Real Solving on Algebraic Systems of Small Dimension
|
|
|
- Στράτων Καψής
- 6 χρόνια πριν
- Προβολές:
Transcript
1 Εθνικο και Καποδιστριακο Πανεπιστημιο Αθηνων Σχολη Θετικων Επιστημων ΜΠΛΑ Προγραμμα Μεταπτυχιακων Σπουδων Διπλωματική Εργασία: Real Solving on Algebraic Systems of Small Dimension Φοιτητής Διώχνος Δημήτρης Αριθμός Μητρώου: Επιβλέπων Καθηγητής Ιωάννης Εμίρης Αθήνα Ιούνιος 2007
2
3
4
5 Στην οικογένειά μου
6 Ευχαριστίες Είμαι πολύ χαρούμενος που είχα την τιμή να συνεργαστώ με τον καθηγητή κ.γιάννηεμίρηγιατηδιπλωματικήμουεργασίαστο µ λ. Ταμαθήματάτου καθώς επίσης και οι παρατηρήσεις του στις κατ³ιδίαν συζητήσεις που είχαμε, είτε αυτές αναφέρονταν αποκλειστικά στη πεδίο της διπλωματικής μου είτε όχι, ήταν πάντοτε μια πηγή έμπνευσης και πρόσφεραν χώρο για δημιουργική δουλειά. Επιπλέον, ο χαρακτήρας του θα είναι πάντοτε πρότυπο για εμένα. Δουλεύοντας δίπλα του έμαθα πως μπορεί κανείς να ασχολείται εντατικά με διάφορα προβλήματα και να διαχειρίζεται κρίσεις χωρίς όμως να παραγκωνίζει και την προσωπική του ζωή.τολίγοτεροπουμπορώνακάνωείναινατονευχαριστήσωγιακάθεστιγμή συνεργασίας μας. Επίσης οι καθηγητές κύριοι Ηλίας Κουτσουπιάς και Ευάγγελος Ράπτης μου έκαναν την τιμή να είναι στην τριμελή επιτροπή μου και τους ευχαριστώ θερμά γι³αυτό. Καιοιδύο,κυρίωςμέσααπόταμαθήματάτους,μουπρόσφερανμετις συζητήσεις τους μια νέα προοπτική σε θέματα αλγορίθμων και άλγεβρας αντίστοιχα.σίγουραηκατανόησηδιαφόρωνεννοιώνδενθαήταντοίδιοεύκοληχωρίςτη συμβολή και των δύο. Ακόμη, δεν μπορώ παρά να πω ένα μεγάλο ευχαριστώ και στον Ηλία Τσιγαρίδα. Ο Ηλίας τελείωνε το διδακτορικό του την εποχή που ξεκινούσα τη διπλωματική μουσεέναθέματοοποίοστηνουσίαβασιζότανσεέναμεγάλομέροςστηδουλειά πουείχεκάνειοίδιοςέωςτότε.οισυζητήσειςμαςήτανπάντοτεέναανεκτίμητο κράμα μαθηματικών και προγραμματισμού αφού το πάθος του για την ομορφιά που βρίσκεται πίσω από τις εξίσωσεις καθώς επίσης και η δινή προγραμματιστική του εμπειρία μας έφερνε πάντοτε να ασχολούμαστε με την καρδιά των προβλημάτων που αντιμετωπίσαμε. Δίχως τη βοήθεια του Ηλία είναι αμφίβολο αν η διπλωματική μουθαείχετηνίδιαμορφή. ΦυσικάδενμπορώναπαραλείψωκαιτηνπαρέατόσοτουΗλίαόσοκαιτων υπολοίπων παιδιών στο γραφείο. Δεν είναι λίγες οι φορές που χρειάστηκε να δουλέψουμεωςαργάτηνύχταστησχολήκαιηπαρέατουςαλλάκαιοιπαρεμφερείς ανησυχίες τους βοηθούσαν να ξεπεραστούν πιο εύκολα τα όποια εμπόδια αντιμετωπίζαμε. Θέλω λοιπόν να πω κι ένα ευχαριστώ στους Χρήστο Κοναξή και Γιώργο Τζούμα. Τέλος θα ήθελα να ευχαριστήσω θερμά και τους καθηγητές μου κυρίους Γιάννη Μοσχοβάκη και Κώστα Δημητρακόπουλο που μου έδωσαν την ευκαιρία να φοιτήσωστο µ λ.μέσααπόταμαθήματατωνίδιωναλλάκαιτωνυπολοίπων συναδέλφωντουςστο µ λ είχατηνευκαιρίαναγνωρίσωμιαπιομαθηματική πλευρά της πληροφορικής την οποία δύσκολα πιστεύω πως θα μπορούσα να βρω σε οποιοδήποτε άλλο μεταπτυχιακό πρόγραμμα στην Ελλάδα. Τους είμαι πραγματικά ευγνώμων. Δημήτρης Διώχνος, Αθήνα, ½ Ιουνίου ¾¼¼ º
7 Περίληψη Η παρούσα διπλωματική ασχολείται με την ακριβή(exact) επίλυση στους πραγματικούς αριθμούς, καλώς ορισμένων πολυωνυμικών συστημάτων. Το κύριο πρόβλημα είναι η εύρεση όλων των πραγματικών λύσεων του συστήματος και ο υπολογισμός των πολλαπλοτήτων στα σημεία τομής. Για το σκοπό αυτό παρουσιάζονται τρεις αλγόριθμοι και αναλύεται η δυαδική πολυπλοκότητά τους. Οι δύο από τους τρειςαλγορίθμουςεπιτυγχάνουνέναφράγμα ÕB(N ½¾ ) [DET07a, DET07b],ξεχνώντας λογαριθμικούς παράγοντες, ενώ το προηγούμενο καλύτερο φράγμα ήταν Õ B (N ½ ),όπουτο Nφράσσειτοβαθμόκαιτοδυαδικόμήκοςτωνσυντελεστών των πολυωνύμων εισόδου. Η έξοδος των αλγορίθμων είναι οι ακριβείς συντεταγμένες των σημείων τομής, δηλαδή διατεταγμένα ζεύγη πραγματικών αλγεβρικών αριθμών και δίνονται υπό μορφή διαστημάτων απομόνωσης(isolating interval representation). Το κύριο εργαλείο είναι οι ακολουθίες υποαπαλοιφουσών(subresultants) και Sturm-Habicht, οι οποίες εξετάζονται σε πολλές μεταβλητές μέσω της τεχνικής της δυαδικής κατάτμησης. Για την επίτευξη των φραγμάτων χρησιμοποιούνται πρόσφατα αποτελέσματα πολυπλοκότητας στην απομόνωση των ριζών πολυωνύμων μιας μεταβλητής. Ακόμη παρουσιάζεται νέο φράγμα στον υπολογισμό προσήμου πολυωνύμου σε δύο μεταβλητές. Επίσης, οι αλγόριθμοι επίλυσης σε δύο μεταβλητές εφαρμόζονται και για τον υπολογισμό της τοπολογίας μιας πραγματικής αλγεβρικής καμπύλης. Τέλος, όλοι οι αλγόριθμοι έχουν υλοποιηθεί στο maple με πολύ ενθαρρυντικά αποτελέσματα. Η υλοποίηση χρησιμοποιεί αριθμητικά φίλτρα προκειμένου να επιταχύνονται οι υπολογισμοί όταν οι ρίζες είναι καλά διαχωρισμένες. Η δυναμική της βιβλιοθήκης παρουσιάζεται με τη βοήθεια πειραμάτων συγκριτικά με άλλες ευρέως διαδεδομένες βιβλιοθήκες όπως είναι το fgb/rs, τρεις αλγόριθμοι της synaps (sturm, subdiv και newmac), και δύο ελαφρά αλλαγμένες μορφές των insulate και top τα οποία υπολογίζουν την τοπολογία μιας πραγματικής αλγεβρικής καμπύλης.
8 Abstract This thesis is concerned with exact real solving of well-constrained, bivariate algebraic systems. The main problem is to isolate all real solutions of the system and determine their intersection multiplicities. Three projection-based algorithms are presented and their asymptotic bit complexity is analyzed. This leads to a bound of ÕB(N ½¾ ) [DET07a, DET07b], when ignoring polylogarithmic factors, whereas the previous record bound was in ÕB(N ½ ), where N bounds the degree and the bitsize of the input polynomials. The output of the solvers are pairs of real algebraic numbers in isolating interval representation. The main tool is Sturm-Habicht and subresultant remainder sequences, extended to several variables by the technique of binary segmentation. In order to achieve the bounds, recent advances on the complexity of univariate root isolation are exploited. New bound for the sign evaluation of bivariate polynomials over a pair of real algebraic numbers is also presented. Moreover, the algorithms for bivariate real solving are applied to compute the topology of real plane algebraic curves. Lastly, all algorithms have been implemented in maple with very encouraging results. The implementation uses numeric filtering to speed up computation when the roots are well-separated. We illustrate it by experiments against well-established libraries such as fgb/rs, synaps solvers (sturm, subdiv, and newmac), and modified versions of insulate and top which compute the topology of real plane algebraic curves.
9 Contents 1 Introduction Previous Work Contributions Outline Foundations Notation and Basic Complexity Results Evaluation at a point x ¼ Z using Horner s rule Pseudo-Division and Pseudo-Remainder Greatest Common Divisor Resultant Discriminant Mahler Bound Classical Fan-In / Fan-Out Representing Real Algebraic Numbers Polynomial Remainder Sequences Signed Polynomial Remainder Sequences Univariate Polynomials Bounding Roots Root Isolation and Sturm s algorithm Univariate sign determination Bounding root separation Multivariate polynomials Bivariate sign evaluation Real Solving of Bivariate Systems The grid algorithm Deterministic shear and counting multiplicities The m_rur algorithm Projection The sub-algorithm compute_k Matching solutions and algorithm find The g_rur algorithm Applications Real root counting
10 2 CONTENTS Simultaneous inequalities in two variables The complexity of topology Implementation and Experiments Augmenting performance Bivariate solving and slv library Comparing slv solvers Decomposing running times The effect of filtering Bivariate solving and other packages g_rur and other solvers Computing multiplicities Comparing slv solvers Decomposing running times The effect of filtering Conclusion Future Work A Test-Bed Polynomials 73 A.1 Input Polynomials B Sample Usage 77
11 List of Tables 4.1 Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM The performance of grid and g_rur implementations on bivariate solving and the speedup that is achieved when choosing g_rur The performance of m_rur and g_rur implementations on bivariate solving and the speedup that is achieved when choosing g_rur Statistics on the performance of slv s algorithms in bivariate solving Analyzing the percent of time required for various procedures in each algorithm. Values in m_rur refer to sheared systems (whenever it was necessary). A column about Sorting in the case of grid and g_rur is not shown Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM The performance of fgb/rs and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur The performance of synaps/sturm and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur The performance of synaps/subdiv and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur The performance of synaps/newmac and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur The performance of insulate and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur The performance of top with precision set to ¼ digits and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur
12 4 LIST OF TABLES 4.15 The performance of top with precision set to ¼¼ digits and g_rur on bivariate solving and the speedup that is achieved when choosing g_rur Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM The performance of grid and g_rur implementations when computing multiplicities on the intersections and the speedup that is achieved when choosing g_rur The performance of m_rur and g_rur implementations when computing multiplicities on the intersections and the speedup that is achieved when choosing g_rur The performance of grid and m_rur implementations when computing multiplicities on the intersections and the speedup that is achieved when choosing m_rur Statistics on the performance of slv s algorithms when computing multiplicities Analyzing the percent of time required for various procedures in each algorithm. All values refer to the sheared systems (whenever it was necessary). A column about Sorting in the case of grid and g_rur is not shown Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM Performance averages over 10 runs in maple º on a ¾GHz AMD64@3K+ processor with ½GB RAM
13 List of Algorithms 1 Sturm::univariate univariate-sign_at bivariate-sign_at Sturm::grid Sturm::m_rur Sturm::g_rur
14 6 LIST OF ALGORITHMS
15 Chapter 1 Introduction The problem of well-constrained algebraic system solving is fundamental. However, most of the algorithms treat the general case or consider solutions over an algebraically closed field [Can87, LL91, Emi95, EV99, Mou96, MP97, MP98, Mou99]. This thesis is based on the results presented in [DET07a, DET07b] and focuses on real solving in the bivariate case in order to provide precise complexity bounds and study different algorithms in practice. The work can be considered as an extension to the bivariate solvers presented in [Tsi06]. The idea is that if someone treats specific cases on their own it is possible to obtain better bounds than those provided in the general case. This is important in several applications ranging from nonlinear computational geometry and computer-aided geometric design to real quantifier elimination and robotics. A question of independent interest is to compute the topology of a plane real algebraic curve, which is also studied in this thesis. The algorithms isolate all common real roots inside non-overlapping rational rectangles, and determine the intersection multiplicity per root. The output is pairs of real algebraic numbers. Three projection-based algorithms are presented and their asymptotic bit complexity is analyzed. Similarly to other works, O B means bit complexity and Õ ÕB means that we are ignoring polylogarithmic factors. This leads to a bound of ÕB(N ½¾ ), whereas the previous record bound was ÕB(N ½ ) [GVEK96, BPM06], derived from the closely related problem of computing the topology of real plane algebraic curves, where N bounds the degree and the bitsize of the input polynomials. The approach in [GVEK96] depends on Thom s encoding for representing the real roots of a univariate polynomial. Real algebraic numbers in this thesis are represented in isolating interval representation, since it is more intuitive, it is used in applications, and the preliminary experiments that were conducted in this thesis (see also [DET07a, DET07b]) demonstrate that it supports as efficient algorithms as other representations. In [GVEK96] it is stated that isolating intervals provide worst [sic] bounds. Moreover, it is widely believed that isolating intervals do not produce good theoretical results. [DET07a, DET07b] suggest that isolating intervals should be re-evaluated. The main tool is Sturm-Habicht and subresultant remainder sequences, ex- 7
16 8 INTRODUCTION tended to several variables by the technique of binary segmentation. Recent breakthroughs on univariate root isolation are exploited. These have reduced complexity by ½- orders of magnitude to ÕB(N ) [DSY05, ESY06, EMT07]. Note that the complexity that is achieved by numerical methods [Pan02] is Õ B (N ) and hence the gap between the two approaches has narrowed. Hence, new bounds are derived for the sign evaluation of bivariate polynomials over two real algebraic numbers. 1.1 Previous Work In [KSP05], ¾ ¾ systems are solved and the multiplicities computed under the assumption that a generic shear has been obtained, based on [SF90]. In [Wol02], ¾ ¾ systems of bounded degree were studied, obtained as projections of the arrangement of D quadrics. This algorithm is a precursor of ours, see also [ET05], except that matching and multiplicity computation was simpler. In [MP05], a subdivision algorithm is proposed, exploiting the properties of the Bernstein basis, with unknown bit complexity, and arithmetic complexity based on the characteristics of the graphs of the polynomials. For other approaches based on multivariate Sturm sequences the reader may refer to e.g. [Mil92, PRS93]. Determining the topology of a real algebraic plane curve is a closely related problem. The best bound is ÕB(N ½ ) [BPM06, GVEK96]. In [WS05] three projections are used; this is implemented in insulate, with which we make several comparisons. Work in [EKW07] is based on Sturm-Habicht sequences and solves the problem of singularities and vertical asymptotes with the Bitstream Descartes method [EKK + 05]. For an alternative using Gröbner bases the reader may refer to [CFPR06]. To the best of our knowledge the only result in topology determination using isolating intervals is [AM88], where a ÕB(N ¼ ) bound is proved. We establish a bound of ÕB(N ½¾ ) using the isolating interval representation. It seems that the complexity in [GVEK96] could be improved to ÕB(N ½¼ ) using fast multiplication algorithms, fast algorithms for computations of signed subresultant sequences and improved bounds for the bitsize of the integers appearing in computations. To put the bounds that are presented in this thesis and [DET07a, DET07b] into perspective, note that the input is O B (N ), and the bitsize of all output isolation points for univariate solving is ÕB(N ¾ ), and this is tight. 1.2 Contributions The main contributions of [DET07a, DET07b] and this thesis are the following: An improved complexity bound for bivariate sign evaluation (theorem 2.37) is established, which helps us derive bounds for root counting in an extension field (lemma 3.7) and for the problem of simultaneous inequalities (corollary 3.10). We study the complexity of bivariate polynomial real solving, using
17 1.3 OUTLINE 9 three projection-based algorithms: a straightforward grid method (theorem 3.1), a specialized RUR approach (theorem 3.5), and an improvement of the latter using fast GCD (theorem 3.6). The first two algorithms also appeared in [Tsi06]. The best bound is ÕB(N ½¾ ); within this bound, root multiplicities are computed as well. Computing the topology of a real plane algebraic curve is in ÕB(N ½¾ ) (theorem 3.12). Moreover, a maple package has been developed which allows computations with real algebraic numbers and for implementing our algorithms presented also in [DET07a, DET07b]. It is easy to use and it integrates seminumerical filtering to speed up computations when the roots are well-separated. It guarantees exactness and completeness of results; moreover, the runtimes seem very encouraging. We illustrate it by experiments against well-established C/C++ libraries fgb/rs and synaps. We also examine maple libraries insulate and top, which compute curve topology. Our software is robust and effective; its runtime is within a small constant factor with respect to the fastest C/C++ library. 1.3 Outline The thesis is divided as follows. Chapter 2 presents basic tools and complexity results in univariate solving and on operations of Sturm sequences. Having formed a solid background chapter 3 presents the three projection based algorithms that are also presented in [DET07a, DET07b]. Chapter 4 presents extensive experiments that were conducted with the library that was developed in this thesis. Chapter 5 summarizes the most important results and states the goals for future work with Sturm sequences and projection based solvers. Chapter A in the appendix presents the polynomials that were used for testing. Finally, chapter B in the appendix gives an overview of the commands that are provided through the library at the moment. Sample executions of the basic commands are shown and the output is explained. For an up-to-date coverage of the commands available for the library bundled with sample execution and explanation of each command, the reader is urged to visit the homepage of the slv (Sturm solver) library:
18 10 INTRODUCTION
19 Chapter 2 Foundations This chapter is devoted to basic tools and complexity results that will be used by the three algorithms for real solving bivariate systems in chapter 3. The heart of the algorithms relies on Sturm sequences. Therefore most of the results of this chapter deal with or are based on sequences generation and evaluation on rational points. Moreover, Fan-In / Fan-Out techniques are described in section for completeness, although they are not applied in bivariate solving since at the moment seem not to yield better bounds there. 2.1 Notation and Basic Complexity Results This section sets the necessary notation and covers basic complexity results mainly on primitive operations with univariate polynomials. In what follows O B means bit complexity and the ÕB-notation means that we are ignoring polylogarithmic factors. For f Z[y ½ º º º, y k x], deg(f) denotes its total degree, while x (f) denotes its degree if we consider it as a univariate polynomial with respect to x. L(f) bounds the bitsize of the coefficients of f (including a bit for the sign). We assume L(deg(f)) = O(L(f)). For a Q, L(a) is the maximum bitsize of numerator and denominator. Let M (τ) denote the bit complexity of multiplying two integers of bit size at most τ and M (d τ) denote the bit complexity of multiplying two univariate polynomials of degrees d and coefficient bit size τ. Using FFT, M (τ) = O B (τ Ð c ½ τ), M (d τ) = O B (dτ Ð c ¾ (dτ)) = ÕB(dτ), for suitable constants c ½ c ¾. Let f g Z[x], deg(f) = p q = deg(g) and L(f) L(g) τ. rem (f g) and quo(f g) denote the Euclidean remainder and quotient, respectively. We compute f ½ ÑÓ f ¾ in ÕB(d(δτ ¾ + τ ½ )), where d deg(f i ) δ = deg(f ½ ) deg(f ¾ ) L(f i ) = τ i Evaluation at a point x ¼ Z using Horner s rule Given f = d i=½ c ix i such that L(c i ) τ and x ¼ N such that L(x ¼ ) = σ we can perform the evaluation with Horner s rule by applying only d multiplications 11
20 12 FOUNDATIONS plus d + ½ additions, since Horner s rule implies c ¼ + x ¼ (c ½ + x ¼ (º º º (c d ½ + x ¼ c d ) º º º))º More formally, the evaluation Eval Horner (f x ¼ ) can be described with the following recursive equations: Eval Horner (f x ¼ ) = h(f d + ½ x ¼ ) h(f i + ½ x ¼ ) = c d i + x ¼ h(f i x ¼ ) h(f ¼ x ¼ ) = The running time is asymptotically bounded by the d multiplications, hence it is ÕB(d Ñ Ü{dσ τ})º The bitsize of the result is L(f(x ¼ )) = O(dσ + τ)º c d Pseudo-Division and Pseudo-Remainder In cases where the coefficients of the polynomials do not belong to a field, then classical division has to be redefined. This redefinition is the following: Definition 2.1. Let f g Z[x]º There exist unique polynomials Q R Z[x] such that lead(g) δ ½ f = Qg + R and deg(r) < deg(g) and δ = Ñ Ü{½ deg(f) deg(g)}º Q and R are called pseudo-quotient and pseudo-remainder respectively. Q is denoted as pquo and R as prem. Note that for simplicity in the above definition f g Z[x]º However, the definition still applies for f g K[x] for any commutative ring K. Lemma 2.2. Let f g Z[x] such that deg(f) = m n = deg(g) and L(f) = σ L(g) = τ. Then L(prem (f g)) = L(pquo(f g)) = Õ(δτ + σ), where δ = m n. Proof. Let f = m i=¼ a ix i and g = n i=¼ b ix i and consider M = b n b n ½ º º º b ¼ b n º º º b ½ b ¼ b n b n ½ º º º b ½ b ¼ a m a m ½ º º º a m n a m n ½ º º º a ½ a ¼ The dimension is (m n+¾) (m+½). The coefficients of the remainder can be computed as determinants of certain sub-matrices of M [BPM06, Yap00]. By Bareiss algorithm, this also holds for pseudo-remainders. The coefficient of x n ½ j in the remainder, where n ½ j ¼, is the determinant of matrix M j, formed by taking the first m n + ½ columns of M and column m n + ¾ + j.
21 2.1 NOTATION AND BASIC COMPLEXITY RESULTS 13 Using Hadamard s inequality on the rows c j = ØM j ((δ + ¾) ¾ τ ) δ+½ ¾ σ (δ + ¾): The coefficients of pquo (f g) can be computed as principal minors of a m a m ½ º º º a m n a m n ½ º º º a ½ a ¼ b n b n ½ º º º b ¼ b n º º º b ½ b ¼ b n b n ½ º º º b ½ b ¼ Greatest Common Divisor Let K be a unique factorization domain. For example K = Z or K = Z[y]º Then we can define the greatest common divisor of two polynomials f g K[x] as the polynomial of maximal degree that divides the two polynomials f and gº This is denoted as (f g)º The greatest common divisor is of extreme importance in what follows. It allows us to compute the number of common roots between two different polynomials as well as compute the number of different roots of a polynomial fº Given f g K[x] such that deg(f) = d ½ deg(g) = d ¾ L(f) τ and L(g) τ, we can compute the in ÕB(d ½ d ¾ τ)º The bitsize of its coefficients is O(Ñ Ü{d ½ d ¾ }τ)º Due to the importance of the in the computations that arise in the subsequent algorithms, more details will be discussed at the appropriate points Resultant Another significant tool that forms the basis for all algorithms that will be discussed in chapter 3 is the resultant of two polynomials. Theorem 2.3. Given f g K[x] such that f = n i=½ a ix x and g = m j=½ b jx j with a n b m ¼ there is a unique (up to sign) irreducible polynomial res(f g) K[a n º º º a ¼ b m º º º b ¼ ] which is zero iff f g have a common factor. It is homogeneous and deg(res(f g)) = deg(f) + deg(g) = n + mº This polynomial is called resultant. Theorem 2.4. Given f g K[x] we can compute the resultant res(f g) via the Sylvester matrix Syl(f g)º More specifically, we have: res(f g) = Ø(Syl(f g))º Definition 2.5 (Sylvester Matrix). The Sylvester matrix of f and g is the
22 14 FOUNDATIONS (n + m) (n + m) matrix defined as follows: Syl(f g) = a n a n ½ a n ¾ º º º º º º a ¼ a n a n ½ a n ¾ º º º º º º a ¼ a n a n ½ a n ¾ º º º º º º a ¼ b m b m ½ b m ¾ º º º b ¼ b m b m ½ b m ¾ º º º b ¼ b m b m ½ b m ¾ º º º b ¼ Note that we can compute the resultant in time ÕB(nmτ) where τ is a bound on the bitsize of the coefficients of f and gº Discriminant Definition 2.6. Let f = d i=¼ a ix i K[x] d ¾ and ρ ½ º º º ρ d K its roots. The discriminant of f is the quantity disc(f) = a ¾d ¾ n ½ i<j d (ρ i ρ j ) ¾ In order to compute the discriminant we need the following theorem: Theorem 2.7. Given f = d i=¼ a ix i K[x] d ¾ we have: res(f f ) = ±a n disc(f) = ( ½) n(n ½) ¾ a n disc(f) A useful remark that will be used later on in section is the following: Remark 2.8 (Multiplicities). The definition of the discriminant does not require only different roots of the polynomial. Therefore, if a polynomial has a multiple root, then the discriminant must be zero (0). Equivalently, res(f f ) = ¼ if and only if f has multiple roots. If f Z[x] does not contain multiple roots, then disc(f) ½º An upper bound on the discriminant can be obtained with the following theorem: Theorem 2.9. Let f = d i=¼ a ix i Z[x]º Then: d disc(f) d d M(f) ¾(d ½) d d f ¾(d ½) ¾ where f ¾ = i=¼ a¾ i and M(f) is the Mahler bound of f which will be described in the following paragraph.
23 2.1 NOTATION AND BASIC COMPLEXITY RESULTS Mahler Bound Definition Let A = d i=¼ a ix i C[x] \ C such that d d A = a i x i = a d (X ρ i ) i=¼ with a d ¼º Then, the Mahler bound of A, denoted as M(A) is d M(A) = a d Ñ Ü{½ ρ j } j=½ i=½ The following identities are presented without proof: Proposition Given A B C[x]\C such that Mahler bound is defined and deg(a) = d and n N the following hold: a. M(x d A( ½ x )) = M(A(x))º b. M(A B) = M(A) M(B)º c. M(A(x k )) = M(A(x))º Classical Fan-In / Fan-Out Consider the setting of the previous paragraph but this time assume we want to evaluate f over a set J of natural numbers such that J dº The obvious technique would be to apply J times Horner s rule, thereby evaluating f over all J numbers in ÕB( J d Ñ Ü{dσ τ}) = ÕB(Ñ Ü{d σ d ¾ τ})º However, we can do better. This is a classic result [EP99] called Fan-In / Fan-Out and is based on an extension of the following lemma. Lemma Given a b c N (a ÑÓ (bc)) ÑÓ b = a ÑÓ bº Proof. a ÑÓ (bc) = k a = jbc + kº a ÑÓ b = m a = ib + mº Therefore, k = ib + m jbc k ÑÓ b = mº Corollary The following holds: p(x) ÑÓ (x x i ) = p(x) ÑÓ (x x j ) ÑÓ (x xi ) i J Nº j J Example 2.1. Let f(x) = x ¾x + ½ and assume we want to evaluate the function on { ¾ ½ ¼ ½}º The evaluation consists of two parts. Fan-In: In the first part we generate products of the form j (x x j)º Thus we start with the polynomials that have as roots the required integers; in this case we have (x + ¾) (x + ½) x (x ½)º In the following step we take two polynomials each time and generate their product, thereby obtaining this time (x ¾ + x + ¾) and (x ¾ x)º Finally, we compute the product p = (x ¾ + x + ¾)(x ¾ x) of these two polynomials that occurred. Working this way we generated a binary tree bottom-up as shown below: 2 x + ¾x x ¾ ¾x 1 x ¾ + x + ¾ x ¾ x 0 x + ¾ x + ½ x x ½
24 16 FOUNDATIONS Fan-Out: The next step consists of computing the required remainders. This time we traverse the tree top-down and store the results of each level. Therefore on the first level we must compute the pseudo-remainder prem (f p) º Note that f remains intact since deg(p) = > = deg(f)º On each subsequent level we work similarly; i.e. we compute the pseudoremainder between the polynomial of the previous level and the polynomial that is directed by the fan-in tree at the respective position. Hence on level ¾ we compute prem ( x ¾x + ½ x ¾ + x + ¾ ) = x+ and prem ( x ¾x + ½ x ¾ x ) = x + ½º Finally, on the third level we compute the pseudo-remainders prem ( x + x + ¾) = prem ( x + x + ½) = ¾ prem( x + ½ x) = ½ and prem ( x + ½ x ½) = ¼º The whole process and the new binary tree that has been formed is shown below: 0 x ¾x + ½ 1 x + ½ x 2 ¾ ½ ¼ Note that the requested values have been computed; i.e. f( ¾) = f( ½) = ¾ f(¼) = ½ and f(½) = ¼º Theorem 2.14 (Fan-In / Fan-Out). Let f Z[x] such that deg(f) d and L(f) τº We can evaluate f at n ¾ m d + ½ natural numbers of bitsize σ in time ÕB(d ¾ σ + dτ)º Proof. For simplicity assume that d is of the form ¾ m ½ and n = d + ½º Fan-In: Generating j (x x j). We form a binary tree with leaves the polynomials (x x j ) nodes the various polynomials that arise as products from the nodes of the previous level, and root the polynomial ¼ i d (x x j)º If we start counting from ¼ at the leaf-level, then at level j we have n polynomials ¾ j of degree ¾ j º Moreover, the bitsize of these polynomials is Õ((j + ½)σ)º The cost for computing the n polynomials of degree ¾ j ¾ j where j = ½ ¾ º º º Ð n is Õ B ((n/¾ j )M(¾ j ½ jσ)) = ÕB(njσ) since M(a b) = ÕB(ab) denotes the cost of multiplying two polynomials of degree bounded by a and coefficient bitsize bounded by b. Overall, the complexity for this step is O B (nσ Ð ¾ n) = ÕB(nσ) = Õ B (dσ)º Fan-Out: Subdivision. We now traverse the tree in the inverse direction. Moving from level j to j + ½ (j = ¼ º º º (Ð n ½)) we have to perform ¾ j+½ divisions with remainder with polynomials of degree n and respective bitsize ¾ j β j = O((Ð n + ½ j)σ)º Let s have a look on the degrees of the resulting polynomials (remainders). At root level the given polynomial f does not change. Dividing this polynomial with polynomials of degree n we obtain polynomials ¾ of degree n ½º Similarly, at level j (again counting from ¼ at root level) we have ¾ polynomials of degree n ¾ j ½ j = ½ º º º Ð nº Now, let s examine their respective bitsizes. Moving from level ¼ to level ½ we perform division on polynomials with bitsize b ¼ = τ (bound for coefficients of f) and β ½ = O(σ Ð n)º Thus, the result has bitsize b ½ = O(δ ½ β ½ +b ¼ ) = O(δ ½ σ Ð n+τ) where δ ½ = (n ½) n ¾ = n ¾ ½º Similarly, when reaching level j we have performed division with polynomials of bitsize b j ½ and β j which results in b j = O(δ j β j +b j ½ )º Note that β j is defined as β j = O((Ð n + ½ j)σ) j = ¼ º º º Ð nº Also, δ j = n ¾ j ½ j = ½ º º º Ð nº
25 2.2 REPRESENTING REAL ALGEBRAIC NUMBERS 17 Hence for all j = ¼ º º º Ð n, b j O(nσ Ð n+τ) = Õ(nσ+τ)º As a consequence, the running time complexity for this phase is: T = Ð n ½ j=¼ ¾ j+½ O B (( n ¾ j ½)( n ¾j)(nσ Ð n + τ)) Ð n ½ n = O B ((nσ Ð n + τ) ¾ j) j=¼ = O B ((nσ Ð n + τ)¾(n ½)) = ÕB(n ¾ σ + nτ) since we perform ¾ j+½ divisions per level j and the degrees are ( n ¾ j ½) and n ¾ j and the bitsizes are bounded by O(nσ Ð n + τ)º 2.2 Representing Real Algebraic Numbers We choose to represent a real algebraic number α R alg by the isolating interval representation. because it is more intuitive, it facilitates geometric applications, and turns out to be as efficient as other representations. It includes a square-free polynomial which vanishes on α and a (rational) interval containing α and no other root. More particularly, assume that α is the unique root of the square-free polynomial f in the interval I = [I L I R ] where I L I R Qº We denote this with the following representation: α [f I] = [f [I L I R ]]º Remark 2.15 (Bolzano). Note that since f is square-free and I is an isolating interval of the unique root α of f in the interval, then f satisfies the Bolzano criterion in the interval, i.e. f(i L ) f(i R ) < ¼º Remark 2.16 (Derivative). Moreover, it is easy to compute the sign of the derivative of f when evaluating at x = αº Since f is square-free, there exists an interval J I containing α such that f is monotone. Moreover, since the square-free f satisfies the Bolzano criterion in I it does not change sign on the intervals [I L α) and (α I R ] by construction. Therefore, sign ( f (α) ) ( = sign sign ( f(i R ) ) sign ( f(i L ) )) º 2.3 Polynomial Remainder Sequences We now return to the problem of computing the of two polynomials. In applications the interest relies on the roots (or the factorization) of the º Hence, it is acceptable to compute the up to similarity. An easy way of computing the of two polynomials f g Z[x] would be to perform successive pseudo-divisions (see section 2.1.2), thereby producing the sequence of (remainder) polynomials R ¼ = f R ½ = g R ¾ = prem (f g) º º º R k = prem (R k ¾ R k ½ )
26 18 FOUNDATIONS such that prem (R k ½ R k ) = ¼. Therefore, any sequence that mimics the above remainder sequence is called Polynomial Remainder Sequence (PRS for short). Moreover, if the degree at each step drops by 1, we call the sequence regular (or normal). The variations of the possible sequences rely on different computations of the parameters k λ of the following identity λ i f = Qg + krº Hence, apart from the Pseudo-Euclidean PRS which is rarely, if ever, used in practice, other PRSs are the Primitive-PRS which maintains primitive polynomials at each step, as well as the most commonly used in practice Subresultant PRS and Sturm-Habicht PRS. The Subresultant and the Sturm-Habicht sequences avoid the costly computation of the at each step (contrary to the Primitive-PRS) and the bitsize of the coefficients of the polynomials that arise in the sequence increases only linearly contrary to the Pseudo-Euclidean PRS where the bitsize of the coefficients exhibits exponential growth. The following example illustrates this fact: Example 2.2. Given f = x + x x x + x ¾ + ¾x g = x + x x ¾ x + ¾½ we obtain the following Remainder Sequences: Euclidean: ½ x + x ¾ ½ x ¾ + ¼ x ½¾ ¾ ½ ¼x ½ ¼ ¼¼ ½¾ ¼¼ ½¼¼ ½½ ½ ¾½ ¼¼ Primitive Part: x + x ¾ ½ x ¾ + ¾ x x ½ ¼ ½ Subresultant: ½ x x ¾ + x ¾ + ½¾ x ¾ ¾ x ½¾ ¼¼ ¾ ¼ ¼ The reader may refer to [Yap00] for a detailed treatment of the Polynomial Remainder Sequences. We now switch to the class of Polynomial Remainder Sequences that are actually used in real solving and are the heart of all computations that are described in this thesis.
27 2.3 POLYNOMIAL REMAINDER SEQUENCES Signed Polynomial Remainder Sequences Definition [LR01] The signed polynomial remainder sequence of f and g is denoted by ÈÊË (f g) and is a polynomial sequence similar to the R ¼ = f R ½ = g R ¾ = prem(f g) º º º R k = prem (R k ¾ R k ½ ) where prem (R k ½ R k ) = ¼. The quotient sequence contains the {Q i } ¼ i k, where Q i = pquo(r i R i+½ ), and the quotient boot is (Q ¼ º º º Q k ½ R k ). There is a huge bibliography on signed polynomial remainder sequences (c.f [BPM06, vzgg03, Yap00] and references therein). Here, we consider signed subresultant sequences, which contain polynomials similar to the polynomials in the signed polynomial remainder sequence; see [vzgl03] for a unified approach to subresultants. We consider the signed Subresultant sequences and Sturm-Habicht sequences (ËÊ(f g) and ËØÀ (f g) respectively) of f g, which contain polynomials proportional to the polynomials in ÈÊË (f g) since they achieve better bounds on the coefficient bitsize as it was demonstrated in example 2.2 and have good specialization properties since they are defined through determinants. To be more specific, we will consider subresultant sequences, or Sturm-Habicht sequences, in the case where g is the derivative of f. The reader may refer to [GVLRR89, BPM06] for information. We recall here the main results regarding the computation and the evaluation of such sequences. By Ö(f g) the sequence of the principal subresultant coefficients, by ËÉ(f g) the corresponding quotient boot, and by ËÊ(f g a) the evaluated sequence over a Q. If the polynomials are multivariate, then the aforementioned sequences are considered w.r.t. variable x, except if explicitly stated otherwise. Proposition [LR01, LRSED00, Rei97] Assuming p q, ËÊ(f g) is computed in ÕB(p ¾ qτ) and L(ËÊ j (f g)) = O(pτ). For any f g, their quotient boot, any polynomial in ËÊ(f g), their resultant, and their are computed in ÕB(pqτ). Lemma [LR01, Rei97] Let p q. We can compute ËÊ(f g a), where a Q {± } and L(a) = σ, in ÕB(pqτ + q ¾ σ + p ¾ σ). If f(a) is known, then the bound becomes ÕB(pqτ + q ¾ σ)º Proof. Let ËÊ q+½ = f and ËÊ q = g. For the moment we forget ËÊ q+½. We may assume that ËÊ q ½ is computed, since the cost of computing one element of ËÊ is the same as that of computing ËÉ(f g) (proposition 2.18). We follow Lickteig and Roy [LR01]. For two polynomials A B of degree bounded by D and bit size bounded by L, we can compute ËÊ(A B)(a), where L(a) L, in ÕB(M (D L)). In our case D = O(q) and L = O(pτ + qσ), thus the total costs is ÕB(pqτ + q ¾ σ). It remains to compute the evaluation ËÊ q+½ (a) = f(a). This can be done using Horner s scheme in ÕB(p Ñ Ü{τ pσ}). Thus, the whole procedure has complexity Õ B (pqτ + q ¾ σ + p Ñ Ü{τ pσ}) where the term pτ is dominated by pqτ.
28 20 FOUNDATIONS If L(f) = τ f τ g = L(g) then τ = Ñ Ü{τ f τ g } in the previous theorem. When q > p, ËÊ(f g) is f g f (g ÑÓ ( f)) º º º, thus ËÊ(f g a) starts with a sign variation irrespective of Ò(g(a)). If only the sign variations are needed, there is no need to evaluate g, so prop yields ÕB(pqτ + p ¾ σ). Definition Let L denote a list of real numbers. VAR(L) denotes the number of (possibly modified, see e.g. [BPM06, GVLRR89]) sign variations. Corollary For any f g, VAR(ËÊ(f g a)) is computed in ÕB(pqτ + Ñ Ò{p q} ¾ σ), provided Ò(f(a)) is known. 2.4 Univariate Polynomials The heart of the algorithms that are presented in chapter 3 relies on real solving univariate polynomials. Starting with some bounds, Sturm s algorithm will be briefly presented in the sequel, as well as the algorithm for determining the sign of a polynomial when evaluated at a real algebraic number. Finally, some bounds on root separation are going to be presented. These are critical on the complexity analysis of all the subsequent algorithms Bounding Roots Let f = d i=¼ a ix i Z[x]º Then we can obtain a bound for the roots of f with the following lemmas. Maximal Bounds Maximal bounds for roots are presented first. Lemma [Cauchy, Mignotte] Let α be a root of fº Then ( ) a d ½ α ½ + Ñ Ü º º º a ¼ º Note that the bound in lemma 2.22 is invariant if we multiply the polynomial by a constant. However, it behaves badly under the transformation x x ¾ which only changes the roots by a factor of 2, but may change the bound by a factor of ¾ d º The following bounds do not have this effect. Lemma [Cauchy] Let α be a root of fº Then a d a d ( ½ ½ da d ½ α Ñ Ü da d ¾ ¾ a d a d º º º da ¼ ) d a d º Lemma [Zassenhaus] Let α be a root of fº Then ( ½ ½ a d ½ α ¾ Ñ Ü a d ¾ ¾ a d a d º º º a ¼ ) d a d º
29 2.4 UNIVARIATE POLYNOMIALS 21 Complexity: All the above bounds can be computed in time ÕB(dτ)º Minimal Bounds The above lemmas 2.22, 2.23, 2.24 can be used for obtaining a bound on the minimal absolute value of a root of a polynomial (assuming that the constant coefficient is not zero - which is easy to check). The idea and algorithm for computing a bound comes from the following remark: Remark Let f = d i=¼ a ix i Z[x] and assume that α ¼ is a root of fº Then it holds that d a i α i = ¼º (2.1) i=¼ Consider the reciprocal polynomial g(x) = x d f( ½ x ) = d i=¼ a ix d i º Then by equation (2.1) and the hypothesis it follows that ½ α is a root of gº Hence, obtaining an upper bound on the roots of g we actually obtain a lower bound on the roots of fº Root Isolation and Sturm s algorithm Algorithm 1 presents Sturm s algorithm for computing isolating intervals of the roots of a polynomial f Z[x]º For simplicity, the input polynomial f is square-free. Proposition [DSY05, ESY06, EMT07] Let f Z[x] have degree p and bitsize τ f. We compute the isolating interval representation of its real roots and their multiplicities in ÕB(p + p τ ¾ f ). The endpoints of the isolating intervals have bitsize O(p ¾ + p τ f ) and L(f red ) = O(p + τ f ). There is no need to evaluate f red over the interval s endpoints because its sign is known; moreover, f red (a)f red (b) < ¼ Univariate sign determination Corollary [BPM06, EMT07] Given a real algebraic number α = (f [a b]), where L(a) = L(b) = O(pτ f ), and g Z[x], such that deg(g) = q L(g) = τ g, we compute Ò(g(α)) in bit complexity ÕB(pq Ñ Ü{τ f τ g } + p Ñ Ò{p q} ¾ τ f ). Proof. Assume that α is not a common root of f and g in [a b], then it is known that Òg(α) = [VAR(ËÊ(f g a)) VAR(ËÊ(f g b))] Ò(f (α))º Actually the previous relation holds in a more general context, when f dominates g, see [Yap00] for details. Notice that Ò(f (α)) = Ò(f(b)) Ò(f(b)), which is known from the real root isolation process. The complexity of the operation is dominated by the computation of VAR(ËÊ(f g a)) and VAR(ËÊ(f g b)), i.e. we compute ËÉ and evaluate it on a and b.
30 22 FOUNDATIONS Algorithm 1: Sturm::univariate. Input: A square-free polynomial f Z[x] Output: A list of isolating intervals of the roots of f. 1 S ËÊ(f f ); 2 N VAR(S ) VAR(S + ); 3 if N = ¼ then return ; 4 if N = ½ then return [ + ]; 5 M Maximal_Bound(f); 6 Intervals ; 7 Stack {[ M M VAR(S ) VAR(S + )]}; 8 while Stack do 9 [a b V a V b ] Pop(Stack); 10 c = a+b ¾ ; 11 if f(c) = ¼ then 12 Intervals Intervals {[c c]}; 13 M Minimal_Bound(Subst(x = x c, f)/x); 14 V c+ VAR(S c + M); 15 V c V c+ ½; 16 if V a = V c + ½ then Intervals Intervals {[a c M]}; 17 if V a > V c + ½ then Push(Stack, {[a c M V a V c ]}); 18 if V b = V c+ ½ then Intervals Intervals {[c + M b]}; 19 if V b < V c+ ½ then Push(Stack, {[c + M b V c+ V b ]}); else V c VAR(S c); if V a = V c + ½ then Intervals Intervals {[a c]}; if V a > V c + ½ then Push(Stack, {[a c V a V c ]}); if V b = V c ½ then Intervals Intervals {[c b]}; if V b < V c ½ then Push(Stack, {[c b V c V b ]}); 26 return Intervals ; As explained above, there is no need to evaluate the polynomial of the biggest degree, i.e. the first (and the second if p < q) of ËÊ(f g) over a and b. Thus the complexity is that of corollary 2.21, viz. Õ B (pq Ñ Ü{τ f τ g } + Ñ Ò{p q} ¾ p τ f ) Thus the complexity of the operation is two times the complexity of the evaluation of the sequence over the endpoints of the isolating interval. If α is a common root of f and g, or if f and g are not relative prime, then their gcd, which is the last non-zero polynomial in ËÊ(f g) is not a constant. Hence, we evaluate ËÊ on a and b, we check if the last polynomial is not a constant and if it changes sign on a and b. If this is the case, then Ò(g(α)) = ¼. Otherwise we proceed as above.
31 2.5 MULTIVARIATE POLYNOMIALS 23 Algorithm 2: univariate-sign_at. Input: A Polynomial g Z[x] and α = (f [a b]) R alg. Output: The sign of g(α)º 1 PRS ËÊ(f g); 2 v L VAR(ËÊ(PRS a)); 3 v R VAR(ËÊ(PRS b)); 4 return Sign([v L v R ] [f (α)]); Bounding root separation Theorem 2.28 (Davenport-Mahler-Mignotte). [TE06] Let A Z[X], with (A) = d and L(A) = τ, where A(¼) ¼. Let Ω be any set of k pairs of indices (i j) such that ½ i < j d and let the non-zero (complex) roots of A be ¼ < γ ½ γ ¾ γ d. Then ¾ k M(A) k d(d ½) k γ i γ j ¾ ¾ M(A) ½ d k disc(a)º (i j) Ω Proposition 2.26 expresses the state-of-the-art in univariate root isolation. It relies on the previous propositions for fast computation of polynomial sequences, and extensions of the Davenport-Mahler bound on aggregate root separation. The following lemma, derived from Davenport-Mahler s bound, is crucial. Lemma 2.29 (Aggregate separation). Given f Z[x], the sum of the bitsize of all isolating points of the real roots of f is O(p ¾ + p τ f ). Proof. Let there be r p real roots. The isolating point between two consecutive real roots α j α j+½ is of magnitude at most ½ ¾ α j α j+½ := ½ ¾ j. Thus their product is ½ ¾ r j j. Using the Davenport-Mahler-Mignotte bound by theorem 2.28, j j ¾ O(p¾ +pτ f ) and we take logarithms. Corollary 2.30 (Intermediate Points). Given the list of real roots of f in isolating interval representation, we compute rational numbers between them in ÕB(p ¾ + pτ f ). 2.5 Multivariate polynomials We discuss multivariate polynomials, using binary segmentation [Rei97]. An alternative approach could be [Klo95]. Let f g (Z[y ½ º º º y k ])[x] with deg x (f) = p q = deg x (g), deg yi (f) d i and deg yi (g) d i. Let d = k i=½ d i and L(f) L(g) τ. The y i -degree of every polynomial in ËÊ(f g), is bounded by deg yi (res(f g)) (p + q)d i. Thus, the homomorphism ψ : Z[y ½ º º º y k ] Z[y], where y ½ y y ¾ y (p+q)d½ º º º y k y (p+q)k ½ d ½ d k ½ allows us to decode res(ψ(f) ψ(g)) = ψ(res(f g)) and obtain res(f g). The same holds for every polynomial in ËÊ(f g). Now ψ(f) ψ(g) (Z[y])[x] have
32 24 FOUNDATIONS y degree d = (p+q) k ½ d ½ d k since, in the worst case, f or g hold a monomial such as y d ½ ½ yd ¾ ¾ º º º yd k k. Thus, deg y (res(ψ(f) ψ(g))) < (p + q) k d. Proposition [Rei97] We can compute ËÉ(f g), any polynomial in ËÊ(f g), and res(f g) in ÕB(q(p + q) k+½ dτ). Lemma ËÊ(f g) is computed in ÕB(q(p + q) k+¾ dτ). Proof. Every polynomial in ËÊ(f g) has coefficients of magnitude bounded by ¾ c(p+q)τ, for a suitable constant c, assuming τ > Ð (d). Consider the map χ : Z[y] Z, such that y ¾ c(p+q)τ, and let φ = ψ χ : Z[y ½ y ¾ º º º y k ] Z. Then L(φ(f)) L(φ(g)) c (p + q) k d τ. Now apply proposition Theorem We can evaluate ËÊ(f g) at x = α where a Q { } and L(a) = σ in ÕB(q(p + q) k+½ d Ñ Ü{τ σ}). Proof. By proposition 2.31 ËÉ(f g) can be computed and then evaluated it over a using binary segmentation in ÕB(q(p + q) k+½ d τ). For this we need to bound the bitsize of the resulting polynomials. The polynomials in ËÊ(f g) have total degree in y ½ º º º y k bounded by (p + q) k i=½ d i and coefficient bitsize bounded by (p + q)τ. With respect to x, the polynomials in ËÊ(f g) have degrees in O(p), so substitution x = a yields values of size Õ(pσ). After the evaluation we obtain polynomials in Z[y ½ º º º y k ] with coefficient bitsize bounded by Ñ Ü{(p + q)τ pσ} (p + q) Ñ Ü{τ σ}. Consider χ : Z[y] Z, such that y ¾ c(p+q) Ñ Ü{τ σ}, for a suitable constant c. Apply the map φ = ψ χ to f g. Now, L(φ(f)) L(φ(g)) cd(p + q) k Ñ Ü{τ σ}. By proposition 2.19, the evaluation costs ÕB(q(p + q) k+½ d Ñ Ü{τ σ}). We obtain the following corollaries for f g (Z[y])[x], such that deg x (f) = p, q = deg x (g), deg y (f) deg y (g) d and L(f) L(g) τ. Corollary We compute ËÊ(f g) in ÕB(pq(p+q) ¾ dτ). For any polynomial ËÊ j (f g) in ËÊ(f g), deg x (ËÊ j (f g)) = O(Ñ Ü{p q}), deg y (ËÊ j (f g)) = O(Ñ Ü{p q}d), and also L(ËÊ j (f g)) = O(Ñ Ü{p q}τ). Corollary We compute ËÉ(f g), any polynomial in ËÊ(f g), and res(f g) in ÕB(pq Ñ Ü{p q}dτ). Corollary We compute ËÊ(f g a), where a Q { } and L(a) = σ, in ÕB(pq Ñ Ü{p q}d Ñ Ü{τ σ}). For the polynomials ËÊ j (f g a) Z[y], except for f g, we have deg y (ËÊ j (f g a)) = O((p+q)d) and L(ËÊ j (f g a)) = O(Ñ Ü{p q}τ + Ñ Ò{p q}σ) Bivariate sign evaluation We now reduce the computation of the sign of f Z[x y] over (α β) R ¾ alg to that over several points in Q ¾. Let deg x (f) = deg y (f) = n ½, L(f) = σ and α = (A [a ½ a ¾ ]), β = (B [b ½ b ¾ ]), where A B Z[X], deg(a) = deg(b) = n ¾,
33 2.5 MULTIVARIATE POLYNOMIALS 25 Algorithm 3: bivariate-sign_at. Input: α = [A [A L A R ]] β = [B [B L B R ]] and f R[x y]; A B square-free. Output: sign(f(α β)) 1 PRS ËÊ(A f x); 2 PRS ½ (PRS(A L )); 3 for i ½ to PRS do 4 PRS ½ [i] = SignAt(PRS ½ [i] β); V L VAR(PRS ½ ); PRS ¾ (PRS(A L )); for i ½ to PRS do PRS ¾ [i] = SignAt(PRS ¾ [i] β); V R VAR(PRS ¾ ); return sign((v L V R ) A (α)); L(A) = L(B) = σ. We assume n ½ n ¾, which is relevant below. Algorithm 3 presents the whole procedure in pseudocode, see [Sak89], and generalizes the univariate case, e.g. [EMT07, Yap00] (algorithm 2). One has to obtain the sign variations of ËÊ(A F a ½ ), respectively ËÊ(A F a ¾ ) and substract them. After the evaluation of the sequence on a ½, respectively a ¾, polynomials in Z[y] occur. In order to obtain the sign variations, the sign of these polynomials over β has to be computed. This is performed with algorithm 2. For A, respectively B, we assume that we know their values on a ½ a ¾, respectively b ½ b ¾. Theorem 2.37 (Bivariate sign_at). Let f Z[x y] such that deg x (f) = deg y (f) = n ½ and L(f) = σ and two real algebraic numbers α = (A I α ) = [a ½ a ¾ ], β = (B I β ) = [b ½ b ¾ ] where A B Z[X], deg(a) = deg(b) = n ¾, L(A) = L(B) = σ and I α I β Q ¾. Then, one computes the sign of f evaluated over α and β with complexity ÕB(n ¾ ½ n ¾ σ), assuming that n ½ n ¾. Proof. First, we compute ËÉ x (A f) so as to evaluate ËÊ(A f) on the endpoints of α, in ÕB(n ¾ ½n ¾ ¾σ) (corollary 2.35). We compute ËÊ(A f a ½ ). The first polynomial in the sequence is A, but we already know its value on a ½. This computation costs ÕB(n ¾ ½ n ¾ σ) by corollary 2.36 with q = n ½, p = n ¾, d = n ½, τ = σ, and σ = n ¾ σ, where the latter corresponds to the bitsize of the endpoints. After the evaluation we obtain a list L ½, which contains O(n ½ ) polynomials, say h Z[y], such that deg(h) = O(n ½ n ¾ ). To bound the bitsize, notice that the polynomials in ËÊ(f g) are of degrees O(n ½ ) with respect to x and of bitsize O(n ¾ σ). After we evaluate on a ½, L(f) = O(n ½ n ¾ σ). For each h L ½ we compute its sign over β and count the sign variations. We could apply directly corollary 2.27, but we can do better. If deg(h) n ¾ then ËÊ(B h) = (B h B, g = prem (h B) º º º). We start the evaluations at g: it is computed in ÕB(n ¾ ½ n ¾ σ) (proposition 2.18), deg(g) = O(n ¾) and L(g) = O(n ½ n ¾ σ). Thus, we evaluate ËÊ( B g a ½ ) in ÕB(n ½ n ¾σ), by
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
6.3 Forecasting ARMA processes
 122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
122 CHAPTER 6. ARMA MODELS 6.3 Forecasting ARMA processes The purpose of forecasting is to predict future values of a TS based on the data collected to the present. In this section we will discuss a linear
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3
 Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
SCHOOL OF MATHEMATICAL SCIENCES G11LMA Linear Mathematics Examination Solutions
 SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
SCHOOL OF MATHEMATICAL SCIENCES GLMA Linear Mathematics 00- Examination Solutions. (a) i. ( + 5i)( i) = (6 + 5) + (5 )i = + i. Real part is, imaginary part is. (b) ii. + 5i i ( + 5i)( + i) = ( i)( + i)
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
2. THEORY OF EQUATIONS. PREVIOUS EAMCET Bits.
 EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
EAMCET-. THEORY OF EQUATIONS PREVIOUS EAMCET Bits. Each of the roots of the equation x 6x + 6x 5= are increased by k so that the new transformed equation does not contain term. Then k =... - 4. - Sol.
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Απόκριση σε Μοναδιαία Ωστική Δύναμη (Unit Impulse) Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο. Απόστολος Σ.
 Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Problem Set 3: Solutions
 CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
CMPSCI 69GG Applied Information Theory Fall 006 Problem Set 3: Solutions. [Cover and Thomas 7.] a Define the following notation, C I p xx; Y max X; Y C I p xx; Ỹ max I X; Ỹ We would like to show that C
forms This gives Remark 1. How to remember the above formulas: Substituting these into the equation we obtain with
 Week 03: C lassification of S econd- Order L inear Equations In last week s lectures we have illustrated how to obtain the general solutions of first order PDEs using the method of characteristics. We
Week 03: C lassification of S econd- Order L inear Equations In last week s lectures we have illustrated how to obtain the general solutions of first order PDEs using the method of characteristics. We
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Partial Differential Equations in Biology The boundary element method. March 26, 2013
 The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
Srednicki Chapter 55
 Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Exercises 10. Find a fundamental matrix of the given system of equations. Also find the fundamental matrix Φ(t) satisfying Φ(0) = I. 1.
 Exercises 0 More exercises are available in Elementary Differential Equations. If you have a problem to solve any of them, feel free to come to office hour. Problem Find a fundamental matrix of the given
Exercises 0 More exercises are available in Elementary Differential Equations. If you have a problem to solve any of them, feel free to come to office hour. Problem Find a fundamental matrix of the given
Quadratic Expressions
 Quadratic Expressions. The standard form of a quadratic equation is ax + bx + c = 0 where a, b, c R and a 0. The roots of ax + bx + c = 0 are b ± b a 4ac. 3. For the equation ax +bx+c = 0, sum of the roots
Quadratic Expressions. The standard form of a quadratic equation is ax + bx + c = 0 where a, b, c R and a 0. The roots of ax + bx + c = 0 are b ± b a 4ac. 3. For the equation ax +bx+c = 0, sum of the roots
New bounds for spherical two-distance sets and equiangular lines
 New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
New bounds for spherical two-distance sets and equiangular lines Michigan State University Oct 8-31, 016 Anhui University Definition If X = {x 1, x,, x N } S n 1 (unit sphere in R n ) and x i, x j = a
Lecture 15 - Root System Axiomatics
 Lecture 15 - Root System Axiomatics Nov 1, 01 In this lecture we examine root systems from an axiomatic point of view. 1 Reflections If v R n, then it determines a hyperplane, denoted P v, through the
Lecture 15 - Root System Axiomatics Nov 1, 01 In this lecture we examine root systems from an axiomatic point of view. 1 Reflections If v R n, then it determines a hyperplane, denoted P v, through the
Uniform Convergence of Fourier Series Michael Taylor
 Uniform Convergence of Fourier Series Michael Taylor Given f L 1 T 1 ), we consider the partial sums of the Fourier series of f: N 1) S N fθ) = ˆfk)e ikθ. k= N A calculation gives the Dirichlet formula
Uniform Convergence of Fourier Series Michael Taylor Given f L 1 T 1 ), we consider the partial sums of the Fourier series of f: N 1) S N fθ) = ˆfk)e ikθ. k= N A calculation gives the Dirichlet formula
SOLVING CUBICS AND QUARTICS BY RADICALS
 SOLVING CUBICS AND QUARTICS BY RADICALS The purpose of this handout is to record the classical formulas expressing the roots of degree three and degree four polynomials in terms of radicals. We begin with
SOLVING CUBICS AND QUARTICS BY RADICALS The purpose of this handout is to record the classical formulas expressing the roots of degree three and degree four polynomials in terms of radicals. We begin with
Section 7.6 Double and Half Angle Formulas
 09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
09 Section 7. Double and Half Angle Fmulas To derive the double-angles fmulas, we will use the sum of two angles fmulas that we developed in the last section. We will let α θ and β θ: cos(θ) cos(θ + θ)
Chapter 6: Systems of Linear Differential. be continuous functions on the interval
 Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Chapter 6: Systems of Linear Differential Equations Let a (t), a 2 (t),..., a nn (t), b (t), b 2 (t),..., b n (t) be continuous functions on the interval I. The system of n first-order differential equations
Fractional Colorings and Zykov Products of graphs
 Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Tridiagonal matrices. Gérard MEURANT. October, 2008
 Tridiagonal matrices Gérard MEURANT October, 2008 1 Similarity 2 Cholesy factorizations 3 Eigenvalues 4 Inverse Similarity Let α 1 ω 1 β 1 α 2 ω 2 T =......... β 2 α 1 ω 1 β 1 α and β i ω i, i = 1,...,
Tridiagonal matrices Gérard MEURANT October, 2008 1 Similarity 2 Cholesy factorizations 3 Eigenvalues 4 Inverse Similarity Let α 1 ω 1 β 1 α 2 ω 2 T =......... β 2 α 1 ω 1 β 1 α and β i ω i, i = 1,...,
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
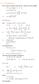 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
Reminders: linear functions
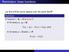 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
Problem Set 9 Solutions. θ + 1. θ 2 + cotθ ( ) sinθ e iφ is an eigenfunction of the ˆ L 2 operator. / θ 2. φ 2. sin 2 θ φ 2. ( ) = e iφ. = e iφ cosθ.
 Chemistry 362 Dr Jean M Standard Problem Set 9 Solutions The ˆ L 2 operator is defined as Verify that the angular wavefunction Y θ,φ) Also verify that the eigenvalue is given by 2! 2 & L ˆ 2! 2 2 θ 2 +
Chemistry 362 Dr Jean M Standard Problem Set 9 Solutions The ˆ L 2 operator is defined as Verify that the angular wavefunction Y θ,φ) Also verify that the eigenvalue is given by 2! 2 & L ˆ 2! 2 2 θ 2 +
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Math221: HW# 1 solutions
 Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS
 CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
CHAPTER 48 APPLICATIONS OF MATRICES AND DETERMINANTS EXERCISE 01 Page 545 1. Use matrices to solve: 3x + 4y x + 5y + 7 3x + 4y x + 5y 7 Hence, 3 4 x 0 5 y 7 The inverse of 3 4 5 is: 1 5 4 1 5 4 15 8 3
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Solutions to Exercise Sheet 5
 Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
Notes on the Open Economy
 Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
Notes on the Open Econom Ben J. Heijdra Universit of Groningen April 24 Introduction In this note we stud the two-countr model of Table.4 in more detail. restated here for convenience. The model is Table.4.
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Second Order Partial Differential Equations
 Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
PARTIAL NOTES for 6.1 Trigonometric Identities
 PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
= λ 1 1 e. = λ 1 =12. has the properties e 1. e 3,V(Y
 Stat 50 Homework Solutions Spring 005. (a λ λ λ 44 (b trace( λ + λ + λ 0 (c V (e x e e λ e e λ e (λ e by definition, the eigenvector e has the properties e λ e and e e. (d λ e e + λ e e + λ e e 8 6 4 4
Stat 50 Homework Solutions Spring 005. (a λ λ λ 44 (b trace( λ + λ + λ 0 (c V (e x e e λ e e λ e (λ e by definition, the eigenvector e has the properties e λ e and e e. (d λ e e + λ e e + λ e e 8 6 4 4
9.09. # 1. Area inside the oval limaçon r = cos θ. To graph, start with θ = 0 so r = 6. Compute dr
 9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
9.9 #. Area inside the oval limaçon r = + cos. To graph, start with = so r =. Compute d = sin. Interesting points are where d vanishes, or at =,,, etc. For these values of we compute r:,,, and the values
ST5224: Advanced Statistical Theory II
 ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
ST5224: Advanced Statistical Theory II 2014/2015: Semester II Tutorial 7 1. Let X be a sample from a population P and consider testing hypotheses H 0 : P = P 0 versus H 1 : P = P 1, where P j is a known
( ) 2 and compare to M.
 Problems and Solutions for Section 4.2 4.9 through 4.33) 4.9 Calculate the square root of the matrix 3!0 M!0 8 Hint: Let M / 2 a!b ; calculate M / 2!b c ) 2 and compare to M. Solution: Given: 3!0 M!0 8
Problems and Solutions for Section 4.2 4.9 through 4.33) 4.9 Calculate the square root of the matrix 3!0 M!0 8 Hint: Let M / 2 a!b ; calculate M / 2!b c ) 2 and compare to M. Solution: Given: 3!0 M!0 8
SCITECH Volume 13, Issue 2 RESEARCH ORGANISATION Published online: March 29, 2018
 Journal of rogressive Research in Mathematics(JRM) ISSN: 2395-028 SCITECH Volume 3, Issue 2 RESEARCH ORGANISATION ublished online: March 29, 208 Journal of rogressive Research in Mathematics www.scitecresearch.com/journals
Journal of rogressive Research in Mathematics(JRM) ISSN: 2395-028 SCITECH Volume 3, Issue 2 RESEARCH ORGANISATION ublished online: March 29, 208 Journal of rogressive Research in Mathematics www.scitecresearch.com/journals
Matrices and vectors. Matrix and vector. a 11 a 12 a 1n a 21 a 22 a 2n A = b 1 b 2. b m. R m n, b = = ( a ij. a m1 a m2 a mn. def
 Matrices and vectors Matrix and vector a 11 a 12 a 1n a 21 a 22 a 2n A = a m1 a m2 a mn def = ( a ij ) R m n, b = b 1 b 2 b m Rm Matrix and vectors in linear equations: example E 1 : x 1 + x 2 + 3x 4 =
Matrices and vectors Matrix and vector a 11 a 12 a 1n a 21 a 22 a 2n A = a m1 a m2 a mn def = ( a ij ) R m n, b = b 1 b 2 b m Rm Matrix and vectors in linear equations: example E 1 : x 1 + x 2 + 3x 4 =
A Note on Intuitionistic Fuzzy. Equivalence Relation
 International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής
 Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
Πρόβλημα 1: Αναζήτηση Ελάχιστης/Μέγιστης Τιμής Να γραφεί πρόγραμμα το οποίο δέχεται ως είσοδο μια ακολουθία S από n (n 40) ακέραιους αριθμούς και επιστρέφει ως έξοδο δύο ακολουθίες από θετικούς ακέραιους
Lecture 13 - Root Space Decomposition II
 Lecture 13 - Root Space Decomposition II October 18, 2012 1 Review First let us recall the situation. Let g be a simple algebra, with maximal toral subalgebra h (which we are calling a CSA, or Cartan Subalgebra).
Lecture 13 - Root Space Decomposition II October 18, 2012 1 Review First let us recall the situation. Let g be a simple algebra, with maximal toral subalgebra h (which we are calling a CSA, or Cartan Subalgebra).
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Second Order RLC Filters
 ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
ECEN 60 Circuits/Electronics Spring 007-0-07 P. Mathys Second Order RLC Filters RLC Lowpass Filter A passive RLC lowpass filter (LPF) circuit is shown in the following schematic. R L C v O (t) Using phasor
Numerical Analysis FMN011
 Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
Numerical Analysis FMN011 Carmen Arévalo Lund University carmen@maths.lth.se Lecture 12 Periodic data A function g has period P if g(x + P ) = g(x) Model: Trigonometric polynomial of order M T M (x) =
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
Lecture 34 Bootstrap confidence intervals
 Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
Lecture 34 Bootstrap confidence intervals Confidence Intervals θ: an unknown parameter of interest We want to find limits θ and θ such that Gt = P nˆθ θ t If G 1 1 α is known, then P θ θ = P θ θ = 1 α
5. Choice under Uncertainty
 5. Choice under Uncertainty Daisuke Oyama Microeconomics I May 23, 2018 Formulations von Neumann-Morgenstern (1944/1947) X: Set of prizes Π: Set of probability distributions on X : Preference relation
5. Choice under Uncertainty Daisuke Oyama Microeconomics I May 23, 2018 Formulations von Neumann-Morgenstern (1944/1947) X: Set of prizes Π: Set of probability distributions on X : Preference relation
Μηχανική Μάθηση Hypothesis Testing
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΠΑΝΕΠΙΣΤΗΜΙΟ ΚΡΗΤΗΣ Μηχανική Μάθηση Hypothesis Testing Γιώργος Μπορμπουδάκης Τμήμα Επιστήμης Υπολογιστών Procedure 1. Form the null (H 0 ) and alternative (H 1 ) hypothesis 2. Consider
Bounding Nonsplitting Enumeration Degrees
 Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
DERIVATION OF MILES EQUATION FOR AN APPLIED FORCE Revision C
 DERIVATION OF MILES EQUATION FOR AN APPLIED FORCE Revision C By Tom Irvine Email: tomirvine@aol.com August 6, 8 Introduction The obective is to derive a Miles equation which gives the overall response
DERIVATION OF MILES EQUATION FOR AN APPLIED FORCE Revision C By Tom Irvine Email: tomirvine@aol.com August 6, 8 Introduction The obective is to derive a Miles equation which gives the overall response
ORDINAL ARITHMETIC JULIAN J. SCHLÖDER
 ORDINAL ARITHMETIC JULIAN J. SCHLÖDER Abstract. We define ordinal arithmetic and show laws of Left- Monotonicity, Associativity, Distributivity, some minor related properties and the Cantor Normal Form.
ORDINAL ARITHMETIC JULIAN J. SCHLÖDER Abstract. We define ordinal arithmetic and show laws of Left- Monotonicity, Associativity, Distributivity, some minor related properties and the Cantor Normal Form.
Abstract Storage Devices
 Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
Chapter 3: Ordinal Numbers
 Chapter 3: Ordinal Numbers There are two kinds of number.. Ordinal numbers (0th), st, 2nd, 3rd, 4th, 5th,..., ω, ω +,... ω2, ω2+,... ω 2... answers to the question What position is... in a sequence? What
Chapter 3: Ordinal Numbers There are two kinds of number.. Ordinal numbers (0th), st, 2nd, 3rd, 4th, 5th,..., ω, ω +,... ω2, ω2+,... ω 2... answers to the question What position is... in a sequence? What
A Bonus-Malus System as a Markov Set-Chain. Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics
 A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Pg The perimeter is P = 3x The area of a triangle is. where b is the base, h is the height. In our case b = x, then the area is
 Pg. 9. The perimeter is P = The area of a triangle is A = bh where b is the base, h is the height 0 h= btan 60 = b = b In our case b =, then the area is A = = 0. By Pythagorean theorem a + a = d a a =
Pg. 9. The perimeter is P = The area of a triangle is A = bh where b is the base, h is the height 0 h= btan 60 = b = b In our case b =, then the area is A = = 0. By Pythagorean theorem a + a = d a a =
Inverse trigonometric functions & General Solution of Trigonometric Equations. ------------------ ----------------------------- -----------------
 Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
ω ω ω ω ω ω+2 ω ω+2 + ω ω ω ω+2 + ω ω+1 ω ω+2 2 ω ω ω ω ω ω ω ω+1 ω ω2 ω ω2 + ω ω ω2 + ω ω ω ω2 + ω ω+1 ω ω2 + ω ω+1 + ω ω ω ω2 + ω
 0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
Areas and Lengths in Polar Coordinates
 Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
Kiryl Tsishchanka Areas and Lengths in Polar Coordinates In this section we develop the formula for the area of a region whose boundary is given by a polar equation. We need to use the formula for the
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Practice Exam 2. Conceptual Questions. 1. State a Basic identity and then verify it. (a) Identity: Solution: One identity is csc(θ) = 1
 Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
Conceptual Questions. State a Basic identity and then verify it. a) Identity: Solution: One identity is cscθ) = sinθ) Practice Exam b) Verification: Solution: Given the point of intersection x, y) of the
b. Use the parametrization from (a) to compute the area of S a as S a ds. Be sure to substitute for ds!
 MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
Fourier Series. MATH 211, Calculus II. J. Robert Buchanan. Spring Department of Mathematics
 Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
DESIGN OF MACHINERY SOLUTION MANUAL h in h 4 0.
 DESIGN OF MACHINERY SOLUTION MANUAL -7-1! PROBLEM -7 Statement: Design a double-dwell cam to move a follower from to 25 6, dwell for 12, fall 25 and dwell for the remader The total cycle must take 4 sec
DESIGN OF MACHINERY SOLUTION MANUAL -7-1! PROBLEM -7 Statement: Design a double-dwell cam to move a follower from to 25 6, dwell for 12, fall 25 and dwell for the remader The total cycle must take 4 sec
SOME PROPERTIES OF FUZZY REAL NUMBERS
 Sahand Communications in Mathematical Analysis (SCMA) Vol. 3 No. 1 (2016), 21-27 http://scma.maragheh.ac.ir SOME PROPERTIES OF FUZZY REAL NUMBERS BAYAZ DARABY 1 AND JAVAD JAFARI 2 Abstract. In the mathematical
Sahand Communications in Mathematical Analysis (SCMA) Vol. 3 No. 1 (2016), 21-27 http://scma.maragheh.ac.ir SOME PROPERTIES OF FUZZY REAL NUMBERS BAYAZ DARABY 1 AND JAVAD JAFARI 2 Abstract. In the mathematical
Parametrized Surfaces
 Parametrized Surfaces Recall from our unit on vector-valued functions at the beginning of the semester that an R 3 -valued function c(t) in one parameter is a mapping of the form c : I R 3 where I is some
Parametrized Surfaces Recall from our unit on vector-valued functions at the beginning of the semester that an R 3 -valued function c(t) in one parameter is a mapping of the form c : I R 3 where I is some
Commutative Monoids in Intuitionistic Fuzzy Sets
 Commutative Monoids in Intuitionistic Fuzzy Sets S K Mala #1, Dr. MM Shanmugapriya *2 1 PhD Scholar in Mathematics, Karpagam University, Coimbatore, Tamilnadu- 641021 Assistant Professor of Mathematics,
Commutative Monoids in Intuitionistic Fuzzy Sets S K Mala #1, Dr. MM Shanmugapriya *2 1 PhD Scholar in Mathematics, Karpagam University, Coimbatore, Tamilnadu- 641021 Assistant Professor of Mathematics,
Space-Time Symmetries
 Chapter Space-Time Symmetries In classical fiel theory any continuous symmetry of the action generates a conserve current by Noether's proceure. If the Lagrangian is not invariant but only shifts by a
Chapter Space-Time Symmetries In classical fiel theory any continuous symmetry of the action generates a conserve current by Noether's proceure. If the Lagrangian is not invariant but only shifts by a
Lecture 21: Properties and robustness of LSE
 Lecture 21: Properties and robustness of LSE BLUE: Robustness of LSE against normality We now study properties of l τ β and σ 2 under assumption A2, i.e., without the normality assumption on ε. From Theorem
Lecture 21: Properties and robustness of LSE BLUE: Robustness of LSE against normality We now study properties of l τ β and σ 2 under assumption A2, i.e., without the normality assumption on ε. From Theorem
