Phases Dormant phase (θάζη ύπνωζης) - the virus is idle Propagation phase (θάζη διάδοζης) - the virus places an identical copy of itself into other programs Triggering phase (θάζη πσροδόηηζης) the virus is activated to perform the function for which it was intended Execution phase (θάζη εκηέλεζης) the function is performed
129 Virus Protection Have a well-known virus protection program, configured to scan disks and downloads automatically for known viruses. Do not execute programs (or "macro's") from unknown sources (e.g., PS files, Hypercard files, MS Office documents, Avoid the most common operating systems and programs, if possible.
130 Virus Structure 1 ε γξακκή: άικα ζην θπξην πξόγξακκα ηνύ 2 ε γξακκή: αλαδεηά ακόιπληα εθηειέζηκα θαη ηα κνιύλεη... Ο ηόο πξαγκαηνπνηεί θάπνηα επδήκηα ελέξγεηα (κπνξεί λα εθηειείηαη θαζε θνξά πνπ ηξέρεη ην πξόγξακκα ή λα είλαη κηα ινγηθή βόκβα)
131 A Compression Virus
132 Types of Viruses Parasitic Virus (παξαζηηηθόο) - attaches itself to executable files as part of their code. Runs whenever the host program runs. Memory-resident Virus (ιός μόνιμα εγκαηεζηημένος ζηη μνήμη) - Lodges in main memory as part of the residual operating system. Boot Sector Virus (ιός ηομέα εκκίνηζης) - infects the boot sector of a disk, and spreads when the operating system boots up (original DOS viruses). Stealth Virus (αόξαηνο ηόο) - explicitly designed to hide from Virus Scanning programs. Polymorphic Virus (πνιπκνξθηθόο ηόο)- mutates with every new host to prevent signature detection. Metamorphic Virus (κεηακνξθηθόο ηόο) mutates with every new host, rewrites itself and changes its behavior and appearance
133 Macro Viruses Microsoft Office applications allow macros to be part of the document. The macro could run whenever the document is opened, or when a certain command is selected (Save File). Platform independent. Infect documents, delete files, generate and edit letters.
134 Ινί ει. ηαρπδξνκείνπ Φαξαθηεξηζηηθά Σηέιλεηαη ζε όια ηα άηνκα πνπ ππάξρνπλ ζηε ιίζηα επαθώλ ηνπ ρξήζηε Ο ηόο πξνθαιεί ηνπηθή δεκηά ελεξγνπνίεζε θαη κε απιό άλνηγκα ηνπ κελύκαηνο ει. ηαρπδξ. δπλαηόηεηεο ηαρείαο δηάδνζεο κέζσ Γηαδηθηύνπ Σθνπιήθηα Χάρλεη ελεξγεηηθά γηα άιια ζπζηήκαηα πξνθεηκέλνπ λα δηαδνζεί ρξεζηκνπνηεί «δηθηπαθό όρεκα»:» Υπεξεζία ει. ηαρπδξνκείνπ» Γπλαηόηεηα απνκαθξπζκέλεο εθηέιεζεο (εθηειεί ελα αληηγξαθό ηνπ ζε ελα αιιν ζύζηεκα)» Γπλαηόηεηα απνκαθξπζκέλεο ζύλδεζεο (ζπλδέεηαη σο ρξήζηεο ζε απνκαθξπζκέλν ζύζηεκα θαη ρξεζηκνπνηεί εληνιεο γηα λα αληηγξαθεί από ην έλα ζύζηεκα ζην άιιν) Τν ζθνπιήθη Morris: Robert Morris 1998, γηα ζπζηήκαηα UNIX, αλαθάιπςε άιισλ ππνινγηζηώλ ηνπο νπνηνπο εκπηζηεπόηαλ ν ππνινγηζηήο
135 Τερλνινγία Σθνπιεθηώλ Πνιππιαηθνξκηθά: κπνξνύλ λα επηηεζνύλ ζε WINDOWS, UNIX θιπ Πνιιαπιήο εθκεηάιιεπζεο: πνηθίινη ηξόπνη δηείζδπζεο(ρξεζηκνπνηώληαο εππάζεηεο ζε δηαθνκηζηέο Γηαδηθηύνπ, θνηλνρξεζηία αξρείσλ θιπ) Δμαηξεηηθά γξήγνξε εμάπισζε: ηερληθή γηα επηηάρπλζε ηεο εμάπισζεο-αλίρλεπζε ζην Γηαδηθηπν γηα ηελ ζπγθέληξσζε δηεπζύλζεσλ Πνιπκνξθηζκόο Μεηακνξθηζκόο Μεηαθνξηθά νρήκαηα: είλαη ηδαληθά κέζα κεηαθνξάο γηα άιια εξγαιεία θαηαλεκεκέλεο επίζεζεο Δθκεηάιιεπζε ηελ «εκέξα κεδελ»: γηα επίηεπμε κέγηζηνπ βαζκνύ αηθληδηαζκνύ θαη δηάδνζεο ην ζθνπιήθη εθκεηαιεύεηαη κηα άγλσζηε εππάζεηα
136 Μέηξα αληηκηώπηζεο Ιώλ Αλίρλεπζε: δηαπηζηώλεηαη ε κόιπλζε θαη εληνπίδεηαη ν ηόο Αλαγλώξηζε: αλαγλσξίδεηαη ν ζπγθεθξηκέλνο ηόο πνπ έρεη πξνζβάιιεη ην ζύζηεκα Καηάξγεζε: αθνπ αλαγλσξηζηεί ν ηνο, αθαηξνύληαη ηα ίρλε ηνπ
137 Antivirus Approaches 1st Generation, Scanners (απινί αληρλεπηέο): searched files for any of a library of known virus signatures. Checked executable files for length changes. 2nd Generation, Heuristic Scanners (επξεηηθνί αληρλεπηέο): looks for more general signs than specific signatures (code segments common to many viruses). Checked files for checksum or hash changes. Διεγρνο αθεξαηόηεηαο integrity checking: checksum-πξνζάξηεζε αζξνίζκαηνο ειεγρνπ 3rd Generation, Activity Traps (παγίδεο δξαζηεξηόηεηαο): stay resident in memory and look for certain patterns of software behavior (e.g., scanning files). 4th Generation, Full Featured (πιήξεο πξνζηαζία): combine the best of the techniques above.
138 Πξνεγκέλεο ηερληθέο αληηβηνηηθώλ
139 Χεθηαθό αλνζνπνηεηηθό ζύζηεκα
140
141 Advanced Antivirus Techniques
142
143
144 Δπίζεζε εζσηεξηθνύ πόξνπ
145
146 Δπίζεζε πνπ θαηαλαιώλεη πόξνπο κεηάδνζεο δεδνκέλσλ
147
148
149 Σηξαηεγηθέο ζάξσζεο ινγηζκηθνύ δόκπη γηα κόιπλζε ζπζηεκάησλ
150 Advanced Antivirus Techniques Generic Decryption (GD) CPU Emulator Virus Signature Scanner Emulation Control Module For how long should a GD scanner run each interpretation?
Πανεπιςτήμιο Πελοποννήςου Τμήμα Επιςτήμησ και Τεχνολογίασ Τηλεπικοινωνιών. Διαχείριςη και Αςφάλεια Δικτύων. Το Πρωτόκολλο SNMP
 Το Πρωτόκολλο SNMP Βάςη Πληροφοριών Διαχείριςησ Διαχειριςτήσ και διαχειριζόμενοσ Διαχειριζόμενο Σύςτημα Πράκτορασ UDP IP Δίκτυο Λειτουργίεσ Διαχείριςησ UDP IP Δίκτυο Βάςη Δεδομένων Διαχείριςησ Σταθμόσ
Το Πρωτόκολλο SNMP Βάςη Πληροφοριών Διαχείριςησ Διαχειριςτήσ και διαχειριζόμενοσ Διαχειριζόμενο Σύςτημα Πράκτορασ UDP IP Δίκτυο Λειτουργίεσ Διαχείριςησ UDP IP Δίκτυο Βάςη Δεδομένων Διαχείριςησ Σταθμόσ
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 6/11/2017
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 6/11/2017
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ ΤΟ ΠΡΩΤΟΚΟΛΛΟ SNMP. Β. Μάγκλαρης 01/12/2014
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ ΤΟ ΠΡΩΤΟΚΟΛΛΟ SNMP Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 01/12/2014 Άδεια Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ ΤΟ ΠΡΩΤΟΚΟΛΛΟ SNMP Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 01/12/2014 Άδεια Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων (επανάληψη) NETCONF (Network Configuration Protocol)
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 13/11/2017
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 13/11/2017
Διαχείριση Δικτύων με τη χρήση SNMP (5 η άσκηση)
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ - ΕΜΠ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ & ΜΗΧ. ΥΠΟΛΟΓΙΣΤΩΝ Τομέας Επικοινωνιών, Ηλεκτρονικής & Συστημάτων Πληροφορικής Εργαστήριο Διαχείρισης & Βελτίστου Σχεδιασμού Δικτύων Τηλεματικής
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ - ΕΜΠ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ & ΜΗΧ. ΥΠΟΛΟΓΙΣΤΩΝ Τομέας Επικοινωνιών, Ηλεκτρονικής & Συστημάτων Πληροφορικής Εργαστήριο Διαχείρισης & Βελτίστου Σχεδιασμού Δικτύων Τηλεματικής
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (ΙI) SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol)
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (ΙI) SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 24/11/2015
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (ΙI) SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 24/11/2015
Διαχείριση Δικτύων με τη χρήση SNMP (5η άσκηση) Διαχείριση Δικτύων - Ευφυή Δίκτυα, 9 ο Εξάμηνο,
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ - ΕΜΠ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ & ΜΗΧ. ΥΠΟΛΟΓΙΣΤΩΝ Τομέας Επικοινωνιών, Ηλεκτρονικής & Συστημάτων Πληροφορικής Εργαστήριο Διαχείρισης & Βελτίστου Σχεδιασμού Δικτύων Τηλεματικής
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ - ΕΜΠ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ & ΜΗΧ. ΥΠΟΛΟΓΙΣΤΩΝ Τομέας Επικοινωνιών, Ηλεκτρονικής & Συστημάτων Πληροφορικής Εργαστήριο Διαχείρισης & Βελτίστου Σχεδιασμού Δικτύων Τηλεματικής
Β. Μάγκλαρης.
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP SNMP MIB - Αντικείμενα & Ορισμοί Πινάκων NETCONF (Network Configuration Protocol) Β. Μάγκλαρης maglaris@netmode.ntua.gr
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (Ι) Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP Δομή SNMP Agent - MIB
 ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (Ι) Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP Δομή SNMP Agent - MIB Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 24/11/2015 Άδεια Χρήσης
ΔΙΑΧΕΙΡΙΣΗ ΔΙΚΤΥΩΝ Αρχιτεκτονικές Διαχείρισης Δικτύων (Ι) Υλοποιήσεις Client Server Το Πρωτόκολλο SNMP Δομή SNMP Agent - MIB Β. Μάγκλαρης maglaris@netmode.ntua.gr www.netmode.ntua.gr 24/11/2015 Άδεια Χρήσης
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
ιαχείριση ικτύων ρ.αρίστη Γαλάνη
 Πανεπιστήμιο Πειραιώς Τμήμα Ψηφιακών Συστημάτων ρ.αρίστη Γαλάνη Ακαδημαϊκό Έτος 2016-2017 Simple Network Management Protocol (SNMP) Simple Network Management Protocol (Απλό Πρωτόκολλο ιαχείρισης ικτύων):
Πανεπιστήμιο Πειραιώς Τμήμα Ψηφιακών Συστημάτων ρ.αρίστη Γαλάνη Ακαδημαϊκό Έτος 2016-2017 Simple Network Management Protocol (SNMP) Simple Network Management Protocol (Απλό Πρωτόκολλο ιαχείρισης ικτύων):
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ
 ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration
 Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration Δρ. Απόστολος Γκάμας Διδάσκων 407/80 gkamas@uop.gr Δίκτυα Επικοινωνιών ΙΙ Διαφάνεια 1 1 Dynamic Routing Configuration Router (config) # router protocol [ keyword
Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration Δρ. Απόστολος Γκάμας Διδάσκων 407/80 gkamas@uop.gr Δίκτυα Επικοινωνιών ΙΙ Διαφάνεια 1 1 Dynamic Routing Configuration Router (config) # router protocol [ keyword
CYTA Cloud Server Set Up Instructions
 CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
(C) 2010 Pearson Education, Inc. All rights reserved.
 Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Cryptography and Network Security Chapter 21. Fifth Edition by William Stallings
 Cryptography and Network Security Chapter 21 Fifth Edition by William Stallings Chapter 21 Malicious Software What is the concept of defense: : The parrying of a blow. What is its characteristic feature:
Cryptography and Network Security Chapter 21 Fifth Edition by William Stallings Chapter 21 Malicious Software What is the concept of defense: : The parrying of a blow. What is its characteristic feature:
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost
 Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης & Τεχνολογίας Τηλεπικοινωνιών Ευάγγελος Α. Κοσμάτος Basic OSPF Configuration Υλοποίηση Δικτυακών Υποδομών
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης & Τεχνολογίας Τηλεπικοινωνιών Ευάγγελος Α. Κοσμάτος Basic OSPF Configuration Υλοποίηση Δικτυακών Υποδομών
SOAP API. https://bulksmsn.gr. Table of Contents
 SOAP API https://bulksmsn.gr Table of Contents Send SMS...2 Query SMS...3 Multiple Query SMS...4 Credits...5 Save Contact...5 Delete Contact...7 Delete Message...8 Email: sales@bulksmsn.gr, Τηλ: 211 850
SOAP API https://bulksmsn.gr Table of Contents Send SMS...2 Query SMS...3 Multiple Query SMS...4 Credits...5 Save Contact...5 Delete Contact...7 Delete Message...8 Email: sales@bulksmsn.gr, Τηλ: 211 850
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
TaxiCounter Android App. Περδίκης Ανδρέας ME10069
 TaxiCounter Android App Περδίκης Ανδρέας ME10069 Content Android Operating System Development Tools Taxi Counter Algorithm Design Development Process Android Operating System Android is a Linux-based operating
TaxiCounter Android App Περδίκης Ανδρέας ME10069 Content Android Operating System Development Tools Taxi Counter Algorithm Design Development Process Android Operating System Android is a Linux-based operating
Συστήματα Διαχείρισης Βάσεων Δεδομένων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
Modbus basic setup notes for IO-Link AL1xxx Master Block
 n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
UNIVERSITY OF CALIFORNIA. EECS 150 Fall ) You are implementing an 4:1 Multiplexer that has the following specifications:
 UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches
 Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches ultiplexing: TD, FD, Statistical multiplexing, CDA OSI
Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches ultiplexing: TD, FD, Statistical multiplexing, CDA OSI
Special edition of the Technical Chamber of Greece on Video Conference Services on the Internet, 2000 NUTWBCAM
 NUTWBCAM A.S. DRIGAS Applied Technologies Department NCSR DEMOKRITOS Ag. Paraskevi GREECE dr@imm.demokritos.gr http://imm.demokritos.gr Το NutWBCam είναι ένα RealVideo πρόγραµµα που σας δίνει τη δυνατότητα
NUTWBCAM A.S. DRIGAS Applied Technologies Department NCSR DEMOKRITOS Ag. Paraskevi GREECE dr@imm.demokritos.gr http://imm.demokritos.gr Το NutWBCam είναι ένα RealVideo πρόγραµµα που σας δίνει τη δυνατότητα
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
the total number of electrons passing through the lamp.
 1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Διαχείριση και Ασφάλεια Τηλεπικοινωνιακών Συστημάτων
 Διαχείριση και Ασφάλεια Τηλεπικοινωνιακών Συστημάτων Διαχείριση Δικτύων Ανάγκη για Συστήματα Διαχείρισης ΠΑΡΑΓΟΝΤΕΣ γεωγραφική επέκταση δικτύων ετερογένεια δικτύων πλήθος και πολυπλοκότητα εφαρμογών υποστήριξη
Διαχείριση και Ασφάλεια Τηλεπικοινωνιακών Συστημάτων Διαχείριση Δικτύων Ανάγκη για Συστήματα Διαχείρισης ΠΑΡΑΓΟΝΤΕΣ γεωγραφική επέκταση δικτύων ετερογένεια δικτύων πλήθος και πολυπλοκότητα εφαρμογών υποστήριξη
Connected Threat Defense
 Connected Threat Defense συγκοινωνούντα συστήματα προστασίας Χριστόφορος Χριστοφή Channel Manager Πριν πέντε χρόνια η ασφάλεια των επιχειρήσεων ήταν ήδη δύσκολη υπόθεση 2 Ο μοντέρνος χώρος εργασίας δεν
Connected Threat Defense συγκοινωνούντα συστήματα προστασίας Χριστόφορος Χριστοφή Channel Manager Πριν πέντε χρόνια η ασφάλεια των επιχειρήσεων ήταν ήδη δύσκολη υπόθεση 2 Ο μοντέρνος χώρος εργασίας δεν
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
Διαχείριση Δικτύων. Κέντρο Δικτύων ΕΜΠ. Θανάσης Δουΐτσης, Βασίλης Μάγκλαρης Φεβρουάριος 2009
 Διαχείριση Δικτύων Κέντρο Δικτύων ΕΜΠ Θανάσης Δουΐτσης, Βασίλης Μάγκλαρης Φεβρουάριος 2009 Περίληψη Το πρωτόκολλο SNMP Το δίκτυο του ΕΜΠ Συχνά χρησιμοποιούμενες ΜΙΒs Το εργαλείο MRTG/RRD Το εργαλείο Nagios
Διαχείριση Δικτύων Κέντρο Δικτύων ΕΜΠ Θανάσης Δουΐτσης, Βασίλης Μάγκλαρης Φεβρουάριος 2009 Περίληψη Το πρωτόκολλο SNMP Το δίκτυο του ΕΜΠ Συχνά χρησιμοποιούμενες ΜΙΒs Το εργαλείο MRTG/RRD Το εργαλείο Nagios
Connected Threat Defense
 Connected Threat Defense συγκοινωνούντα συστήματα προστασίας Χριστόφορος Χριστοφή Διευθύνων Σύμβουλος CHANNEL IT Πριν πέντε χρόνια η ασφάλεια των επιχειρήσεων ήταν ήδη δύσκολη υπόθεση 2 Ο μοντέρνος χώρος
Connected Threat Defense συγκοινωνούντα συστήματα προστασίας Χριστόφορος Χριστοφή Διευθύνων Σύμβουλος CHANNEL IT Πριν πέντε χρόνια η ασφάλεια των επιχειρήσεων ήταν ήδη δύσκολη υπόθεση 2 Ο μοντέρνος χώρος
department listing department name αχχουντσ ϕανε βαλικτ δδσϕηασδδη σδηφγ ασκϕηλκ τεχηνιχαλ αλαν ϕουν διξ τεχηνιχαλ ϕοην µαριανι
 She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
Εγκατάσταση λογισμικού και αναβάθμιση συσκευής Device software installation and software upgrade
 Για να ελέγξετε το λογισμικό που έχει τώρα η συσκευή κάντε κλικ Menu > Options > Device > About Device Versions. Στο πιο κάτω παράδειγμα η συσκευή έχει έκδοση λογισμικού 6.0.0.546 με πλατφόρμα 6.6.0.207.
Για να ελέγξετε το λογισμικό που έχει τώρα η συσκευή κάντε κλικ Menu > Options > Device > About Device Versions. Στο πιο κάτω παράδειγμα η συσκευή έχει έκδοση λογισμικού 6.0.0.546 με πλατφόρμα 6.6.0.207.
Partial Trace and Partial Transpose
 Partial Trace and Partial Transpose by José Luis Gómez-Muñoz http://homepage.cem.itesm.mx/lgomez/quantum/ jose.luis.gomez@itesm.mx This document is based on suggestions by Anirban Das Introduction This
Partial Trace and Partial Transpose by José Luis Gómez-Muñoz http://homepage.cem.itesm.mx/lgomez/quantum/ jose.luis.gomez@itesm.mx This document is based on suggestions by Anirban Das Introduction This
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Test Data Management in Practice
 Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
HP Network Node Manager (NNM) Tutorial
 Telecommunication Networks and integrated Services Laboratory tns.ds.unipi.gr HP Network Node Manager (NNM) Tutorial Καθηγ. Π. Δεμέστιχας, Δρ.K. Τσαγκάρης, Δρ. Μ. Λογοθέτης, Δ. Καρβουνάς Email: {pdemest,
Telecommunication Networks and integrated Services Laboratory tns.ds.unipi.gr HP Network Node Manager (NNM) Tutorial Καθηγ. Π. Δεμέστιχας, Δρ.K. Τσαγκάρης, Δρ. Μ. Λογοθέτης, Δ. Καρβουνάς Email: {pdemest,
Στρατηγικές Ασφάλειας
 Στρατηγικές Ασφάλειας Ασφάλεια Πληροφοριακών Συστημάτων. Διδάσκων: Σ. Κοντογιάννης Least/(Most) Privileges Defense in Depth Συγκεντρωτική Στρατηγική Weakest Link Strategy Fail Safe Stance Fail Safe Stance
Στρατηγικές Ασφάλειας Ασφάλεια Πληροφοριακών Συστημάτων. Διδάσκων: Σ. Κοντογιάννης Least/(Most) Privileges Defense in Depth Συγκεντρωτική Στρατηγική Weakest Link Strategy Fail Safe Stance Fail Safe Stance
ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ - ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΕΠΛ 133: ΑΝΤΙΚΕΙΜΕΝΟΣΤΡΕΦΗΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΕΡΓΑΣΤΗΡΙΟ 3 Javadoc Tutorial
 ΕΡΓΑΣΤΗΡΙΟ 3 Javadoc Tutorial Introduction Το Javadoc είναι ένα εργαλείο που παράγει αρχεία html (παρόμοιο με τις σελίδες στη διεύθυνση http://docs.oracle.com/javase/8/docs/api/index.html) από τα σχόλια
ΕΡΓΑΣΤΗΡΙΟ 3 Javadoc Tutorial Introduction Το Javadoc είναι ένα εργαλείο που παράγει αρχεία html (παρόμοιο με τις σελίδες στη διεύθυνση http://docs.oracle.com/javase/8/docs/api/index.html) από τα σχόλια
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Dynamic types, Lambda calculus machines Section and Practice Problems Apr 21 22, 2016
 Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
ΚΥΠΡΙΑΚΟΣ ΣΥΝΔΕΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY 21 ος ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ Δεύτερος Γύρος - 30 Μαρτίου 2011
 Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
VBA ΣΤΟ WORD. 1. Συχνά, όταν ήθελα να δώσω ένα φυλλάδιο εργασίας με ασκήσεις στους μαθητές έκανα το εξής: Version 25-7-2015 ΗΜΙΤΕΛΗΣ!!!!
 VBA ΣΤΟ WORD Version 25-7-2015 ΗΜΙΤΕΛΗΣ!!!! Μου παρουσιάστηκαν δύο θέματα. 1. Συχνά, όταν ήθελα να δώσω ένα φυλλάδιο εργασίας με ασκήσεις στους μαθητές έκανα το εξής: Εγραφα σε ένα αρχείο του Word τις
VBA ΣΤΟ WORD Version 25-7-2015 ΗΜΙΤΕΛΗΣ!!!! Μου παρουσιάστηκαν δύο θέματα. 1. Συχνά, όταν ήθελα να δώσω ένα φυλλάδιο εργασίας με ασκήσεις στους μαθητές έκανα το εξής: Εγραφα σε ένα αρχείο του Word τις
EPL 603 TOPICS IN SOFTWARE ENGINEERING. Lab 5: Component Adaptation Environment (COPE)
 EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
Advanced Subsidiary Unit 1: Understanding and Written Response
 Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
ίκτυο προστασίας για τα Ελληνικά αγροτικά και οικόσιτα ζώα on.net e-foundatio //www.save itute: http:/ toring Insti SAVE-Monit
 How to run a Herdbook: Basics and Basics According to the pedigree scheme, you need to write down the ancestors of your animals. Breeders should be able easily to write down the necessary data It is better
How to run a Herdbook: Basics and Basics According to the pedigree scheme, you need to write down the ancestors of your animals. Breeders should be able easily to write down the necessary data It is better
How to register an account with the Hellenic Community of Sheffield.
 How to register an account with the Hellenic Community of Sheffield. (1) EN: Go to address GR: Πηγαίνετε στη διεύθυνση: http://www.helleniccommunityofsheffield.com (2) EN: At the bottom of the page, click
How to register an account with the Hellenic Community of Sheffield. (1) EN: Go to address GR: Πηγαίνετε στη διεύθυνση: http://www.helleniccommunityofsheffield.com (2) EN: At the bottom of the page, click
Introduction to the TCP IP protocol stack through a role playing game
 Introduction to the TCP IP protocol stack through a role playing game Based on : Norman Pendegraft. 2003. The TCP/IP game. In Current issues in IT education, Tanya McGill (Ed.). IGI Publishing, Hershey,
Introduction to the TCP IP protocol stack through a role playing game Based on : Norman Pendegraft. 2003. The TCP/IP game. In Current issues in IT education, Tanya McGill (Ed.). IGI Publishing, Hershey,
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Διαδίκτυο των Αντικειμένων - IoT.
 Διαδίκτυο των Αντικειμένων - IoT sdima@ece.upatras.gr ΑΠΟΚΤΗΣΗ ΑΚΑΔΗΜΑΪΚΗΣ ΔΙΔΑΚΤΙΚΗΣ ΕΜΠΕΙΡΙΑΣ ΣΕ ΝΕΟΥΣ ΕΠΙΣΤΗΜΟΝΕΣ ΚΑΤΟΧΟΥΣ ΔΙΔΑΚΤΟΡΙΚΟΥ ΣΤΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ (ΦΚ/MIS) Ε.655/ 5001184. sdima@ece.upatras.gr
Διαδίκτυο των Αντικειμένων - IoT sdima@ece.upatras.gr ΑΠΟΚΤΗΣΗ ΑΚΑΔΗΜΑΪΚΗΣ ΔΙΔΑΚΤΙΚΗΣ ΕΜΠΕΙΡΙΑΣ ΣΕ ΝΕΟΥΣ ΕΠΙΣΤΗΜΟΝΕΣ ΚΑΤΟΧΟΥΣ ΔΙΔΑΚΤΟΡΙΚΟΥ ΣΤΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ (ΦΚ/MIS) Ε.655/ 5001184. sdima@ece.upatras.gr
SPEEDO AQUABEAT. Specially Designed for Aquatic Athletes and Active People
 SPEEDO AQUABEAT TM Specially Designed for Aquatic Athletes and Active People 1 2 Decrease Volume Increase Volume Reset EarphonesUSBJack Power Off / Rewind Power On / Fast Forward Goggle clip LED Status
SPEEDO AQUABEAT TM Specially Designed for Aquatic Athletes and Active People 1 2 Decrease Volume Increase Volume Reset EarphonesUSBJack Power Off / Rewind Power On / Fast Forward Goggle clip LED Status
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration
 Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration Δρ. Απόστολος Γκάμας Διδάσκων (407/80) gkamas@uop.gr Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών Διαφάνεια 1 1 Dynamic Routing Configuration
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration Δρ. Απόστολος Γκάμας Διδάσκων (407/80) gkamas@uop.gr Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών Διαφάνεια 1 1 Dynamic Routing Configuration
A browser-based digital signing solution over the web
 A browser-based digital signing solution over the web Fotis Loukos Charalampos Tsipizidis Dimitris Daskopoulos The problem Contents Proposed solution Architecture Native Messaging Host Native Messaging
A browser-based digital signing solution over the web Fotis Loukos Charalampos Tsipizidis Dimitris Daskopoulos The problem Contents Proposed solution Architecture Native Messaging Host Native Messaging
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Oracle SQL Developer An Oracle Database stores and organizes information. Oracle SQL Developer is a tool for accessing and maintaining the data
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Oracle SQL Developer An Oracle Database stores and organizes information. Oracle SQL Developer is a tool for accessing and maintaining the data
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1
 Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Στο εστιατόριο «ToDokimasesPrinToBgaleisStonKosmo?» έξω από τους δακτυλίους του Κρόνου, οι παραγγελίες γίνονται ηλεκτρονικά.
 Διαστημικό εστιατόριο του (Μ)ΑστροΈκτορα Στο εστιατόριο «ToDokimasesPrinToBgaleisStonKosmo?» έξω από τους δακτυλίους του Κρόνου, οι παραγγελίες γίνονται ηλεκτρονικά. Μόλις μια παρέα πελατών κάτσει σε ένα
Διαστημικό εστιατόριο του (Μ)ΑστροΈκτορα Στο εστιατόριο «ToDokimasesPrinToBgaleisStonKosmo?» έξω από τους δακτυλίους του Κρόνου, οι παραγγελίες γίνονται ηλεκτρονικά. Μόλις μια παρέα πελατών κάτσει σε ένα
ΜΟΝΤΕΛΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ
 ΜΟΝΤΕΛΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ Ενότητα 12 Τμήμα Εφαρμοσμένης Πληροφορικής Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό, όπως εικόνες, που υπόκειται
ΜΟΝΤΕΛΑ ΛΗΨΗΣ ΑΠΟΦΑΣΕΩΝ Ενότητα 12 Τμήμα Εφαρμοσμένης Πληροφορικής Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό, όπως εικόνες, που υπόκειται
[1] P Q. Fig. 3.1
![[1] P Q. Fig. 3.1 [1] P Q. Fig. 3.1](/thumbs/79/80362156.jpg) 1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Τμήμα Πολιτικών και Δομικών Έργων
 Τμήμα Πολιτικών και Δομικών Έργων Πτυχιακή Εργασία: Τοπογραφικό διάγραμμα σε ηλεκτρονική μορφή κεντρικού λιμένα Κέρκυρας και κτιρίου νέου επιβατικού σταθμού σε τρισδιάστατη μορφή και σχεδίαση με AutoCAD
Τμήμα Πολιτικών και Δομικών Έργων Πτυχιακή Εργασία: Τοπογραφικό διάγραμμα σε ηλεκτρονική μορφή κεντρικού λιμένα Κέρκυρας και κτιρίου νέου επιβατικού σταθμού σε τρισδιάστατη μορφή και σχεδίαση με AutoCAD
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/2006
 ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής
 Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
ΠΑΝΔΠΙΣΗΜΙΟ ΜΑΚΔΓΟΝΙΑ ΠΡΟΓΡΑΜΜΑ ΜΔΣΑΠΣΤΥΙΑΚΧΝ ΠΟΤΓΧΝ ΣΜΗΜΑΣΟ ΔΦΑΡΜΟΜΔΝΗ ΠΛΗΡΟΦΟΡΙΚΗ
 ΠΑΝΔΠΙΣΗΜΙΟ ΜΑΚΔΓΟΝΙΑ ΠΡΟΓΡΑΜΜΑ ΜΔΣΑΠΣΤΥΙΑΚΧΝ ΠΟΤΓΧΝ ΣΜΗΜΑΣΟ ΔΦΑΡΜΟΜΔΝΗ ΠΛΗΡΟΦΟΡΙΚΗ ΑΝΑΠΣΤΞΗ ΓΤΝΑΜΙΚΗ ΙΣΟΔΛΙΓΑ ΓΙΑ ΣΟ ΓΔΝΙΚΟ ΚΑΣΑΣΗΜΑ ΚΡΑΣΗΗ ΓΡΔΒΔΝΧΝ ΜΔ ΣΗ ΒΟΗΘΔΙΑ PHP MYSQL Γηπισκαηηθή Δξγαζία ηνπ Υξήζηνπ
ΠΑΝΔΠΙΣΗΜΙΟ ΜΑΚΔΓΟΝΙΑ ΠΡΟΓΡΑΜΜΑ ΜΔΣΑΠΣΤΥΙΑΚΧΝ ΠΟΤΓΧΝ ΣΜΗΜΑΣΟ ΔΦΑΡΜΟΜΔΝΗ ΠΛΗΡΟΦΟΡΙΚΗ ΑΝΑΠΣΤΞΗ ΓΤΝΑΜΙΚΗ ΙΣΟΔΛΙΓΑ ΓΙΑ ΣΟ ΓΔΝΙΚΟ ΚΑΣΑΣΗΜΑ ΚΡΑΣΗΗ ΓΡΔΒΔΝΧΝ ΜΔ ΣΗ ΒΟΗΘΔΙΑ PHP MYSQL Γηπισκαηηθή Δξγαζία ηνπ Υξήζηνπ
PortSip Softphone. Ελληνικά Ι English 1/20
 PortSip Softphone Ελληνικά Ι English 1/20 1. Περιεχόμενα 2. Εγκατάσταση σε Smartphone & Tablet (Android ή ios)... 1 3. Εγκατάσταση σε ηλεκτρονικό υπολογιστή (Windows ή Mac).... 5 4. Installation in Smartphone
PortSip Softphone Ελληνικά Ι English 1/20 1. Περιεχόμενα 2. Εγκατάσταση σε Smartphone & Tablet (Android ή ios)... 1 3. Εγκατάσταση σε ηλεκτρονικό υπολογιστή (Windows ή Mac).... 5 4. Installation in Smartphone
Επίπεδο Μεταφοράς. (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών Τμήμα Μηχανικών Η/Υ και Πληροφορικής
 Επίπεδο Μεταφοράς (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο Μεταφοράς(Transport layer) Επίπεδο εφαρμογής (Application layer): Συντονισμός
Επίπεδο Μεταφοράς (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο Μεταφοράς(Transport layer) Επίπεδο εφαρμογής (Application layer): Συντονισμός
Δίκτυα Δακτυλίου. Token Ring - Polling
 Δίκτυα Δακτυλίου Token Ring - Polling Όλοι οι κόμβοι είναι τοποθετημένοι σε ένα δακτύλιο. Εκπέμπει μόνο ο κόμβος ο οποίος έχει τη σκυτάλη (token). The token consists of a number of octets in a specific
Δίκτυα Δακτυλίου Token Ring - Polling Όλοι οι κόμβοι είναι τοποθετημένοι σε ένα δακτύλιο. Εκπέμπει μόνο ο κόμβος ο οποίος έχει τη σκυτάλη (token). The token consists of a number of octets in a specific
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook
 Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook Βήμα 1: Step 1: Βρείτε το βιβλίο που θα θέλατε να αγοράσετε και πατήστε Add to Cart, για να το προσθέσετε στο καλάθι σας. Αυτόματα θα
Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook Βήμα 1: Step 1: Βρείτε το βιβλίο που θα θέλατε να αγοράσετε και πατήστε Add to Cart, για να το προσθέσετε στο καλάθι σας. Αυτόματα θα
Abstract Storage Devices
 Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ»
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
Reminders: linear functions
 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Potential Dividers. 46 minutes. 46 marks. Page 1 of 11
 Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
9.09. # 1. Area inside the oval limaçon r = cos θ. To graph, start with θ = 0 so r = 6. Compute dr
 9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
Architecture οf Integrated Ιnformation Systems (ARIS)
 Architecture οf Integrated Ιnformation Systems (ARIS) Η αρχιτεκτονική ARIS (ARchitecture οf Integrated information Systems) έχει ως στόχο της την περιγρφή όλων των όψεων ή οπτικών ενός επιχειρηματικού
Architecture οf Integrated Ιnformation Systems (ARIS) Η αρχιτεκτονική ARIS (ARchitecture οf Integrated information Systems) έχει ως στόχο της την περιγρφή όλων των όψεων ή οπτικών ενός επιχειρηματικού
Galatia SIL Keyboard Information
 Galatia SIL Keyboard Information Keyboard ssignments The main purpose of the keyboards is to provide a wide range of keying options, so many characters can be entered in multiple ways. If you are typing
Galatia SIL Keyboard Information Keyboard ssignments The main purpose of the keyboards is to provide a wide range of keying options, so many characters can be entered in multiple ways. If you are typing
Επίπεδο δικτύου IP Forwading κτλ
 Επίπεδο δικτύου IP Forwading κτλ (IP για που το έβαλες) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο δικτύου (Network layer) Επίπεδο εφαρμογής (Application layer):
Επίπεδο δικτύου IP Forwading κτλ (IP για που το έβαλες) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο δικτύου (Network layer) Επίπεδο εφαρμογής (Application layer):
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Business English. Ενότητα # 9: Financial Planning. Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Section 1: Listening and responding. Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016
 Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
Démographie spatiale/spatial Demography
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
