UNIVERSITY OF THESSALY
|
|
|
- ÍΕρρίκος Αλαφούζος
- 8 χρόνια πριν
- Προβολές:
Transcript
1 Πανεπιστήμιο Θεσσαλίας Τμήμα Ηλεκτρολόγων Μηχανικών & Μηχανικών Υπολογιστών Διπλωματική εργασία Θέμα: «Ποιοτική σύγκριση και αξιολόγηση πρωτοκόλλων δρομολόγησης σε ασύρματα δίκτυα πλέγματος» Βουλγαράκης Δημήτριος UNIVERSITY OF THESSALY Επιβλέπων καθηγητής: Κοράκης Αθανάσιος (Λέκτορας Καθηγητής) Συνεπιβλέπων καθηγητής: Αργυρίου Αντώνιος (Λέκτορας Καθηγητής) Βόλος, 2015
2 University of Thessaly Department of Electrical & Computer Engineering Thesis Title: «Evaluation of routing algorithms on top of wireless mesh networks» Voulgarakis Dimitrios UNIVERSITY OF THESSALY Supervisor professor: Korakis Athanasios Co-supervisor professor: Argyriou Antonios Volos, 2015
3 Ευχαριστίες Η παρούσα Διπλωματική εργασία πραγματοποιήθηκε στο τμήμα Ηλεκτρολόγων Μηχανικών και Μηχανικών Υπολογιστών Βόλου. Θα ήθελα να ευχαριστήσω τον επιβλέποντα καθηγητή και λέκτορα του τμήματος Ηλεκτρολόγων Μηχανικών και Μηχανικών Υπολογιστών, κ. Κοράκη Αθανάσιο, που μου έδωσε την ευκαιρία να ασχοληθώ με αυτό το θέμα. Επίσης, θα ήθελα να ευχαριστήσω θερμά τον υποψήφιο διδάκτορα, Χούμα Κωνσταντίνο, που καθ όλη τη διάρκεια της διπλωματικής εργασίας ήταν εκεί και με καθοδηγούσε με χρήσιμες συμβουλές και προτάσεις. Τέλος, ένα μεγάλο ευχαριστώ στην οικογένεια και τους φίλους μου, που με στήριζαν όλο αυτό το διάστημα.
4 CONTENTS Ευχαριστίες...3 Περίληψη...6 Abstract Introduction Dynamic routing protocols Proactive protocols Reactive protocols AODV: Ad hoc On-demand Distance Vector Introduction Overview AODV Operation Route Discovery Generating and Forwarding a RREQ Generating a RREP Generating Gratuitous RREP Receiving and Forwarding RREP Route Maintenance Hello Messages Message Formats Route Request (RREQ) Message Format Route Reply (RREP) Message Format Route Error (RERR) Message Format OLSR: Optimized Link State Routing Introduction Overview OLSR Operation Link Sensing Efficient Control Flooding Using MPRs 21
5 4.6 Optimal Path Calculation Using Shortest Path Algorithm Packet Format Experimentation Experimentation in Wireless Testbeds NITOS Testbed Outdoor Nodes Experiment Parameters and Setup Experimental results on single-path topology Experimental results on multi-path topology...32 References...36
6 Περίληψη Σκοπός της διπλωματικής εργασίας είναι η πειραματική σύγκριση δύο πρωτοκόλλων δρομολόγησης σε πραγματικά δίκτυα πλέγματος. Συγκεκριμένα, αξιολογούμε την απόδοση του OLSR, το οποίο είναι proactive πρωτόκολλο και του AODV το οποίο είναι ένα reactive πρωτόκολλο. Όλα τα πειράματα πραγματοποιήθηκαν στους εξωτερικούς κόμβους του NITOS. Για την αξιολόγηση των πρωτοκόλλων χρησιμοποιήθηκαν δύο ειδών τοπολογίες, μία μονού μονοπατιού και μία πολλαπλών διαδρομών. Οι μετρικές που χρησιμοποιήθηκαν για την αξιολόγηση ήταν: η αναλογία παράδοσης πακέτων (PDR), η μέση καθυστέρηση του κάθε πρωτοκόλλου και το μέσο throughput της μετάδοσης.
7 Abstract The purpose of this thesis is to report an experimental comparison, on real ad hoc networks, between two routing protocols. Specifically, we evaluate the performance of Optimized Link State Routing Protocol (OLSR) which is a proactive protocol and Ad hoc On-Demand Distance Vector (AODV) which is a reactive protocol. We compared them in NITOS outdoor testbed nodes. To evaluate routing protocols performance we used two configurations: i) a single-path string network, ii) a mesh multi-path network. In the performance comparison we analyzed metrics such as Packet Delivery Ratio (PDR), average end-to-end delay and mean throughput.
8 1 Introduction Routing is the act of moving information from a source to a destination in a network. Along the way, at least one intermediate node typically is encountered. The topic of routing has been covered in computer science literature for more than two decades, but routing achieved commercial popularity as late as the mid-1980s. The primary reason for this time lag is that networks in the 1970s were simple, homogeneous environments. Only relatively recently has large-scale internetworking become popular. The main tasks of a routing protocol are topology discovery and topology maintenance. The topology discovery phase is usually periodic advertisements about a node's location as well as exchange of certain request-reply messages. However, topology maintenance is detecting link connectivity breaks and fix the broken link, if possible. Routing protocols use several metrics to calculate the best path for routing the packets to its destination. These metrics could be number of hops, which is used by the routing algorithm to determine the optimal path for the packet to its destination. The process of path determination is that, routing algorithms initialize and maintain routing tables, which contain the total route information for the packet. These route information varies from one routing algorithm to another. Routing is mainly classified into static routing and dynamic routing. Static routing refers to the routing strategy being stated manually or statically, in the router. Static routing maintains a routing table usually written by a network s administrator. The routing table doesn t depend on the state of the network status. Dynamic routing refers to the routing strategy that is being learnt by a routing protocol. This routing mainly depends on the state of the network i.e., the routing table is affected by the activeness of the destination. The major disadvantage of static routing is that if a new router is added or removed in the network then it is the responsibility of the administrator to make the necessary changes in the routing tables. But this is not the case with dynamic routing as each router announces its presence by flooding the information packet in the network so that every router within the network learn about the newly added or removed router and its entries. 2 Dynamic routing protocols Dynamic routing protocols are classified depending on what the routers tell each other and how they use the information to form their routing tables. Most of the protocols available in the networks fit into one of the two categories. The two main categories of dynamic routing protocols in packet switching networks are distance vector and link state. Both categories use the shortest path algorithm to find the best next hop neighbor. Link state routing is performed by every switching node in the network. The basic concept of link-state routing is
9 that every node constructs a map of the connectivity to the network, in the form of a graph, showing which nodes are connected to which other nodes. Each node then independently calculates the next best logical path from it to every possible destination in the network. The collection of best paths will then form the node's routing table. In distance vector protocols, each router over the network send the neighboring routers, the information about destination that it knows how to reach. Furthermore the routers send two pieces of information: i) the router tells how far it thinks the destination is ii) it tells in what direction (vector) to use to get to the destination. When the router receives the information from the others, it could then develop a table of destination addresses, distances and associated neighboring routers. From this table then, selects the shortest route to the destination. Using a distance vector protocol, the router simply forwards the packet to the neighboring host (or destination) with the available shortest path in the routing table and assumes that the receiving router will know how to forward the packet beyond that point. Compared to link-state protocols, distance-vector routing protocols have less computational complexity and message overhead. Routing protocols can be classified in many ways depending on routing algorithm and network organization. Depending on the network structure, classification can be flat, hierarchical routing and geographic position assisted, while based on routing strategy used, they can categorized as table driven or on-demand as shown in Figure 2.1.
10 2.1 Proactive protocols Proactive routing protocols attempt to maintain consistent and updated routing information for every pair of network nodes by proactively propagating route updates at fixed rime intervals (periodically). Proactive routing is also known as table driven routing. The main advantage of such an algorithm is that there is no delay in establishing a communication session and routing table is updated as soon as there is a change in topology. Disadvantages are additional control traffic to keep the routing table up to date irrespective of whether all the routes are used in a session or not. Proactive protocols are not suitable for larger networks, as they need to maintain node entries for each and every node in the routing table of every node. This causes more overhead in the routing table leading to consumption of more bandwidth. Example of proactive algorithm is Optimized Link State Routing (OLSR). 2.2 Reactive protocols Reactive routing is also called on-demand routing as the routes are established only when needed to forward the data packets. They don t maintain routing information or routing activity at the network nodes if there is no communication. If a node wants to send packets to another node then this protocol searches for the route in an on-demand manner and establishes the connection in order to transmit and receive the packets. The route discovery usually occurs by flooding the route request packets throughout the network. This algorithm has significantly low routing overhead when the traffic is light and network is less dynamic, since there is no need maintain the routes when there is no data traffic. The major disadvantages are longer delay in establishing the routes for forwarding the data and excessive flooding of the control messages that may lead to network block. Example of reactive routing are Ad hoc On-demand Distance Vector (AODV).
11 3 AODV: Ad hoc On-demand Distance Vector 3.1 Introduction Ad hoc On-demand Distance Vector (AODV), as the name suggests is an ondemand protocol designed for mobile ad hoc networks. This protocol responds quickly to changing link conditions and link breakages. The nodes mark the routes as invalid whenever there is a link breakage. AODV does not require a node to maintain routes to destinations that are not in active communication. The operation of AODV is loop-free, by using destination sequence numbers. These also allow nodes to use the most recent route to a destination. The routing table information includes the destination address and the next hop address with the number of hops required to reach the destination. Also, the most recent destination sequence number associated with destination and lifetime of the route is stored in the table. If during the lifetime, the route is not used, the routing table entry is discarded. 3.2 Overview The message types defined by AODV are Route Request (RREQ), Route Reply (RREP) and Route Error (RERR). As long as the endpoints of a communication connection have valid routes to each other, AODV does not play any role. When a route to a new destination is needed, a node broadcasts the RREQ message to find a route. A route is found when the RREQ reaches the destination itself, or an intermediate node that has a fresh enough route to the destination. The route is made available by unicasting the RREP message back to the source of the destination. Since, each node that receives the RREQ caches the route back to the source, the RREP can be unicasted to the origination of the RREQ. The link status of active routes is continuously monitored for any link breakage. When a link breaks, RERR message is propagated down the route to notify the affected nodes about the loss of link. The purpose of RERR message is to indicate which destinations are now unreachable because of the link breakage. Each node keeps a precursor list that contains the IP address for each of its neighbors that are likely to use it as a next hop towards each destination.
12 Figure 3.1: AODV Operation 3.3 AODV Operation The basic operation of AODV can be divided into three phases: > Route discovery > Route maintenance > Hello message 3.4 Route Discovery Generating and Forwarding a RREQ When a destination is previously unknown to the node or the route to the destination is no longer valid, the node propagates a RREQ. The Destination Sequence Number (DSN) is the last known DSN for this destination. If no sequence number is known, unknown sequence number flag is set. After broadcasting a RREQ, the node waits for a RREP. If the RREP is not received with NET TRAVERSAL TIME milliseconds, the node rebroadcast the RREQ, up to a maximum of RREQ RETRIES times, which is set to 2. When a node receives a RREQ, it creates or updates the route to the previous hop without valid sequence number and then checks if it has received the RREQ with same originator IP address and RREQ ID. If such a RREQ has been received, the node removes the newly received RREQ. If the RREQ received is not removed, the intermediate node searches for a reverse route to the Originator IP address. If the reverse route already exists, it is updated only if the originator sequence number is higher than the destination sequence number of the originator IP address in the routing table or if the sequence numbers are equal but the hop
13 count in RREQ is smaller than the existing hop count in the routing table. The RREQ is rebroadcasted if the active route does not exist in its routing table or if the existing DSN is smaller than the DSN field of the RREQ. The Time to Live (TTL) in the outgoing RREQ is decremented by one and the hop count field is incremented by one to account for the new hop through the intermediate node Generating a RREP A node generates a RREP if: > It is itself the destination. > It has an active route to the destination The RREP is unicast to the next hop towards the originator of the RREQ. As the RREP is propagated, the hop count field in RREP is incremented by one at each hop Generating Gratuitous RREP When a node receives a RREQ and responds with a RREP, it discards the RREQ. If the RREQ has 'G' flag set, and the intermediate node replies to the RREQ, it unicasts a gratuitous RREP to the destination node Receiving and Forwarding RREP When a node receives a RREP, it searches for a route to the previous hop. Once the route to the destination is created or updated in the route table, the route is marked active and the next hop is assigned to the node from which RREP was received. Therefore, the node can use this route to forward the data to the destination. If the node is not indicated by the Originator IP address in RREP, then the RREP packet is forwarded towards the next hop, selected based on the route table entry. When a node forwards a RREP, the precursor list for the corresponding destination node is updated by adding to it the next hop node to which the RREP is forwarded.
14 3.5 Route Maintenance A RERR message is generated in following three scenarios: 1. While transmitting data, if a node detects a link break for the next hop of an active route, the node makes a list of unreachable destinations containing the unreachable neighbors and other destinations that use the unreachable neighbor as next hop. 2. A node receives a packet for the node it does not have an active route in its routing table. For this, there is only one unreachable destination. 3. If a node receives a RERR from a neighbor for one or more active routes. The list consists of destinations in RERR for which there exists a corresponding entry in the local routing table that has the transmitter of the received RERR as the next hop. AODV has a mechanism called Local Repair by which the upstream node of the broken link attempts to repair the link locally instead of sending RERR. The node initiating the local repair follows the route discovery phase. If the node does not receive a RREP, it then transmits a RERR message for that destination. The process of local repair may result in greater path lengths to the destinations for which local repair was initiated. 3.6 Hello Messages AODV maintains network connectivity by reception of broadcast hello messages on the active routes. A node that is a part of an active route periodically broadcasts hello messages, which are RREP messages with TTL=1, to announce its presence. If a node does not receive a hello message within a specified interval, then it is assumed that the neighbor node is no longer in transmission range and the connectivity to this node has been lost. Whenever a node receives a hello message from a neighbor, the node checks if it has an active route to the neighbor and if not, it creates one. If the route already exists, the TTL for the route is increased.
15 3.7 Message Formats Route Request (RREQ) Message Format H ( ype 5 R G D U Reserved Hop Court H ) RREQ ID h Destination IP Address h Destination Sequence Number Originator I 5 Address Originator Sequence Number f I l I I H h-4 The format of the Route Request message is illustrated above, and contains the following fields: Type 1 J R G D U Join flag, reserved for multicast. Repair flag, reserved for multicast. Gratuitous RREP flag, indicates whether a gratuitous RREP should be unicast to the node specified in the Destination IP Address field Destination only flag, indicates only the destination may respond to this RREQ Unknown sequence number; indicates the destination sequence number is unknown Reserved Sent as 0, ignored on reception. Hop Count The number of hops from the Originator IP Address to the node handling the request. RREQ ID A sequence number uniquely identifying the particular RREQ when taken in conjunction with the originating node's IP address.
16 Destination IP Address The IP address of the destination for which a route is desired. Destination Sequence Number The latest sequence number received in the past by the originator for any route towards the destination. Originator IP Address The IP address of the node which originated the Route Request. Originator Sequence Number The current sequence number to be used in the route entry pointing towards the originator of the route request Route Reply (RREP) Message Format I Type R A Reserved Prefix Sz Hop Count Destination IP address Destination Sequence Number H I I H Originator I 3 address Lifetime The format of the Route Reply message is illustrated above, and contains the following fields: Type 2 R A Repair flag, used for multicast. Acknowledgment required Reserved Sent as 0, ignored on reception.
17 Prefix Size If nonzero, the 5-bit Prefix Size specifies that the indicated next hop may be used for any nodes with the same routing prefix (as defined by the Prefix Size) as the requested destination. Hop Count The number of hops from the Originator IP Address to the Destination IP Address. For multicast route requests this indicates the number of hops to the multicast tree member sending the RREP. Destination IP Address The IP address of the destination for which a route is supplied. Destination Sequence Number The destination sequence number associated to the route. Originator IP Address The IP address of the node which originated the RREQ for which the route is supplied. Lifetime The time in milliseconds for which nodes receiving the RREP consider the route to be valid Route Error (RERR) Message Format S S S Type Γ11 Reserved DestCourt Unreachable D e s tin a tio n IP Address (1) Unreachable D e s tin a tio n Sequerce Number (1) I I H j A d c itio n a l Unreachable D e s tin a tio n IP Addresses ( i f needed) A d d itio n a l. Unreachable D e s tin a tio n Sequence Numbers ( i f needed) The format of the Route Error message is illustrated above, and contains the following fields:
18 Type 3 N No delete flag, set when a node has performed a local repair of a link, and upstream nodes should not delete the route. Reserved Sent as 0, ignored on reception. DestCount The number of unreachable destinations included in the message, MUST be at least 1. Unreachable Destination IP Address The IP address of the destination that has become unreachable due to a link break. Unreachable Destination Sequence Number The sequence number in the route table entry for the destination listed in the previous Unreachable Destination IP Address field.
19 4 OLSR: Optimized Link State Routing 4.1 Introduction The Optimized Link State Routing (OLSR) is a proactive table driven protocol for mobile ad hoc networks. It eases efficient flooding of control messages throughout the network by using selected nodes called MultiPoint Relays (MPRs). MPRs are selected by each node and are used to forward control messages resulting in a distributed operation of the protocol. In addition to this, a node continuously maintains routes to all destinations in the network, thus making the protocol suited for traffic pattern that is random and sporadic. 4.2 Overview The protocol is an optimization of classical link state routing algorithm and uses the concept of MultiPoint Relays (MPRs). The problem of flooding the network with control messages is overcome by the MPR nodes. A node periodically exchanges hello messages to discover its two-hop neighbor. Using this information, each node selects a set of MPRs, which are one-hop neighbors. A node selects MPR such that there exists a path to each of its twohop neighbors via a node selected as a MPR. The main responsibility of MPR is to forward the control messages throughout the network, thus minimizing the number of transmissions. MPRs periodically broadcast the control information, there by announcing the reachability to the nodes that have selected it as a MPR. A node uses this information to determine next hop destinations for all the nodes in the network using the shortest path algorithm. Because of its proactive nature, routing overhead is generally greater than that of a reactive protocol.
20 Figure 4.1: Multipoint relays selection 4.3 OLSR Operation The core functioning of OLSR can be divided into three processes namely: 1. Link Sensing 2. Efficient control flooding using MPR 3. Optimal path calculation using shortest path algorithm. 4.4 Link Sensing Nodes periodically exchanges HELLO message with each other. A hello message mainly consists of link information and neighborhood information. The three important tasks performed by hello message exchange are: i) link sensing ii) neighbor detection iii) MPR selection signaling. For neighbor and link sensing, a hello message typically comprised of list of links and list of onehop symmetric neighbors. A hello message is broadcasted by a node to its neighbors and is never forwarded by other nodes. On reception of a hello message, a node performs a link sensing, neighbor detection and MPR selection set population. Each node in the network selects its MPR set. MPR set is elected based on the rule: MPR (N) is selected such that all two-hop neighbors of N are covered by (one-hop neighbors) of MPR (N). Smaller the MPR set, minimum is its protocol overhead.
21 4.5 Efficient Control Flooding Using MPRs Due to the proactive nature of OLSR, each node maintains the partial topology graph of the network. This information is extracted from Topology Control (TC) messages and is then used for calculating the shortest paths to destinations. A MPR node broadcasts a TC message periodically that is propagated across the network using the other MPR nodes. A TC message contains MPR selector set of the source of the message and is forwarded by MPR if and only if it received the message for the first time by that node and it is in the MPR set of the previous hop node. This controlled flooding results in minimized retransmissions. 4.6 Optimal Path Calculation Using Shortest Path Algorithm A routing table is maintained by every node, which is updated whenever a change in the topology is detected. To populate a routing table, shortest path algorithm is used on the partial topology graph obtained from TC messages. It is important to note that OLSR is not involved in forwarding of data packets.
22 4.7 Packet Format The basic layout of any packet in OLSR is as follows (omitting IP and UDP headers): Θ Ι Jacket Length Packet Sequence Number H--h h- + -H h- + -H Message Type Vtlne Message Size Originator Address Tine To Live ---Hop Count Message Sequence Number I : MESSAGE : I Message Type Vtine Message Size Originator Address Tine To Live ---Hop Count Message Sequerce Number I : MESSAGE : I (etc.) I I I I Packet Header Packet Length The length (in bytes) of the packet Packet Sequence Number The Packet Sequence Number (PSN) MUST be incremented by one each time a new OLSR packet is transmitted. "Wrap-around" is handled as described in section 19. A separate Packet Sequence Number is maintained for each interface such that packets transmitted over an interface are sequentially enumerated. The IP address of the interface over which a packet was transmitted is obtainable from the IP header of the packet. If the packet contains no messages (i.e., the Packet Length is less than or equal to the size of the packet header), the packet MUST silently be discarded.
23 For IPv4 addresses, this implies that packets, where the Packet Length <16 MUST silently be discarded. Message Header Message Type Vtime This field indicates which type of message is to be found in the "MESSAGE" part. Message types in the range of are reserved for messages in this document and in possible extensions. This field indicates for how long time after reception a node MUST consider the information contained in the message as valid, unless a more recent update to the information is received. The validity time is represented by its mantissa (four highest bits of Vtime field) and by its exponent (four lowest bits of Vtime field). In other words: validity time = C*(1+a/16)* 2Ab [in seconds] where a is the integer represented by the four highest bits of Vtime field and b the integer represented by the four lowest bits of Vtime field. The proposed value of the scaling factor C is specified in section 18. Message Size This gives the size of this message, counted in bytes and measured from the beginning of the "Message Type" field and until the beginning of the next "Message Type" field (or - if there are no following messages - until the end of the packet). Originator Address This field contains the main address of the node, which has
24 originally generated this message. This field SHOULD NOT be confused with the source address from the IP header, which is changed each time to the address of the intermediate interface which is re-transmitting this message. The Originator Address field MUST *NEVER* be changed in retransmissions. Time To Live This field contains the maximum number of hops a message will be transmitted. Before a message is retransmitted, the Time To Live MUST be decremented by 1. When a node receives a message with a Time to Live equal to 0 or 1, the message MUST NOT be retransmitted under any circumstances. Normally, a node would not receive a message with a TTL of zero. Thus, by setting this field, the originator of a message can limit the flooding radius. Hop Count This field contains the number of hops a message has attained. Before a message is retransmitted, the Hop Count MUST be incremented by 1. Initially, this is set to '0' by the originator of the message. Message Sequence Number While generating a message, the "originator" node will assign a unique identification number to each message. This number is inserted into the Sequence Number field of the message. The sequence number is increased by 1 (one) for each message originating from the node. "Wrap-around" is handled as described in section 19. Message sequence numbers are used to ensure that a given message is not retransmitted more than once by any node.
25 5 Experimentation 5.1 Experimentation in Wireless Testbeds A testbed is a platform for experimentation of large development projects. A wireless network testbed consists of the hardware and software needed, in order to give researchers a wide range of environments in which to develop, debug, and evaluate their wireless network systems and protocols, in realistic conditions. 5.2 NITOS Testbed NITOS (Network Implementation Testbed using Open Source code) is a testbed created by the Network Implementation Testbed Laboratory of the Computer and Communication Engineering Department at University of Thessaly, in collaboration with the Centre for Research and Technology Hellas (CERTH). The NITOS platform is open to any researchers who would like to test their protocols in a real-time wireless network. They are given the opportunity to implement their protocols and study their behavior in a custom environment. The testbed s capabilities are constantly extended. Up to now it consists of 45 nodes of different types. More specifically there are 10 Orbit nodes, 15 diskless nodes and 20 custom made outdoor nodes. For the purpose of this thesis we used the outdoor nodes. Figure 5.1: NITOS nodes
26 5.3 Outdoor Nodes The outdoor nodes have been developed by UTH in order to enable experimentation that requires high processing power. They feature 2-core Intel CPU, a new generation solid state drive, a USB web camera and are also equipped with a/b/g and a/b/g/n wireless interfaces. Furthermore, they are equipped with a Chassis Manager (CM) card in order to enable remote control of their operational status. Another feature of the attached CM card is the support of real time sensor measurements, gathered through their integrated light, temperature and humidity sensors. Detailed specifications of the Outdoor nodes can be found in the following table. Table 1: Outdoor nodes specifications Motherboard CPU RAM Wireless interfaces Chassis Manager Card Storage Power supply Antennas Pigtails Features 2 Gigabit network interfaces and supports 2 wireless interfaces Intel Core 2 Duo P Ghz 2G DDR3 Atheros 802/11 a/b/g & Atheros a/b/g/n (ΜΙΜΟ) UTH's CM card Solid state drive 350 Watt mini-atx Multi-band 5dbi, operates both on 2,4Ghz& 5Ghz High quality pigtails (UFL to RP-SMA) Figure 5.2: NITOS outdoor nodes
27 5.4 Experiment Parameters and Setup AODV implementation developed by Uppsala University called AODV-UU version number was used. For OLSR, OLSRd implementation version number was used. Both these implementations are freely available on the internet. To evaluate routing protocols performance we mainly used two configurations: i) a mesh multi-path network, ii) a single-path string network. To have a meaningful comparison between them, we introduced some traffic at the application layer using the ping utility. In the performance comparison we analyzed i) Packet Delivery Ratio (PDR) at the application level which is the ratio of application packets delivered to the destination and the total number of generated packets ii) Average end-lo-end delay introduced in data transfer measured at application level. Also IPERF traffic generator used to generate UDP traffic flows. IPERF is a network performance tool that measures TCP and UDP bandwidth performances. The UDP traffic was used to capture the mean throughput depending on the packet size. Measurements during the experiments were collected and evaluated using Wireshark. Figure 5.4: Multi-path topology
28 5.5 Experimental results on single-path topology To create this single path topology we used /sbin/iptables -A INPUT -m mac - mac-source mac_address -j DROP command to block traffic from specific MAC Addresses. The first experiment was conducted using the same two-hop (A B C) and three-hop (A B C D) topology, as shown in figure 5.3 and measuring the throughput while varying the data packet sizes from 256, 512 and 1024 bytes. IPERF was used to generate UDP traffic flows with -l option for various data packets. The main objective behind this was to understand if there was a correlation between packet size and observed throughput. Figure 5.5 and Figure 5.6 show the mean throughput over an experimental duration of 30 seconds. As the size of data packet is increased, mean throughput also increases. It can be seen from the results that throughput scales down as the number of nodes increases. Adding more hops increases protocol s overhead. Note that the throughput for AODV decreases at a faster rate compared to OLSR, as hop count increases. Due to AODV s higher overhead. is Packet Size {in bytes) AODV OLSR Figure 5.5: Performance-Varying Packet size in two-hop topology
29 Mean Throughput (in Mbps) ,572 0, Packet Size (in bytes) AODV 10LSR Figure 5.6: Performance-Varying Packet size in three-hop topology
30 In second experiment we used the single-path topology varying the hop count from one to three, to observe packet delivery ratio for both protocols. For this experiment ping utility was used to create traffic at the application layer between the sender A and the other nodes in the string topology using the sequence B, C, D. Specifically, the duration of each ping operation is variable depending on the distance from destination (1 minute for node B at 1-hop, 2 minutes for C at 2-hops, and 3 minutes for C at 3-hops). Considering the testbed s results, note that OLSR is able to deliver all sent packets for 1-hop destination, while AODV introduces a 16.4% packet loss. For 2-hop destination both protocols introduce a 13.9% packet loss. For 3-hop distance OLSR introduces a 9.9% packet loss, while AODV introduces 38.9%. So, OLSR is more reliable than AODV for static single-path topologies. Figure 5.7: Packet Delivery Ratio in single-path topology
31 Another experiment was conducted to measure the delay each protocol generates in single-path topology varying the hop count from one to three. Ping utility also used for this experiment. For AODV in order to find its delay we subtracted the time of the first RREQ from the time of first ICMP request in the node which creates the UDP traffic. In the case of OLSR, the delay of the protocol is the subtraction of first and last OLSR packets before the first ICMP request was sent. As a proactive protocol, this is the delay to specify the network s topology. As we see from the diagrams, as the number of hops increases, the delay of AODV protocol remains constant around 15 seconds. But in the case of OLSR, protocol s delay goes up as the complexity of network increases r97i Number of hops AODV OLSR Figure 5.8: Delay in single-path topology
32 5.6 Experimental results on multi-path topology We also studied protocols behavior on multi-path topology as in figure 5.4. To create this multi-path topology we used /sbin/iptables -A INPUT -m mac - mac-source mac_address -j DROP command to block traffic from specific MAC Addresses. For this experiment ping utility was used to create UDP traffic at the application layer between the sender node A and node D. Both protocols followed the shortest path to the destination. Considering the testbed s results, note that OLSR introduces a 16% packet loss, while AODV introduces 19%. So, OLSR is more reliable than AODV for static multi-path topologies. Packet Delivery Ratio for 100 second transmission from node A to D are presented below: 100,00% 95,00% 90,00% S5,00% a so,oo% Q. 75,00% 70,00% 65,00% 60,00% AODV OLSR Figure 5.9: Packet Delivery Ratio in multi-path topology
33 For multi-path topology, we also performed two types of experiments. In the first one, node A starts pinging continuously the same destination D as in figure 5.4, and after a while, node B which is included in the shortest path disconnects itself from the network. OLSR showed a correct behavior. Routing tables were correctly filled in with the shortest path to each destination. In addition the routes were quickly updated with an alternative path upon the node B removal. In case of AODV, each sender was always able to discover the correct path towards each destination, even though the discovery procedure was more timeexpensive. In addition, the node was able to discover a new route towards the destination, after the disconnection event, including more delay than OLSR protocol. OLSR is also more reliable, as we see in the chart below. 5 4r5 4 AODV QLSR Figure 5.10: Protocol delay in multi-path topology with disconnection event 100,00% 95,00% 90,00% S5,00% 35,00% a so,oo% Q. 75,00% 70,00% 65,00% 60,00% AODV 0L5R Figure 5.11: Packet Delivery Ratio in multi-path topology with disconnection event
34 In the second experiment, we studied how fast each protocol switched to an optimal route (shortest path) if a neighboring node in transmission range comes out in the middle of communication. The initial topology used was a three-hop linear topology, as shown in figure After a while, node E appears, so that a 2-hop path to the destination can be followed. In case of OLSR, protocol used the 2-hop path after 37 seconds from the time that node E appeared. But AODV finds the shortest path in 21 seconds. So AODV adapts much faster than OLSR when connection events than lead to shortest path encountered. On the other hand, OLSR is again more reliable than AODV protocol, it is able to deliver all sent packets to node D, while AODV introduces 11.7% packet loss. Figure 5.12: Connection event
35 Figure 5.13: Protocol delay in multi-path topology with connection event Figure 5.14: Packet Delivery Ratio in multi-path topology with connection event
36 References [1] NITOS Wireless Testbed: [2] Outdoor Testbed: [3] Outdoor Nodes specifications: [4] Ad-Hoc Networks: al.org/manet-and-routing-techniques/ [5] Routing Basics: Basics [6] Routing Protocols Classification: [7] Reactive Protocols: html/node16.html [8] Proactive Protocols: html/node17.html [9] Routing Protocols Classification: classification-routing-protocols.html [10] Ad hoc On-Demand Distance Vector Documentation: [11] Optimized Link State Routing Protocol Documentation: [12] IPERF command: [13] Wireshark tool: [14] AODV protocol daemon: [15] OLSR protocol daemon: [16] PING command: ping.htm [17] Iptables MAC Address Filtering:
Μειέηε θαη αλάιπζε επίδνζεο πξσηνθόιισλ δξνκνιόγεζεο ζε θηλεηά ad hoc δίθηπα κε βάζε ελεξγεηαθά θξηηήξηα ΓΗΠΛΩΜΑΣΗΚΖ ΔΡΓΑΗΑ
 ΔΘΝΗΚΟ ΜΔΣΟΒΗΟ ΠΟΛΤΣΔΥΝΔΗΟ ΥΟΛΖ ΖΛΔΚΣΡΟΛΟΓΩΝ ΜΖΥΑΝΗΚΩΝ ΚΑΗ ΜΖΥΑΝΗΚΩΝ ΤΠΟΛΟΓΗΣΩΝ ΣΟΜΔΑ ΤΣΖΜΑΣΩΝ ΜΔΣΑΓΟΖ ΠΛΖΡΟΦΟΡΗΑ ΚΑΗ ΣΔΥΝΟΛΟΓΗΑ ΤΛΗΚΩΝ Μειέηε θαη αλάιπζε επίδνζεο πξσηνθόιισλ δξνκνιόγεζεο ζε θηλεηά ad
ΔΘΝΗΚΟ ΜΔΣΟΒΗΟ ΠΟΛΤΣΔΥΝΔΗΟ ΥΟΛΖ ΖΛΔΚΣΡΟΛΟΓΩΝ ΜΖΥΑΝΗΚΩΝ ΚΑΗ ΜΖΥΑΝΗΚΩΝ ΤΠΟΛΟΓΗΣΩΝ ΣΟΜΔΑ ΤΣΖΜΑΣΩΝ ΜΔΣΑΓΟΖ ΠΛΖΡΟΦΟΡΗΑ ΚΑΗ ΣΔΥΝΟΛΟΓΗΑ ΤΛΗΚΩΝ Μειέηε θαη αλάιπζε επίδνζεο πξσηνθόιισλ δξνκνιόγεζεο ζε θηλεηά ad
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration
 Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration Δρ. Απόστολος Γκάμας Διδάσκων 407/80 gkamas@uop.gr Δίκτυα Επικοινωνιών ΙΙ Διαφάνεια 1 1 Dynamic Routing Configuration Router (config) # router protocol [ keyword
Δίκτυα Επικοινωνιών ΙΙ: OSPF Configuration Δρ. Απόστολος Γκάμας Διδάσκων 407/80 gkamas@uop.gr Δίκτυα Επικοινωνιών ΙΙ Διαφάνεια 1 1 Dynamic Routing Configuration Router (config) # router protocol [ keyword
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
Δίκτυα Δακτυλίου. Token Ring - Polling
 Δίκτυα Δακτυλίου Token Ring - Polling Όλοι οι κόμβοι είναι τοποθετημένοι σε ένα δακτύλιο. Εκπέμπει μόνο ο κόμβος ο οποίος έχει τη σκυτάλη (token). The token consists of a number of octets in a specific
Δίκτυα Δακτυλίου Token Ring - Polling Όλοι οι κόμβοι είναι τοποθετημένοι σε ένα δακτύλιο. Εκπέμπει μόνο ο κόμβος ο οποίος έχει τη σκυτάλη (token). The token consists of a number of octets in a specific
(C) 2010 Pearson Education, Inc. All rights reserved.
 Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
the total number of electrons passing through the lamp.
 1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
1. A 12 V 36 W lamp is lit to normal brightness using a 12 V car battery of negligible internal resistance. The lamp is switched on for one hour (3600 s). For the time of 1 hour, calculate (i) the energy
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
σχεδιαστικές προκλήσεις, θεωρία γράφων
 Δομή παρουσίασης 1. Εισαγωγή στις κατανεμημένες εφαρμογές: σχεδιαστικές προκλήσεις, θεωρία γράφων 2. Χαρακτηριστικά και πεδία εφαρμογών: ιδιαιτερότητες και χαρακτηριστικά που απαιτούν τη χρήση αλγορίθμων
Δομή παρουσίασης 1. Εισαγωγή στις κατανεμημένες εφαρμογές: σχεδιαστικές προκλήσεις, θεωρία γράφων 2. Χαρακτηριστικά και πεδία εφαρμογών: ιδιαιτερότητες και χαρακτηριστικά που απαιτούν τη χρήση αλγορίθμων
department listing department name αχχουντσ ϕανε βαλικτ δδσϕηασδδη σδηφγ ασκϕηλκ τεχηνιχαλ αλαν ϕουν διξ τεχηνιχαλ ϕοην µαριανι
 She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
She selects the option. Jenny starts with the al listing. This has employees listed within She drills down through the employee. The inferred ER sttricture relates this to the redcords in the databasee
Στρατηγικές Ασφάλειας
 Στρατηγικές Ασφάλειας Ασφάλεια Πληροφοριακών Συστημάτων. Διδάσκων: Σ. Κοντογιάννης Least/(Most) Privileges Defense in Depth Συγκεντρωτική Στρατηγική Weakest Link Strategy Fail Safe Stance Fail Safe Stance
Στρατηγικές Ασφάλειας Ασφάλεια Πληροφοριακών Συστημάτων. Διδάσκων: Σ. Κοντογιάννης Least/(Most) Privileges Defense in Depth Συγκεντρωτική Στρατηγική Weakest Link Strategy Fail Safe Stance Fail Safe Stance
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost
 Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης & Τεχνολογίας Τηλεπικοινωνιών Ευάγγελος Α. Κοσμάτος Basic OSPF Configuration Υλοποίηση Δικτυακών Υποδομών
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: OSPF Cost Πανεπιστήμιο Πελοποννήσου Τμήμα Επιστήμης & Τεχνολογίας Τηλεπικοινωνιών Ευάγγελος Α. Κοσμάτος Basic OSPF Configuration Υλοποίηση Δικτυακών Υποδομών
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Potential Dividers. 46 minutes. 46 marks. Page 1 of 11
 Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Potential Dividers 46 minutes 46 marks Page 1 of 11 Q1. In the circuit shown in the figure below, the battery, of negligible internal resistance, has an emf of 30 V. The pd across the lamp is 6.0 V and
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
[1] P Q. Fig. 3.1
![[1] P Q. Fig. 3.1 [1] P Q. Fig. 3.1](/thumbs/79/80362156.jpg) 1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
1 (a) Define resistance....... [1] (b) The smallest conductor within a computer processing chip can be represented as a rectangular block that is one atom high, four atoms wide and twenty atoms long. One
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1
 Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ
 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ. του φοιτητή του Τμήματος Ηλεκτρολόγων Μηχανικών και. Τεχνολογίας Υπολογιστών της Πολυτεχνικής Σχολής του. Πανεπιστημίου Πατρών
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΗΛΕΚΤΡΙΚΗΣ ΕΝΕΡΓΕΙΑΣ ΕΡΓΑΣΤΗΡΙΟ ΗΛΕΚΤΡΟΜΗΧΑΝΙΚΗΣ ΜΕΤΑΤΡΟΠΗΣ ΕΝΕΡΓΕΙΑΣ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ του φοιτητή του
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΗΛΕΚΤΡΙΚΗΣ ΕΝΕΡΓΕΙΑΣ ΕΡΓΑΣΤΗΡΙΟ ΗΛΕΚΤΡΟΜΗΧΑΝΙΚΗΣ ΜΕΤΑΤΡΟΠΗΣ ΕΝΕΡΓΕΙΑΣ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ του φοιτητή του
(1) Describe the process by which mercury atoms become excited in a fluorescent tube (3)
 Q1. (a) A fluorescent tube is filled with mercury vapour at low pressure. In order to emit electromagnetic radiation the mercury atoms must first be excited. (i) What is meant by an excited atom? (1) (ii)
Q1. (a) A fluorescent tube is filled with mercury vapour at low pressure. In order to emit electromagnetic radiation the mercury atoms must first be excited. (i) What is meant by an excited atom? (1) (ii)
Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches
 Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches ultiplexing: TD, FD, Statistical multiplexing, CDA OSI
Internet protocol stack Encapsulation Connection oriented VS connectionless services Circuit Switching Packet Switching Store-and-forward switches ultiplexing: TD, FD, Statistical multiplexing, CDA OSI
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Introduction to the TCP IP protocol stack through a role playing game
 Introduction to the TCP IP protocol stack through a role playing game Based on : Norman Pendegraft. 2003. The TCP/IP game. In Current issues in IT education, Tanya McGill (Ed.). IGI Publishing, Hershey,
Introduction to the TCP IP protocol stack through a role playing game Based on : Norman Pendegraft. 2003. The TCP/IP game. In Current issues in IT education, Tanya McGill (Ed.). IGI Publishing, Hershey,
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
HY335Α Δίκτυα Υπολογιστών Xειμερινό Εξάμηνο Πανεπιστήμιο Κρήτης, Τμήμα Επιστήμης Υπολογιστών. Routing Algorithms. Network Layer.
 HY335Α Δίκτυα Υπολογιστών Xειμερινό Εξάμηνο 2016-2017 Πανεπιστήμιο Κρήτης, Τμήμα Επιστήμης Υπολογιστών Routing Algorithms Network Layer Nena Basina Υποδίκτυα (subnets) 200.23.18.0/23 11001000 00010111
HY335Α Δίκτυα Υπολογιστών Xειμερινό Εξάμηνο 2016-2017 Πανεπιστήμιο Κρήτης, Τμήμα Επιστήμης Υπολογιστών Routing Algorithms Network Layer Nena Basina Υποδίκτυα (subnets) 200.23.18.0/23 11001000 00010111
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ ΤΣΗΜΑΣΟ ΨΗΦΙΑΚΗ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ
 ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/2006
 ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 11/3/26 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι το 1 εκτός αν ορίζεται διαφορετικά στη διατύπωση
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ. Υποβάλλεται στην
 ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
CYTA Cloud Server Set Up Instructions
 CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
Capacitors - Capacitance, Charge and Potential Difference
 Capacitors - Capacitance, Charge and Potential Difference Capacitors store electric charge. This ability to store electric charge is known as capacitance. A simple capacitor consists of 2 parallel metal
Capacitors - Capacitance, Charge and Potential Difference Capacitors store electric charge. This ability to store electric charge is known as capacitance. A simple capacitor consists of 2 parallel metal
Προσομοίωση BP με το Bizagi Modeler
 Προσομοίωση BP με το Bizagi Modeler Α. Τσαλγατίδου - Γ.-Δ. Κάπος Πρόγραμμα Μεταπτυχιακών Σπουδών Τεχνολογία Διοίκησης Επιχειρησιακών Διαδικασιών 2017-2018 BPMN Simulation with Bizagi Modeler: 4 Levels
Προσομοίωση BP με το Bizagi Modeler Α. Τσαλγατίδου - Γ.-Δ. Κάπος Πρόγραμμα Μεταπτυχιακών Σπουδών Τεχνολογία Διοίκησης Επιχειρησιακών Διαδικασιών 2017-2018 BPMN Simulation with Bizagi Modeler: 4 Levels
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
«Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων. Η μεταξύ τους σχέση και εξέλιξη.»
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration
 Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration Δρ. Απόστολος Γκάμας Διδάσκων (407/80) gkamas@uop.gr Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών Διαφάνεια 1 1 Dynamic Routing Configuration
Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών: IOS Routing Configuration Δρ. Απόστολος Γκάμας Διδάσκων (407/80) gkamas@uop.gr Υλοποίηση Δικτυακών Υποδομών και Υπηρεσιών Διαφάνεια 1 1 Dynamic Routing Configuration
Χρήση συστημάτων πληροφορικής στην οδική υποδομή
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΕΜΠ Εργαστήριο Συγκοινωνιακής Τεχνικής Χρήση συστημάτων πληροφορικής στην οδική υποδομή Συσχέτιση δεδομένων GPS και χάρτη Βύρωνας Νάκος Καθηγήτης ΕΜΠ bnakos@central.ntua.gr
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΕΜΠ Εργαστήριο Συγκοινωνιακής Τεχνικής Χρήση συστημάτων πληροφορικής στην οδική υποδομή Συσχέτιση δεδομένων GPS και χάρτη Βύρωνας Νάκος Καθηγήτης ΕΜΠ bnakos@central.ntua.gr
ΚΥΠΡΙΑΚΟΣ ΣΥΝΔΕΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY 21 ος ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ Δεύτερος Γύρος - 30 Μαρτίου 2011
 Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
AODV - SD ΕΠΕΚΤΑΣΗ ΤΟΥ ΠΡΩΤΟΚΟΛΛΟΥ ΔΡΟΜΟΛΟΓΗΣΗΣ AODV ΓΙΑ ΑΝΑΚΑΛΥΨΗ ΥΠΗΡΕΣΙΩΝ ΣΕ ΚΙΝΗΤΑ AD HOC ΔΙΚΤΥΑ SIMULATION WITH J-SIM
 AODV - SD ΕΠΕΚΤΑΣΗ ΤΟΥ ΠΡΩΤΟΚΟΛΛΟΥ ΔΡΟΜΟΛΟΓΗΣΗΣ AODV ΓΙΑ ΑΝΑΚΑΛΥΨΗ ΥΠΗΡΕΣΙΩΝ ΣΕ ΚΙΝΗΤΑ AD HOC ΔΙΚΤΥΑ SIMULATION WITH J-SIM MANETS MANETS = Mobile Ad Hoc Networks Δεν υπάρχει fixed network infrastructure
AODV - SD ΕΠΕΚΤΑΣΗ ΤΟΥ ΠΡΩΤΟΚΟΛΛΟΥ ΔΡΟΜΟΛΟΓΗΣΗΣ AODV ΓΙΑ ΑΝΑΚΑΛΥΨΗ ΥΠΗΡΕΣΙΩΝ ΣΕ ΚΙΝΗΤΑ AD HOC ΔΙΚΤΥΑ SIMULATION WITH J-SIM MANETS MANETS = Mobile Ad Hoc Networks Δεν υπάρχει fixed network infrastructure
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ
 ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
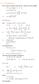 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
Modbus basic setup notes for IO-Link AL1xxx Master Block
 n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
n Modbus has four tables/registers where data is stored along with their associated addresses. We will be using the holding registers from address 40001 to 49999 that are R/W 16 bit/word. Two tables that
Business English. Ενότητα # 9: Financial Planning. Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ Ανώτατο Εκπαιδευτικό Ίδρυμα Πειραιά Τεχνολογικού Τομέα Business English Ενότητα # 9: Financial Planning Ευαγγελία Κουτσογιάννη Τμήμα Διοίκησης Επιχειρήσεων Άδειες Χρήσης Το παρόν εκπαιδευτικό
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
EPL 603 TOPICS IN SOFTWARE ENGINEERING. Lab 5: Component Adaptation Environment (COPE)
 EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
TaxiCounter Android App. Περδίκης Ανδρέας ME10069
 TaxiCounter Android App Περδίκης Ανδρέας ME10069 Content Android Operating System Development Tools Taxi Counter Algorithm Design Development Process Android Operating System Android is a Linux-based operating
TaxiCounter Android App Περδίκης Ανδρέας ME10069 Content Android Operating System Development Tools Taxi Counter Algorithm Design Development Process Android Operating System Android is a Linux-based operating
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Bayesian statistics. DS GA 1002 Probability and Statistics for Data Science.
 Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Mean bond enthalpy Standard enthalpy of formation Bond N H N N N N H O O O
 Q1. (a) Explain the meaning of the terms mean bond enthalpy and standard enthalpy of formation. Mean bond enthalpy... Standard enthalpy of formation... (5) (b) Some mean bond enthalpies are given below.
Q1. (a) Explain the meaning of the terms mean bond enthalpy and standard enthalpy of formation. Mean bond enthalpy... Standard enthalpy of formation... (5) (b) Some mean bond enthalpies are given below.
Math221: HW# 1 solutions
 Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΤΜΗΜΑ ΠΟΛΙΤΙΚΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΟΜΟΣΤΑΤΙΚΗΣ ΕΡΓΑΣΤΗΡΙΟ ΜΕΤΑΛΛΙΚΩΝ ΚΑΤΑΣΚΕΥΩΝ ΕΙΣΑΓΩΓΗ ΣΤΟΝ ΑΥΤΟΜΑΤΟ ΕΛΕΓΧΟ ΤΩΝ ΚΑΤΑΣΚΕΥΩΝ Ανεµόµετρο AMD 1 Αισθητήρας AMD 2 11 ος όροφος Υπολογιστής
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΤΜΗΜΑ ΠΟΛΙΤΙΚΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΟΜΟΣΤΑΤΙΚΗΣ ΕΡΓΑΣΤΗΡΙΟ ΜΕΤΑΛΛΙΚΩΝ ΚΑΤΑΣΚΕΥΩΝ ΕΙΣΑΓΩΓΗ ΣΤΟΝ ΑΥΤΟΜΑΤΟ ΕΛΕΓΧΟ ΤΩΝ ΚΑΤΑΣΚΕΥΩΝ Ανεµόµετρο AMD 1 Αισθητήρας AMD 2 11 ος όροφος Υπολογιστής
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Αναερόβια Φυσική Κατάσταση
 Αναερόβια Φυσική Κατάσταση Γιάννης Κουτεντάκης, BSc, MA. PhD Αναπληρωτής Καθηγητής ΤΕΦΑΑ, Πανεπιστήµιο Θεσσαλίας Περιεχόµενο Μαθήµατος Ορισµός της αναερόβιας φυσικής κατάστασης Σχέσης µε µηχανισµούς παραγωγής
Αναερόβια Φυσική Κατάσταση Γιάννης Κουτεντάκης, BSc, MA. PhD Αναπληρωτής Καθηγητής ΤΕΦΑΑ, Πανεπιστήµιο Θεσσαλίας Περιεχόµενο Μαθήµατος Ορισµός της αναερόβιας φυσικής κατάστασης Σχέσης µε µηχανισµούς παραγωγής
ΚΑΘΟΡΙΣΜΟΣ ΠΑΡΑΓΟΝΤΩΝ ΠΟΥ ΕΠΗΡΕΑΖΟΥΝ ΤΗΝ ΠΑΡΑΓΟΜΕΝΗ ΙΣΧΥ ΣΕ Φ/Β ΠΑΡΚΟ 80KWp
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΜΕΤΑΔΟΣΗΣ ΠΛΗΡΟΦΟΡΙΑΣ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΛΙΚΩΝ ΚΑΘΟΡΙΣΜΟΣ ΠΑΡΑΓΟΝΤΩΝ ΠΟΥ ΕΠΗΡΕΑΖΟΥΝ ΤΗΝ ΠΑΡΑΓΟΜΕΝΗ ΙΣΧΥ
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΣΥΣΤΗΜΑΤΩΝ ΜΕΤΑΔΟΣΗΣ ΠΛΗΡΟΦΟΡΙΑΣ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΛΙΚΩΝ ΚΑΘΟΡΙΣΜΟΣ ΠΑΡΑΓΟΝΤΩΝ ΠΟΥ ΕΠΗΡΕΑΖΟΥΝ ΤΗΝ ΠΑΡΑΓΟΜΕΝΗ ΙΣΧΥ
Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών δικτύων ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΕΠΙΚΟΙΝΩΝΙΩΝ, ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΣΥΣΤΗΜΑΤΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΜΗΧΑΝΙΚΩΝ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ ΕΠΙΚΟΙΝΩΝΙΩΝ, ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΣΥΣΤΗΜΑΤΩΝ ΠΛΗΡΟΦΟΡΙΚΗΣ Μηχανισμοί πρόβλεψης προσήμων σε προσημασμένα μοντέλα κοινωνικών
Homework 8 Model Solution Section
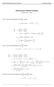 MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
Démographie spatiale/spatial Demography
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
Μηχανική Μάθηση Hypothesis Testing
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Δίκτυα Υπολογιστών ΙΙ (Ασκήσεις Πράξης)
 TEI Σερρών Τμήμα Πληροφορικής και Επικοινωνιών Δίκτυα Υπολογιστών ΙΙ (Ασκήσεις Πράξης) Ανάλυση Πρωτοκόλλων Τομέας Τηλεπικοινωνιών και Δικτύων Δρ. Αναστάσιος Πολίτης Καθηγητής Εφαρμογών anpol@teiser.gr
TEI Σερρών Τμήμα Πληροφορικής και Επικοινωνιών Δίκτυα Υπολογιστών ΙΙ (Ασκήσεις Πράξης) Ανάλυση Πρωτοκόλλων Τομέας Τηλεπικοινωνιών και Δικτύων Δρ. Αναστάσιος Πολίτης Καθηγητής Εφαρμογών anpol@teiser.gr
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
6.3 Forecasting ARMA processes
 122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
ΠΕΡΙΕΧΟΜΕΝΑ. Μάρκετινγκ Αθλητικών Τουριστικών Προορισμών 1
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΙΓΑΙΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΤΗΣ ΔΙΟΙΚΗΣΗΣ ΤΜΗΜΑ ΔΙΟΙΚΗΣΗΣ ΕΠΙΧΕΙΡΗΣΕΩΝ ΔΙΑΤΜΗΜΑΤΙΚΟ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ «Σχεδιασμός, Διοίκηση και Πολιτική του Τουρισμού» ΜΑΡΚΕΤΙΝΓΚ ΑΘΛΗΤΙΚΩΝ ΤΟΥΡΙΣΤΙΚΩΝ
ΠΑΝΕΠΙΣΤΗΜΙΟ ΑΙΓΑΙΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ ΤΗΣ ΔΙΟΙΚΗΣΗΣ ΤΜΗΜΑ ΔΙΟΙΚΗΣΗΣ ΕΠΙΧΕΙΡΗΣΕΩΝ ΔΙΑΤΜΗΜΑΤΙΚΟ ΠΡΟΓΡΑΜΜΑ ΜΕΤΑΠΤΥΧΙΑΚΩΝ ΣΠΟΥΔΩΝ «Σχεδιασμός, Διοίκηση και Πολιτική του Τουρισμού» ΜΑΡΚΕΤΙΝΓΚ ΑΘΛΗΤΙΚΩΝ ΤΟΥΡΙΣΤΙΚΩΝ
ΒΕΛΤΙΣΤΟΠΟΙΗΣΗ ΧΡΟΝΟΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ ΕΡΓΑΣΙΩΝ & ΑΝΑΘΕΣΗΣ ΑΝΘΡΩΠΙΝΩΝ ΠΟΡΩΝ ΣΕ ΠΟΛΛΑΠΛΑ ΕΡΓΑ ΠΑΡΑΓΩΓΗΣ ΛΟΓΙΣΜΙΚΟΥ ΜΕ ΠΟΛΛΑΠΛΕΣ ΟΜΑΔΕΣ
 Σχολή Μηχανικής και Τεχνολογίας Πτυχιακή εργασία ΒΕΛΤΙΣΤΟΠΟΙΗΣΗ ΧΡΟΝΟΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ ΕΡΓΑΣΙΩΝ & ΑΝΑΘΕΣΗΣ ΑΝΘΡΩΠΙΝΩΝ ΠΟΡΩΝ ΣΕ ΠΟΛΛΑΠΛΑ ΕΡΓΑ ΠΑΡΑΓΩΓΗΣ ΛΟΓΙΣΜΙΚΟΥ ΜΕ ΠΟΛΛΑΠΛΕΣ ΟΜΑΔΕΣ Ηλίας Κωνσταντίνου Λεμεσός,
Σχολή Μηχανικής και Τεχνολογίας Πτυχιακή εργασία ΒΕΛΤΙΣΤΟΠΟΙΗΣΗ ΧΡΟΝΟΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ ΕΡΓΑΣΙΩΝ & ΑΝΑΘΕΣΗΣ ΑΝΘΡΩΠΙΝΩΝ ΠΟΡΩΝ ΣΕ ΠΟΛΛΑΠΛΑ ΕΡΓΑ ΠΑΡΑΓΩΓΗΣ ΛΟΓΙΣΜΙΚΟΥ ΜΕ ΠΟΛΛΑΠΛΕΣ ΟΜΑΔΕΣ Ηλίας Κωνσταντίνου Λεμεσός,
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
Section 1: Listening and responding. Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016
 Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
Section 1: Listening and responding Presenter: Niki Farfara MGTAV VCE Seminar 7 August 2016 Section 1: Listening and responding Section 1: Listening and Responding/ Aκουστική εξέταση Στο πρώτο μέρος της
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Συστήματα Διαχείρισης Βάσεων Δεδομένων
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Συστήματα Διαχείρισης Βάσεων Δεδομένων Φροντιστήριο 9: Transactions - part 1 Δημήτρης Πλεξουσάκης Τμήμα Επιστήμης Υπολογιστών Tutorial on Undo, Redo and Undo/Redo
ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ
 ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ Μελέτη των υλικών των προετοιμασιών σε υφασμάτινο υπόστρωμα, φορητών έργων τέχνης (17ος-20ος αιώνας). Διερεύνηση της χρήσης της τεχνικής της Ηλεκτρονικής Μικροσκοπίας
ΑΡΙΣΤΟΤΕΛΕΙΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΟΝΙΚΗΣ Μελέτη των υλικών των προετοιμασιών σε υφασμάτινο υπόστρωμα, φορητών έργων τέχνης (17ος-20ος αιώνας). Διερεύνηση της χρήσης της τεχνικής της Ηλεκτρονικής Μικροσκοπίας
Aluminum Electrolytic Capacitors (Large Can Type)
 Aluminum Electrolytic Capacitors (Large Can Type) Snap-In, 85 C TS-U ECE-S (U) Series: TS-U Features General purpose Wide CV value range (33 ~ 47,000 µf/16 4V) Various case sizes Top vent construction
Aluminum Electrolytic Capacitors (Large Can Type) Snap-In, 85 C TS-U ECE-S (U) Series: TS-U Features General purpose Wide CV value range (33 ~ 47,000 µf/16 4V) Various case sizes Top vent construction
UNIVERSITY OF CALIFORNIA. EECS 150 Fall ) You are implementing an 4:1 Multiplexer that has the following specifications:
 UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
UNIVERSITY OF CALIFORNIA Department of Electrical Engineering and Computer Sciences EECS 150 Fall 2001 Prof. Subramanian Midterm II 1) You are implementing an 4:1 Multiplexer that has the following specifications:
Επίπεδο Μεταφοράς. (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών Τμήμα Μηχανικών Η/Υ και Πληροφορικής
 Επίπεδο Μεταφοράς (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο Μεταφοράς(Transport layer) Επίπεδο εφαρμογής (Application layer): Συντονισμός
Επίπεδο Μεταφοράς (ανεβαίνουμε προς τα πάνω) Εργαστήριο Δικτύων Υπολογιστών 2014-2015 Τμήμα Μηχανικών Η/Υ και Πληροφορικής Επίπεδο Μεταφοράς(Transport layer) Επίπεδο εφαρμογής (Application layer): Συντονισμός
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
1) Abstract (To be organized as: background, aim, workpackages, expected results) (300 words max) Το όριο λέξεων θα είναι ελαστικό.
 UΓενικές Επισημάνσεις 1. Παρακάτω θα βρείτε απαντήσεις του Υπουργείου, σχετικά με τη συμπλήρωση της ηλεκτρονικής φόρμας. Διευκρινίζεται ότι στα περισσότερα θέματα οι απαντήσεις ήταν προφορικές (τηλεφωνικά),
UΓενικές Επισημάνσεις 1. Παρακάτω θα βρείτε απαντήσεις του Υπουργείου, σχετικά με τη συμπλήρωση της ηλεκτρονικής φόρμας. Διευκρινίζεται ότι στα περισσότερα θέματα οι απαντήσεις ήταν προφορικές (τηλεφωνικά),
Διπλωματική Εργασία του φοιτητή του Τμήματος Ηλεκτρολόγων Μηχανικών και Τεχνολογίας Υπολογιστών της Πολυτεχνικής Σχολής του Πανεπιστημίου Πατρών
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ:ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΥΠΟΛΟΓΙΣΤΩΝ ΕΡΓΑΣΤΗΡΙΟ ΗΛΕΚΤΡΟΝΙΚΩΝ ΕΦΑΡΜΟΓΩΝ Διπλωματική Εργασία του φοιτητή του Τμήματος Ηλεκτρολόγων
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΑΤΡΩΝ ΤΜΗΜΑ ΗΛΕΚΤΡΟΛΟΓΩΝ ΜΗΧΑΝΙΚΩΝ ΚΑΙ ΤΕΧΝΟΛΟΓΙΑΣ ΥΠΟΛΟΓΙΣΤΩΝ ΤΟΜΕΑΣ:ΗΛΕΚΤΡΟΝΙΚΗΣ ΚΑΙ ΥΠΟΛΟΓΙΣΤΩΝ ΕΡΓΑΣΤΗΡΙΟ ΗΛΕΚΤΡΟΝΙΚΩΝ ΕΦΑΡΜΟΓΩΝ Διπλωματική Εργασία του φοιτητή του Τμήματος Ηλεκτρολόγων
On a four-dimensional hyperbolic manifold with finite volume
 BULETINUL ACADEMIEI DE ŞTIINŢE A REPUBLICII MOLDOVA. MATEMATICA Numbers 2(72) 3(73), 2013, Pages 80 89 ISSN 1024 7696 On a four-dimensional hyperbolic manifold with finite volume I.S.Gutsul Abstract. In
BULETINUL ACADEMIEI DE ŞTIINŢE A REPUBLICII MOLDOVA. MATEMATICA Numbers 2(72) 3(73), 2013, Pages 80 89 ISSN 1024 7696 On a four-dimensional hyperbolic manifold with finite volume I.S.Gutsul Abstract. In
Correction Table for an Alcoholometer Calibrated at 20 o C
 An alcoholometer is a device that measures the concentration of ethanol in a water-ethanol mixture (often in units of %abv percent alcohol by volume). The depth to which an alcoholometer sinks in a water-ethanol
An alcoholometer is a device that measures the concentration of ethanol in a water-ethanol mixture (often in units of %abv percent alcohol by volume). The depth to which an alcoholometer sinks in a water-ethanol
Nuclear Physics 5. Name: Date: 8 (1)
 Name: Date: Nuclear Physics 5. A sample of radioactive carbon-4 decays into a stable isotope of nitrogen. As the carbon-4 decays, the rate at which the amount of nitrogen is produced A. decreases linearly
Name: Date: Nuclear Physics 5. A sample of radioactive carbon-4 decays into a stable isotope of nitrogen. As the carbon-4 decays, the rate at which the amount of nitrogen is produced A. decreases linearly
Case 1: Original version of a bill available in only one language.
 currentid originalid attributes currentid attribute is used to identify an element and must be unique inside the document. originalid is used to mark the identifier that the structure used to have in the
currentid originalid attributes currentid attribute is used to identify an element and must be unique inside the document. originalid is used to mark the identifier that the structure used to have in the
