4. GREEDY ALGORITHMS II
|
|
|
- Φῆλιξ Αναστασιάδης
- 7 χρόνια πριν
- Προβολές:
Transcript
1 4. GREEDY ALGORITHMS II Dijkstra's algorithm minimum spanning trees Prim, Kruskal, Boruvka single-link clustering min-cost arborescences Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley Copyright 2013 Kevin Wayne Last updated on Sep 8, :30 AM
2 4. GREEDY ALGORITHMS II Dijkstra's algorithm minimum spanning trees Prim, Kruskal, Boruvka single-link clustering min-cost arborescences SECTION 4.4
3 Shortest-paths problem Problem. Given a digraph G = (V, E), edge lengths e 0, source s V, and destination t V, find the shortest directed path from s to t source s length of path = = 25 6 destination t 3
4 Car navigation 4
5 Shortest path applications PERT/CPM. Map routing. Seam carving. Robot navigation. Texture mapping. Typesetting in LaTeX. Urban traffic planning. Telemarketer operator scheduling. Routing of telecommunications messages. Network routing protocols (OSPF, BGP, RIP). Optimal truck routing through given traffic congestion pattern. Reference: Network Flows: Theory, Algorithms, and Applications, R. K. Ahuja, T. L. Magnanti, and J. B. Orlin, Prentice Hall,
6 Dijkstra's algorithm Greedy approach. Maintain a set of explored nodes S for which algorithm has determined the shortest path distance d(u) from s to u. Initialize S = { s }, d(s) = 0. Repeatedly choose unexplored node v which minimizes shortest path to some node u in explored part, followed by a single edge (u, v) S d(u) u e v s 6
7 Dijkstra's algorithm Greedy approach. Maintain a set of explored nodes S for which algorithm has determined the shortest path distance d(u) from s to u. Initialize S = { s }, d(s) = 0. Repeatedly choose unexplored node v which minimizes add v to S, and set d(v) = π(v). shortest path to some node u in explored part, followed by a single edge (u, v) S d(u) u e d(v) v s 7
8 Dijkstra's algorithm: proof of correctness Invariant. For each node u S, d(u) is the length of the shortest su path. Pf. [ by induction on S ] Base case: S = 1 is easy since S = { s } and d(s) = 0. Inductive hypothesis: Assume true for S = k 1. Let v be next node added to S, and let (u, v) be the final edge. The shortest su path plus (u, v) is an sv path of length π(v). Consider any sv path P. We show that it is no shorter than π(v). Let (x, y) be the first edge in P that leaves S, and let P' be the subpath to x. P is already too long as soon as it reaches y. s P' x y P S u (P) (P') + (x, y) d(x) + (x, y) π (y) π (v) v nonnegative lengths inductive hypothesis definition of π(y) Dijkstra chose v instead of y 8
9 Dijkstra's algorithm: efficient implementation Implementation. Algorithm stores d(v) for each explored node v. Priority queue stores π (v) for each unexplored node v. Recall: d(u) = π (u) when u is deleted from priority queue. DIJKSTRA (V, E, s) Create an empty priority queue. FOR EACH v s : d(v) ; d(s) 0. FOR EACH v V : insert v with key d(v) into priority queue. WHILE (the priority queue is not empty) u delete-min from priority queue. FOR EACH edge (u, v) E leaving u: IF d(v) > d(u) + (u, v) decrease-key of v to d(u) + (u, v) in priority queue. d(v) d(u) + (u, v). 10
10 Dijkstra's algorithm: which priority queue? Performance. Depends on PQ: n insert, n delete-min, m decrease-key. Array implementation optimal for dense graphs. Binary heap much faster for sparse graphs. 4-way heap worth the trouble in performance-critical situations. Fibonacci/Brodal best in theory, but not worth implementing. PQ implementation insert delete-min decrease-key total unordered array O(1) O(n) O(1) O(n 2 ) binary heap O(log n) O(log n) O(log n) O(m log n) d-way heap (Johnson 1975) O(d logd n) O(d logd n) O(logd n) O(m logm/n n) Fibonacci heap (Fredman-Tarjan 1984) O(1) O(log n) O(1) O(m + n log n) Brodal queue (Brodal 1996) O(1) O(log n) O(1) O(m + n log n) amortized 11
11 4. GREEDY ALGORITHMS II Dijkstra's algorithm minimum spanning trees Prim, Kruskal, Boruvka single-link clustering min-cost arborescences SECTION 6.1
12 Cycles and cuts Def. A path is a sequence of edges which connects a sequence of nodes. Def. A cycle is a path with no repeated nodes or edges other than the starting and ending nodes cycle C = { (1, 2), (2, 3), (3, 4), (4, 5), (5, 6), (6, 1) } 14
13 Cycles and cuts Def. A cut is a partition of the nodes into two nonempty subsets S and V S. Def. The cutset of a cut S is the set of edges with exactly one endpoint in S cut S 7 8 cutset D = { (3, 4), (3, 5), (5, 6), (5, 7), (8, 7) } 15
14 Cycle-cut intersection Proposition. A cycle and a cutset intersect in an even number of edges cutset D = { (3, 4), (3, 5), (5, 6), (5, 7), (8, 7) } cycle C = { (1, 2), (2, 3), (3, 4), (4, 5), (5, 6), (6, 1) } intersection C D = { (3, 4), (5, 6) } 16
15 Cycle-cut intersection Proposition. A cycle and a cutset intersect in an even number of edges. Pf. [by picture] S cycle C 17
16 Spanning tree properties Proposition. Let T = (V, F) be a subgraph of G = (V, E). TFAE: T is a spanning tree of G. T is acyclic and connected. T is connected and has n 1 edges. T is acyclic and has n 1 edges. T is minimally connected: removal of any edge disconnects it. T is maximally acyclic: addition of any edge creates a cycle. T has a unique simple path between every pair of nodes. T = (V, F) 18
17 Minimum spanning tree Given a connected graph G = (V, E) with edge costs c e, an MST is a subset of the edges T E such that T is a spanning tree whose sum of edge costs is minimized MST cost = 50 = Cayley's theorem. There are n n 2 spanning trees of K n. can't solve by brute force 19
18 Applications MST is fundamental problem with diverse applications. Dithering. Cluster analysis. Max bottleneck paths. Real-time face verification. LDPC codes for error correction. Image registration with Renyi entropy. Find road networks in satellite and aerial imagery. Reducing data storage in sequencing amino acids in a protein. Model locality of particle interactions in turbulent fluid flows. Autoconfig protocol for Ethernet bridging to avoid cycles in a network. Approximation algorithms for NP-hard problems (e.g., TSP, Steiner tree). Network design (communication, electrical, hydraulic, computer, road). 20
19 Fundamental cycle Fundamental cycle. Adding any non-tree edge e to a spanning tree T forms unique cycle C. Deleting any edge f C from T { e } results in new spanning tree. e f T = (V, F) Observation. If c e < c f, then T is not an MST. 21
20 Fundamental cutset Fundamental cutset. Deleting any tree edge f from a spanning tree T divide nodes into two connected components. Let D be cutset. Adding any edge e D to T { f } results in new spanning tree. e f T = (V, F) Observation. If c e < c f, then T is not an MST. 22
21 4. GREEDY ALGORITHMS II Dijkstra's algorithm minimum spanning trees Prim, Kruskal, Boruvka single-link clustering min-cost arborescences SECTION 6.2
22 Prim's algorithm Initialize S = any node. Repeat n 1 times: Add to tree the min weight edge with one endpoint in S. Add new node to S. Theorem. Prim's algorithm computes the MST. Pf. Special case of greedy algorithm (blue rule repeatedly applied to S). S 30
23 Prim's algorithm: implementation Theorem. Prim's algorithm can be implemented in O(m log n) time. Pf. Implementation almost identical to Dijkstra's algorithm. [ d(v) = weight of cheapest known edge between v and S ] PRIM (V, E, c) Create an empty priority queue. s any node in V. FOR EACH v s : d(v) ; d(s) 0. FOR EACH v : insert v with key d(v) into priority queue. WHILE (the priority queue is not empty) u delete-min from priority queue. FOR EACH edge (u, v) E incident to u: IF d(v) > c(u, v) decrease-key of v to c(u, v) in priority queue. d(v) c(u, v). 31
24 Kruskal's algorithm Consider edges in ascending order of weight: Add to tree unless it would create a cycle. Theorem. Kruskal's algorithm computes the MST. Pf. Special case of greedy algorithm. Case 1: both endpoints of e in same blue tree. color red by applying red rule to unique cycle. all other edges in cycle are blue Case 2. If both endpoints of e are in different blue trees. color blue by applying blue rule to cutset defined by either tree. no edge in cutset has smaller weight (since Kruskal chose it first) e 32
25 Kruskal's algorithm: implementation Theorem. Kruskal's algorithm can be implemented in O(m log m) time. Sort edges by weight. Use union-find data structure to dynamically maintain connected components. KRUSKAL (V, E, c) SORT m edges by weight so that c(e1) c(e2) c(em) S φ FOREACH v V: MAKESET(v). FOR i = 1 TO m (u, v) ei IF FINDSET(u) FINDSET(v) RETURN S S S { ei } UNION(u, v). make u and v in same component are u and v in same component? 33
26 Does a linear-time MST algorithm exist? deterministic compare-based MST algorithms year worst case discovered by 1975 O(m log log n) Yao 1976 O(m log log n) Cheriton-Tarjan 1984 O(m log*n) O(m + n log n) Fredman-Tarjan 1986 O(m log (log* n)) Gabow-Galil-Spencer-Tarjan 1997 O(m α(n) log α(n)) Chazelle 2000 O(m α(n)) Chazelle 2002 optimal Pettie-Ramachandran 20xx O(m)??? Remark 1. O(m) randomized MST algorithm. [Karger-Klein-Tarjan 1995] Remark 2. O(m) MST verification algorithm. [Dixon-Rauch-Tarjan 1992] 41
27 4. GREEDY ALGORITHMS II Dijkstra's algorithm minimum spanning trees Prim, Kruskal, Boruvka single-link clustering min-cost arborescences SECTION 4.7
28 Clustering Goal. Given a set U of n objects labeled p 1,, p n, partition into clusters so that objects in different clusters are far apart. outbreak of cholera deaths in London in 1850s (Nina Mishra) Applications. Routing in mobile ad hoc networks. Document categorization for web search. Similarity searching in medical image databases Skycat: cluster 109 sky objects into stars, quasars, galaxies
29 Clustering of maximum spacing k-clustering. Divide objects into k non-empty groups. Distance function. Numeric value specifying "closeness" of two objects. d(p i, p j ) = 0 iff p i = p j [identity of indiscernibles] d(p i, p j ) 0%% % % % [nonnegativity] d(p i, p j ) = d(p j, p i ) [symmetry] Spacing. Min distance between any pair of points in different clusters. Goal. Given an integer k, find a k-clustering of maximum spacing. distance between two clusters distance between two closest clusters 4-clustering 44
30 Greedy clustering algorithm Well-known algorithm in science literature for single-linkage k-clustering: Form a graph on the node set U, corresponding to n clusters. Find the closest pair of objects such that each object is in a different cluster, and add an edge between them. Repeat n k times until there are exactly k clusters. Key observation. This procedure is precisely Kruskal's algorithm (except we stop when there are k connected components). Alternative. Find an MST and delete the k 1 longest edges. 45
31 Dendrogram of cancers in human Tumors in similar tissues cluster together. gene 1 gene n Reference: Botstein & Brown group gene expressed gene not expressed 47
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 016 - I. ΜΗΛΗΣ AΛΓΟΡΙΘΜΟΙ ΓΡΑΦΩΝ ΙΙΙ Minimum Spanning Trees ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 016 - Ι. ΜΗΛΗΣ 14 - GRAPHS III - MSTs 1 Trees Ένας γράφος T = (V,
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 016 - I. ΜΗΛΗΣ AΛΓΟΡΙΘΜΟΙ ΓΡΑΦΩΝ ΙΙΙ Minimum Spanning Trees ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 016 - Ι. ΜΗΛΗΣ 14 - GRAPHS III - MSTs 1 Trees Ένας γράφος T = (V,
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Fractional Colorings and Zykov Products of graphs
 Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Αλγόριθμοι και πολυπλοκότητα Depth-First Search
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Depth-First Search Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Depth-First Search A B D E C Depth-First Search 1 Outline and Reading
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Depth-First Search Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Depth-First Search A B D E C Depth-First Search 1 Outline and Reading
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2)
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2) Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness (2) x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 11 13 21
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2) Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness (2) x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 11 13 21
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Distances in Sierpiński Triangle Graphs
 Distances in Sierpiński Triangle Graphs Sara Sabrina Zemljič joint work with Andreas M. Hinz June 18th 2015 Motivation Sierpiński triangle introduced by Wac law Sierpiński in 1915. S. S. Zemljič 1 Motivation
Distances in Sierpiński Triangle Graphs Sara Sabrina Zemljič joint work with Andreas M. Hinz June 18th 2015 Motivation Sierpiński triangle introduced by Wac law Sierpiński in 1915. S. S. Zemljič 1 Motivation
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf6/ Άνοιξη 06 - I. ΜΗΛΗΣ P NP και NP-complete προβλήματα (Κλάσεις Πολυπλοκότητας) ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 06 - Ι. ΜΗΛΗΣ 5 NP-COMPLETENESS I Γιατί για πολλά προβλήματα
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf6/ Άνοιξη 06 - I. ΜΗΛΗΣ P NP και NP-complete προβλήματα (Κλάσεις Πολυπλοκότητας) ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 06 - Ι. ΜΗΛΗΣ 5 NP-COMPLETENESS I Γιατί για πολλά προβλήματα
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Homework 8 Model Solution Section
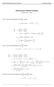 MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
The Probabilistic Method - Probabilistic Techniques. Lecture 7: The Janson Inequality
 The Probabilistic Method - Probabilistic Techniques Lecture 7: The Janson Inequality Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2014-2015 Sotiris Nikoletseas,
The Probabilistic Method - Probabilistic Techniques Lecture 7: The Janson Inequality Sotiris Nikoletseas Associate Professor Computer Engineering and Informatics Department 2014-2015 Sotiris Nikoletseas,
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 2016 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 2016 - Ι. ΜΗΛΗΣ 08 DP I 1 Dynamic Programming Richard Bellman (1953) Etymology (at
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 2016 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 2016 - Ι. ΜΗΛΗΣ 08 DP I 1 Dynamic Programming Richard Bellman (1953) Etymology (at
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ. Ψηφιακή Οικονομία. Διάλεξη 10η: Basics of Game Theory part 2 Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Ψηφιακή Οικονομία Διάλεξη 0η: Basics of Game Theory part 2 Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών Best Response Curves Used to solve for equilibria in games
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Ψηφιακή Οικονομία Διάλεξη 0η: Basics of Game Theory part 2 Mαρίνα Μπιτσάκη Τμήμα Επιστήμης Υπολογιστών Best Response Curves Used to solve for equilibria in games
Practice Exam 2. Conceptual Questions. 1. State a Basic identity and then verify it. (a) Identity: Solution: One identity is csc(θ) = 1
 Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Αλγόριθμοι και πολυπλοκότητα Minimum Spanning Trees
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Minimum Spanning Trees Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Minimum Spanning Trees 204 86 BOS SFO 33 LAX 1464 1235 849 PVD ORD
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Minimum Spanning Trees Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Minimum Spanning Trees 204 86 BOS SFO 33 LAX 1464 1235 849 PVD ORD
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
Network Algorithms and Complexity Παραλληλοποίηση του αλγορίθμου του Prim. Αικατερίνη Κούκιου
 Network Algorithms and Complexity Παραλληλοποίηση του αλγορίθμου του Prim Αικατερίνη Κούκιου Άδεια Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό,
Network Algorithms and Complexity Παραλληλοποίηση του αλγορίθμου του Prim Αικατερίνη Κούκιου Άδεια Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό,
Bounding Nonsplitting Enumeration Degrees
 Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Homomorphism in Intuitionistic Fuzzy Automata
 International Journal of Fuzzy Mathematics Systems. ISSN 2248-9940 Volume 3, Number 1 (2013), pp. 39-45 Research India Publications http://www.ripublication.com/ijfms.htm Homomorphism in Intuitionistic
International Journal of Fuzzy Mathematics Systems. ISSN 2248-9940 Volume 3, Number 1 (2013), pp. 39-45 Research India Publications http://www.ripublication.com/ijfms.htm Homomorphism in Intuitionistic
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS
 CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 216 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 216 - Ι. ΜΗΛΗΣ 9 DP II 1 Dynamic Programming ΓΕΝΙΚΗ ΙΔΕΑ 1. Ορισμός υπο-προβλήματος/ων
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 216 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 216 - Ι. ΜΗΛΗΣ 9 DP II 1 Dynamic Programming ΓΕΝΙΚΗ ΙΔΕΑ 1. Ορισμός υπο-προβλήματος/ων
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
ω ω ω ω ω ω+2 ω ω+2 + ω ω ω ω+2 + ω ω+1 ω ω+2 2 ω ω ω ω ω ω ω ω+1 ω ω2 ω ω2 + ω ω ω2 + ω ω ω ω2 + ω ω+1 ω ω2 + ω ω+1 + ω ω ω ω2 + ω
 0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Problem Set 3: Solutions
 CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
CRASH COURSE IN PRECALCULUS
 CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
Minimum Spanning Tree: Prim's Algorithm
 Minimum Spanning Tree: Prim's Algorithm 1. Initialize a tree with a single vertex, chosen arbitrarily from the graph. 2. Grow the tree by one edge: of the edges that connect the tree to vertices not yet
Minimum Spanning Tree: Prim's Algorithm 1. Initialize a tree with a single vertex, chosen arbitrarily from the graph. 2. Grow the tree by one edge: of the edges that connect the tree to vertices not yet
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Chapter 3: Ordinal Numbers
 Chapter 3: Ordinal Numbers There are two kinds of number.. Ordinal numbers (0th), st, 2nd, 3rd, 4th, 5th,..., ω, ω +,... ω2, ω2+,... ω 2... answers to the question What position is... in a sequence? What
Chapter 3: Ordinal Numbers There are two kinds of number.. Ordinal numbers (0th), st, 2nd, 3rd, 4th, 5th,..., ω, ω +,... ω2, ω2+,... ω 2... answers to the question What position is... in a sequence? What
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
A Note on Intuitionistic Fuzzy. Equivalence Relation
 International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
LTL to Buchi. Overview. Buchi Model Checking LTL Translating LTL into Buchi. Ralf Huuck. Buchi Automata. Example
 Overview LTL to Buchi Buchi Model Checking LTL Translating LTL into Buchi Ralf Huuck Buchi Automata Example Automaton which accepts infinite traces δ A Buchi automaton is 5-tuple Σ, Q, Q 0,δ, F Σ is a
Overview LTL to Buchi Buchi Model Checking LTL Translating LTL into Buchi Ralf Huuck Buchi Automata Example Automaton which accepts infinite traces δ A Buchi automaton is 5-tuple Σ, Q, Q 0,δ, F Σ is a
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Arithmetical applications of lagrangian interpolation. Tanguy Rivoal. Institut Fourier CNRS and Université de Grenoble 1
 Arithmetical applications of lagrangian interpolation Tanguy Rivoal Institut Fourier CNRS and Université de Grenoble Conference Diophantine and Analytic Problems in Number Theory, The 00th anniversary
Arithmetical applications of lagrangian interpolation Tanguy Rivoal Institut Fourier CNRS and Université de Grenoble Conference Diophantine and Analytic Problems in Number Theory, The 00th anniversary
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
SCITECH Volume 13, Issue 2 RESEARCH ORGANISATION Published online: March 29, 2018
 Journal of rogressive Research in Mathematics(JRM) ISSN: 2395-028 SCITECH Volume 3, Issue 2 RESEARCH ORGANISATION ublished online: March 29, 208 Journal of rogressive Research in Mathematics www.scitecresearch.com/journals
Journal of rogressive Research in Mathematics(JRM) ISSN: 2395-028 SCITECH Volume 3, Issue 2 RESEARCH ORGANISATION ublished online: March 29, 208 Journal of rogressive Research in Mathematics www.scitecresearch.com/journals
Overview. Transition Semantics. Configurations and the transition relation. Executions and computation
 Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Quadratic Expressions
 Quadratic Expressions. The standard form of a quadratic equation is ax + bx + c = 0 where a, b, c R and a 0. The roots of ax + bx + c = 0 are b ± b a 4ac. 3. For the equation ax +bx+c = 0, sum of the roots
Quadratic Expressions. The standard form of a quadratic equation is ax + bx + c = 0 where a, b, c R and a 0. The roots of ax + bx + c = 0 are b ± b a 4ac. 3. For the equation ax +bx+c = 0, sum of the roots
Parametrized Surfaces
 Parametrized Surfaces Recall from our unit on vector-valued functions at the beginning of the semester that an R 3 -valued function c(t) in one parameter is a mapping of the form c : I R 3 where I is some
Parametrized Surfaces Recall from our unit on vector-valued functions at the beginning of the semester that an R 3 -valued function c(t) in one parameter is a mapping of the form c : I R 3 where I is some
ΚΥΠΡΙΑΚΟΣ ΣΥΝΔΕΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY 21 ος ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ Δεύτερος Γύρος - 30 Μαρτίου 2011
 Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
2. THEORY OF EQUATIONS. PREVIOUS EAMCET Bits.
 EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
Abstract Storage Devices
 Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Θεωρία Γραφημάτων Θεμελιώσεις-Αλγόριθμοι-Εφαρμογές
 Θεωρία Γραφημάτων Θεμελιώσεις-Αλγόριθμοι-Εφαρμογές Ενότητα 8 ΤΕΛΕΙΑ ΓΡΑΦΗΜΑΤΑ Σταύρος Δ. Νικολόπουλος 2017-18 www.cs.uoi.gr/~stavros Εισαγωγή Βασικοί Αλγόριθμοι Γραφημάτων Πολυπλοκότητα χώρου και χρόνου:
Θεωρία Γραφημάτων Θεμελιώσεις-Αλγόριθμοι-Εφαρμογές Ενότητα 8 ΤΕΛΕΙΑ ΓΡΑΦΗΜΑΤΑ Σταύρος Δ. Νικολόπουλος 2017-18 www.cs.uoi.gr/~stavros Εισαγωγή Βασικοί Αλγόριθμοι Γραφημάτων Πολυπλοκότητα χώρου και χρόνου:
New bounds for spherical two-distance sets and equiangular lines
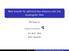 New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Models for Probabilistic Programs with an Adversary
 Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf6/ Άνοιξη 26 - I. ΜΗΛΗΣ NP-complete προβλήματα ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 26 - Ι. ΜΗΛΗΣ 6 NP-COMPLETENESS II Tree of reductions (partial) Cook s Th. Π NP SAT 3-SAT
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf6/ Άνοιξη 26 - I. ΜΗΛΗΣ NP-complete προβλήματα ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 26 - Ι. ΜΗΛΗΣ 6 NP-COMPLETENESS II Tree of reductions (partial) Cook s Th. Π NP SAT 3-SAT
Dynamic types, Lambda calculus machines Section and Practice Problems Apr 21 22, 2016
 Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
PARTIAL NOTES for 6.1 Trigonometric Identities
 PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
Elements of Information Theory
 Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
SOME PROPERTIES OF FUZZY REAL NUMBERS
 Sahand Communications in Mathematical Analysis (SCMA) Vol. 3 No. 1 (2016), 21-27 http://scma.maragheh.ac.ir SOME PROPERTIES OF FUZZY REAL NUMBERS BAYAZ DARABY 1 AND JAVAD JAFARI 2 Abstract. In the mathematical
Sahand Communications in Mathematical Analysis (SCMA) Vol. 3 No. 1 (2016), 21-27 http://scma.maragheh.ac.ir SOME PROPERTIES OF FUZZY REAL NUMBERS BAYAZ DARABY 1 AND JAVAD JAFARI 2 Abstract. In the mathematical
Mock Exam 7. 1 Hong Kong Educational Publishing Company. Section A 1. Reference: HKDSE Math M Q2 (a) (1 + kx) n 1M + 1A = (1) =
 Mock Eam 7 Mock Eam 7 Section A. Reference: HKDSE Math M 0 Q (a) ( + k) n nn ( )( k) + nk ( ) + + nn ( ) k + nk + + + A nk... () nn ( ) k... () From (), k...() n Substituting () into (), nn ( ) n 76n 76n
Mock Eam 7 Mock Eam 7 Section A. Reference: HKDSE Math M 0 Q (a) ( + k) n nn ( )( k) + nk ( ) + + nn ( ) k + nk + + + A nk... () nn ( ) k... () From (), k...() n Substituting () into (), nn ( ) n 76n 76n
Potential Dividers. 46 minutes. 46 marks. Page 1 of 11
 Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
CHAPTER 101 FOURIER SERIES FOR PERIODIC FUNCTIONS OF PERIOD
 CHAPTER FOURIER SERIES FOR PERIODIC FUNCTIONS OF PERIOD EXERCISE 36 Page 66. Determine the Fourier series for the periodic function: f(x), when x +, when x which is periodic outside this rge of period.
CHAPTER FOURIER SERIES FOR PERIODIC FUNCTIONS OF PERIOD EXERCISE 36 Page 66. Determine the Fourier series for the periodic function: f(x), when x +, when x which is periodic outside this rge of period.
Bayesian statistics. DS GA 1002 Probability and Statistics for Data Science.
 Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Solution Series 9. i=1 x i and i=1 x i.
 Lecturer: Prof. Dr. Mete SONER Coordinator: Yilin WANG Solution Series 9 Q1. Let α, β >, the p.d.f. of a beta distribution with parameters α and β is { Γ(α+β) Γ(α)Γ(β) f(x α, β) xα 1 (1 x) β 1 for < x
Lecturer: Prof. Dr. Mete SONER Coordinator: Yilin WANG Solution Series 9 Q1. Let α, β >, the p.d.f. of a beta distribution with parameters α and β is { Γ(α+β) Γ(α)Γ(β) f(x α, β) xα 1 (1 x) β 1 for < x
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
b. Use the parametrization from (a) to compute the area of S a as S a ds. Be sure to substitute for ds!
 MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
Section 7.6 Double and Half Angle Formulas
 09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ. ΕΠΛ342: Βάσεις Δεδομένων. Χειμερινό Εξάμηνο Φροντιστήριο 10 ΛΥΣΕΙΣ. Επερωτήσεις SQL
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΕΠΛ342: Βάσεις Δεδομένων Χειμερινό Εξάμηνο 2013 Φροντιστήριο 10 ΛΥΣΕΙΣ Επερωτήσεις SQL Άσκηση 1 Για το ακόλουθο σχήμα Suppliers(sid, sname, address) Parts(pid, pname,
ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΕΠΛ342: Βάσεις Δεδομένων Χειμερινό Εξάμηνο 2013 Φροντιστήριο 10 ΛΥΣΕΙΣ Επερωτήσεις SQL Άσκηση 1 Για το ακόλουθο σχήμα Suppliers(sid, sname, address) Parts(pid, pname,
Αλγόριθμοι και πολυπλοκότητα Graphs
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Graphs Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Graphs ORD 843 SFO 802 743 337 233 LAX DFW Graphs Outline and Reading Graphs ( 6.)
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα Graphs Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών Graphs ORD 843 SFO 802 743 337 233 LAX DFW Graphs Outline and Reading Graphs ( 6.)
Second Order RLC Filters
 ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
Math 446 Homework 3 Solutions. (1). (i): Reverse triangle inequality for metrics: Let (X, d) be a metric space and let x, y, z X.
 Math 446 Homework 3 Solutions. (1). (i): Reverse triangle inequalit for metrics: Let (X, d) be a metric space and let x,, z X. Prove that d(x, z) d(, z) d(x, ). (ii): Reverse triangle inequalit for norms:
Math 446 Homework 3 Solutions. (1). (i): Reverse triangle inequalit for metrics: Let (X, d) be a metric space and let x,, z X. Prove that d(x, z) d(, z) d(x, ). (ii): Reverse triangle inequalit for norms:
SCHOOL OF MATHEMATICAL SCIENCES G11LMA Linear Mathematics Examination Solutions
 SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Homomorphism of Intuitionistic Fuzzy Groups
 International Mathematical Forum, Vol. 6, 20, no. 64, 369-378 Homomorphism o Intuitionistic Fuzz Groups P. K. Sharma Department o Mathematics, D..V. College Jalandhar Cit, Punjab, India pksharma@davjalandhar.com
International Mathematical Forum, Vol. 6, 20, no. 64, 369-378 Homomorphism o Intuitionistic Fuzz Groups P. K. Sharma Department o Mathematics, D..V. College Jalandhar Cit, Punjab, India pksharma@davjalandhar.com
SYLLABUS CHAPTER - 1 : INTRODUCTION TO ALGORITHMS CHAPTER - 2 : DIVIDE AND CONQUER CHAPTER - 3 : GREEDY METHOD
 i SYLLABUS UNIT - I CHAPTER - 1 : INTRODUCTION TO ALGORITHMS AND ELEMENTARY DATA A STRUCTURES Order Notation, Analysis of Algorithm, Review of Elementary Data Structures, Heaps and Heap Sort, Hashing,
i SYLLABUS UNIT - I CHAPTER - 1 : INTRODUCTION TO ALGORITHMS AND ELEMENTARY DATA A STRUCTURES Order Notation, Analysis of Algorithm, Review of Elementary Data Structures, Heaps and Heap Sort, Hashing,
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Optimal Impartial Selection
 Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
ORDINAL ARITHMETIC JULIAN J. SCHLÖDER
 ORDINAL ARITHMETIC JULIAN J. SCHLÖDER Abstract. We define ordinal arithmetic and show laws of Left- Monotonicity, Associativity, Distributivity, some minor related properties and the Cantor Normal Form.
ORDINAL ARITHMETIC JULIAN J. SCHLÖDER Abstract. We define ordinal arithmetic and show laws of Left- Monotonicity, Associativity, Distributivity, some minor related properties and the Cantor Normal Form.
Αλγόριθμοι Επανάληψη για πρόοδο
 Αλγόριθμοι Επανάληψη για πρόοδο Προτεινόμενη βιβλιογραφία: S. Dasgupta, C.H. Papadimitriou, ad U.V. Vazirai «Αλγόριθμοι» Κλειδάριθμος 2009 Κεφάλαια 0,3,4,5. http://www.cs.berkeley.edu/~vazirai/algorithms/chap0.pdf
Αλγόριθμοι Επανάληψη για πρόοδο Προτεινόμενη βιβλιογραφία: S. Dasgupta, C.H. Papadimitriou, ad U.V. Vazirai «Αλγόριθμοι» Κλειδάριθμος 2009 Κεφάλαια 0,3,4,5. http://www.cs.berkeley.edu/~vazirai/algorithms/chap0.pdf
Uniform Convergence of Fourier Series Michael Taylor
 Uniform Convergence of Fourier Series Michael Taylor Given f L 1 T 1 ), we consider the partial sums of the Fourier series of f: N 1) S N fθ) = ˆfk)e ikθ. k= N A calculation gives the Dirichlet formula
Uniform Convergence of Fourier Series Michael Taylor Given f L 1 T 1 ), we consider the partial sums of the Fourier series of f: N 1) S N fθ) = ˆfk)e ikθ. k= N A calculation gives the Dirichlet formula
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ. Δομές Δεδομένων. Ιωάννης Γ. Τόλλης Τμήμα Επιστήμης Υπολογιστών Πανεπιστήμιο Κρήτης
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Δομές Δεδομένων Ιωάννης Γ. Τόλλης Τμήμα Επιστήμης Υπολογιστών Πανεπιστήμιο Κρήτης Χρηματοδότηση Το παρόν εκπαιδευτικό υλικό έχει αναπτυχθεί στα πλαίσια του εκπαιδευτικού
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Δομές Δεδομένων Ιωάννης Γ. Τόλλης Τμήμα Επιστήμης Υπολογιστών Πανεπιστήμιο Κρήτης Χρηματοδότηση Το παρόν εκπαιδευτικό υλικό έχει αναπτυχθεί στα πλαίσια του εκπαιδευτικού
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Graph Algorithms. Παρουσίαση στα πλαίσια του μαθήματος «Παράλληλοι Αλγόριθμοι» Καούρη Γεωργία Μήτσου Βασιλική
 Graph Algorithms Παρουσίαση στα πλαίσια του μαθήματος «Παράλληλοι Αλγόριθμοι» Καούρη Γεωργία Μήτσου Βασιλική Περιεχόμενα minimum weight spanning tree connected components transitive closure shortest paths
Graph Algorithms Παρουσίαση στα πλαίσια του μαθήματος «Παράλληλοι Αλγόριθμοι» Καούρη Γεωργία Μήτσου Βασιλική Περιεχόμενα minimum weight spanning tree connected components transitive closure shortest paths
