A Static Approach to Secure Service Composition
|
|
|
- Ιωάννα Κρεστενίτης
- 7 χρόνια πριν
- Προβολές:
Transcript
1 A Static Approach to Secure Service Composition Massimo Bartoletti Pierpaolo Degano Gian-Luigi Ferrari Roberto Zunino Dipartimento di Informatica Università di Pisa
2 Summary Overview issues in secure service composition safety framings and policies req-by-contract for service request plans for secure orchestration A calculus for service composition syntax and operational semantics type & effect system Plans & Orchestration constructions of plans and linearization model-checking viable plans
3 Programming in a world of services l 1 τ 1 l 3 τ 3 S1 S3 l 2 τ 2 client l 4 τ 4 S2 S4
4 Programming in a world of services service location l 1 τ 1 service code l 3 τ 3 S1 S3 l 2 τ 2 client l 4 τ 4 S2 service interface S4 service orchestration
5 Security and service composition two kinds of security concerns: secrecy of transmitted data, authentication, etc (protocol analysis techniques) control on computational resources (access control, resource usage analysis, information flow control, etc) need for linguistic mechanisms that: work in a distributed setting assume no trust relations among services can also cope with mobile code
6 Security and service composition: safety framings Client wants to protect from untrusted results client applet service Linguistic mechanism: safety framing ϕ[applet] applet service The policy ϕ is enforced stepwise within its scope
7 Security and service composition: safety framings Similarly, services want to protect from clients client remote exec result service (now the safety framing belongs to the service) client remote exec result ϕ [exec] Scoped policies check the local execution histories
8 Security and service composition: service selection Req-by-name: request a given service among many S1 req S2 S2 S3 Why S2 and not S1 or S3, if all functionally equivalent?
9 Security and service composition: service selection Problems with request by name : what if named service S2 becomes unavailable? and if S2 is outperformed by S1 or S3? hard reasoning about non-functional properties of services (e.g. security) security level independent of the execution context (unless hard-wired in the service code) From syntax-based to semantics-based invocation Service names l,l,.. tell me nothing about the behaviour!
10 Security and service composition: service selection Req-by-contract: request a service respecting the desired behaviour req τ S1 only S1 is guaranteed to match the behaviour τ τ1 τ2 τ3 S1 S2 S3 τ imposes both functional and non-functional constraints
11 Use cases for Req-by-contract Example: download an applet that obeys the policy ϕ req τ 0 ( τ 1 ϕ[ ] τ 2 ) Example: a remote executer that obeys the policy ϕ req ( τ 0 τ 1 ) ϕ ϕ [ ] τ 2
12 Observable behaviour access events are the actions relevant for security (e.g. read/write local files, invoke/be invoked by a given service, etc) mechanically inferred, or inserted by programmer. their meaning is fixed globally. access events cannot be hidden. the (abstract) behaviour observable by the orchestrator over-approximates the run-time histories, i.e. sequences of access events (via a type & effect system).
13 What kind of policies? History-based security Policies ϕ are regular properties event histories Policies ϕ,ϕ ϕ have a local scope, possibily nested ϕ[ ϕ ϕ [ ] A policy can only control histories of a single site (no trust among services) Histories are local to stateless service sites (stateful easy)
14 Example: the Chinese Wall policy ϕ Chinese Wall: cannot write (α w ) after read (α r ) A ϕ α r α w q0 q1 q2 q2 non-final sink α w α r * α w α r α w ϕ
15 Principle of Least Privilege Programs should be granted the minimum set of rights needed to accomplish their task A service must always obey all the active policies (no policy override) Policies can always inspect the whole past history (no event can be discarded) Privileged calls implemented by policies that explicitly discard the past
16 Service publication (1) l 1 τ 1 l 1 {S1}: τ 1 l 2 {S2}: τ 2 1. infer τ 3 from S3 2. mark S3 so to prevent spoofing l 2 l 3 S1 τ 2 S2? S3
17 Service publication (2) l 1 τ 1 l 1 {S1}: τ 1 l 2 {S2}: τ 2 l 3 {S3}: τ 3 l 2 S1 τ 2 S2 Service Repository l 3 τ 3 S3
18 Service orchestration l 0 H l 1 S1 l i {S i }: τ i req r τ π 1. combine τ with the τ i to infer the abstract behaviour H 2. extract from H a viable plan π forl 0 l 2 l 3 S2 S3
19 Service orchestration l 0 H req r τ Plan π = r[l 2 ] l 1 l 2 S1 S2 l 3 S3 Names are only known by the orchestrator!
20 What is a plan? A plan drives the execution of an application, by associating each service request with one (or more) appropriate services With a viable plan: executions never violate policies there are no unresolved requests you can then dispose from any execution monitoring! Many kinds of plans: Simple: one service for each request Multi-choice: more services for each request Dependent: one service, and a continuation plan
21 Who do we trust? The orchestrator, that: certifies the behavioural descriptions of services (types annotated with effects H) composes the descriptions, and ensures that selected services match the requested types extracts the viable plans (through model-checking) Also, someone must ensure that services do not change their code on-the-fly
22 Summing up a calculus for secure service composition: distributed services safety framings scoped policies on localized execution histories req-by-contract service invocation static orchestrator: certifies the behavioural interfaces of services provides a client with the viable plans driving secure executions
23 What s next calculus: syntax and operational semantics static semantics: type & effect system types carry annotations H about service behaviour effects H are history expressions, which overapproximate the actual execution histories extracting viable plans: linearization: unscrambling the structure of H model checking: valid plans are viable
24 Services Services e ::= x α if b then e else e λ z x.e e e ϕ[e] req r τ (only in configs) wait l variable access event conditional abstraction application safety framing service request wait reply
25 Networks location service code and published interface N ::= l{e:τ}: η, e N N published service composition running code execution history
26 (Simple) Plans A plan is a function from requests r to services l π ::= 0 r[l] π π empty service choice composition Plans respect the partial knowledge l < l of services about the network (< is a partial ordering)
27 Example: delegating code execution l 1 l 3 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 l 4 α c ;(λx.α r ; ;α w ) req r2 (f) f()
28 Example: delegating code execution l 1 use in certified sites α c only l 3 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 α c ;(λx.α r ; ;α w ) req r2 (f) do not write α w after a read α r l 4 f()
29 Executing a network of services l 0 l 1 l 3 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 l 4 α c ; (λx.α r ; ;α w ) req r2 (f) f() π = r 1 [l 2 ] r 2 [l 3 ]
30 Executing a network of services l 0 l 1 l 3 λx.ϕ[α r ; ] f = wait l 1 α c ; ϕ [f()] l 2 ε l 4 α c ; (λx.α r ; ;α w ) req r2 (f) f() π = r 1 [l 2 ] r 2 [l 3 ]
31 Executing a network of services l 0 l 1 l 3 λx.ϕ[α r ; ] f = wait l 1 α c ; ϕ [f()] l 2 α c l 4 λx.α r ; ;α w req r2 (f) f() π = r 1 [l 2 ] r 2 [l 3 ]
32 Executing a network of services l 1 l 0 l 3 ε λx.ϕ[α r ; ] f = λx.α r ; ;α w α c ; ϕ [f()] l 2 l 4 α c ; (λx.α r ; ;α w ) wait l 3 f() π = r 1 [l 2 ] r 2 [l 3 ]
33 Executing a network of services l 0 l 1 l 3 α c λx.ϕ[α r ; ] ϕ [αr; ; αw] l 2 l 4 α c ; (λx.α r ; ;α w ) wait l 3 f() π = r 1 [l 2 ] r 2 [l 3 ]
34 Executing a network of services l 0 l 1 l 3 α c α r λx.ϕ[α r ; ] ϕ [α w ] l 2 l 4 α c ; (λx.α r ; ;α w ) wait l 3 f() π = r 1 [l 2 ] r 2 [l 3 ]
35 Executing a network of services l 1 l 0 l 3 α c α r α w ϕ λx.ϕ[α r ; ] ϕ [α w ] l 2 l 4 α c ; (λx.α r ; ;α w ) wait l 3 f() π = r 1 [l 2 ] r 2 [l 3 ] not viable!
36 Semantics of services (1) [App1] η,e 1 η,e 1 η, e 1 e 2 η, e 1 e 2 [App2] η,e 2 η,e 2 η, v e 2 η, v e 2 [AbsApp] η, (λ z x.e) v η, e{v/x, λ z x.e/z} [If] η, if b then e true else e false η, e B (b)
37 Semantics of services (2) [Event] η, α ηα, () [Framing Out] [Framing In] η,e η,e η = ϕ η, ϕ[e] η, ϕ[e ] η = ϕ η, ϕ[v] η, v
38 Semantics of networks (1) [Inject] η, e η, e {e:τ} omitted l: η, e π l: η, e N 1 π N 1 [Par] N 1 N 2 π N 1 N 2
39 Semantics of networks (2) [Request] π = r[l ] π -- plan l: η, req r v l {e }: ε, π l: η, wait l l {e }: ε, e v [Reply] l: η, wait l l {e }: η, v π l: η, v l {e }: ε,
40 Other kinds of plans Simple plans π ::= 0 π π r[l] l: req r l : {P} r[l ] l: wait l l : P Multi-choice plans π ::= 0 π π r[l 1 l k ] l: req r l : {P} r[l,l ] l: wait l l : P Dependent plans π ::= 0 π π r[l. π] l: r[l.π] req r l : {P} l: r[l.π] wait l l : π P many others: multi+dependent, regular, dynamic,
41 Static semantics Type & effect system types carry annotations H about service abstract behaviour effects H, namely history expressions, over-approximate the actual execution histories the type & effect inferred for a service depends on its partial knowledge < of the network
42 Types (pretty standard) τ ::= int bool 1 τ τ H
43 Effects (history expressions) H ::= ε α H H H + H h µh.h ϕ[h] l: H {π 1 H 1 π k H k } empty access event sequence choice variable recursion safety framing localization planned selection
44 Semantics of history expressions [[ α ]] π = (?: α) [[ l: H ]] π = [[ H ]] π {l /?} [[{π 1 H 1 π k H k } ]] π = U i=1..k [[ {π i H i } ]] π [[ {π H} ]] π = [[ H ]] π if π π plan π resolves the requests as π 0 π r[l] r[l] π π 0 π 1 π if π 0 π & π 1 π
45 Semantics of history expressions [[ H H ]] π = [[ H ]] π [[ H ]] π [[ H + H ]] π = [[ H ]] π + [[ H ]] π [[ µh.h]] π = U n>0 f n( ) where f(x) = [[ H ]] π { X / h}
46 Example H = {r[l] {r [l 1 ] α 1, r [l 2 ] α 2 }, r[l ] β} π = r[l] r [l 2 ] [[ H ]] π = [[ {r[l] {r [l 1 ] α 1, r [l 2 ] α 2 }} ]] π U [[ {r[l ] β} ]] π = [[ {r [l 1 ] α 1, r [l 2 ] α 2 } ]] π = [[ {r [l 1 ] α 1 } ]] π U [[ {r [l 2 ] α 2 } ]] π = [[ α 2 ]] π = (?: α 2 )
47 Example H = l: {r[l 1 ] l 1 :α 1, r[l 2 ] l 2 :α 2 } β π = r[l 1 ] [[ H ]] π = [[{r[l 1 ] l 1 :α 1, r[l 2 ] l 2 :α 2 } β ]] π {l/?} = [[{r[l 1 ] l 1 :α 1, r[l 2 ] l 2 :α 2 }]] π (l: β) = [[ l 1 :α 1 ]] π (l: β) = (?: α 1 ) {l 1 /?} (l: β) = (l: β, l 1 : α 1 )
48 Typing rules (1) [T-Ev] Γ, α - l α : 1 [T-Var] Γ, ε - l x : Γ(x) [T-Loc] Γ, H - l e: τ Γ, l: H - e: τ [T-Wk] Γ, H - l e: τ Γ, H+H - l e: τ
49 Typing rules (2) [T-If] [T-Fr] Γ, H - l e: τ Γ, ϕ[h] - l ϕ[e] : τ Γ, H - l e: τ Γ, H - l e : τ Γ, H - l if b then e else e : τ
50 Typing rules (3) [T-Abs] Γ; x:τ;z: τ τ, H - l e : τ [T-App] H Γ, ε - l λ z x.e : H Γ, H - l e: τ τ Γ, H H H τ τ H τ - l e e : τ Γ, H - l e : τ
51 Typing Example (1) α - l α:1 z:1 H? - l (λy.zx)β:1 1,α+? - l if b then α else (λy.zx)β:1
52 Typing Example (2) H ε - l (λy.zx):1 1 β - l β:1 α - l α:1 ε β H - l (λy.zx)β:1 z:1 H 1,α+β H - l if b then α else (λy.zx)β:1
53 Typing Example (3) x:1;z:1 H 1, H - l zx:1 H ε - l (λy.zx):1 1 β - l β:1 α - l α:1 z:1 H β H - l (λy.zx)β:1 1,α+ β H - l if b then α else (λy.zx)β:1
54 Typing Example (4) z:1 H H 1, ε - l z:1 1 x:1;z:1 H x:1, ε - l x:1 1, ε ε H - l zx:1 H ε - l (λy.zx):1 1 β - l β:1 α - l α:1 z:1 H β H - l (λy.zx)β:1 1,α+ β H - l if b then α else (λy.zx)β:1
55 Typing Example z:1 H 1,α+ β H - l if b then α else (λy.zx)β:1 ε - l λ z x.if b then α else (λy.zx)β: τ H τ [T-Abs] To use rule the latent and actual effects must be unified, i.e. H = α+ β H A history expression that satisfies the above is: H = µh. α + β h
56 Typing rules (3) [T-Req] τ = U { ρ + r[l] τ A & B & C } A, ε - l e: τ C l <l {e: τ } Γ, ε - l req r ρ : τ B ρ τ
57 Typing rules (3) [T-Req] certified interface τ = U { ρ + r[l] τ A & B & C } A, ε - l e: τ C l <l {e: τ } Γ, ε - l req r ρ : τ B ρ τ
58 Typing rules (3) [T-Req] compatible types τ = U { ρ + r[l] τ A & B & C } A, ε - l e: τ C l <l {e: τ } Γ, ε - l req r ρ : τ B ρ τ
59 Typing rules (3) [T-Req] τ = U { ρ + r[l] τ A & B & C } A, ε - l e: τ C l <l {e: τ } Γ, ε - l req r ρ : τ B ρ τ visibility
60 Certified published interfaces l 1 ϕ[α r ] 1 (1 1) l 3 h (1 1) α c ϕ [h] 1 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 α c α r α w 1 (1 1) l 4 h (1 1) h 1 α c ; λx.α r ; ;α w req r2 (f) f()
61 Abstracting client behaviour l 1 ε ϕ[α r ] 1 (1 1) l 3 h (1 1) α c ϕ [h] 1 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 α c α r α w 1 (1 1) l 4 h (1 1) h 1 α c ; λx.α r ; ;α w req r2 (f) f() { r 1 [l 1 ] l 1 : ε, r 1 [l 2 ] l 2 : α c ] }
62 Abstracting client behaviour l 1 ε ϕ[α r ] 1 (1 1) l 3 h (1 1) α c ϕ [h] 1 λx.ϕ[α r ; ] f = req r1 () α c ; ϕ [f()] l 2 α c α r α w 1 (1 1) l 4 h (1 1) h 1 α c ; λx.α r ; ;α w req r2 (f) f() { r 2 [l 3 ] l 3 : α c ϕ [{ r 1 [l 1 ] ϕ[α r ], r 1 [l 2 ] α r α w }], r 2 [l 4 ] l 4 : { r 1 [l 1 ] ϕ[α r ], r 1 [l 2 ] α r α w }}
63 Summing up Calculus: operational semantics and type & effect system effects are history expressions, and overapproximate the actual execution histories planned selections therein hinder information about which plans to choose for secure compositions
64 What s next: the road to viable plans linearization: extracting plans and their pure effects by unscrambling the structure of history expressions validity: defining when an effect denotes histories that never go wrong model checking: valid plans are viable transform history expression into BPAs transform policies into FSAs orchestrator: uses viable plans to drive safe service composition
65 Which are the viable plans? { r 1 [l 1 ] l 1 : ε, r 1 [l 2 ] l 2 : α c ] } { r 2 [l 3 ] l 3 : α c ϕ [{ r 1 [l 1 ] ϕ[α r ], r 1 [l 2 ] α r α w }], r 2 [l 4 ] l 4 : { r 1 [l 1 ] ϕ[α r ], r 1 [l 2 ] α r α w }} Difficult to tell: the planned selections are nested! { r 1 [l 1 ] r 2 [l 3 ] l 1 : ε,l 3 : α c ϕ [ϕ[α r ]], { r 1 [l 2 ] r 2 [l 4 ] l 2 : α c, l 4 : α r α w, { r 1 [l 1 ] r 2 [l 4 ] l 1 : ε,l 4 : ϕ[α r ], { r 1 [l 2 ] r 2 [l 3 ] l 2 : α c, l 3 : α c ϕ [α r α w ]} viable viable not viable not viable
66 Linearization transform H into a semantically equivalent H Hsuch that H is in linear form, i.e.: H = {π 1 H 1 π k H k } and the H i have no planned selections. defined through oriented equations that groups r[l] in topmost position
67 Linearization H {0 H} {π i H i } i {π j H j } {π j i π j H i H j } i,j {π i H i } i + {π j H j } j {π i π j H i + H j } i,j ϕ[ {π i H i } i ] {π i ϕ[h i ] } i µh.{π i H i } i {π i µh. H i } i {π i {π i,j H i,j } j } i {π i π i,j H i,j } i,j
68 Example H ϕ[ λ z x. req r ρ; z x ] l 1 l 2 α β H = ϕ[ µh. { r[l 1 ] α, r[l 2 ] β} h ]
69 Example H = ϕ[ µh. { r[l 1 ] α, r[l 2 ] β} h ] ϕ[ µh. { r[l 1 ] α, r[l 2 ] β} {0 h} ] ϕ[ µh. { r[l 1 ] 0 α h, r[l 2 ] 0 β h} ] = ϕ[ µh. { r[l 1 ] α h, r[l 2 ] β h}] ϕ[ { r[l 1 ] µh. α h, r[l 2 ] µh. β h } ] { r[l 1 ] ϕ[ µh. α h], r[l 2 ] ϕ[ µh. β h] }
70 Simple vs multi-choice plans With simple plans: H { r[l 1 ] ϕ[ µh. α h], r[l 2 ] ϕ[ µh. β h] } With multi-choice plans: H { r[l 1 ] ϕ[ µh. α h], r[l 2 ] ϕ[ µh. β h], r[l 1,l 2 ] ϕ[ µh. (α+ β) h]} Plan r[l 1,l 2 ] useful when l 1 or l 2 unavailable
71 Example: bottleneck service l 0 H ϕ= never αα nor ββ l 2 ϕ[req r ; req r ] l 1 reqr1 l 3 α β H = ϕ[ { r[l 1 ] { r 1 [l 2 ] α, r 1 [l 3 ] β} } { r [l 1 ] { r 1 [l 2 ] α, r 1 [l 3 ] β}}]
72 Simple vs dependent plans With simple plans: H { r[l 1 ] r 1 [l 2 ] r [l 1 ] ϕ[α α], r[l 1 ] r 1 [l 3 ] r [l 1 ] ϕ[β β] } With dependent plans: H { r[l 1. r 1 [l 2 ]] r [l 1. r 1 [l 2 ]] ϕ[α α], r[l 1. r 1 [l 2 ]] r [l 1. r 1 [l 3 ]] ϕ[α β], r[l 1. r 1 [l 3 ]] r [l 1. r 1 [l 2 ]] ϕ[β α], r[l 1. r 1 [l 3 ]] r [l 1. r 1 [l 3 ]] ϕ[β β] } not viable not viable not viable viable viable not viable
73 Validity histories are enriched with [ ϕ and ] ϕ to point out the scope of policies. a history is valid when all the policies are respected, within their scopes ex: α w α r [ ϕ α w ] ϕ not valid (write after read) ex: α w [ ϕ α r ] ϕ α w valid (write outside scope of ϕ) a history expression H is π-valid when all the histories in [[ H ]] π are valid.
74 Validity, formally Safe sets: S(ε) = 0 S(η α) = S(η) S(η 0 [ ϕ η 1 ] ϕ ) = S(η 0 η 1 ) U ϕ[ flat(η 0 ) flat pref(η 1 ) ] Example: S([ ϕ α [ Ψ β ] Ψ γ ] ) = S(α [ ϕ Ψ β ] Ψ γ ) U ϕ[{ε, α, αβ,αβγ }] = Ψ[{α, αβ}], ϕ[{ε, α, αβ,αβγ }] η is valid if, for each ϕ[{η 1,,η k }] in S(η): η i = ϕ for 1 i k
75 Verifying validity Model checking: valid plans are viable (drive executions that never go wrong) transform linearized history expression into BPAs (Basic Process Algebras) transform policies into scoped policies (in the form of Finite State Automata)
76 From history expressions to BPAs Example H = β (µh. α + h h + ϕ[h]) BPA(H) = β X, { X = α + X X + [ ϕ X ] ϕ } Theorem: [[ H ]] = [[ BPA(H) ]]
77 From policies to scoped policies Example α w α r * A ϕ α r α w q0 q1 q2 Chinese Wall policy: no write after read
78 From policies to scoped policies Example α w α r α r, α w A ϕ[ ] α r α w q0 q1 q2 ] ϕ ] ϕ [ ϕ [ ϕ q2 α r q3 α w α r
79 From policies to scoped policies Theorem: η valid iff η accepted by A ϕ[ ] for all ϕ occurring in η η w/o redundant framings ϕ[...ϕ[ ]...] =ϕ[......]
80 Model- checking BPAs with FSAs Theorem: H valid iff [[ BPA(H) ]] = A ϕ[ ] ϕ in H
81 Main result Network N = l 1 { e 1 : τ 1 } l k { e k : τ k } 0, H i - e i : τ i for 1 i k / If H i is π-valid then π is viable for e i
82 Summing up hypothesis: client with history expression H linearization: transform H into a semantically equivalent H in linear form, i.e.: H = {π 1 H 1 π k H k } and the H i have no planned selections. verification: model-check the H i for validity theorem: if H i is valid, then π i is viable
83 Conclusions A linguistic framework for secure service composition safety framings, policies, req-by-contract type & effect system verification of effects, to extract viable plans The orchestrator securely composes and runs service-based applications
84 Other issues considered instrumentation: how to compile local policies into local checks, in case that some policy may fail resource creation: how to create fresh resources liveness: how to deal with properties of the form something good will eventually happen multi-choice and dependent plans
85 Future work other kinds of plans (e.g. dynamic) other kinds of effects (e.g. sessions) safety framings and security protocols safety framings for information flow incremental analysis, when new services can be discovered at run-time trust relations between services spatial types and logics
86 References M. Bartoletti, P. Degano, G.L. Ferrari. Types and Effects for Secure Service Orchestration. CSFW 06. M. Bartoletti, P. Degano, G.L. Ferrari. Plans for service composition. WITS 06. M. Bartoletti, P. Degano, G.L. Ferrari. Enforcing Secure Service Composition. CSFW 05. M. Bartoletti, P. Degano, G.L. Ferrari. Checking risky events is enough for local policies. ICTCS 05.
Secure Service Orchestration
 Secure Service Orchestration Massimo Bartoletti Pierpaolo Degano Gian-Luigi Ferrari Roberto Zunino Dipartimento di Informatica Università di Pisa Summary Overview issues in secure service composition security
Secure Service Orchestration Massimo Bartoletti Pierpaolo Degano Gian-Luigi Ferrari Roberto Zunino Dipartimento di Informatica Università di Pisa Summary Overview issues in secure service composition security
Enforcing Secure Service Composition
 CSFW 05 p.1 Enforcing Secure Service Composition Massimo Bartoletti Pierpaolo Degano Gian Luigi Ferrari Dipartimento di Informatica, Università di Pisa CSFW 05 p.2 Example: contract signing ψ e trusted
CSFW 05 p.1 Enforcing Secure Service Composition Massimo Bartoletti Pierpaolo Degano Gian Luigi Ferrari Dipartimento di Informatica, Università di Pisa CSFW 05 p.2 Example: contract signing ψ e trusted
The Simply Typed Lambda Calculus
 Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Type Inference Instead of writing type annotations, can we use an algorithm to infer what the type annotations should be? That depends on the type system. For simple type systems the answer is yes, and
Overview. Transition Semantics. Configurations and the transition relation. Executions and computation
 Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Overview Transition Semantics Configurations and the transition relation Executions and computation Inference rules for small-step structural operational semantics for the simple imperative language Transition
Dynamic types, Lambda calculus machines Section and Practice Problems Apr 21 22, 2016
 Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Dynamic types, Lambda calculus machines Apr 21 22, 2016 1 Dynamic types and contracts (a) To make sure you understand the
Other Test Constructions: Likelihood Ratio & Bayes Tests
 Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
Other Test Constructions: Likelihood Ratio & Bayes Tests Side-Note: So far we have seen a few approaches for creating tests such as Neyman-Pearson Lemma ( most powerful tests of H 0 : θ = θ 0 vs H 1 :
C.S. 430 Assignment 6, Sample Solutions
 C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
C.S. 430 Assignment 6, Sample Solutions Paul Liu November 15, 2007 Note that these are sample solutions only; in many cases there were many acceptable answers. 1 Reynolds Problem 10.1 1.1 Normal-order
Every set of first-order formulas is equivalent to an independent set
 Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
Every set of first-order formulas is equivalent to an independent set May 6, 2008 Abstract A set of first-order formulas, whatever the cardinality of the set of symbols, is equivalent to an independent
2 Composition. Invertible Mappings
 Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
Arkansas Tech University MATH 4033: Elementary Modern Algebra Dr. Marcel B. Finan Composition. Invertible Mappings In this section we discuss two procedures for creating new mappings from old ones, namely,
derivation of the Laplacian from rectangular to spherical coordinates
 derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
derivation of the Laplacian from rectangular to spherical coordinates swapnizzle 03-03- :5:43 We begin by recognizing the familiar conversion from rectangular to spherical coordinates (note that φ is used
Fractional Colorings and Zykov Products of graphs
 Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Fractional Colorings and Zykov Products of graphs Who? Nichole Schimanski When? July 27, 2011 Graphs A graph, G, consists of a vertex set, V (G), and an edge set, E(G). V (G) is any finite set E(G) is
Lecture 2. Soundness and completeness of propositional logic
 Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Lecture 2 Soundness and completeness of propositional logic February 9, 2004 1 Overview Review of natural deduction. Soundness and completeness. Semantics of propositional formulas. Soundness proof. Completeness
Bounding Nonsplitting Enumeration Degrees
 Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
Bounding Nonsplitting Enumeration Degrees Thomas F. Kent Andrea Sorbi Università degli Studi di Siena Italia July 18, 2007 Goal: Introduce a form of Σ 0 2-permitting for the enumeration degrees. Till now,
The challenges of non-stable predicates
 The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
The challenges of non-stable predicates Consider a non-stable predicate Φ encoding, say, a safety property. We want to determine whether Φ holds for our program. The challenges of non-stable predicates
Instruction Execution Times
 1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
1 C Execution Times InThisAppendix... Introduction DL330 Execution Times DL330P Execution Times DL340 Execution Times C-2 Execution Times Introduction Data Registers This appendix contains several tables
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit
 Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Ordinal Arithmetic: Addition, Multiplication, Exponentiation and Limit Ting Zhang Stanford May 11, 2001 Stanford, 5/11/2001 1 Outline Ordinal Classification Ordinal Addition Ordinal Multiplication Ordinal
Phys460.nb Solution for the t-dependent Schrodinger s equation How did we find the solution? (not required)
 Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Phys460.nb 81 ψ n (t) is still the (same) eigenstate of H But for tdependent H. The answer is NO. 5.5.5. Solution for the tdependent Schrodinger s equation If we assume that at time t 0, the electron starts
Models for Probabilistic Programs with an Adversary
 Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
Models for Probabilistic Programs with an Adversary Robert Rand, Steve Zdancewic University of Pennsylvania Probabilistic Programming Semantics 2016 Interactive Proofs 2/47 Interactive Proofs 2/47 Interactive
ω ω ω ω ω ω+2 ω ω+2 + ω ω ω ω+2 + ω ω+1 ω ω+2 2 ω ω ω ω ω ω ω ω+1 ω ω2 ω ω2 + ω ω ω2 + ω ω ω ω2 + ω ω+1 ω ω2 + ω ω+1 + ω ω ω ω2 + ω
 0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
0 1 2 3 4 5 6 ω ω + 1 ω + 2 ω + 3 ω + 4 ω2 ω2 + 1 ω2 + 2 ω2 + 3 ω3 ω3 + 1 ω3 + 2 ω4 ω4 + 1 ω5 ω 2 ω 2 + 1 ω 2 + 2 ω 2 + ω ω 2 + ω + 1 ω 2 + ω2 ω 2 2 ω 2 2 + 1 ω 2 2 + ω ω 2 3 ω 3 ω 3 + 1 ω 3 + ω ω 3 +
4.6 Autoregressive Moving Average Model ARMA(1,1)
 84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
84 CHAPTER 4. STATIONARY TS MODELS 4.6 Autoregressive Moving Average Model ARMA(,) This section is an introduction to a wide class of models ARMA(p,q) which we will consider in more detail later in this
Homework 3 Solutions
 Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Homework 3 Solutions Igor Yanovsky (Math 151A TA) Problem 1: Compute the absolute error and relative error in approximations of p by p. (Use calculator!) a) p π, p 22/7; b) p π, p 3.141. Solution: For
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3
 Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Lecture 2: Dirac notation and a review of linear algebra Read Sakurai chapter 1, Baym chatper 3 1 State vector space and the dual space Space of wavefunctions The space of wavefunctions is the set of all
Statistical Inference I Locally most powerful tests
 Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
Statistical Inference I Locally most powerful tests Shirsendu Mukherjee Department of Statistics, Asutosh College, Kolkata, India. shirsendu st@yahoo.co.in So far we have treated the testing of one-sided
3.4 SUM AND DIFFERENCE FORMULAS. NOTE: cos(α+β) cos α + cos β cos(α-β) cos α -cos β
 3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
3.4 SUM AND DIFFERENCE FORMULAS Page Theorem cos(αβ cos α cos β -sin α cos(α-β cos α cos β sin α NOTE: cos(αβ cos α cos β cos(α-β cos α -cos β Proof of cos(α-β cos α cos β sin α Let s use a unit circle
Reminders: linear functions
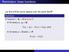 Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Reminders: linear functions Let U and V be vector spaces over the same field F. Definition A function f : U V is linear if for every u 1, u 2 U, f (u 1 + u 2 ) = f (u 1 ) + f (u 2 ), and for every u U
Approximation of distance between locations on earth given by latitude and longitude
 Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
Approximation of distance between locations on earth given by latitude and longitude Jan Behrens 2012-12-31 In this paper we shall provide a method to approximate distances between two points on earth
LTL to Buchi. Overview. Buchi Model Checking LTL Translating LTL into Buchi. Ralf Huuck. Buchi Automata. Example
 Overview LTL to Buchi Buchi Model Checking LTL Translating LTL into Buchi Ralf Huuck Buchi Automata Example Automaton which accepts infinite traces δ A Buchi automaton is 5-tuple Σ, Q, Q 0,δ, F Σ is a
Overview LTL to Buchi Buchi Model Checking LTL Translating LTL into Buchi Ralf Huuck Buchi Automata Example Automaton which accepts infinite traces δ A Buchi automaton is 5-tuple Σ, Q, Q 0,δ, F Σ is a
ANSWERSHEET (TOPIC = DIFFERENTIAL CALCULUS) COLLECTION #2. h 0 h h 0 h h 0 ( ) g k = g 0 + g 1 + g g 2009 =?
 Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Teko Classes IITJEE/AIEEE Maths by SUHAAG SIR, Bhopal, Ph (0755) 3 00 000 www.tekoclasses.com ANSWERSHEET (TOPIC DIFFERENTIAL CALCULUS) COLLECTION # Question Type A.Single Correct Type Q. (A) Sol least
Congruence Classes of Invertible Matrices of Order 3 over F 2
 International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
International Journal of Algebra, Vol. 8, 24, no. 5, 239-246 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/.2988/ija.24.422 Congruence Classes of Invertible Matrices of Order 3 over F 2 Ligong An and
Concrete Mathematics Exercises from 30 September 2016
 Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Concrete Mathematics Exercises from 30 September 2016 Silvio Capobianco Exercise 1.7 Let H(n) = J(n + 1) J(n). Equation (1.8) tells us that H(2n) = 2, and H(2n+1) = J(2n+2) J(2n+1) = (2J(n+1) 1) (2J(n)+1)
Section 8.3 Trigonometric Equations
 99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
99 Section 8. Trigonometric Equations Objective 1: Solve Equations Involving One Trigonometric Function. In this section and the next, we will exple how to solving equations involving trigonometric functions.
CHAPTER 25 SOLVING EQUATIONS BY ITERATIVE METHODS
 CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
CHAPTER 5 SOLVING EQUATIONS BY ITERATIVE METHODS EXERCISE 104 Page 8 1. Find the positive root of the equation x + 3x 5 = 0, correct to 3 significant figures, using the method of bisection. Let f(x) =
HOMEWORK 4 = G. In order to plot the stress versus the stretch we define a normalized stretch:
 HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
HOMEWORK 4 Problem a For the fast loading case, we want to derive the relationship between P zz and λ z. We know that the nominal stress is expressed as: P zz = ψ λ z where λ z = λ λ z. Therefore, applying
Fourier Series. MATH 211, Calculus II. J. Robert Buchanan. Spring Department of Mathematics
 Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Fourier Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Introduction Not all functions can be represented by Taylor series. f (k) (c) A Taylor series f (x) = (x c)
Απόκριση σε Μοναδιαία Ωστική Δύναμη (Unit Impulse) Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο. Απόστολος Σ.
 Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Απόκριση σε Δυνάμεις Αυθαίρετα Μεταβαλλόμενες με το Χρόνο The time integral of a force is referred to as impulse, is determined by and is obtained from: Newton s 2 nd Law of motion states that the action
Assalamu `alaikum wr. wb.
 LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
LUMP SUM Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. Assalamu `alaikum wr. wb. LUMP SUM Wassalamu alaikum wr. wb. LUMP SUM Lump sum lump sum lump sum. lump sum fixed price lump sum lump
TMA4115 Matematikk 3
 TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
TMA4115 Matematikk 3 Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet Trondheim Spring 2010 Lecture 12: Mathematics Marvellous Matrices Andrew Stacey Norges Teknisk-Naturvitenskapelige Universitet
Block Ciphers Modes. Ramki Thurimella
 Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
Block Ciphers Modes Ramki Thurimella Only Encryption I.e. messages could be modified Should not assume that nonsensical messages do no harm Always must be combined with authentication 2 Padding Must be
PARTIAL NOTES for 6.1 Trigonometric Identities
 PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
PARTIAL NOTES for 6.1 Trigonometric Identities tanθ = sinθ cosθ cotθ = cosθ sinθ BASIC IDENTITIES cscθ = 1 sinθ secθ = 1 cosθ cotθ = 1 tanθ PYTHAGOREAN IDENTITIES sin θ + cos θ =1 tan θ +1= sec θ 1 + cot
Inverse trigonometric functions & General Solution of Trigonometric Equations. ------------------ ----------------------------- -----------------
 Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
Inverse trigonometric functions & General Solution of Trigonometric Equations. 1. Sin ( ) = a) b) c) d) Ans b. Solution : Method 1. Ans a: 17 > 1 a) is rejected. w.k.t Sin ( sin ) = d is rejected. If sin
5.4 The Poisson Distribution.
 The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
The worst thing you can do about a situation is nothing. Sr. O Shea Jackson 5.4 The Poisson Distribution. Description of the Poisson Distribution Discrete probability distribution. The random variable
Homework 8 Model Solution Section
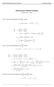 MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
MATH 004 Homework Solution Homework 8 Model Solution Section 14.5 14.6. 14.5. Use the Chain Rule to find dz where z cosx + 4y), x 5t 4, y 1 t. dz dx + dy y sinx + 4y)0t + 4) sinx + 4y) 1t ) 0t + 4t ) sinx
b. Use the parametrization from (a) to compute the area of S a as S a ds. Be sure to substitute for ds!
 MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
MTH U341 urface Integrals, tokes theorem, the divergence theorem To be turned in Wed., Dec. 1. 1. Let be the sphere of radius a, x 2 + y 2 + z 2 a 2. a. Use spherical coordinates (with ρ a) to parametrize.
EE512: Error Control Coding
 EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
EE512: Error Control Coding Solution for Assignment on Finite Fields February 16, 2007 1. (a) Addition and Multiplication tables for GF (5) and GF (7) are shown in Tables 1 and 2. + 0 1 2 3 4 0 0 1 2 3
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Procedures and Functions Stored procedures and functions are named blocks of code that enable you to group and organize a series of SQL and PL/SQL
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ
 ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
ΓΡΑΜΜΙΚΟΣ & ΔΙΚΤΥΑΚΟΣ ΠΡΟΓΡΑΜΜΑΤΙΣΜΟΣ Ενότητα 12: Συνοπτική Παρουσίαση Ανάπτυξης Κώδικα με το Matlab Σαμαράς Νικόλαος Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons.
EPL 603 TOPICS IN SOFTWARE ENGINEERING. Lab 5: Component Adaptation Environment (COPE)
 EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
EPL 603 TOPICS IN SOFTWARE ENGINEERING Lab 5: Component Adaptation Environment (COPE) Performing Static Analysis 1 Class Name: The fully qualified name of the specific class Type: The type of the class
Partial Trace and Partial Transpose
 Partial Trace and Partial Transpose by José Luis Gómez-Muñoz http://homepage.cem.itesm.mx/lgomez/quantum/ jose.luis.gomez@itesm.mx This document is based on suggestions by Anirban Das Introduction This
Partial Trace and Partial Transpose by José Luis Gómez-Muñoz http://homepage.cem.itesm.mx/lgomez/quantum/ jose.luis.gomez@itesm.mx This document is based on suggestions by Anirban Das Introduction This
«Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων. Η μεταξύ τους σχέση και εξέλιξη.»
 ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
ΕΘΝΙΚΟ ΜΕΤΣΟΒΙΟ ΠΟΛΥΤΕΧΝΕΙΟ ΣΧΟΛΗ ΑΓΡΟΝΟΜΩΝ ΚΑΙ ΤΟΠΟΓΡΑΦΩΝ ΜΗΧΑΝΙΚΩΝ ΤΟΜΕΑΣ ΓΕΩΓΡΑΦΙΑΣ ΚΑΙ ΠΕΡΙΦΕΡΕΙΑΚΟΥ ΣΧΕΔΙΑΣΜΟΥ ΔΙΠΛΩΜΑΤΙΚΗ ΕΡΓΑΣΙΑ: «Χρήσεις γης, αξίες γης και κυκλοφοριακές ρυθμίσεις στο Δήμο Χαλκιδέων.
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in
 Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Nowhere-zero flows Let be a digraph, Abelian group. A Γ-circulation in is a mapping : such that, where, and : tail in X, head in : tail in X, head in A nowhere-zero Γ-flow is a Γ-circulation such that
Math221: HW# 1 solutions
 Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Math: HW# solutions Andy Royston October, 5 7.5.7, 3 rd Ed. We have a n = b n = a = fxdx = xdx =, x cos nxdx = x sin nx n sin nxdx n = cos nx n = n n, x sin nxdx = x cos nx n + cos nxdx n cos n = + sin
Σχολή Εφαρμοσμένων Μαθηματικών και Φυσικών Επιστημών. Εθνικό Μετσόβιο Πολυτεχνείο. Thales Workshop, 1-3 July 2015
 Σχολή Εφαρμοσμένων Μαθηματικών και Φυσικών Επιστημών Εθνικό Μετσόβιο Πολυτεχνείο Thales Workshop, 1-3 July 2015 Integrating Behavioural Algebraic Specifications and Design by Contract Nikolaos Triantafyllou
Σχολή Εφαρμοσμένων Μαθηματικών και Φυσικών Επιστημών Εθνικό Μετσόβιο Πολυτεχνείο Thales Workshop, 1-3 July 2015 Integrating Behavioural Algebraic Specifications and Design by Contract Nikolaos Triantafyllou
Galatia SIL Keyboard Information
 Galatia SIL Keyboard Information Keyboard ssignments The main purpose of the keyboards is to provide a wide range of keying options, so many characters can be entered in multiple ways. If you are typing
Galatia SIL Keyboard Information Keyboard ssignments The main purpose of the keyboards is to provide a wide range of keying options, so many characters can be entered in multiple ways. If you are typing
A Note on Intuitionistic Fuzzy. Equivalence Relation
 International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
International Mathematical Forum, 5, 2010, no. 67, 3301-3307 A Note on Intuitionistic Fuzzy Equivalence Relation D. K. Basnet Dept. of Mathematics, Assam University Silchar-788011, Assam, India dkbasnet@rediffmail.com
Advanced Subsidiary Unit 1: Understanding and Written Response
 Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
Write your name here Surname Other names Edexcel GE entre Number andidate Number Greek dvanced Subsidiary Unit 1: Understanding and Written Response Thursday 16 May 2013 Morning Time: 2 hours 45 minutes
Bring Your Own Device (BYOD) Legal Challenges of the new Business Trend MINA ZOULOVITS LAWYER, PARNTER FILOTHEIDIS & PARTNERS LAW FIRM
 Bring Your Own Device (BYOD) Legal Challenges of the new Business Trend MINA ZOULOVITS LAWYER, PARNTER FILOTHEIDIS & PARTNERS LAW FIRM minazoulovits@phrlaw.gr What is BYOD? Information Commissioner's Office
Bring Your Own Device (BYOD) Legal Challenges of the new Business Trend MINA ZOULOVITS LAWYER, PARNTER FILOTHEIDIS & PARTNERS LAW FIRM minazoulovits@phrlaw.gr What is BYOD? Information Commissioner's Office
Finite Field Problems: Solutions
 Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Finite Field Problems: Solutions 1. Let f = x 2 +1 Z 11 [x] and let F = Z 11 [x]/(f), a field. Let Solution: F =11 2 = 121, so F = 121 1 = 120. The possible orders are the divisors of 120. Solution: The
Paper Reference. Paper Reference(s) 1776/04 Edexcel GCSE Modern Greek Paper 4 Writing. Thursday 21 May 2009 Afternoon Time: 1 hour 15 minutes
 Centre No. Candidate No. Paper Reference(s) 1776/04 Edexcel GCSE Modern Greek Paper 4 Writing Thursday 21 May 2009 Afternoon Time: 1 hour 15 minutes Materials required for examination Nil Paper Reference
Centre No. Candidate No. Paper Reference(s) 1776/04 Edexcel GCSE Modern Greek Paper 4 Writing Thursday 21 May 2009 Afternoon Time: 1 hour 15 minutes Materials required for examination Nil Paper Reference
Math 6 SL Probability Distributions Practice Test Mark Scheme
 Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Math 6 SL Probability Distributions Practice Test Mark Scheme. (a) Note: Award A for vertical line to right of mean, A for shading to right of their vertical line. AA N (b) evidence of recognizing symmetry
Sequent Calculi for the Modal µ-calculus over S5. Luca Alberucci, University of Berne. Logic Colloquium Berne, July 4th 2008
 Sequent Calculi for the Modal µ-calculus over S5 Luca Alberucci, University of Berne Logic Colloquium Berne, July 4th 2008 Introduction Koz: Axiomatisation for the modal µ-calculus over K Axioms: All classical
Sequent Calculi for the Modal µ-calculus over S5 Luca Alberucci, University of Berne Logic Colloquium Berne, July 4th 2008 Introduction Koz: Axiomatisation for the modal µ-calculus over K Axioms: All classical
Test Data Management in Practice
 Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
Problems, Concepts, and the Swisscom Test Data Organizer Do you have issues with your legal and compliance department because test environments contain sensitive data outsourcing partners must not see?
A Bonus-Malus System as a Markov Set-Chain. Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics
 A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
A Bonus-Malus System as a Markov Set-Chain Małgorzata Niemiec Warsaw School of Economics Institute of Econometrics Contents 1. Markov set-chain 2. Model of bonus-malus system 3. Example 4. Conclusions
About these lecture notes. Simply Typed λ-calculus. Types
 About these lecture notes Simply Typed λ-calculus Akim Demaille akim@lrde.epita.fr EPITA École Pour l Informatique et les Techniques Avancées Many of these slides are largely inspired from Andrew D. Ker
About these lecture notes Simply Typed λ-calculus Akim Demaille akim@lrde.epita.fr EPITA École Pour l Informatique et les Techniques Avancées Many of these slides are largely inspired from Andrew D. Ker
Jesse Maassen and Mark Lundstrom Purdue University November 25, 2013
 Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Notes on Average Scattering imes and Hall Factors Jesse Maassen and Mar Lundstrom Purdue University November 5, 13 I. Introduction 1 II. Solution of the BE 1 III. Exercises: Woring out average scattering
Partial Differential Equations in Biology The boundary element method. March 26, 2013
 The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
The boundary element method March 26, 203 Introduction and notation The problem: u = f in D R d u = ϕ in Γ D u n = g on Γ N, where D = Γ D Γ N, Γ D Γ N = (possibly, Γ D = [Neumann problem] or Γ N = [Dirichlet
Example Sheet 3 Solutions
 Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Example Sheet 3 Solutions. i Regular Sturm-Liouville. ii Singular Sturm-Liouville mixed boundary conditions. iii Not Sturm-Liouville ODE is not in Sturm-Liouville form. iv Regular Sturm-Liouville note
Formal Semantics. 1 Type Logic
 Formal Semantics Principle of Compositionality The meaning of a sentence is determined by the meanings of its parts and the way they are put together. 1 Type Logic Types (a measure on expressions) The
Formal Semantics Principle of Compositionality The meaning of a sentence is determined by the meanings of its parts and the way they are put together. 1 Type Logic Types (a measure on expressions) The
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ»
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
ΠΑΝΕΠΙΣΤΗΜΙΟ ΠΕΙΡΑΙΩΣ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΜΣ «ΠΡΟΗΓΜΕΝΑ ΣΥΣΤΗΜΑΤΑ ΠΛΗΡΟΦΟΡΙΚΗΣ» ΚΑΤΕΥΘΥΝΣΗ «ΕΥΦΥΕΙΣ ΤΕΧΝΟΛΟΓΙΕΣ ΕΠΙΚΟΙΝΩΝΙΑΣ ΑΝΘΡΩΠΟΥ - ΥΠΟΛΟΓΙΣΤΗ» ΜΕΤΑΠΤΥΧΙΑΚΗ ΙΑΤΡΙΒΗ ΤΟΥ ΕΥΘΥΜΙΟΥ ΘΕΜΕΛΗ ΤΙΤΛΟΣ Ανάλυση
Econ 2110: Fall 2008 Suggested Solutions to Problem Set 8 questions or comments to Dan Fetter 1
 Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
Eon : Fall 8 Suggested Solutions to Problem Set 8 Email questions or omments to Dan Fetter Problem. Let X be a salar with density f(x, θ) (θx + θ) [ x ] with θ. (a) Find the most powerful level α test
From the finite to the transfinite: Λµ-terms and streams
 From the finite to the transfinite: Λµ-terms and streams WIR 2014 Fanny He f.he@bath.ac.uk Alexis Saurin alexis.saurin@pps.univ-paris-diderot.fr 12 July 2014 The Λµ-calculus Syntax of Λµ t ::= x λx.t (t)u
From the finite to the transfinite: Λµ-terms and streams WIR 2014 Fanny He f.he@bath.ac.uk Alexis Saurin alexis.saurin@pps.univ-paris-diderot.fr 12 July 2014 The Λµ-calculus Syntax of Λµ t ::= x λx.t (t)u
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 6/5/2006
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Ολοι οι αριθμοί που αναφέρονται σε όλα τα ερωτήματα είναι μικρότεροι το 1000 εκτός αν ορίζεται διαφορετικά στη διατύπωση του προβλήματος. Διάρκεια: 3,5 ώρες Καλή
ΑΓΓΛΙΚΑ Ι. Ενότητα 7α: Impact of the Internet on Economic Education. Ζωή Κανταρίδου Τμήμα Εφαρμοσμένης Πληροφορικής
 Ενότητα 7α: Impact of the Internet on Economic Education Τμήμα Εφαρμοσμένης Πληροφορικής Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό, όπως
Ενότητα 7α: Impact of the Internet on Economic Education Τμήμα Εφαρμοσμένης Πληροφορικής Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης Creative Commons. Για εκπαιδευτικό υλικό, όπως
ΣΟΡΟΠΤΙΜΙΣΤΡΙΕΣ ΕΛΛΗΝΙΔΕΣ
 ΕΛΛΗΝΙΔΕΣ ΣΟΡΟΠΤΙΜΙΣΤΡΙΕΣ ΕΚΔΟΣΗ ΤΗΣ ΣΟΡΟΠΤΙΜΙΣΤΙΚΗΣ ΕΝΩΣΗΣ ΕΛΛΑΔΟΣ - ΤΕΥΧΟΣ Νο 110 - Δ ΤΡΙΜΗΝΟ 2014 Το πρώτο βραβείο κέρδισε η Ελλάδα για την φωτογραφία Blue + Yellow = Green στον διαγωνισμό 2014 του
ΕΛΛΗΝΙΔΕΣ ΣΟΡΟΠΤΙΜΙΣΤΡΙΕΣ ΕΚΔΟΣΗ ΤΗΣ ΣΟΡΟΠΤΙΜΙΣΤΙΚΗΣ ΕΝΩΣΗΣ ΕΛΛΑΔΟΣ - ΤΕΥΧΟΣ Νο 110 - Δ ΤΡΙΜΗΝΟ 2014 Το πρώτο βραβείο κέρδισε η Ελλάδα για την φωτογραφία Blue + Yellow = Green στον διαγωνισμό 2014 του
Γιπλυμαηική Δπγαζία. «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ. Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο
 ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
ΔΘΝΙΚΟ ΜΔΣΟΒΙΟ ΠΟΛΤΣΔΥΝΔΙΟ ΥΟΛΗ ΝΑΤΠΗΓΩΝ ΜΗΥΑΝΟΛΟΓΩΝ ΜΗΥΑΝΙΚΩΝ Γιπλυμαηική Δπγαζία «Ανθπυποκενηπικόρ ζσεδιαζμόρ γέθςπαρ πλοίος» Φοςζιάνηρ Αθανάζιορ Δπιβλέπυν Καθηγηηήρ: Νηθφιανο Π. Βεληίθνο Σπιμελήρ Δξεηαζηική
Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook
 Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook Βήμα 1: Step 1: Βρείτε το βιβλίο που θα θέλατε να αγοράσετε και πατήστε Add to Cart, για να το προσθέσετε στο καλάθι σας. Αυτόματα θα
Οδηγίες Αγοράς Ηλεκτρονικού Βιβλίου Instructions for Buying an ebook Βήμα 1: Step 1: Βρείτε το βιβλίο που θα θέλατε να αγοράσετε και πατήστε Add to Cart, για να το προσθέσετε στο καλάθι σας. Αυτόματα θα
Srednicki Chapter 55
 Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
Srednicki Chapter 55 QFT Problems & Solutions A. George August 3, 03 Srednicki 55.. Use equations 55.3-55.0 and A i, A j ] = Π i, Π j ] = 0 (at equal times) to verify equations 55.-55.3. This is our third
ΚΥΠΡΙΑΚΗ ΕΤΑΙΡΕΙΑ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ 19/5/2007
 Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Οδηγίες: Να απαντηθούν όλες οι ερωτήσεις. Αν κάπου κάνετε κάποιες υποθέσεις να αναφερθούν στη σχετική ερώτηση. Όλα τα αρχεία που αναφέρονται στα προβλήματα βρίσκονται στον ίδιο φάκελο με το εκτελέσιμο
Solutions to Exercise Sheet 5
 Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
Solutions to Eercise Sheet 5 jacques@ucsd.edu. Let X and Y be random variables with joint pdf f(, y) = 3y( + y) where and y. Determine each of the following probabilities. Solutions. a. P (X ). b. P (X
Démographie spatiale/spatial Demography
 ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
ΠΑΝΕΠΙΣΤΗΜΙΟ ΘΕΣΣΑΛΙΑΣ Démographie spatiale/spatial Demography Session 1: Introduction to spatial demography Basic concepts Michail Agorastakis Department of Planning & Regional Development Άδειες Χρήσης
6.1. Dirac Equation. Hamiltonian. Dirac Eq.
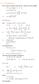 6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
6.1. Dirac Equation Ref: M.Kaku, Quantum Field Theory, Oxford Univ Press (1993) η μν = η μν = diag(1, -1, -1, -1) p 0 = p 0 p = p i = -p i p μ p μ = p 0 p 0 + p i p i = E c 2 - p 2 = (m c) 2 H = c p 2
Matrices and Determinants
 Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Matrices and Determinants SUBJECTIVE PROBLEMS: Q 1. For what value of k do the following system of equations possess a non-trivial (i.e., not all zero) solution over the set of rationals Q? x + ky + 3z
Figure A.2: MPC and MPCP Age Profiles (estimating ρ, ρ = 2, φ = 0.03)..
 Supplemental Material (not for publication) Persistent vs. Permanent Income Shocks in the Buffer-Stock Model Jeppe Druedahl Thomas H. Jørgensen May, A Additional Figures and Tables Figure A.: Wealth and
Supplemental Material (not for publication) Persistent vs. Permanent Income Shocks in the Buffer-Stock Model Jeppe Druedahl Thomas H. Jørgensen May, A Additional Figures and Tables Figure A.: Wealth and
Strain gauge and rosettes
 Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Strain gauge and rosettes Introduction A strain gauge is a device which is used to measure strain (deformation) on an object subjected to forces. Strain can be measured using various types of devices classified
Abstract Storage Devices
 Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Abstract Storage Devices Robert König Ueli Maurer Stefano Tessaro SOFSEM 2009 January 27, 2009 Outline 1. Motivation: Storage Devices 2. Abstract Storage Devices (ASD s) 3. Reducibility 4. Factoring ASD
Bayesian statistics. DS GA 1002 Probability and Statistics for Data Science.
 Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
Bayesian statistics DS GA 1002 Probability and Statistics for Data Science http://www.cims.nyu.edu/~cfgranda/pages/dsga1002_fall17 Carlos Fernandez-Granda Frequentist vs Bayesian statistics In frequentist
On the Galois Group of Linear Difference-Differential Equations
 On the Galois Group of Linear Difference-Differential Equations Ruyong Feng KLMM, Chinese Academy of Sciences, China Ruyong Feng (KLMM, CAS) Galois Group 1 / 19 Contents 1 Basic Notations and Concepts
On the Galois Group of Linear Difference-Differential Equations Ruyong Feng KLMM, Chinese Academy of Sciences, China Ruyong Feng (KLMM, CAS) Galois Group 1 / 19 Contents 1 Basic Notations and Concepts
Προσωπική Aνάπτυξη. Ενότητα 2: Διαπραγμάτευση. Juan Carlos Martínez Director of Projects Development Department
 Προσωπική Aνάπτυξη Ενότητα 2: Διαπραγμάτευση Juan Carlos Martínez Director of Projects Development Department Unit Scope Σε αυτή την ενότητα θα μελετήσουμε τα βασικά των καταστάσεων διαπραγμάτευσης winwin,
Προσωπική Aνάπτυξη Ενότητα 2: Διαπραγμάτευση Juan Carlos Martínez Director of Projects Development Department Unit Scope Σε αυτή την ενότητα θα μελετήσουμε τα βασικά των καταστάσεων διαπραγμάτευσης winwin,
Second Order Partial Differential Equations
 Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
Chapter 7 Second Order Partial Differential Equations 7.1 Introduction A second order linear PDE in two independent variables (x, y Ω can be written as A(x, y u x + B(x, y u xy + C(x, y u u u + D(x, y
CYTA Cloud Server Set Up Instructions
 CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
CYTA Cloud Server Set Up Instructions ΕΛΛΗΝΙΚΑ ENGLISH Initial Set-up Cloud Server To proceed with the initial setup of your Cloud Server first login to the Cyta CloudMarketPlace on https://cloudmarketplace.cyta.com.cy
Η ΠΡΟΣΩΠΙΚΗ ΟΡΙΟΘΕΤΗΣΗ ΤΟΥ ΧΩΡΟΥ Η ΠΕΡΙΠΤΩΣΗ ΤΩΝ CHAT ROOMS
 ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ Ι Ο Ν Ι Ω Ν Ν Η Σ Ω Ν ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : ΑΤΕΙ Ιονίων Νήσων- Λεωφόρος Αντώνη Τρίτση Αργοστόλι Κεφαλληνίας, Ελλάδα 28100,+30
ΕΛΛΗΝΙΚΗ ΔΗΜΟΚΡΑΤΙΑ ΤΕΧΝΟΛΟΓΙΚΟ ΕΚΠΑΙΔΕΥΤΙΚΟ ΙΔΡΥΜΑ Ι Ο Ν Ι Ω Ν Ν Η Σ Ω Ν ΤΜΗΜΑ ΔΗΜΟΣΙΩΝ ΣΧΕΣΕΩΝ & ΕΠΙΚΟΙΝΩΝΙΑΣ Ταχ. Δ/νση : ΑΤΕΙ Ιονίων Νήσων- Λεωφόρος Αντώνη Τρίτση Αργοστόλι Κεφαλληνίας, Ελλάδα 28100,+30
ΚΥΠΡΙΑΚΟΣ ΣΥΝΔΕΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ CYPRUS COMPUTER SOCIETY 21 ος ΠΑΓΚΥΠΡΙΟΣ ΜΑΘΗΤΙΚΟΣ ΔΙΑΓΩΝΙΣΜΟΣ ΠΛΗΡΟΦΟΡΙΚΗΣ Δεύτερος Γύρος - 30 Μαρτίου 2011
 Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
Διάρκεια Διαγωνισμού: 3 ώρες Απαντήστε όλες τις ερωτήσεις Μέγιστο Βάρος (20 Μονάδες) Δίνεται ένα σύνολο από N σφαιρίδια τα οποία δεν έχουν όλα το ίδιο βάρος μεταξύ τους και ένα κουτί που αντέχει μέχρι
General 2 2 PT -Symmetric Matrices and Jordan Blocks 1
 General 2 2 PT -Symmetric Matrices and Jordan Blocks 1 Qing-hai Wang National University of Singapore Quantum Physics with Non-Hermitian Operators Max-Planck-Institut für Physik komplexer Systeme Dresden,
General 2 2 PT -Symmetric Matrices and Jordan Blocks 1 Qing-hai Wang National University of Singapore Quantum Physics with Non-Hermitian Operators Max-Planck-Institut für Physik komplexer Systeme Dresden,
Locking to ensure serializability
 Locking to ensure serializability Concurrent access to database items is controlled by strategies based on locking, timestamping or certification A lock is an access privilege to a single database item
Locking to ensure serializability Concurrent access to database items is controlled by strategies based on locking, timestamping or certification A lock is an access privilege to a single database item
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1
 Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
Main source: "Discrete-time systems and computer control" by Α. ΣΚΟΔΡΑΣ ΨΗΦΙΑΚΟΣ ΕΛΕΓΧΟΣ ΔΙΑΛΕΞΗ 4 ΔΙΑΦΑΝΕΙΑ 1 A Brief History of Sampling Research 1915 - Edmund Taylor Whittaker (1873-1956) devised a
k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +
[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R + k A = [k, k]( )[a 1, a 2 ] = [ka 1,ka 2 ] 4For the division of two intervals of confidence in R +](/thumbs/73/69566903.jpg) Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Chapter 3. Fuzzy Arithmetic 3- Fuzzy arithmetic: ~Addition(+) and subtraction (-): Let A = [a and B = [b, b in R If x [a and y [b, b than x+y [a +b +b Symbolically,we write A(+)B = [a (+)[b, b = [a +b
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων. Εξάμηνο 7 ο
 Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Oracle SQL Developer An Oracle Database stores and organizes information. Oracle SQL Developer is a tool for accessing and maintaining the data
Εργαστήριο Ανάπτυξης Εφαρμογών Βάσεων Δεδομένων Εξάμηνο 7 ο Oracle SQL Developer An Oracle Database stores and organizes information. Oracle SQL Developer is a tool for accessing and maintaining the data
Προσωπική Aνάπτυξη. Ενότητα 4: Συνεργασία. Juan Carlos Martínez Director of Projects Development Department
 Προσωπική Aνάπτυξη Ενότητα 4: Συνεργασία Juan Carlos Martínez Director of Projects Development Department Σκοπός 1. Πώς να χτίσετε και να διατηρήσετε μια αποτελεσματική ομάδα Σε αυτό πρόγραμμα, εντός
Προσωπική Aνάπτυξη Ενότητα 4: Συνεργασία Juan Carlos Martínez Director of Projects Development Department Σκοπός 1. Πώς να χτίσετε και να διατηρήσετε μια αποτελεσματική ομάδα Σε αυτό πρόγραμμα, εντός
ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ
 ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ Ενότητα 1β: Principles of PS Ιφιγένεια Μαχίλη Τμήμα Οικονομικών Επιστημών Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης
ΑΓΓΛΙΚΗ ΓΛΩΣΣΑ ΣΕ ΕΙΔΙΚΑ ΘΕΜΑΤΑ ΔΙΕΘΝΩΝ ΣΧΕΣΕΩΝ & ΟΙΚΟΝΟΜΙΑΣ Ενότητα 1β: Principles of PS Ιφιγένεια Μαχίλη Τμήμα Οικονομικών Επιστημών Άδειες Χρήσης Το παρόν εκπαιδευτικό υλικό υπόκειται σε άδειες χρήσης
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική»
 Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
Πανεπιστήμιο Πειραιώς Τμήμα Πληροφορικής Πρόγραμμα Μεταπτυχιακών Σπουδών «Πληροφορική» Μεταπτυχιακή Διατριβή Τίτλος Διατριβής Επίκαιρα Θέματα Ηλεκτρονικής Διακυβέρνησης Ονοματεπώνυμο Φοιτητή Σταμάτιος
Physical DB Design. B-Trees Index files can become quite large for large main files Indices on index files are possible.
 B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
B-Trees Index files can become quite large for large main files Indices on index files are possible 3 rd -level index 2 nd -level index 1 st -level index Main file 1 The 1 st -level index consists of pairs
