Lattice-based (Post Quantum) Cryptography
|
|
|
- Διώνη Κανακάρης-Ρούφος
- 7 χρόνια πριν
- Προβολές:
Transcript
1 Lattice-based (Post Quantum) Cryptography Divesh Aggarwal Center of Quantum Technologies, Singapore February 8, 28 Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 1 / 30
2 Lattices A lattice is a set of points L = {a 1 v a nv n a i integers}. for some linearly independent vectors v 1,..., v n R n. We call v 1,..., v n a basis of L, and n the dimension of the lattice. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 2 / 30
3 Basis is Not Unique Good Basis: v 1, v 2 Bad Basis: v 1, v 2 Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 3 / 30
4 Hard Problems SVP: Given a lattice, find the shortest non-zero vector (of length λ 1 ). Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 4 / 30
5 Hard Problems SVP: Given a lattice, find the shortest non-zero vector (of length λ 1 ). ApproxSVP γ : Given a lattice basis, find a vector of length γ λ 1. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 4 / 30
6 Hard Problems SVP: Given a lattice, find the shortest non-zero vector (of length λ 1 ). ApproxSVP γ : Given a lattice basis, find a vector of length γ λ 1. GapSVP γ : Given a basis and d, decide whether λ 1 d or λ 1 > γ d. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 4 / 30
7 Hard Problems SVP: Given a lattice, find the shortest non-zero vector (of length λ 1 ). ApproxSVP γ : Given a lattice basis, find a vector of length γ λ 1. GapSVP γ : Given a basis and d, decide whether λ 1 d or λ 1 > γ d. There are also other hard problems like CVP, SIVP Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 4 / 30
8 GapSVP γ - Algorithms and Complexity γ 2 (log n)1 ɛ n n O(1) (1 + ɛ) n NP Hard Problem co-np Cryptography P [Ajt98,..., HR07] [GG98, AR05] [Ajtai96,...] [LLL82, Sch87] Fastest known algorithms for γ = r n/r run in 2 O(r) poly(n) time, i.e., For γ = poly(n), the running time is exponential in n. In particular, fastest known algorithm for γ close to 1 runs in time 2 n+o(n) [ADRS15,AS18] Under the Gap exponential time hypothesis, no algorithm can solve GapSVP γ for a constant γ 1 in time better than 2 cn for some constant c [AS17]. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 5 / 30
9 Lattices and Cryptography The first applications included attacking knapsack-based cryptosystems [LagOdl85] and variants of RSA [Has85,Cop]. Lattices began to be used to create cryptography starting with a breakthrough work of Ajtai[Ajt96]. Cryptography based on lattices has many advantages compared with traditional cryptography like RSA: It has strong, mathematically proven, security. It is believed to be resistant to quantum computers. In some cases, it is much faster. It can do more, e.g., fully homomorphic encryption, which is one of the most important cryptographic primitives. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 6 / 30
10 Lattice-based Crypto Public-key Encryption [Reg05,KTX07,PKW08] CCA-Secure PKE [PW08,Pei09]. Identity-based Encryption [GPV08] Oblivious Transfer [PVW08] Circular Secure Encryption [ACPS09] Hierarchical Identity-based Encryption [Gen09,CHKP09,ABB09]. Fully Homomorphic Encryption [Gen09,BV11,Bra12]. And more... Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 7 / 30
11 Talk Outline GGH Public Key Encryption Scheme LWE Problem and Applications Efficiency from Rings Recent Implementations. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 8 / 30
12 GGH Public Key Encryption Scheme Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, 28 9 / 30
13 Public key encryption Suppose Alice wants to send a message m privately to Bob over a public channel. Key Generation: Bob generates a pair (pk, sk). Encryption: Alice sends c = Enc(pk, m) to Bob. Decryption: Bob obtains the message m = Dec(sk, m). Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
14 Public key encryption Suppose Alice wants to send a message m privately to Bob over a public channel. Key Generation: Bob generates a pair (pk, sk). Encryption: Alice sends c = Enc(pk, m) to Bob. Decryption: Bob obtains the message m = Dec(sk, m). Security: An eavesdropper shouldn t learn anything about the message given the public-key and the ciphertext. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
15 Digital Signatures Suppose you wish to digitally sign the message m. Key Generation: The algorithm generates a pair (pk, sk). Sign: A tag for the message is computed using the signing algorithm t = Sign(sk, m). Verify: The signature can be verified using the public key Verify(pk, t, m ) {True, False}. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
16 Digital Signatures Suppose you wish to digitally sign the message m. Key Generation: The algorithm generates a pair (pk, sk). Sign: A tag for the message is computed using the signing algorithm t = Sign(sk, m). Verify: The signature can be verified using the public key Verify(pk, t, m ) {True, False}. Security: An eavesdropper shouldn t be able to forge a signature given a valid signature and the public key. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
17 Reducing a vector modulo a basis u mod B = u B B 1 t If u = α 1 u α n u n, then u mod B = (α 1 α 1 ) u (α n α n ) u n. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
18 Bad Basis u mod B is likely a long vector. Note that u u mod B is a lattice vector close to u. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
19 Good Basis u mod B is a short vector. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
20 Good Basis u mod B is a short vector. Note that u u mod B is a lattice vector close to u. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
21 The encryption scheme Map the message m to a vector close to the origin. Encryption: c = m mod B pk (public basis) Processed plaintext Ciphertext Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
22 The encryption scheme Map the message m to a vector close to the origin. Encryption: c = m mod B pk (public basis) Decryption: m = c mod B sk (secret basis) Processed plaintext Ciphertext Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
23 More on the GGH Scheme There is a dual digital signature scheme based on the same principle. Map the message m to a random vector in space. Signature: t = m m mod B sk (secret(good) basis) resulting in a lattice vector close to m. Verification: Use the public (bad) basis to check whether t is a lattice vector and that t m is short. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
24 More on the GGH Scheme There is a dual digital signature scheme based on the same principle. Map the message m to a random vector in space. Signature: t = m m mod B sk (secret(good) basis) resulting in a lattice vector close to m. Verification: Use the public (bad) basis to check whether t is a lattice vector and that t m is short. Nguyen in 1999 pointed out a flaw in the GGH scheme. He showed that every ciphertext reveals information about the plaintext. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
25 More on the GGH Scheme There is a dual digital signature scheme based on the same principle. Map the message m to a random vector in space. Signature: t = m m mod B sk (secret(good) basis) resulting in a lattice vector close to m. Verification: Use the public (bad) basis to check whether t is a lattice vector and that t m is short. Nguyen in 1999 pointed out a flaw in the GGH scheme. He showed that every ciphertext reveals information about the plaintext. The principle of GGH, however, has been used in several follow-up schemes. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
26 More on the GGH Scheme There is a dual digital signature scheme based on the same principle. Map the message m to a random vector in space. Signature: t = m m mod B sk (secret(good) basis) resulting in a lattice vector close to m. Verification: Use the public (bad) basis to check whether t is a lattice vector and that t m is short. Nguyen in 1999 pointed out a flaw in the GGH scheme. He showed that every ciphertext reveals information about the plaintext. The principle of GGH, however, has been used in several follow-up schemes. In fact, the first fully homomorphic encryption scheme candidate by Gentry [2009] was based on the same principle. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
27 Talk Outline GGH Public Key Encryption Scheme LWE Problem and Applications Efficiency from Rings Recent Implementations. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
28 LWE Problem and Applications Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
29 Learning with Errors Problem [Regev05] Parameters: Dimension n, modulus q = poly(n), error distribution Search: Find uniformly random secret s Z n q given A 11 A 12 A A 1n A = A 21 A 22 A A 2n and b = A s + e, A m1 A m2 A m3... A mn where A Z m n q is chosen uniformly at random and e Z m q is some short noise distribution. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
30 Learning with Errors Problem [Regev05] Parameters: Dimension n, modulus q = poly(n), error distribution Search: Find uniformly random secret s Z n q given A 11 A 12 A A 1n A = A 21 A 22 A A 2n and b = A s + e, A m1 A m2 A m3... A mn where A Z m n q is chosen uniformly at random and e Z m q is some short noise distribution. Decision: Distinguish (A, b) from (A, u) where u is uniform in Z m q. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
31 Learning with Errors Problem [Regev05] Parameters: Dimension n, modulus q = poly(n), error distribution Search: Find uniformly random secret s Z n q given A 11 A 12 A A 1n A = A 21 A 22 A A 2n and b = A s + e, A m1 A m2 A m3... A mn where A Z m n q is chosen uniformly at random and e Z m q is some short noise distribution. Decision: Distinguish (A, b) from (A, u) where u is uniform in Z m q. Worst case to Average Case: Break Crypto = Decision LWE = Search LWE = GapSVP poly(n) Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
32 A PKE scheme from decision LWE hardness Suppose Alice wants to send a bit µ {0, 1} privately to Bob over a public channel. Key Generation: Bob chooses q, m, n and A Z m n q, s Z n q are chosen uniformly at random and e Z m q is chosen from the LWE noise distribution. Then pk = A, b = A s + e, sk = s. Encryption: Alice chooses uniform r {0, 1} m and sends c = (r A, r b + µ q 2 ). Decryption: Bob on receiving the ciphertext (C 1, c 2 ) checks whether c 2 C 1 s is closer to 0 or q and hence deciphers the 2 message bit µ. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
33 A PKE scheme from decision LWE hardness Suppose Alice wants to send a bit µ {0, 1} privately to Bob over a public channel. Key Generation: Bob chooses q, m, n and A Z m n q, s Z n q are chosen uniformly at random and e Z m q is chosen from the LWE noise distribution. Then pk = A, b = A s + e, sk = s. Encryption: Alice chooses uniform r {0, 1} m and sends c = (r A, r b + µ q 2 ). Decryption: Bob on receiving the ciphertext (C 1, c 2 ) checks whether c 2 C 1 s is closer to 0 or q and hence deciphers the 2 message bit µ. Security is almost immediate from the Decision LWE Hardness assumption. The ciphertext looks random given the public key. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
34 Talk Outline GGH Public Key Encryption Scheme LWE Problem and Applications Efficiency from Rings Recent Implementations. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
35 Efficiency from Rings. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
36 How efficient is LWE? Getting one pseudorandom b i Z q requires an n-dimensional inner product modulo q. Cryptosystems have larger keys of size larger than n 2 log q. Wishful thinking: (a 1, a 2,..., a n) (s 1, s 2,..., s n) + (e 1, e 2,..., e n) = (b 1, b 2,..., b n). Get n pseudorandom elements in Z q from one inner product. Replace every n 2 length key by a key of length n. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
37 How efficient is LWE? Getting one pseudorandom b i Z q requires an n-dimensional inner product modulo q. Cryptosystems have larger keys of size larger than n 2 log q. Wishful thinking: (a 1, a 2,..., a n) (s 1, s 2,..., s n) + (e 1, e 2,..., e n) = (b 1, b 2,..., b n). Get n pseudorandom elements in Z q from one inner product. Replace every n 2 length key by a key of length n. Question: How to define the operation? Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
38 How efficient is LWE? Getting one pseudorandom b i Z q requires an n-dimensional inner product modulo q. Cryptosystems have larger keys of size larger than n 2 log q. Wishful thinking: (a 1, a 2,..., a n) (s 1, s 2,..., s n) + (e 1, e 2,..., e n) = (b 1, b 2,..., b n). Get n pseudorandom elements in Z q from one inner product. Replace every n 2 length key by a key of length n. Question: How to define the operation? With small error, co-ordinate wise multiplication is insecure. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
39 LWE over Rings Let R = Z[X]/(X n + 1), and R q = R/qR. Operations in R q are very efficient using algorithms similar to FFT. Search: Find secret s R q given a 1 R q, b 1 = a 1 s + e 1 a 2 R q, b 2 = a 2 s + e 2 Decision: Distinguish (a i, b i ) from (a i, u i ) where u i is uniform in R q. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
40 LWE over Rings Let R = Z[X]/(X n + 1), and R q = R/qR. Operations in R q are very efficient using algorithms similar to FFT. Search: Find secret s R q given a 1 R q, b 1 = a 1 s + e 1 a 2 R q, b 2 = a 2 s + e 2 Decision: Distinguish (a i, b i ) from (a i, u i ) where u i is uniform in R q. Worst case to Average Case [LPR10, PRS17] Decision R-LWE = Search R-LWE = ApproxSVP poly(n) on ideal lattices Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
41 Complexity of SVP on Ideal Lattices We know that if we can solve R-LWE, then we can also solve SVP on ideal lattices. The other direction is unknown. There has been some recent progress[cdpr16, BS16, K16, CDW16] giving an efficient quantum algorithm for 2 O( n log n) approximation of SVP on Ideal Lattices. This does not say anything about the hardness of Ring-LWE. There is more algebraic structure in Ring-LWE that can possibly lead to quantum attacks, but so far there has been little success. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
42 Complexity of SVP on Ideal Lattices We know that if we can solve R-LWE, then we can also solve SVP on ideal lattices. The other direction is unknown. There has been some recent progress[cdpr16, BS16, K16, CDW16] giving an efficient quantum algorithm for 2 O( n log n) approximation of SVP on Ideal Lattices. This does not say anything about the hardness of Ring-LWE. There is more algebraic structure in Ring-LWE that can possibly lead to quantum attacks, but so far there has been little success. Ring-LWE based crypto is more efficient, but perhaps less secure. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
43 Talk Outline GGH Public Key Encryption Scheme LWE Problem and Applications Efficiency from Rings Recent Implementations. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
44 Recent Implementations. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
45 Key Exchange [BCNS15] Ring-LWE based key exchange. NewHope [ADPS 15]: Optimized Ring-LWE key exchange with λ = 200 bit quantum security. Comparable to or even faster than current ECDH with 128-bit classical security. Google has experimentally deployed NewHope + ECDH. Frodo [BCDMNNRS 16]: Plain-LWE key exchange with some optimizations. Conjectures 128-bit quantum security. About 10 times slower than NewHope, but almost as fast as ECDH (and much faster than RSA). NTRU EES743EP1 [WEJ13]. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
46 Other Implementations BLISS: [DDLL 13] An efficient digital signature scheme based on [Lyu09,Lyu12] DILITHIUM: [DLLSSS17] Another efficient digital signature based on [GLP12] that eliminates some of the vulnerabilities of BLISS. HELib: [HaleviShoup] Implementation of Fully Homomorphic Encryption. Λ λ: [CroPei 16] A high level framework aimed at advanced lattice cryptosystems. Lots of ongoing work including many proposals of new post-quantum crypto schemes submitted to NIST. Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
47 Questions? Divesh Aggarwal (CQT) Lattice-based Cryptography February 8, / 30
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Μηχανική Μάθηση Hypothesis Testing
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Abstract Storage Devices
 Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική»
 Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
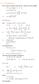 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Problem Set 3: Solutions
 CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
Models for Probabilistic Programs with an Adversary
 Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Solutions to Exercise Sheet 5
 Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
New bounds for spherical two-distance sets and equiangular lines
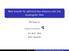 New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
Srednicki Chapter 55
 Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ
 ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ ΕΛΕΝΑ ΦΛΟΚΑ Επίκουρος Καθηγήτρια Τµήµα Φυσικής, Τοµέας Φυσικής Περιβάλλοντος- Μετεωρολογίας ΓΕΝΙΚΟΙ ΟΡΙΣΜΟΙ Πληθυσµός Σύνολο ατόµων ή αντικειµένων στα οποία αναφέρονται
ΕΙΣΑΓΩΓΗ ΣΤΗ ΣΤΑΤΙΣΤΙΚΗ ΑΝΑΛΥΣΗ ΕΛΕΝΑ ΦΛΟΚΑ Επίκουρος Καθηγήτρια Τµήµα Φυσικής, Τοµέας Φυσικής Περιβάλλοντος- Μετεωρολογίας ΓΕΝΙΚΟΙ ΟΡΙΣΜΟΙ Πληθυσµός Σύνολο ατόµων ή αντικειµένων στα οποία αναφέρονται
Access Control Encryption Enforcing Information Flow with Cryptography
 Access Control Encryption Enforcing Information Flow with Cryptography Ivan Damgård, Helene Haagh, and Claudio Orlandi http://eprint.iacr.org/2016/106 Outline Access Control Encryption Motivation Definition
Access Control Encryption Enforcing Information Flow with Cryptography Ivan Damgård, Helene Haagh, and Claudio Orlandi http://eprint.iacr.org/2016/106 Outline Access Control Encryption Motivation Definition
Numerical Analysis FMN011
 Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Partial Differential Equations in Biology The boundary element method. March 26, 2013
 The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
Lecture 15 - Root System Axiomatics
 Lecture 15 - Root System Axiomatics Nov 1, 01 In this lecture we examine root systems from an axiomatic point of view. 1 Reflections If v R n, then it determines a hyperplane, denoted P v, through the
Lecture 15 - Root System Axiomatics Nov 1, 01 In this lecture we examine root systems from an axiomatic point of view. 1 Reflections If v R n, then it determines a hyperplane, denoted P v, through the
Bayesian statistics. DS GA 1002 Probability and Statistics for Data Science.
 Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3
 Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
Practice Exam 2. Conceptual Questions. 1. State a Basic identity and then verify it. (a) Identity: Solution: One identity is csc(θ) = 1
 Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
Exercises to Statistics of Material Fatigue No. 5
 Prof. Dr. Christine Müller Dipl.-Math. Christoph Kustosz Eercises to Statistics of Material Fatigue No. 5 E. 9 (5 a Show, that a Fisher information matri for a two dimensional parameter θ (θ,θ 2 R 2, can
Prof. Dr. Christine Müller Dipl.-Math. Christoph Kustosz Eercises to Statistics of Material Fatigue No. 5 E. 9 (5 a Show, that a Fisher information matri for a two dimensional parameter θ (θ,θ 2 R 2, can
Section 7.6 Double and Half Angle Formulas
 09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Elements of Information Theory
 Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
Elements of Information Theory Model of Digital Communications System A Logarithmic Measure for Information Mutual Information Units of Information Self-Information News... Example Information Measure
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Reminders: linear functions
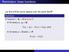 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2)
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2) Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness (2) x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 11 13 21
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness (2) Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness (2) x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 11 13 21
CRASH COURSE IN PRECALCULUS
 CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
CRASH COURSE IN PRECALCULUS Shiah-Sen Wang The graphs are prepared by Chien-Lun Lai Based on : Precalculus: Mathematics for Calculus by J. Stuwart, L. Redin & S. Watson, 6th edition, 01, Brooks/Cole Chapter
ω ω ω ω ω ω+2 ω ω+2 + ω ω ω ω+2 + ω ω+1 ω ω+2 2 ω ω ω ω ω ω ω ω+1 ω ω2 ω ω2 + ω ω ω2 + ω ω ω ω2 + ω ω+1 ω ω2 + ω ω+1 + ω ω ω ω2 + ω
 0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
Απόκριση σε Μοναδιαία Ωστική Δύναμη (Unit Impulse) Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο. Απόστολος Σ.
 Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
w o = R 1 p. (1) R = p =. = 1
 Πανεπιστήµιο Κρήτης - Τµήµα Επιστήµης Υπολογιστών ΗΥ-570: Στατιστική Επεξεργασία Σήµατος 205 ιδάσκων : Α. Μουχτάρης Τριτη Σειρά Ασκήσεων Λύσεις Ασκηση 3. 5.2 (a) From the Wiener-Hopf equation we have:
Πανεπιστήµιο Κρήτης - Τµήµα Επιστήµης Υπολογιστών ΗΥ-570: Στατιστική Επεξεργασία Σήµατος 205 ιδάσκων : Α. Μουχτάρης Τριτη Σειρά Ασκήσεων Λύσεις Ασκηση 3. 5.2 (a) From the Wiener-Hopf equation we have:
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
9.09. # 1. Area inside the oval limaçon r = cos θ. To graph, start with θ = 0 so r = 6. Compute dr
 9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
SCHOOL OF MATHEMATICAL SCIENCES G11LMA Linear Mathematics Examination Solutions
 SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
Space-Time Symmetries
 Chapter Space-Time Symmetries In classical fiel theory any continuous symmetry of the action generates a conserve current by Noether's proceure. If the Lagrangian is not invariant but only shifts by a
Chapter Space-Time Symmetries In classical fiel theory any continuous symmetry of the action generates a conserve current by Noether's proceure. If the Lagrangian is not invariant but only shifts by a
LESSON 14 (ΜΑΘΗΜΑ ΔΕΚΑΤΕΣΣΕΡΑ) REF : 202/057/34-ADV. 18 February 2014
 LESSON 14 (ΜΑΘΗΜΑ ΔΕΚΑΤΕΣΣΕΡΑ) REF : 202/057/34-ADV 18 February 2014 Slowly/quietly Clear/clearly Clean Quickly/quick/fast Hurry (in a hurry) Driver Attention/caution/notice/care Dance Σιγά Καθαρά Καθαρός/η/ο
LESSON 14 (ΜΑΘΗΜΑ ΔΕΚΑΤΕΣΣΕΡΑ) REF : 202/057/34-ADV 18 February 2014 Slowly/quietly Clear/clearly Clean Quickly/quick/fast Hurry (in a hurry) Driver Attention/caution/notice/care Dance Σιγά Καθαρά Καθαρός/η/ο
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Homework 8 Model Solution Section
 MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
Lecture 34 Bootstrap confidence intervals
 Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
Math221: HW# 1 solutions
 Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM
 SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr (T t N n) Pr (max (X 1,..., X N ) t N n) Pr (max
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr (T t N n) Pr (max (X 1,..., X N ) t N n) Pr (max
6.003: Signals and Systems. Modulation
 6.003: Signals and Systems Modulation May 6, 200 Communications Systems Signals are not always well matched to the media through which we wish to transmit them. signal audio video internet applications
6.003: Signals and Systems Modulation May 6, 200 Communications Systems Signals are not always well matched to the media through which we wish to transmit them. signal audio video internet applications
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ ΤΣΗΜΑΣΟ ΨΗΦΙΑΚΗ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ
 ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
ΕΘΝΙΚΟ ΜΕΣΟΒΙΟ ΠΟΛΤΣΕΧΝΕΙΟ ΣΜΗΜΑ ΑΓΡΟΝΟΜΩΝ-ΣΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΣΟΜΕΑ ΣΟΠΟΓΡΑΦΙΑ ΕΡΓΑΣΗΡΙΟ ΦΩΣΟΓΡΑΜΜΕΣΡΙΑ ΓΕΩΜΕΣΡΙΚΗ ΣΕΚΜΗΡΙΩΗ ΣΟΤ ΙΕΡΟΤ ΝΑΟΤ ΣΟΤ ΣΙΜΙΟΤ ΣΑΤΡΟΤ ΣΟ ΠΕΛΕΝΔΡΙ ΣΗ ΚΤΠΡΟΤ ΜΕ ΕΦΑΡΜΟΓΗ ΑΤΣΟΜΑΣΟΠΟΙΗΜΕΝΟΤ
Estimation for ARMA Processes with Stable Noise. Matt Calder & Richard A. Davis Colorado State University
 Estimation for ARMA Processes with Stable Noise Matt Calder & Richard A. Davis Colorado State University rdavis@stat.colostate.edu 1 ARMA processes with stable noise Review of M-estimation Examples of
Estimation for ARMA Processes with Stable Noise Matt Calder & Richard A. Davis Colorado State University rdavis@stat.colostate.edu 1 ARMA processes with stable noise Review of M-estimation Examples of
Overview. Transition Semantics. Configurations and the transition relation. Executions and computation
 Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Γιπλυμαηική Δπγαζία. «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ. Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο
 ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
Notes on the Open Economy
 Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 24/3/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Όλοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα μικρότεροι του 10000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Αν κάπου κάνετε κάποιες υποθέσεις
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Fourier Series. MATH 211, Calculus II. J. Robert Buchanan. Spring Department of Mathematics
 Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ
 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΤΜΗΜΑ ΝΟΣΗΛΕΥΤΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΨΥΧΟΛΟΓΙΚΕΣ ΕΠΙΠΤΩΣΕΙΣ ΣΕ ΓΥΝΑΙΚΕΣ ΜΕΤΑ ΑΠΟ ΜΑΣΤΕΚΤΟΜΗ ΓΕΩΡΓΙΑ ΤΡΙΣΟΚΚΑ Λευκωσία 2012 ΤΕΧΝΟΛΟΓΙΚΟ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΥΠΡΟΥ ΣΧΟΛΗ ΕΠΙΣΤΗΜΩΝ
Local Approximation with Kernels
 Local Approximation with Kernels Thomas Hangelbroek University of Hawaii at Manoa 5th International Conference Approximation Theory, 26 work supported by: NSF DMS-43726 A cubic spline example Consider
Local Approximation with Kernels Thomas Hangelbroek University of Hawaii at Manoa 5th International Conference Approximation Theory, 26 work supported by: NSF DMS-43726 A cubic spline example Consider
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Αλγόριθμοι και πολυπλοκότητα NP-Completeness
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness x x x 2 x 2 x 3 x 3 x 4 x 4 2 22 32 3 2 23 3 33 NP-Completeness
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Αλγόριθμοι και πολυπλοκότητα NP-Completeness Ιωάννης Τόλλης Τμήμα Επιστήμης Υπολογιστών NP-Completeness x x x 2 x 2 x 3 x 3 x 4 x 4 2 22 32 3 2 23 3 33 NP-Completeness
Exercises 10. Find a fundamental matrix of the given system of equations. Also find the fundamental matrix Φ(t) satisfying Φ(0) = I. 1.
 Exercises 0 More exercises are available in Elementary Differential Equations. If you have a problem to solve any of them, feel free to come to office hour. Problem Find a fundamental matrix of the given
Exercises 0 More exercises are available in Elementary Differential Equations. If you have a problem to solve any of them, feel free to come to office hour. Problem Find a fundamental matrix of the given
Advanced Subsidiary Unit 1: Understanding and Written Response
 Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
( ) 2 and compare to M.
 Problems and Solutions for Section 4.2 4.9 through 4.33) 4.9 Calculate the square root of the matrix 3!0 M!0 8 Hint: Let M / 2 a!b ; calculate M / 2!b c ) 2 and compare to M. Solution: Given: 3!0 M!0 8
Problems and Solutions for Section 4.2 4.9 through 4.33) 4.9 Calculate the square root of the matrix 3!0 M!0 8 Hint: Let M / 2 a!b ; calculate M / 2!b c ) 2 and compare to M. Solution: Given: 3!0 M!0 8
Πώς μπορεί κανείς να έχει έναν διερμηνέα κατά την επίσκεψή του στον Οικογενειακό του Γιατρό στο Ίσλινγκτον Getting an interpreter when you visit your
 Πώς μπορεί κανείς να έχει έναν διερμηνέα κατά την επίσκεψή του στον Οικογενειακό του Γιατρό στο Ίσλινγκτον Getting an interpreter when you visit your GP practice in Islington Σε όλα τα Ιατρεία Οικογενειακού
Πώς μπορεί κανείς να έχει έναν διερμηνέα κατά την επίσκεψή του στον Οικογενειακό του Γιατρό στο Ίσλινγκτον Getting an interpreter when you visit your GP practice in Islington Σε όλα τα Ιατρεία Οικογενειακού
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM
 SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr T t N n) Pr max X 1,..., X N ) t N n) Pr max
SOLUTIONS TO MATH38181 EXTREME VALUES AND FINANCIAL RISK EXAM Solutions to Question 1 a) The cumulative distribution function of T conditional on N n is Pr T t N n) Pr max X 1,..., X N ) t N n) Pr max
(C) 2010 Pearson Education, Inc. All rights reserved.
 Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Connectionless transmission with datagrams. Connection-oriented transmission is like the telephone system You dial and are given a connection to the telephone of fthe person with whom you wish to communicate.
Second Order Partial Differential Equations
 Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Right Rear Door. Let's now finish the door hinge saga with the right rear door
 Right Rear Door Let's now finish the door hinge saga with the right rear door You may have been already guessed my steps, so there is not much to describe in detail. Old upper one file:///c /Documents
Right Rear Door Let's now finish the door hinge saga with the right rear door You may have been already guessed my steps, so there is not much to describe in detail. Old upper one file:///c /Documents
A Note on Intuitionistic Fuzzy. Equivalence Relation
 International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΒΑΛΕΝΤΙΝΑ ΠΑΠΑΔΟΠΟΥΛΟΥ Α.Μ.: 09/061. Υπεύθυνος Καθηγητής: Σάββας Μακρίδης
 Α.Τ.Ε.Ι. ΙΟΝΙΩΝ ΝΗΣΩΝ ΠΑΡΑΡΤΗΜΑ ΑΡΓΟΣΤΟΛΙΟΥ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ ΚΑΙ ΕΠΙΚΟΙΝΩΝΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Η διαμόρφωση επικοινωνιακής στρατηγικής (και των τακτικών ενεργειών) για την ενδυνάμωση της εταιρικής
Α.Τ.Ε.Ι. ΙΟΝΙΩΝ ΝΗΣΩΝ ΠΑΡΑΡΤΗΜΑ ΑΡΓΟΣΤΟΛΙΟΥ ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ ΚΑΙ ΕΠΙΚΟΙΝΩΝΙΑΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ «Η διαμόρφωση επικοινωνιακής στρατηγικής (και των τακτικών ενεργειών) για την ενδυνάμωση της εταιρικής
Fractional Colorings and Zykov Products of graphs
 Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Example of the Baum-Welch Algorithm
 Example of the Baum-Welch Algorithm Larry Moss Q520, Spring 2008 1 Our corpus c We start with a very simple corpus. We take the set Y of unanalyzed words to be {ABBA, BAB}, and c to be given by c(abba)
Example of the Baum-Welch Algorithm Larry Moss Q520, Spring 2008 1 Our corpus c We start with a very simple corpus. We take the set Y of unanalyzed words to be {ABBA, BAB}, and c to be given by c(abba)
