C ab, Algorithms for computations in Jacobian group of C ab curve and their application to discrete-log based public key cryptosystems.
|
|
|
- Δημοστρατη Δελή
- 6 χρόνια πριν
- Προβολές:
Transcript
1 C ab Algorithms for computations in Jacobian group of C ab curve and their application to discrete-log based public key cryptosystems Seigo ARITA C ab C ab C ab C ab C ab 1 RSA 2 C 2 (1) [4] [5] (2) [6] [7] [11] [8] C ab [1] [3] [12] C ab C ab (1) C ab C ab C 2 Gröbner 3 C ab 4 NEC C&C C&C Media Research Laboratories NEC 1-1 Miyakzaki 4- chome Miyamae-ku Kawasaki Kanagawa 216 Japan 1 C C ab 5 4 A Vol J82 A No 8 pp
2 99/8 Vol J82 A No 8 deg(d) + 1 g [10] [18] Gröbner Z> = 0 n x α = x α 1 1 xα n n n 7 C ab α = (α 1 α n ) Z n > = 0 multi-degree / MD(x α ) Z n > = 0 < γ Z n > 2 = 0 α < β α + γ < β + γ < < multi-degree n Gröbner n f 2 1 f leading monomial K C K LM(f) f K m i C K ( ) i D = G n m i i 0 m i D = g 1 g m m i i m = m i D = g 1 g m m i i K[x 1 x n] I deg(d) C G = {g 1 g m} g 1 g m D 0 leading monomial I D 0 leading monomial Gal(K K) D D 0 LM(I) = LM(g 1 ) LM(g m ) D K DK 0 D K G I Gröbner K I Gröbner G = {g 1 g m } I C f :I = g 1 g m K[x 1 x n ] n (or ) v (f) = n(or n) Gröbner f (f) := v (f) 0 leading monomial multi-degree f (f) (f) 0 := α Z n > = 0 I v (f)> v = 0 (f) f (f) := (I) : v (f)< v = 0 (f) f (f) = (f) 0 (f) C (I) = {α Z n > = 0 x α LM(I)} {(f) f K(C)} D 0 (I) δ(i) C J(C) D 0 G = {g 1 g m } Gal(K K) K D g Riemann dim L(D) > = I I J K (C) K δ(g 1 g m ) := (Z n > = 0 m i=1(md(lm(g i )) + Z n > = 0)) J K (C) ( S S ) δ(i) I G = {g 1 g m } L(D) = {f K(C) (f) + D > = 0} {0} G I Gröbner basis δ(i) = δ(g 1 g m)(1) K C 2
3 C ab Gröbner n C ab (C ) f I f I Gröbner 0 C ab (a 1)(b 1)/2 I Gröbner C ab reduced Gröbner I C ab Gröbner reduced 1) G C ab > cab p LM(p) 1 2) G 2 C ab α = (α 1 α 2) β = p p (β 1 β 2) Z 2 > = 0 (i) (ii) LM(G {p}) α > cab β [17] 3 C ab [9] C ab X α Y β C ab C ab K K 1 X α Y β C C 1 v (x α y β ) = aα + bβ C X L( ) L( ) = {f K(C) v Q (f) > = 0 ( Q = )} L( ) f M [13] [14] Noether Residue Divisor Theorem [15] M = { v (f) f L( )} M ( ) 1 C ab M 2 a b (C ) C ab (C ) C ab C ab a x L( ) b y L( ) x y C ab C ab 0< = i< = b0< = j< = aai+bj< = ab α ijx i y j = 0 (2) α ij K α b0 α 0a 0 (2) C ab (C ) C ab J K (C) DK/ 0 K C j [D] α b0 α 0a 0 (2) C 23 C 2b (i) aα 1 + bα 2 > aβ 1 + bβ 2 (ii) aα 1 + bα 2 = aβ 1 + bβ 2 α 1 < β 1 4 K C ab C C g = (a 1)(b 1)/2 D K DK 0 K C K 0 C J K (C) = DK/ 0 K j D DK 0 j = [D] 3 E g n D = E n 0 D 3
4 semi-normal 4 J K (C) j 99/8 Vol J82 A No 8 semi-normal 7 [D] Riemann dim L(D + g ) > = g + 1 g = 1 0 D + g + (f) > = 0 E = D + g + (f) j = [E g ] f E 1 n 1 D 2 = E 2 n 2 4 semi- 1 D 1 + D 2 = (E 1 + E 2) (n 1 + n 2) normal semi- 1 normal D = E n normal 2 normal D = E n D = E n E D semi-normal G 1 (f) 0 > = E L( ) f v (f) f 2 G D + (f) Algorithm1 j J K (C) semi-normal 1 D 1 = E 1 n D 2 = E 2 n C ab semi-normal 1 0 λ E 1 n 1 = E 2 2 n 2 + (λ) D Supp((f 1) ) = { } (f 1) 0 > = K F (X Y ) = E 1 f 1 ( Supp(D) 0< = i< = b0< = j< = aai+bj< = ab αijxi Y j = 0 C ab D ) (f 1λ 1 ) = (f 1) (λ) = (f 1) 0 E 1 + E 2 + (n 1 k 1 n 2) (f 1) 0 C C ab C K[x y] K[X Y ]/(F (X Y )) E 1 + E 2 > = E 2 f 2 = f 1λ 1 f 2 Supp((f 2 ) ) = { } (f 2 ) 0 > = E 2 λ f 1 A K f 2 f 1 f 2 = C J K (C) f 1 λ 1 A K H(A K ) [16] E 2 + n 2 + (f 2 ) = E 2 + n 2 + C ab C Φ (f 1 ) E 1 + E 2 + (n 1 n 2 ) = E 1 + n 1 + (f 1 ) D 1 D 2 1 Φ : 6 1 (semi-normal ) normal Φ normal 1-1 normal (A K 2 semi-normal normal C ab normal 0 D j = 4 2 semi-normal D 1 = D 1 + D 2 normal D 3 = E 3 n 3 normal D 3 = E 3 n J K (C) H(A K ) [ n n ] [L( n )] C ab
5 C ab 1 2 Φ δ(i) A K I K I normal J E = n I I = Φ(E) = 1 I C ab I n I f( = 0) 2 (f) = I J J 4 A K I 1 dim KA/I n = n I 2 dima/i = n = deg(e) I 1 I 2 normal 8 C ab I 3 1 I 1 I 2 3 normal J 2 J 3 normal C 34 {a 0 +a 1 X+ I C g(c) = (3 1)(4 1)/2 = 3 J K (C) j = [ f 3 3 ] C 3 { } J (f) = I 1 I 2 J C 34 4 X XY 6 Y 2 j g I 3 (g) = J I 3 I 1 I 2 (g) = I 1 I 2 J I 3 = (f) I 3 4 ) δ(x 2 + XY + Y 2 + ) = 3 I 3 I 3 = g/f I 1 I 2 8 δ(i) = deg( ) = 3 C ab 22 (1) {X 2 + XY + 5 Y 2 + } I Gröbner 5 C ab 5 C ab F (X Y ) = 0 : K[X Y ]/(F (X Y )) I 1 I 2 K[X Y ]/(F (X Y )) normal I 3 1 J I 1 I 2 2 f f( = 0) J 3 g g( = 0) st g J = f F 4 I 3 g/f J 5 2 C ab Gröbner 5 C ab ) I = {f 1 = X Y + 4X + 5 f 2 = Gröbner XY + 3Y + 4X + 9 f 3 = Y 2 + 9Y + 16X + 2} ( C ab Gröbner 9 ) 2 8 semi-normal E n Φ I deg(e) = [17]Chap5Sec3rop4 δ(i) = dim K A/I A/I = A/In C ab C Gröbner C 34 9 C 34 C J K(C) a 2 Y +X 2 b 0 +b 1 X +b 2 Y +XY c 0 +c 1 X +c 2 Y +Y 2 } reduced Gröbner I X 2 + XY + Y ( C 34 normal C ab semi-normal Gröbner C ab Gröbner a GF (17) F = Y 3 + X C 34 C J GF (17) (C) ( C 34 1 X Y X 2 XY Y 2 X 3 X 2 Y XY 2 5
6 99/8 Vol J82 A No 8 f G hg 5 hg 4 {f F } 1 I I I I 6 C 34 f G 7 X 3 9 I I = {X Y + 5X + 15 XY + 13Y + 5X + 11 Gröbner {X 3 + X 2 Y + XY 2 + } Y 2 + 5Y + 12X + 6} I 3 Gröbner I I 5 g 1 f1 2 {F } = X g 2 f 1 f 2 {g 1 F } = X 3 Y + g 3 f 2 2 {g 2 g 1 F } = X 2 Y 2 + g 4 f 1 f 3 {g 3 g 2 g 1 F } = XY 2 + g 5 f 2 f 3 {g 4 g 3 g 2 g 1 F } = X 2 Y + g 6 f 2 3 {g 5 g 4 g 3 g 2 g 1 F } = X 3 + J I I = {g 6 g 5 g 4 } 2 f g 6 = X Y 2 + 5XY + 7Y + 11X h J f F h( = 0) LM(f) = X 3 LM(F ) = Y 3 RETURN I 3 X 2 {ff } g 5 4X 2 Y 2 + leading monomial X 2 Y 2 {ff } Y g 5 X 2 g 5 4Y g Xg 5 + 2g 5 (mod {f F }) h X Y + 5X (h/f) J = (h/f) {g 6 g 5 g 4} = {h (hg 5)/f (hg 4)/f} {a 5 b 5 } {a 4 b 4 } I 3 {h (hg 5)/f (hg 4)/f} {h a 5 a 4} (mod {F }) {{c 1 c 2 c a } r} Division(g G) g G {c 1 c 2 c a } r ( [17] ) {{a 1 a i } r} Coefficients(f r 1 r i ) f r 1 r i {a 1 a i } r ( f = i a k=1 kr k + r) Mono i C ab i (Mono 1 = 1 Mono 2 = J Gröbner X ) 6 algorithm JacobianSum(inputs I 1 I 2 output I 3) I 3 Compose(I 1 I 2) f the minimum element of I 3 I 3 Reduce(f I 3) {f F } f F Gröbner subroutine Compose(inputs I 1 = {f 1 f 2 f a} I 2 = {g 1 g 2 g a} output I g 5 {f F } 3) I 3 {F } FOR i = 1 TO a j = 1 TO a DO I {ff g } 5 = X 2 g f i g 3 j Y + I 3 {g} I 3 {ff } Xg 5 = XY 2 IF δ(i 3 ) > δ(i 1 ) + δ(i 2 ) THEN I 3 Buchberger(δ(I 1 ) + δ(i 2 ) I 3 ) + I 3 the set of the minimum a elements of I 3 {ff } Y g 5 = X 2 Y 2 RETURN I + 3 subroutine Reduce(inputs f I = {f 1 f 2 f a } output J) G {f f y {F } f y a 1{F } F } LABEL(retry) X 2 g 5 4Y g 5 +12XY 2 + J {} a (mod {f F }) XY 2 {ff } h (random number) fi Xg i=1 5 g Divide(G h) leading monomial FOR i = 1 TO a 6 {{c 1 c 2 c a } r} Division(g f i G) IF r = 0 THEN GOTO retry k c 1 + c 2 y + + c a y a 1 J J {k} RETURN J subroutine Divide(inputs G h output s) r 1 Mono 1 h G s 1 Mono 1 i 1 WHILE r i = 0 DO
7 C ab i i + 1 r i Mono i h G {{A 1 A i 1 } r i } Coefficients(r i {r 1 r i 1 }) s i Mono i i 1 j=1 A js j RETURN s i subroutine Buchberger(inputs m I = {f 1 f s } output G = {g 1 g t }) B {(i j) 1 < = i < j < = s} G F t s WHILE B = φ AND δ(g) > m DO Select (i j) B IF LCM(LT(f i ) LT(f j )) = LT(f i )LT(f j ) THEN S S(f i f j) G IF S = 0 THEN t t + 1; f t S G G {f t} B B {(i t) 1 < = i < = t 1} B B {(i j)} RETURN G B O(g 2 ) O(g 2 ) S G 160 ( SumDoubleScalar )O(g 4 ) 6 simple Y a + αx b + β Buchberger Gröbner C ab random 8 C ab Buchberger G 1 C 35 (ms on 266MHZentiumII) Table 1 erformance for C 35 curve(ms on 266MHZ entiumii) simple random Sum Double Scalar C 37 (ms on 266MHZentiumII) Table 2 erformance for C 37 curve(ms on 266MHZ entiumii) simple random Sum Double Scalar S 6 O(g 3 ) 6 subroutine Compose 6 1subroutine Divide 3 subroutine Reduce C 35 C 37 C Buchberger Buchberger 266MHZentium II millisecond m 2 Gröbner 1 23 Buchberger B 160 C 37 (i j) 300ms C ms O(g) (i j) S G C ab 6 O(g 3 ) 7 / GF (q) C 34 C C / ( 10 F q C 34 C 3 log(q) ) J GF (q) (C) q 3 7
8 99/8 Vol J82 A No 8 3 C 213 (ms on 266MHZentiumII) Table 3 erformance for C 213 curve(ms on 266MHZ entiumii) simple random Sum Double Scalar C ab 160 C ms C ab C ab C ab NEC SONY 1 C 34 / Fig 1 Encryption and decryption functions on C 34 curve [1] IASemaev Evaluation of discrete logarithms in a group of p-torsion points of an elliptic curves in characteristic p Math Comp (1998) [2] TSatoh KAraki Fermat Quotients and the olynomial Time Discrete Log Algorithm for Anomalous Elliptic Curves COMMENTARII MATHEMATICI UNIVERSITATIS SANCTI AULI vol 47 No q [3] NSmart The discrete logarithm problem on elliptic curves of trace one To appear in J Cryptol- 9 J GF (q) (C) ogy {a 0 + a 1 X + a 2 Y + X 2 b 0 + b 1 X + b 2 Y + XY c 0 + [4] DGCantor Computing in the Jacobian of a hy- c 1 X + c 2 Y + Y 2 } perelliptic curve Mathematics of Computation 48(177) pp a 2 = 0 2 a 0 + a 1 X + a 2 Y + X 2 [5] NKoblitz Hyperelliptic cryptosystems JCryptography1(1989) b 0 + b 1 X + b 2 Y + XY pp a 2 = 0 [6] NKoblitz A Very Easy Way to Generate Curves over rime Fields for Hyperelliptic Cryptosytems 1/q Rump Talk Crypto 97 J GF (q) (C) 6 log 2 (q) [7] NMatsudaJChaoSTsujii Efficient construction (a 0 a 1 a 2 b 0 b 1 b 2 ) algorithms of secure hyperelliptic discrete logarithm problems IEICE ISEC96-18(1996) J GF (q) (C) ( ) j 0 = [8] SMiuraNKamiya Geometric Goppa codes on (a 0 a 1 a 2 b 0 b 1 b 2 ) 6 some maximal curves and their minimum distance C(n) = n j 0 C(n) in roc IEEE Workshop on Information Theory (Susono-shiJapanJune 1993) pp85-86 [9] (A)vol 1 / 1 J81-A No Oct 1998 X j = (a 0 a 1 a 2 b 0 b 1 b 2) J GF (q) (C) [10] JHSilverman The Arithmetic of Elliptic Curves X(j) = a0 a 1 a 2( ) Springer-Verlag [11] A-MSpallek Kurven vom Geshlecht 2 und ihre Anwendung in ublick-key-kryptosystemen Doctor 8 thesis Universität GH Essen 1994 [12] IEICE ISEC98(1998) 8
9 C ab [13] EJVolcheck Computing in the Jacobian of a plane algebraic curve ANTS-I Lecture Notes in Computer Science vol 877(1994) Springer-Verlag pp [14] M-DHuang DIerardi Efficient Algorithms for the Riemann-Roch roblem and for Addition in the Jacobian of a Curve J Symbolic Computation (1994) [15] WFulton Algebraic Curves Addison-Wesley [16] RHartshorne Algebraic Geometry Springer- Verlag [17] DCox JLittle DO Shea Ideals Varieties and Algorithms Springer-Verlag [18] HStichtenoth Algebraic Function Fields and Codes Springer-Verlag 1990 NEC C&C 9
IUTeich. [Pano] (2) IUTeich
![IUTeich. [Pano] (2) IUTeich IUTeich. [Pano] (2) IUTeich](/thumbs/76/73790805.jpg) 2014 12 2012 8 IUTeich 2013 12 1 (1) 2014 IUTeich 2 2014 02 20 2 2 2014 05 24 2 2 IUTeich [Pano] 2 10 20 5 40 50 2005 7 2011 3 2 3 1 3 4 2 IUTeich IUTeich (2) 2012 10 IUTeich 2014 3 1 4 5 IUTeich IUTeich
2014 12 2012 8 IUTeich 2013 12 1 (1) 2014 IUTeich 2 2014 02 20 2 2 2014 05 24 2 2 IUTeich [Pano] 2 10 20 5 40 50 2005 7 2011 3 2 3 1 3 4 2 IUTeich IUTeich (2) 2012 10 IUTeich 2014 3 1 4 5 IUTeich IUTeich
Implementation of Index Calculus Attack for Hyperelliptic Curves of High Genera
 041-8655 116-2,,, HCDLP),, F 3 H : y 2 = x 2g+1 + 1, HCDLP,, g = 74 J H F 3 ) HCDLP J H F 3 ) 2 120 ) Implementation of Index Calculus Attack for Hyperelliptic Curves of High Genera Yasunori Kobayashi
041-8655 116-2,,, HCDLP),, F 3 H : y 2 = x 2g+1 + 1, HCDLP,, g = 74 J H F 3 ) HCDLP J H F 3 ) 2 120 ) Implementation of Index Calculus Attack for Hyperelliptic Curves of High Genera Yasunori Kobayashi
Re-Pair n. Re-Pair. Re-Pair. Re-Pair. Re-Pair. (Re-Merge) Re-Merge. Sekine [4, 5, 8] (highly repetitive text) [2] Re-Pair. Blocked-Repair-VF [7]
![Re-Pair n. Re-Pair. Re-Pair. Re-Pair. Re-Pair. (Re-Merge) Re-Merge. Sekine [4, 5, 8] (highly repetitive text) [2] Re-Pair. Blocked-Repair-VF [7] Re-Pair n. Re-Pair. Re-Pair. Re-Pair. Re-Pair. (Re-Merge) Re-Merge. Sekine [4, 5, 8] (highly repetitive text) [2] Re-Pair. Blocked-Repair-VF [7]](/thumbs/78/77313882.jpg) Re-Pair 1 1 Re-Pair Re-Pair Re-Pair Re-Pair 1. Larsson Moffat [1] Re-Pair Re-Pair (Re-Pair) ( ) (highly repetitive text) [2] Re-Pair [7] Re-Pair Re-Pair n O(n) O(n) 1 Hokkaido University, Graduate School
Re-Pair 1 1 Re-Pair Re-Pair Re-Pair Re-Pair 1. Larsson Moffat [1] Re-Pair Re-Pair (Re-Pair) ( ) (highly repetitive text) [2] Re-Pair [7] Re-Pair Re-Pair n O(n) O(n) 1 Hokkaido University, Graduate School
11 Drinfeld. k( ) = A/( ) A K. [Hat1, Hat2] k M > 0. Γ 1 (M) = γ SL 2 (Z) f : H C. ( ) az + b = (cz + d) k f(z) ( z H, γ = cz + d Γ 1 (M))
![11 Drinfeld. k( ) = A/( ) A K. [Hat1, Hat2] k M > 0. Γ 1 (M) = γ SL 2 (Z) f : H C. ( ) az + b = (cz + d) k f(z) ( z H, γ = cz + d Γ 1 (M)) 11 Drinfeld. k( ) = A/( ) A K. [Hat1, Hat2] k M > 0. Γ 1 (M) = γ SL 2 (Z) f : H C. ( ) az + b = (cz + d) k f(z) ( z H, γ = cz + d Γ 1 (M))](/thumbs/91/105488540.jpg) Drinfeld Drinfeld 29 8 8 11 Drinfeld [Hat3] 1 p q > 1 p A = F q [t] A \ F q d > 0 K A ( ) k( ) = A/( ) A K Laurent F q ((1/t)) 1/t C Drinfeld Drinfeld p p p [Hat1, Hat2] 1.1 p 1.1.1 k M > 0 { Γ 1 (M) =
Drinfeld Drinfeld 29 8 8 11 Drinfeld [Hat3] 1 p q > 1 p A = F q [t] A \ F q d > 0 K A ( ) k( ) = A/( ) A K Laurent F q ((1/t)) 1/t C Drinfeld Drinfeld p p p [Hat1, Hat2] 1.1 p 1.1.1 k M > 0 { Γ 1 (M) =
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
On the Galois Group of Linear Difference-Differential Equations
 On the Galois Group of Linear Difference-Differential Equations Ruyong Feng KLMM, Chinese Academy of Sciences, China Ruyong Feng (KLMM, CAS) Galois Group 1 / 19 Contents 1 Basic Notations and Concepts
On the Galois Group of Linear Difference-Differential Equations Ruyong Feng KLMM, Chinese Academy of Sciences, China Ruyong Feng (KLMM, CAS) Galois Group 1 / 19 Contents 1 Basic Notations and Concepts
Quick algorithm f or computing core attribute
 24 5 Vol. 24 No. 5 Cont rol an d Decision 2009 5 May 2009 : 100120920 (2009) 0520738205 1a, 2, 1b (1. a., b., 239012 ; 2., 230039) :,,.,.,. : ; ; ; : TP181 : A Quick algorithm f or computing core attribute
24 5 Vol. 24 No. 5 Cont rol an d Decision 2009 5 May 2009 : 100120920 (2009) 0520738205 1a, 2, 1b (1. a., b., 239012 ; 2., 230039) :,,.,.,. : ; ; ; : TP181 : A Quick algorithm f or computing core attribute
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ
 ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
GPU. CUDA GPU GeForce GTX 580 GPU 2.67GHz Intel Core 2 Duo CPU E7300 CUDA. Parallelizing the Number Partitioning Problem for GPUs
 GPU 1 1 NP number partitioning problem Pedroso CUDA GPU GeForce GTX 580 GPU 2.67GHz Intel Core 2 Duo CPU E7300 CUDA C Pedroso Python 323 Python C 12.2 Parallelizing the Number Partitioning Problem for
GPU 1 1 NP number partitioning problem Pedroso CUDA GPU GeForce GTX 580 GPU 2.67GHz Intel Core 2 Duo CPU E7300 CUDA C Pedroso Python 323 Python C 12.2 Parallelizing the Number Partitioning Problem for
Table 1. morphism U P 1 dominant (MMP) 2. dim = 3 (MMP) 3. (cf. [Ii77], [Miy01]) (Table 1) 3.
![Table 1. morphism U P 1 dominant (MMP) 2. dim = 3 (MMP) 3. (cf. [Ii77], [Miy01]) (Table 1) 3. Table 1. morphism U P 1 dominant (MMP) 2. dim = 3 (MMP) 3. (cf. [Ii77], [Miy01]) (Table 1) 3.](/thumbs/92/108955011.jpg) 338-8570 255 e-mail: tkishimo@rimath.saitama-u.ac.jp 1 C T κ(t ) 1 [Projective] κ = κ =0 κ =1 κ =2 κ =3 dim = 1 P 1 elliptic others dim = 2 P 2 or ruled elliptic surface general type dim = 3 uniruled bir.
338-8570 255 e-mail: tkishimo@rimath.saitama-u.ac.jp 1 C T κ(t ) 1 [Projective] κ = κ =0 κ =1 κ =2 κ =3 dim = 1 P 1 elliptic others dim = 2 P 2 or ruled elliptic surface general type dim = 3 uniruled bir.
Optimization, PSO) DE [1, 2, 3, 4] PSO [5, 6, 7, 8, 9, 10, 11] (P)
![Optimization, PSO) DE [1, 2, 3, 4] PSO [5, 6, 7, 8, 9, 10, 11] (P) Optimization, PSO) DE [1, 2, 3, 4] PSO [5, 6, 7, 8, 9, 10, 11] (P)](/thumbs/85/92153760.jpg) ( ) 1 ( ) : : (Differential Evolution, DE) (Particle Swarm Optimization, PSO) DE [1, 2, 3, 4] PSO [5, 6, 7, 8, 9, 10, 11] 2 2.1 (P) (P ) minimize f(x) subject to g j (x) 0, j = 1,..., q h j (x) = 0, j
( ) 1 ( ) : : (Differential Evolution, DE) (Particle Swarm Optimization, PSO) DE [1, 2, 3, 4] PSO [5, 6, 7, 8, 9, 10, 11] 2 2.1 (P) (P ) minimize f(x) subject to g j (x) 0, j = 1,..., q h j (x) = 0, j
CCA. Simple CCA-Secure Public Key Encryption from Any Non-Malleable ID-based Encryption
 All rights are reserved and copyright of this manuscript belongs to the authors. This manuscript has been published without reviewing and editing as received from the authors: posting the manuscript to
All rights are reserved and copyright of this manuscript belongs to the authors. This manuscript has been published without reviewing and editing as received from the authors: posting the manuscript to
Bundle Adjustment for 3-D Reconstruction: Implementation and Evaluation
 3 2 3 2 3 undle Adjustment or 3-D Reconstruction: Implementation and Evaluation Yuuki Iwamoto, Yasuyuki Sugaya 2 and Kenichi Kanatani We describe in detail the algorithm o bundle adjustment or 3-D reconstruction
3 2 3 2 3 undle Adjustment or 3-D Reconstruction: Implementation and Evaluation Yuuki Iwamoto, Yasuyuki Sugaya 2 and Kenichi Kanatani We describe in detail the algorithm o bundle adjustment or 3-D reconstruction
SCHOOL OF MATHEMATICAL SCIENCES G11LMA Linear Mathematics Examination Solutions
 SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
FX10 SIMD SIMD. [3] Dekker [4] IEEE754. a.lo. (SpMV Sparse matrix and vector product) IEEE754 IEEE754 [5] Double-Double Knuth FMA FMA FX10 FMA SIMD
![FX10 SIMD SIMD. [3] Dekker [4] IEEE754. a.lo. (SpMV Sparse matrix and vector product) IEEE754 IEEE754 [5] Double-Double Knuth FMA FMA FX10 FMA SIMD FX10 SIMD SIMD. [3] Dekker [4] IEEE754. a.lo. (SpMV Sparse matrix and vector product) IEEE754 IEEE754 [5] Double-Double Knuth FMA FMA FX10 FMA SIMD](/thumbs/80/81651565.jpg) FX,a),b),c) Bailey Double-Double [] FMA FMA [6] FX FMA SIMD Single Instruction Multiple Data 5 4.5. [] Bailey SIMD SIMD 8bit FMA (SpMV Sparse matrix and vector product) FX. DD Bailey Double-Double a) em49@ns.kogakuin.ac.jp
FX,a),b),c) Bailey Double-Double [] FMA FMA [6] FX FMA SIMD Single Instruction Multiple Data 5 4.5. [] Bailey SIMD SIMD 8bit FMA (SpMV Sparse matrix and vector product) FX. DD Bailey Double-Double a) em49@ns.kogakuin.ac.jp
Yoshifumi Moriyama 1,a) Ichiro Iimura 2,b) Tomotsugu Ohno 1,c) Shigeru Nakayama 3,d)
 1,a) 2,b) 1,c) 3,d) Quantum-Inspired Evolutionary Algorithm 0-1 Search Performance Analysis According to Interpretation Methods for Dealing with Permutation on Integer-Type Gene-Coding Method based on
1,a) 2,b) 1,c) 3,d) Quantum-Inspired Evolutionary Algorithm 0-1 Search Performance Analysis According to Interpretation Methods for Dealing with Permutation on Integer-Type Gene-Coding Method based on
New bounds for spherical two-distance sets and equiangular lines
 New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
Stabilization of stock price prediction by cross entropy optimization
 ,,,,,,,, Stabilization of stock prediction by cross entropy optimization Kazuki Miura, Hideitsu Hino and Noboru Murata Prediction of series data is a long standing important problem Especially, prediction
,,,,,,,, Stabilization of stock prediction by cross entropy optimization Kazuki Miura, Hideitsu Hino and Noboru Murata Prediction of series data is a long standing important problem Especially, prediction
Supplementary Materials for Evolutionary Multiobjective Optimization Based Multimodal Optimization: Fitness Landscape Approximation and Peak Detection
 IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION, VOL. XX, NO. X, XXXX XXXX Supplementary Materials for Evolutionary Multiobjective Optimization Based Multimodal Optimization: Fitness Landscape Approximation
IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION, VOL. XX, NO. X, XXXX XXXX Supplementary Materials for Evolutionary Multiobjective Optimization Based Multimodal Optimization: Fitness Landscape Approximation
GPGPU. Grover. On Large Scale Simulation of Grover s Algorithm by Using GPGPU
 GPGPU Grover 1, 2 1 3 4 Grover Grover OpenMP GPGPU Grover qubit OpenMP GPGPU, 1.47 qubit On Large Scale Simulation of Grover s Algorithm by Using GPGPU Hiroshi Shibata, 1, 2 Tomoya Suzuki, 1 Seiya Okubo
GPGPU Grover 1, 2 1 3 4 Grover Grover OpenMP GPGPU Grover qubit OpenMP GPGPU, 1.47 qubit On Large Scale Simulation of Grover s Algorithm by Using GPGPU Hiroshi Shibata, 1, 2 Tomoya Suzuki, 1 Seiya Okubo
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
ΛΥΜΕΝΕΣ ΑΣΚΗΣΕΙΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ-ΓΛΩΣΣΑ C ΑΤΕΙ (ΝΑ ΕΚΤΕΛΕΣΤΟΥΝ ΤΑ ΠΑΡΑΚΑΤΩ ΜΕ ΧΡΗΣΗ ΤΟΥ LCC COMPILER)
 ΛΥΜΕΝΕΣ ΑΣΚΗΣΕΙΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ-ΓΛΩΣΣΑ C ΑΤΕΙ (ΝΑ ΕΚΤΕΛΕΣΤΟΥΝ ΤΑ ΠΑΡΑΚΑΤΩ ΜΕ ΧΡΗΣΗ ΤΟΥ LCC COMPILER) 1. Να γραφεί πρόγραµµα το οποίο να αναγνωρίζει αν κάποιος χαρακτήρας είναι ψηφίο, κεφαλαίο γράµµα ή
ΛΥΜΕΝΕΣ ΑΣΚΗΣΕΙΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΥ-ΓΛΩΣΣΑ C ΑΤΕΙ (ΝΑ ΕΚΤΕΛΕΣΤΟΥΝ ΤΑ ΠΑΡΑΚΑΤΩ ΜΕ ΧΡΗΣΗ ΤΟΥ LCC COMPILER) 1. Να γραφεί πρόγραµµα το οποίο να αναγνωρίζει αν κάποιος χαρακτήρας είναι ψηφίο, κεφαλαίο γράµµα ή
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
A research on the influence of dummy activity on float in an AOA network and its amendments
 2008 6 6 :100026788 (2008) 0620106209,, (, 102206) : NP2hard,,..,.,,.,.,. :,,,, : TB11411 : A A research on the influence of dummy activity on float in an AOA network and its amendments WANG Qiang, LI
2008 6 6 :100026788 (2008) 0620106209,, (, 102206) : NP2hard,,..,.,,.,.,. :,,,, : TB11411 : A A research on the influence of dummy activity on float in an AOA network and its amendments WANG Qiang, LI
A Complete Divisor Class Halving Algorithm for Hyperelliptic Curve Cryptosystems of Genus Two
 A Complete Divisor Class Halving Algorithm for Hyperelliptic Curve Cryptosystems of Genus Two Izuru Kitamura 1, Masanobu Katagi 1, and Tsuyoshi Takagi 2 1 Sony Corporation, 6-7-35 Kitashinagawa Shinagawa-ku,
A Complete Divisor Class Halving Algorithm for Hyperelliptic Curve Cryptosystems of Genus Two Izuru Kitamura 1, Masanobu Katagi 1, and Tsuyoshi Takagi 2 1 Sony Corporation, 6-7-35 Kitashinagawa Shinagawa-ku,
Higher order nonlinearity of some cryptographic functions
 International Journal of Computational and Applied Mathematics. ISSN 0973-1768 Volume 1, Number (017), pp. 195-05 Research India Publications http://www.ripublication.com/ijcam.htm Higher order nonlinearity
International Journal of Computational and Applied Mathematics. ISSN 0973-1768 Volume 1, Number (017), pp. 195-05 Research India Publications http://www.ripublication.com/ijcam.htm Higher order nonlinearity
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
ΑΛΓΟΡΙΘΜΟΙ Άνοιξη I. ΜΗΛΗΣ
 ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 2016 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 2016 - Ι. ΜΗΛΗΣ 08 DP I 1 Dynamic Programming Richard Bellman (1953) Etymology (at
ΑΛΓΟΡΙΘΜΟΙ http://eclass.aueb.gr/courses/inf161/ Άνοιξη 2016 - I. ΜΗΛΗΣ ΔΥΝΑΜΙΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ ΑΛΓΟΡΙΘΜΟΙ - ΑΝΟΙΞΗ 2016 - Ι. ΜΗΛΗΣ 08 DP I 1 Dynamic Programming Richard Bellman (1953) Etymology (at
Aquinas College. Edexcel Mathematical formulae and statistics tables DO NOT WRITE ON THIS BOOKLET
 Aquinas College Edexcel Mathematical formulae and statistics tables DO NOT WRITE ON THIS BOOKLET Pearson Edexcel Level 3 Advanced Subsidiary and Advanced GCE in Mathematics and Further Mathematics Mathematical
Aquinas College Edexcel Mathematical formulae and statistics tables DO NOT WRITE ON THIS BOOKLET Pearson Edexcel Level 3 Advanced Subsidiary and Advanced GCE in Mathematics and Further Mathematics Mathematical
Equations. BSU Math 275 sec 002,003 Fall 2018 (Ultman) Final Exam Notes 1. du dv. FTLI : f (B) f (A) = f dr. F dr = Green s Theorem : y da
 BSU Math 275 sec 002,003 Fall 2018 (Ultman) Final Exam Notes 1 Equations r(t) = x(t) î + y(t) ĵ + z(t) k r = r (t) t s = r = r (t) t r(u, v) = x(u, v) î + y(u, v) ĵ + z(u, v) k S = ( ( ) r r u r v = u
BSU Math 275 sec 002,003 Fall 2018 (Ultman) Final Exam Notes 1 Equations r(t) = x(t) î + y(t) ĵ + z(t) k r = r (t) t s = r = r (t) t r(u, v) = x(u, v) î + y(u, v) ĵ + z(u, v) k S = ( ( ) r r u r v = u
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ.
 Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2015-2016 Μαρκάκης Ευάγγελος markakis@aueb.gr Ντούσκας Θεόδωρος tntouskas@aueb.gr
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2015-2016 Μαρκάκης Ευάγγελος markakis@aueb.gr Ντούσκας Θεόδωρος tntouskas@aueb.gr
 1 The problem of the representation of an integer n as the sum of a given number k of integral squares is one of the most celebrated in the theory of numbers... Almost every arithmetician of note since
1 The problem of the representation of an integer n as the sum of a given number k of integral squares is one of the most celebrated in the theory of numbers... Almost every arithmetician of note since
Homomorphism in Intuitionistic Fuzzy Automata
 International Journal of Fuzzy Mathematics Systems. ISSN 2248-9940 Volume 3, Number 1 (2013), pp. 39-45 Research India Publications http://www.ripublication.com/ijfms.htm Homomorphism in Intuitionistic
International Journal of Fuzzy Mathematics Systems. ISSN 2248-9940 Volume 3, Number 1 (2013), pp. 39-45 Research India Publications http://www.ripublication.com/ijfms.htm Homomorphism in Intuitionistic
Cyclic or elementary abelian Covers of K 4
 Cyclic or elementary abelian Covers of K 4 Yan-Quan Feng Mathematics, Beijing Jiaotong University Beijing 100044, P.R. China Summer School, Rogla, Slovenian 2011-06 Outline 1 Question 2 Main results 3
Cyclic or elementary abelian Covers of K 4 Yan-Quan Feng Mathematics, Beijing Jiaotong University Beijing 100044, P.R. China Summer School, Rogla, Slovenian 2011-06 Outline 1 Question 2 Main results 3
ΚΡΥΠΤΟΓΡΑΦΙΑ ΚΑΙ ΑΣΦΑΛΕΙΑ ΥΠΟΛΟΓΙΣΤΩΝ. Δ Εξάμηνο
 ΚΡΥΠΤΟΓΡΑΦΙΑ ΚΑΙ ΑΣΦΑΛΕΙΑ ΥΠΟΛΟΓΙΣΤΩΝ Δ Εξάμηνο Ασύμμετρη Κρυπτογράφηση (Κρυπτογραφία Δημόσιου Κλειδιού) Διδάσκων : Δρ. Παρασκευάς Κίτσος Επίκουρος Καθηγητής e-mail: pkitsos@teimes.gr, pkitsos@ieee.org
ΚΡΥΠΤΟΓΡΑΦΙΑ ΚΑΙ ΑΣΦΑΛΕΙΑ ΥΠΟΛΟΓΙΣΤΩΝ Δ Εξάμηνο Ασύμμετρη Κρυπτογράφηση (Κρυπτογραφία Δημόσιου Κλειδιού) Διδάσκων : Δρ. Παρασκευάς Κίτσος Επίκουρος Καθηγητής e-mail: pkitsos@teimes.gr, pkitsos@ieee.org
7. O κβαντικός αλγόριθμος του Shor
 7. O κβαντικός αλγόριθμος του Shor Σύνοψη Ο κβαντικός αλγόριθμος του Shor μπορεί να χρησιμοποιηθεί για την εύρεση της περιόδου περιοδικών συναρτήσεων και για την ανάλυση ενός αριθμού σε γινόμενο πρώτων
7. O κβαντικός αλγόριθμος του Shor Σύνοψη Ο κβαντικός αλγόριθμος του Shor μπορεί να χρησιμοποιηθεί για την εύρεση της περιόδου περιοδικών συναρτήσεων και για την ανάλυση ενός αριθμού σε γινόμενο πρώτων
Εισαγωγή στις Ελλειπτικές Καµπύλες
 Εισαγωγή στις Ελλειπτικές Καµπύλες Αριστείδης Κοντογεώργης Τµήµα Μαθηµατικών Πανεπιστηµίου Αθηνών. 4 Νοεµβρίου 2014, 1/19 Το ϑεώρηµα Riemann-Roch Θεωρούµε µια επιφάνεια Riemann M και το σώµα των F των
Εισαγωγή στις Ελλειπτικές Καµπύλες Αριστείδης Κοντογεώργης Τµήµα Μαθηµατικών Πανεπιστηµίου Αθηνών. 4 Νοεµβρίου 2014, 1/19 Το ϑεώρηµα Riemann-Roch Θεωρούµε µια επιφάνεια Riemann M και το σώµα των F των
Wavelet based matrix compression for boundary integral equations on complex geometries
 1 Wavelet based matrix compression for boundary integral equations on complex geometries Ulf Kähler Chemnitz University of Technology Workshop on Fast Boundary Element Methods in Industrial Applications
1 Wavelet based matrix compression for boundary integral equations on complex geometries Ulf Kähler Chemnitz University of Technology Workshop on Fast Boundary Element Methods in Industrial Applications
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ. Υποβάλλεται στην
 ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
ΑΠΟΔΟΤΙΚΗ ΑΠΟΤΙΜΗΣΗ ΕΡΩΤΗΣΕΩΝ OLAP Η ΜΕΤΑΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΕΞΕΙΔΙΚΕΥΣΗΣ Υποβάλλεται στην ορισθείσα από την Γενική Συνέλευση Ειδικής Σύνθεσης του Τμήματος Πληροφορικής Εξεταστική Επιτροπή από την Χαρά Παπαγεωργίου
The q-commutators of braided groups
 206 ( ) Journal of East China Normal University (Natural Science) No. Jan. 206 : 000-564(206)0-0009-0 q- (, 20024) : R-, [] ABCD U q(g).,, q-. : R- ; ; q- ; ; FRT- : O52.2 : A DOI: 0.3969/j.issn.000-564.206.0.002
206 ( ) Journal of East China Normal University (Natural Science) No. Jan. 206 : 000-564(206)0-0009-0 q- (, 20024) : R-, [] ABCD U q(g).,, q-. : R- ; ; q- ; ; FRT- : O52.2 : A DOI: 0.3969/j.issn.000-564.206.0.002
Πανεπιζηήμιο Πειπαιώρ Τμήμα Πληποθοπικήρ
 Πανεπιζηήμιο Πειπαιώρ Τμήμα Πληποθοπικήρ Ππόγπαμμα Μεηαπηςσιακών Σποςδών «Πληποθοπική» Μεηαπηστιακή Διαηριβή Τίηλορ Διαηπιβήρ Ονομαηεπώνςμο Φοιηηηή Παηπώνςμο Απιθμόρ Μηηπώος Επιβλέπων Ειδικές Μορφές Εξισώσεων
Πανεπιζηήμιο Πειπαιώρ Τμήμα Πληποθοπικήρ Ππόγπαμμα Μεηαπηςσιακών Σποςδών «Πληποθοπική» Μεηαπηστιακή Διαηριβή Τίηλορ Διαηπιβήρ Ονομαηεπώνςμο Φοιηηηή Παηπώνςμο Απιθμόρ Μηηπώος Επιβλέπων Ειδικές Μορφές Εξισώσεων
Second Order Partial Differential Equations
 Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
ΗΜΥ 325: Επαναληπτικές Μέθοδοι. Διδάσκων: Χρίστος Παναγιώτου
 ΗΜΥ 325: Επαναληπτικές Μέθοδοι Διδάσκων: Χρίστος Παναγιώτου ΗΜΥ 325: Επαναληπτικές Μέθοδοι. A. Levitin, Introduction to the Design and Analysis of Algorithms, 2 nd Ed. Περίληψη µαθήµατος Επιπρόσθετες Πληροφορίες
ΗΜΥ 325: Επαναληπτικές Μέθοδοι Διδάσκων: Χρίστος Παναγιώτου ΗΜΥ 325: Επαναληπτικές Μέθοδοι. A. Levitin, Introduction to the Design and Analysis of Algorithms, 2 nd Ed. Περίληψη µαθήµατος Επιπρόσθετες Πληροφορίες
: Monte Carlo EM 313, Louis (1982) EM, EM Newton-Raphson, /. EM, 2 Monte Carlo EM Newton-Raphson, Monte Carlo EM, Monte Carlo EM, /. 3, Monte Carlo EM
 2008 6 Chinese Journal of Applied Probability and Statistics Vol.24 No.3 Jun. 2008 Monte Carlo EM 1,2 ( 1,, 200241; 2,, 310018) EM, E,,. Monte Carlo EM, EM E Monte Carlo,. EM, Monte Carlo EM,,,,. Newton-Raphson.
2008 6 Chinese Journal of Applied Probability and Statistics Vol.24 No.3 Jun. 2008 Monte Carlo EM 1,2 ( 1,, 200241; 2,, 310018) EM, E,,. Monte Carlo EM, EM E Monte Carlo,. EM, Monte Carlo EM,,,,. Newton-Raphson.
CRASH COURSE IN PRECALCULUS
 CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
Blum Complexity. Αλγόριθμοι και Πολυπλοκότητα ΙΙ. Παναγιώτης Γροντάς. Δεκέμβριος
 Blum Complexity Αλγόριθμοι και Πολυπλοκότητα ΙΙ Παναγιώτης Γροντάς µπλ Δεκέμβριος 2011 Ιστορικά Στοιχεία Manuel Blum (1938, Caracas Venezuela) Turing Award (1995) Foundations Of Computational Complexity
Blum Complexity Αλγόριθμοι και Πολυπλοκότητα ΙΙ Παναγιώτης Γροντάς µπλ Δεκέμβριος 2011 Ιστορικά Στοιχεία Manuel Blum (1938, Caracas Venezuela) Turing Award (1995) Foundations Of Computational Complexity
Επιθέσεις και Ασφάλεια Κρυπτοσυστημάτων
 Στοιχεία Θεωρίας Αριθμών και Εφαρμογές στην Κρυπτογραφία Επιθέσεις και Ασφάλεια Κρυπτοσυστημάτων Άρης Παγουρτζής Στάθης Ζάχος Διαφάνειες: Παναγιώτης Γροντάς Σχολή Ηλεκτρολόγων Μηχανικών - Μηχανικών Υπολογιστών
Στοιχεία Θεωρίας Αριθμών και Εφαρμογές στην Κρυπτογραφία Επιθέσεις και Ασφάλεια Κρυπτοσυστημάτων Άρης Παγουρτζής Στάθης Ζάχος Διαφάνειες: Παναγιώτης Γροντάς Σχολή Ηλεκτρολόγων Μηχανικών - Μηχανικών Υπολογιστών
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 24/3/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
, Evaluation of a library against injection attacks
 THE INSTITUTE OF ELECTRONICS, INFMATION AND COMMUNICATION ENGINEERS TECHNICAL REPT OF IEICE., () 211 8588 4 1 1 221 0835 2 14 1 E-mail: okubo@jp.fujitsu.com, tanaka@iisec.ac.jp Web,,,, Evaluation of a
THE INSTITUTE OF ELECTRONICS, INFMATION AND COMMUNICATION ENGINEERS TECHNICAL REPT OF IEICE., () 211 8588 4 1 1 221 0835 2 14 1 E-mail: okubo@jp.fujitsu.com, tanaka@iisec.ac.jp Web,,,, Evaluation of a
Heisenberg Uniqueness pairs
 Heisenberg Uniqueness pairs Philippe Jaming Bordeaux Fourier Workshop 2013, Renyi Institute Joint work with K. Kellay Heisenberg Uniqueness Pairs µ : finite measure on R 2 µ(x, y) = R 2 e i(sx+ty) dµ(s,
Heisenberg Uniqueness pairs Philippe Jaming Bordeaux Fourier Workshop 2013, Renyi Institute Joint work with K. Kellay Heisenberg Uniqueness Pairs µ : finite measure on R 2 µ(x, y) = R 2 e i(sx+ty) dµ(s,
1 Advanced Encryption Standard (AES)
 Date: Monday, September 24, 2002 Prof.: Dr Jean-Yves Chouinard Design of Secure Computer Systems CSI4138/CEG4394 Notes on the Advanced Encryption Standard (AES) 1 Advanced Encryption Standard (AES) 1.1
Date: Monday, September 24, 2002 Prof.: Dr Jean-Yves Chouinard Design of Secure Computer Systems CSI4138/CEG4394 Notes on the Advanced Encryption Standard (AES) 1 Advanced Encryption Standard (AES) 1.1
Kenta OKU and Fumio HATTORI
 DEIM Forum 2012 A1-3 525 8577 1 1 1 E-mail: oku@fc.ritsumei.ac.jp, fhattori@is.ritsumei.ac.jp Kenta OKU and Fumio HATTORI College of Information Science and Engineering, 1 1 1 Nojihigashi, Kusatsu-city,
DEIM Forum 2012 A1-3 525 8577 1 1 1 E-mail: oku@fc.ritsumei.ac.jp, fhattori@is.ritsumei.ac.jp Kenta OKU and Fumio HATTORI College of Information Science and Engineering, 1 1 1 Nojihigashi, Kusatsu-city,
Partial Differential Equations in Biology The boundary element method. March 26, 2013
 The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
ER-Tree (Extended R*-Tree)
 1-9825/22/13(4)768-6 22 Journal of Software Vol13, No4 1, 1, 2, 1 1, 1 (, 2327) 2 (, 3127) E-mail xhzhou@ustceducn,,,,,,, 1, TP311 A,,,, Elias s Rivest,Cleary Arya Mount [1] O(2 d ) Arya Mount [1] Friedman,Bentley
1-9825/22/13(4)768-6 22 Journal of Software Vol13, No4 1, 1, 2, 1 1, 1 (, 2327) 2 (, 3127) E-mail xhzhou@ustceducn,,,,,,, 1, TP311 A,,,, Elias s Rivest,Cleary Arya Mount [1] O(2 d ) Arya Mount [1] Friedman,Bentley
Applying Markov Decision Processes to Role-playing Game
 1,a) 1 1 1 1 2011 8 25, 2012 3 2 MDPRPG RPG MDP RPG MDP RPG MDP RPG MDP RPG Applying Markov Decision Processes to Role-playing Game Yasunari Maeda 1,a) Fumitaro Goto 1 Hiroshi Masui 1 Fumito Masui 1 Masakiyo
1,a) 1 1 1 1 2011 8 25, 2012 3 2 MDPRPG RPG MDP RPG MDP RPG MDP RPG MDP RPG Applying Markov Decision Processes to Role-playing Game Yasunari Maeda 1,a) Fumitaro Goto 1 Hiroshi Masui 1 Fumito Masui 1 Masakiyo
An Automatic Modulation Classifier using a Frequency Discriminator for Intelligent Software Defined Radio
 C IEEJ Transactions on Electronics, Information and Systems Vol.133 No.5 pp.910 915 DOI: 10.1541/ieejeiss.133.910 a) An Automatic Modulation Classifier using a Frequency Discriminator for Intelligent Software
C IEEJ Transactions on Electronics, Information and Systems Vol.133 No.5 pp.910 915 DOI: 10.1541/ieejeiss.133.910 a) An Automatic Modulation Classifier using a Frequency Discriminator for Intelligent Software
Cable Systems - Postive/Negative Seq Impedance
 Cable Systems - Postive/Negative Seq Impedance Nomenclature: GMD GMR - geometrical mead distance between conductors; depends on construction of the T-line or cable feeder - geometric mean raduius of conductor
Cable Systems - Postive/Negative Seq Impedance Nomenclature: GMD GMR - geometrical mead distance between conductors; depends on construction of the T-line or cable feeder - geometric mean raduius of conductor
The Jordan Form of Complex Tridiagonal Matrices
 The Jordan Form of Complex Tridiagonal Matrices Ilse Ipsen North Carolina State University ILAS p.1 Goal Complex tridiagonal matrix α 1 β 1. γ T = 1 α 2........ β n 1 γ n 1 α n Jordan decomposition T =
The Jordan Form of Complex Tridiagonal Matrices Ilse Ipsen North Carolina State University ILAS p.1 Goal Complex tridiagonal matrix α 1 β 1. γ T = 1 α 2........ β n 1 γ n 1 α n Jordan decomposition T =
Toward a SPARQL Query Execution Mechanism using Dynamic Mapping Adaptation -A Preliminary Report- Takuya Adachi 1 Naoki Fukuta 2.
 SIG-SWO-041-05 SPAIDA: SPARQL Toward a SPARQL Query Execution Mechanism using Dynamic Mapping Adaptation -A Preliminary Report- 1 2 Takuya Adachi 1 Naoki Fukuta 2 1 1 Faculty of Informatics, Shizuoka University
SIG-SWO-041-05 SPAIDA: SPARQL Toward a SPARQL Query Execution Mechanism using Dynamic Mapping Adaptation -A Preliminary Report- 1 2 Takuya Adachi 1 Naoki Fukuta 2 1 1 Faculty of Informatics, Shizuoka University
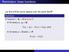
Reminders: linear functions
 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Bounding Nonsplitting Enumeration Degrees
 Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Filter Diagonalization Method which Constructs an Approximation of Orthonormal Basis of the Invariant Subspace from the Filtered Vectors
 1 Av=λBv [a, b] subspace subspace B- subspace B- [a, b] B- Filter Diagonalization Method which Constructs an Approximation of Orthonormal Basis of the Invariant Subspace from the Filtered Vectors Hiroshi
1 Av=λBv [a, b] subspace subspace B- subspace B- [a, b] B- Filter Diagonalization Method which Constructs an Approximation of Orthonormal Basis of the Invariant Subspace from the Filtered Vectors Hiroshi
[4] 1.2 [5] Bayesian Approach min-max min-max [6] UCB(Upper Confidence Bound ) UCT [7] [1] ( ) Amazons[8] Lines of Action(LOA)[4] Winands [4] 1
![[4] 1.2 [5] Bayesian Approach min-max min-max [6] UCB(Upper Confidence Bound ) UCT [7] [1] ( ) Amazons[8] Lines of Action(LOA)[4] Winands [4] 1 [4] 1.2 [5] Bayesian Approach min-max min-max [6] UCB(Upper Confidence Bound ) UCT [7] [1] ( ) Amazons[8] Lines of Action(LOA)[4] Winands [4] 1](/thumbs/93/113995345.jpg) 1,a) Bayesian Approach An Application of Monte-Carlo Tree Search Algorithm for Shogi Player Based on Bayesian Approach Daisaku Yokoyama 1,a) Abstract: Monte-Carlo Tree Search (MCTS) algorithm is quite
1,a) Bayesian Approach An Application of Monte-Carlo Tree Search Algorithm for Shogi Player Based on Bayesian Approach Daisaku Yokoyama 1,a) Abstract: Monte-Carlo Tree Search (MCTS) algorithm is quite
C++ 78 (478) A Parallel Skeleton Library in C++ with Optimization
 78 (478) C++ BMF C++ Skeletal parallel programming enables programmers to build a parallel program from ready-made components called skeletons (parallel primitives) for which efficient implementations
78 (478) C++ BMF C++ Skeletal parallel programming enables programmers to build a parallel program from ready-made components called skeletons (parallel primitives) for which efficient implementations
Lattice-based (Post Quantum) Cryptography
 Lattice-based (Post Quantum) Cryptography Divesh Aggarwal Center of Quantum Technologies, Singapore February 8, 28 Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 1 / 30 Lattices A lattice
Lattice-based (Post Quantum) Cryptography Divesh Aggarwal Center of Quantum Technologies, Singapore February 8, 28 Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 1 / 30 Lattices A lattice
FORTRAN & Αντικειμενοστραφής Προγραμματισμός ΣΝΜΜ 2017
 FORTRAN & Αντικειμενοστραφής Προγραμματισμός ΣΝΜΜ 2017 Μ4. Συναρτήσεις, Υπορουτίνες, Ενότητες - Ασκήσεις Γεώργιος Παπαλάμπρου Επικ. Καθηγητής ΕΜΠ Εργαστήριο Ναυτικής Μηχανολογίας george.papalambrou@lme.ntua.gr
FORTRAN & Αντικειμενοστραφής Προγραμματισμός ΣΝΜΜ 2017 Μ4. Συναρτήσεις, Υπορουτίνες, Ενότητες - Ασκήσεις Γεώργιος Παπαλάμπρου Επικ. Καθηγητής ΕΜΠ Εργαστήριο Ναυτικής Μηχανολογίας george.papalambrou@lme.ntua.gr
Orthogonalization Library with a Numerical Computation Policy Interface
 Vol. 46 No. SIG 7(ACS 10) May 2005 DGKS PC 10 8 10 14 4.8 Orthogonalization Library with a Numerical Computation Policy Interface Ken Naono, Mitsuyoshi Igai and Hiroyuki Kidachi We propose an orthogonalization
Vol. 46 No. SIG 7(ACS 10) May 2005 DGKS PC 10 8 10 14 4.8 Orthogonalization Library with a Numerical Computation Policy Interface Ken Naono, Mitsuyoshi Igai and Hiroyuki Kidachi We propose an orthogonalization
{takasu, Conditional Random Field
 DEIM Forum 2016 C8-6 CRF 700 8530 3 1 1 700 8530 3 1 1 101 8430 2-1-2 E-mail: pobp52cw@s.okayama-u.ac.jp, ohta@de.cs.okayama-u.ac.jp, {takasu, adachi}@nii.ac.jp Conditional Random Field 1. Conditional
DEIM Forum 2016 C8-6 CRF 700 8530 3 1 1 700 8530 3 1 1 101 8430 2-1-2 E-mail: pobp52cw@s.okayama-u.ac.jp, ohta@de.cs.okayama-u.ac.jp, {takasu, adachi}@nii.ac.jp Conditional Random Field 1. Conditional
Discriminantal arrangement
 Discriminantal arrangement YAMAGATA So C k n arrangement C n discriminantal arrangement 1989 Manin-Schectman Braid arrangement Discriminantal arrangement Gr(3, n) S.Sawada S.Settepanella 1 A arrangement
Discriminantal arrangement YAMAGATA So C k n arrangement C n discriminantal arrangement 1989 Manin-Schectman Braid arrangement Discriminantal arrangement Gr(3, n) S.Sawada S.Settepanella 1 A arrangement
Solving an Air Conditioning System Problem in an Embodiment Design Context Using Constraint Satisfaction Techniques
 Solving an Air Conditioning System Problem in an Embodiment Design Context Using Constraint Satisfaction Techniques Raphael Chenouard, Patrick Sébastian, Laurent Granvilliers To cite this version: Raphael
Solving an Air Conditioning System Problem in an Embodiment Design Context Using Constraint Satisfaction Techniques Raphael Chenouard, Patrick Sébastian, Laurent Granvilliers To cite this version: Raphael
ES440/ES911: CFD. Chapter 5. Solution of Linear Equation Systems
 ES440/ES911: CFD Chapter 5. Solution of Linear Equation Systems Dr Yongmann M. Chung http://www.eng.warwick.ac.uk/staff/ymc/es440.html Y.M.Chung@warwick.ac.uk School of Engineering & Centre for Scientific
ES440/ES911: CFD Chapter 5. Solution of Linear Equation Systems Dr Yongmann M. Chung http://www.eng.warwick.ac.uk/staff/ymc/es440.html Y.M.Chung@warwick.ac.uk School of Engineering & Centre for Scientific
Public Key Cryptography. Dimitris Mitropoulos
 Public Key Cryptography Dimitris Mitropoulos dimitro@di.uoa.gr Symmetric Cryptography Key Management Challenge K13 U1 U3 K12 K34 K23 K14 U2 K24 U4 Trusted Third Party (TTP) Bob KΒ K1 U1 KAB TTP KΑ K2 Alice
Public Key Cryptography Dimitris Mitropoulos dimitro@di.uoa.gr Symmetric Cryptography Key Management Challenge K13 U1 U3 K12 K34 K23 K14 U2 K24 U4 Trusted Third Party (TTP) Bob KΒ K1 U1 KAB TTP KΑ K2 Alice
Optimal Impartial Selection
 Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
Optimal Impartial Selection Max Klimm Technische Universität Berlin Head of Junior Research Group Optimization under Uncertainty Einstein-Zentrum für Mathematik Introduction select member of a set of agents
 DEIM Forum 2016 G7-5 152-8565 2-12-1 152-8565 2-12-1 889-1601 5200 E-mail: uragaki.k.aa@m.titech.ac.jp,,,.,,,,,,, 1. 1. 1,,,,,,.,,,,, 1. 2 [1],,,,, [2] (, SPM),,,,,,,. [3],, [4]. 2 A,B, A B, B A, B, 2,,,
DEIM Forum 2016 G7-5 152-8565 2-12-1 152-8565 2-12-1 889-1601 5200 E-mail: uragaki.k.aa@m.titech.ac.jp,,,.,,,,,,, 1. 1. 1,,,,,,.,,,,, 1. 2 [1],,,,, [2] (, SPM),,,,,,,. [3],, [4]. 2 A,B, A B, B A, B, 2,,,
Υπολογιστική Θεωρία Αριθμών και Κρυπτογραφία
 Υπολογιστική Θεωρία Αριθμών και Κρυπτογραφία Επιθέσεις και Ασφάλεια Κρυπτοσυστημάτων Διδάσκοντες: Άρης Παγουρτζής Στάθης Ζάχος Διαφάνειες: Παναγιώτης Γροντάς Εθνικό Μετσόβιο Πολυτεχνείο Σχολή Ηλεκτρολόγων
Υπολογιστική Θεωρία Αριθμών και Κρυπτογραφία Επιθέσεις και Ασφάλεια Κρυπτοσυστημάτων Διδάσκοντες: Άρης Παγουρτζής Στάθης Ζάχος Διαφάνειες: Παναγιώτης Γροντάς Εθνικό Μετσόβιο Πολυτεχνείο Σχολή Ηλεκτρολόγων
page: 2 (2.1) n + 1 n {n} N 0, 1, 2
 page: 1 1 1 ( ) ( ) ( ) ( 1 ) 1) 2 1 page: 2 2 [ 4 ] [11] ( [11] ) Chapter I 0 n ( n ) (2.1) n + 1 n {n} 0, 1, 2, 3, 4,..., { }, {, { }}, {, { }, {, { }}}, {, { }, {, { }}, {, { }, {, { }}}},... n n =
page: 1 1 1 ( ) ( ) ( ) ( 1 ) 1) 2 1 page: 2 2 [ 4 ] [11] ( [11] ) Chapter I 0 n ( n ) (2.1) n + 1 n {n} 0, 1, 2, 3, 4,..., { }, {, { }}, {, { }, {, { }}}, {, { }, {, { }}, {, { }, {, { }}}},... n n =
GÖKHAN ÇUVALCIOĞLU, KRASSIMIR T. ATANASSOV, AND SINEM TARSUSLU(YILMAZ)
 IFSCOM016 1 Proceeding Book No. 1 pp. 155-161 (016) ISBN: 978-975-6900-54-3 SOME RESULTS ON S α,β AND T α,β INTUITIONISTIC FUZZY MODAL OPERATORS GÖKHAN ÇUVALCIOĞLU, KRASSIMIR T. ATANASSOV, AND SINEM TARSUSLU(YILMAZ)
IFSCOM016 1 Proceeding Book No. 1 pp. 155-161 (016) ISBN: 978-975-6900-54-3 SOME RESULTS ON S α,β AND T α,β INTUITIONISTIC FUZZY MODAL OPERATORS GÖKHAN ÇUVALCIOĞLU, KRASSIMIR T. ATANASSOV, AND SINEM TARSUSLU(YILMAZ)
Homework 8 Model Solution Section
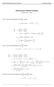 MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
A summation formula ramified with hypergeometric function and involving recurrence relation
 South Asian Journal of Mathematics 017, Vol. 7 ( 1): 1 4 www.sajm-online.com ISSN 51-151 RESEARCH ARTICLE A summation formula ramified with hypergeometric function and involving recurrence relation Salahuddin
South Asian Journal of Mathematics 017, Vol. 7 ( 1): 1 4 www.sajm-online.com ISSN 51-151 RESEARCH ARTICLE A summation formula ramified with hypergeometric function and involving recurrence relation Salahuddin
SOME INTUITIONISTIC FUZZY MODAL OPERATORS OVER INTUITIONISTIC FUZZY IDEALS AND GROUPS
 IFSCOM016 1 Proceeding Book No. 1 pp. 84-90 (016) ISBN: 978-975-6900-54-3 SOME INTUITIONISTIC FUZZY MODAL OPERATORS OVER INTUITIONISTIC FUZZY IDEALS AND GROUPS SINEM TARSUSLU(YILMAZ), GÖKHAN ÇUVALCIOĞLU,
IFSCOM016 1 Proceeding Book No. 1 pp. 84-90 (016) ISBN: 978-975-6900-54-3 SOME INTUITIONISTIC FUZZY MODAL OPERATORS OVER INTUITIONISTIC FUZZY IDEALS AND GROUPS SINEM TARSUSLU(YILMAZ), GÖKHAN ÇUVALCIOĞLU,
APPENDICES APPENDIX A. STATISTICAL TABLES AND CHARTS 651 APPENDIX B. BIBLIOGRAPHY 677 APPENDIX C. ANSWERS TO SELECTED EXERCISES 679
 APPENDICES APPENDIX A. STATISTICAL TABLES AND CHARTS 1 Table I Summary of Common Probability Distributions 2 Table II Cumulative Standard Normal Distribution Table III Percentage Points, 2 of the Chi-Squared
APPENDICES APPENDIX A. STATISTICAL TABLES AND CHARTS 1 Table I Summary of Common Probability Distributions 2 Table II Cumulative Standard Normal Distribution Table III Percentage Points, 2 of the Chi-Squared
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
EM Baum-Welch. Step by Step the Baum-Welch Algorithm and its Application 2. HMM Baum-Welch. Baum-Welch. Baum-Welch Baum-Welch.
 Baum-Welch Step by Step the Baum-Welch Algorithm and its Application Jin ichi MURAKAMI EM EM EM Baum-Welch Baum-Welch Baum-Welch Baum-Welch, EM 1. EM 2. HMM EM (Expectationmaximization algorithm) 1 3.
Baum-Welch Step by Step the Baum-Welch Algorithm and its Application Jin ichi MURAKAMI EM EM EM Baum-Welch Baum-Welch Baum-Welch Baum-Welch, EM 1. EM 2. HMM EM (Expectationmaximization algorithm) 1 3.
Arithmetical applications of lagrangian interpolation. Tanguy Rivoal. Institut Fourier CNRS and Université de Grenoble 1
 Arithmetical applications of lagrangian interpolation Tanguy Rivoal Institut Fourier CNRS and Université de Grenoble Conference Diophantine and Analytic Problems in Number Theory, The 00th anniversary
Arithmetical applications of lagrangian interpolation Tanguy Rivoal Institut Fourier CNRS and Université de Grenoble Conference Diophantine and Analytic Problems in Number Theory, The 00th anniversary
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM
 SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr T t N n) Pr max X 1,..., X N ) t N n) Pr max
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr T t N n) Pr max X 1,..., X N ) t N n) Pr max
College of Life Science, Dalian Nationalities University, Dalian , PR China.
 Electronic Supplementary Material (ESI) for New Journal of Chemistry. This journal is The Royal Society of Chemistry and the Centre National de la Recherche Scientifique 2018 Postsynthetic modification
Electronic Supplementary Material (ESI) for New Journal of Chemistry. This journal is The Royal Society of Chemistry and the Centre National de la Recherche Scientifique 2018 Postsynthetic modification
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ.
 Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2011-2012 Μαριάς Ιωάννης marias@aueb.gr Μαρκάκης Ευάγγελος markakis@gmail.com
Οικονομικό Πανεπιστήμιο Αθηνών Τμήμα Πληροφορικής ΠΜΣ στα Πληροφοριακά Συστήματα Κρυπτογραφία και Εφαρμογές Διαλέξεις Ακ. Έτους 2011-2012 Μαριάς Ιωάννης marias@aueb.gr Μαρκάκης Ευάγγελος markakis@gmail.com
EE434 ASIC & Digital Systems Arithmetic Circuits
 EE434 ASIC & Digital Systems Arithmetic Circuits Spring 25 Dae Hyun Kim daehyun@eecs.wsu.edu Arithmetic Circuits What we will learn Adders Basic High-speed 2 Adder -bit adder SSSSSS = AA BB CCCC CCCC =
EE434 ASIC & Digital Systems Arithmetic Circuits Spring 25 Dae Hyun Kim daehyun@eecs.wsu.edu Arithmetic Circuits What we will learn Adders Basic High-speed 2 Adder -bit adder SSSSSS = AA BB CCCC CCCC =
SUPPLEMENTARY INFORMATION
 Capture of Elusive Hydroxymethylene and its Fast Disappearance through Tunnelling Peter R. Schreiner a, Hans Peter Reisenauer a, Frank Pickard b, Andrew C. Simmonett b, Wesley D. Allen b, Edit Mátyus c
Capture of Elusive Hydroxymethylene and its Fast Disappearance through Tunnelling Peter R. Schreiner a, Hans Peter Reisenauer a, Frank Pickard b, Andrew C. Simmonett b, Wesley D. Allen b, Edit Mátyus c
High order interpolation function for surface contact problem
 3 016 5 Journal of East China Normal University Natural Science No 3 May 016 : 1000-564101603-0009-1 1 1 1 00444; E- 00030 : Lagrange Lobatto Matlab : ; Lagrange; : O41 : A DOI: 103969/jissn1000-56410160300
3 016 5 Journal of East China Normal University Natural Science No 3 May 016 : 1000-564101603-0009-1 1 1 1 00444; E- 00030 : Lagrange Lobatto Matlab : ; Lagrange; : O41 : A DOI: 103969/jissn1000-56410160300
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1
 Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
DiracDelta. Notations. Primary definition. Specific values. General characteristics. Traditional name. Traditional notation
 DiracDelta Notations Traditional name Dirac delta function Traditional notation x Mathematica StandardForm notation DiracDeltax Primary definition 4.03.02.000.0 x Π lim ε ; x ε0 x 2 2 ε Specific values
DiracDelta Notations Traditional name Dirac delta function Traditional notation x Mathematica StandardForm notation DiracDeltax Primary definition 4.03.02.000.0 x Π lim ε ; x ε0 x 2 2 ε Specific values
Expansion formulae of sampled zeros and a method to relocate the zeros
 Vol., No., /7 29 Expansion formulae of sampled zeros and a method to relocate the zeros Takuya SOGO It is known that the transfer function of sampled-data system has so-called intrinsic and discretization
Vol., No., /7 29 Expansion formulae of sampled zeros and a method to relocate the zeros Takuya SOGO It is known that the transfer function of sampled-data system has so-called intrinsic and discretization
Wishart α-determinant, α-hafnian
 Wishart α-determinant, α-hafnian (, JST CREST) (, JST CREST), Wishart,. ( )Wishart,. determinant Hafnian analogue., ( )Wishart,. 1 Introduction, Wishart. p ν M = (µ 1,..., µ ν ) = (µ ij ) i=1,...,p p p
Wishart α-determinant, α-hafnian (, JST CREST) (, JST CREST), Wishart,. ( )Wishart,. determinant Hafnian analogue., ( )Wishart,. 1 Introduction, Wishart. p ν M = (µ 1,..., µ ν ) = (µ ij ) i=1,...,p p p
Fourier Series. MATH 211, Calculus II. J. Robert Buchanan. Spring Department of Mathematics
 Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
BMI/CS 776 Lecture #14: Multiple Alignment - MUSCLE. Colin Dewey
 BMI/CS 776 Lecture #14: Multiple Alignment - MUSCLE Colin Dewey 2007.03.08 1 Importance of protein multiple alignment Phylogenetic tree estimation Prediction of protein secondary structure Critical residue
BMI/CS 776 Lecture #14: Multiple Alignment - MUSCLE Colin Dewey 2007.03.08 1 Importance of protein multiple alignment Phylogenetic tree estimation Prediction of protein secondary structure Critical residue
ITU-R SA (2010/01)! " # $% & '( ) * +,
 (010/01)! " # $% & '( ) * +, SA ii.. (IPR) (ITU-T/ITU-R/ISO/IEC).ITU-R 1 1 http://www.itu.int/itu-r/go/patents/en. (http://www.itu.int/publ/r-rec/en ) () ( ) BO BR BS BT F M P RA S RS SA SF SM SNG TF V
(010/01)! " # $% & '( ) * +, SA ii.. (IPR) (ITU-T/ITU-R/ISO/IEC).ITU-R 1 1 http://www.itu.int/itu-r/go/patents/en. (http://www.itu.int/publ/r-rec/en ) () ( ) BO BR BS BT F M P RA S RS SA SF SM SNG TF V
Intuitionistic Fuzzy Ideals of Near Rings
 International Mathematical Forum, Vol. 7, 202, no. 6, 769-776 Intuitionistic Fuzzy Ideals of Near Rings P. K. Sharma P.G. Department of Mathematics D.A.V. College Jalandhar city, Punjab, India pksharma@davjalandhar.com
International Mathematical Forum, Vol. 7, 202, no. 6, 769-776 Intuitionistic Fuzzy Ideals of Near Rings P. K. Sharma P.G. Department of Mathematics D.A.V. College Jalandhar city, Punjab, India pksharma@davjalandhar.com
